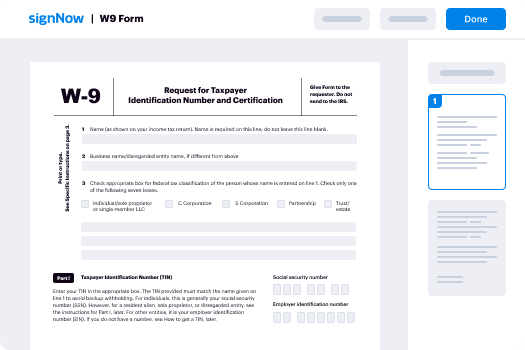
How To Sign Louisiana Banking PDF
Contact Sales
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Discover the easiest way to Sign Louisiana Banking PDF with our powerful tools that go beyond eSignature. Sign documents and collect data, signatures, and payments from other parties from a single solution.
Robust integration and API capabilities
Enable the airSlate SignNow API and supercharge your workspace systems with eSignature tools. Streamline data routing and record updates with out-of-the-box integrations.
Advanced security and compliance
Set up your eSignature workflows while staying compliant with major eSignature, data protection, and eCommerce laws. Use airSlate SignNow to make every interaction with a document secure and compliant.
Various collaboration tools
Make communication and interaction within your team more transparent and effective. Accomplish more with minimal efforts on your side and add value to the business.
Enjoyable and stress-free signing experience
Delight your partners and employees with a straightforward way of signing documents. Make document approval flexible and precise.
Extensive support
Explore a range of video tutorials and guides on how to Sign Louisiana Banking PDF. Get all the help you need from our dedicated support team.
How to industry sign banking louisiana pdf later
Keep your eSignature workflows on track
Make the signing process more streamlined and uniform
Take control of every aspect of the document execution process. eSign, send out for signature, manage, route, and save your documents in a single secure solution.
Add and collect signatures from anywhere
Let your customers and your team stay connected even when offline. Access airSlate SignNow to Sign Louisiana Banking PDF from any platform or device: your laptop, mobile phone, or tablet.
Ensure error-free results with reusable templates
Templatize frequently used documents to save time and reduce the risk of common errors when sending out copies for signing.
Stay compliant and secure when eSigning
Use airSlate SignNow to Sign Louisiana Banking PDF and ensure the integrity and security of your data at every step of the document execution cycle.
Enjoy the ease of setup and onboarding process
Have your eSignature workflow up and running in minutes. Take advantage of numerous detailed guides and tutorials, or contact our dedicated support team to make the most out of the airSlate SignNow functionality.
Benefit from integrations and API for maximum efficiency
Integrate with a rich selection of productivity and data storage tools. Create a more encrypted and seamless signing experience with the airSlate SignNow API.
Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
Our user reviews speak for themselves






-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
Trusted esignature solution— what our customers are saying
be ready to get more
Get legally-binding signatures now!
Related searches to How To Sign Louisiana Banking PDF
ladotd traffic signs
louisiana dotd traffic control
Frequently asked questions
How do i add an electronic signature to a word document?
When a client enters information (such as a password) into the online form on , the information is encrypted so the client cannot see it. An authorized representative for the client, called a "Doe Representative," must enter the information into the "Signature" field to complete the signature.
How to sign a document on pdf viewer?
You can choose to do a copy/paste or a "quick read" and the "smart cut" option. Copy/Paste Copy:
Select your document and press ctrl and a letter to copy it.
Now select all the letter you want to copy and press CTRL and v to copy it and select the letter you want to cut ( b). This will show you a dialog with 2 options. You can then choose "copy and paste", if you want to cut from 1 letter and paste the other.
If you want to cut from the second letter you'll have to use "smart cut"
Smart Cut:
Select all the letter you want to cut and press CTRL and v (Shift-v to paste if it's a "copy and paste").
Now the letter you want to cut will be highlighted, select it.
Now press the space bar to cut to start cutting. This will show you a dialog with the options "copy and cut". You can choose to copy or cut to start cutting.
You must select the cut you want to make with "smart cut"
In this version, when cutting to start cutting it will not show the cut icon, unless you are cutting a letter you have already selected.
You must select the cut you want to make with "smart cut"
In this version, when cutting to start cutting it will not show the cut icon, unless you are cutting a letter you have already selected. Cut with one letter:
In this version, you must select the cut you want to make with "smart cut" and it will not show the cut icon.
How do you create a new esign pin?
The short answer is that you will need to use a computer or Android device in order to create a pin.
Create a pin
Create an esign pin (also called a "key") using an esign program (, ) on a computer/device with a working account.
You can use an esign program or your phone with Android to create a pin.
Create a pin
You may use the version of esignon to create a new pin if you are using an account that you don't need to manage keys in.
If it's your first time creating an esign pin, we recommend that you first generate one on your phone. See How do I create an esign pin on my phone? .
Step1: Create an esign pin
Click the Create button ( ) next to the pin ( ) and click Generate. This will start the generation process. When you are finished, click the Verify button. This will open a pop-up window asking you to confirm that you want to verify your pin. Click the Verify button.
If all works well, you'll see a dialog box, similar to the following, asking you for your account name, pass code or other security information. If you don't know your password or security key, you should create them before proceeding with this process:
Note: If you create an esign pin on a computer and don't use a phone, you'll have to manually enter your account name, pass code or other information.
Note: If you created an esign pin in an Android version earlier than KitKat, you will get a warning on the pop-up dialog box, similar to the following, stating that you don't have an esign account...
Get more for How To Sign Louisiana Banking PDF
- How Can I Sign North Dakota Car Dealer Stock Certificate
- Can I Sign North Dakota Car Dealer Stock Certificate
- Sign North Dakota Car Dealer Stock Certificate Mobile
- Sign North Dakota Car Dealer Stock Certificate Now
- Sign Ohio Car Dealer Job Offer Online
- Sign Ohio Car Dealer Job Offer Computer
- Sign North Dakota Car Dealer Stock Certificate Later
- Sign Ohio Car Dealer Job Offer Mobile
Find out other How To Sign Louisiana Banking PDF
- Request restraining order 497299204 form
- Order juvenile form
- Ca notice hearing form
- Ca caregiver form
- De facto parent request california form
- De facto parent statement california form
- Parent order form
- California ending form
- De facto parent pamphlet california form
- Notice hearing form
- Ca code form
- Request for prospective adoptive parent designation notice and order california form
- Prospective adoptive parent form
- Notice of intent to remove child and proof of notice objection to removal and order after hearing california form
- Emergency removal form
- California objection 497299220 form
- California guardianship 497299221 form
- Guardianship pamphlet california 497299222 form
- Cillero de la tutela a las garantasderecho penal form
- California termination form