Decline Assignee Digital Signature with airSlate SignNow
Get the powerful eSignature features you need from the company you trust
Select the pro platform created for pros
Configure eSignature API with ease
Collaborate better together
Decline assignee digital signature, in minutes
Cut the closing time
Maintain sensitive information safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

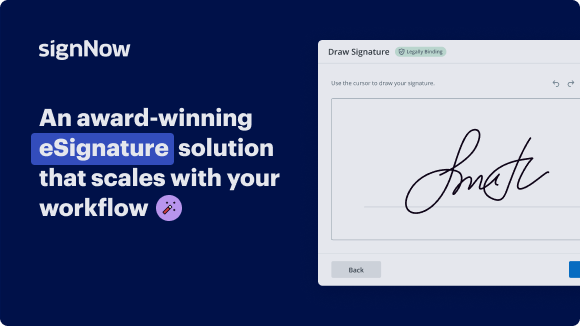
Your step-by-step guide — decline assignee digital signature
Using airSlate SignNow’s eSignature any business can speed up signature workflows and eSign in real-time, delivering a better experience to customers and employees. decline assignee digital signature in a few simple steps. Our mobile-first apps make working on the go possible, even while offline! Sign documents from anywhere in the world and close deals faster.
Follow the step-by-step guide to decline assignee digital signature:
- Log in to your airSlate SignNow account.
- Locate your document in your folders or upload a new one.
- Open the document and make edits using the Tools menu.
- Drag & drop fillable fields, add text and sign it.
- Add multiple signers using their emails and set the signing order.
- Specify which recipients will get an executed copy.
- Use Advanced Options to limit access to the record and set an expiration date.
- Click Save and Close when completed.
In addition, there are more advanced features available to decline assignee digital signature. Add users to your shared workspace, view teams, and track collaboration. Millions of users across the US and Europe agree that a solution that brings everything together in one unified enviroment, is what organizations need to keep workflows performing smoothly. The airSlate SignNow REST API enables you to integrate eSignatures into your app, website, CRM or cloud. Check out airSlate SignNow and get quicker, smoother and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
Get legally-binding signatures now!
FAQs
-
How does signature verification work?
Verifying a signature will tell you if the signed data has changed or not. When a digital signature is verified, the signature is decrypted using the public key to produce the original hash value. The data that was signed is hashed. If the two hash values match, then the signature has been verified. -
How does signature airSlate SignNow verify?
Log in to your account or register a new one. Upload a document and click Open in airSlate SignNow. Modify the document. Sign the PDF using the My Signature tool. -
Is airSlate SignNow legally binding?
airSlate SignNow documents are also legally binding and exceed the security and authentication requirement of ESIGN. Our eSignature solution is safe and dependable for any industry, and we promise that your documents will be kept safe and secure. -
How is online signature verification done?
Signature verification technology requires primarily a digitizing tablet and a special pen connected to the universal serial bus port (USB port) of a computer. An individual can sign on the digitizing tablet using the special pen regardless of his signature size and position.
What active users are saying — decline assignee digital signature
Related searches to decline assignee digital signature with airSlate SignNow
Use double factor authentication, Edit electronic signature and eSignature
all right I just did this whole video my microphone wasn't plugged in so yeah so we're gonna talk about a lot of interesting things here so interesting that you should probably just hit subscribe right now so we're gonna be talking about digital signatures let's get started Pluralsight it's one of the first learning platforms I used as a software developer you can get a completely free trial and start learning by following a path on pretty much anything the learning paths combine numerous courses giving you the step-by-step path to reach your goals or you can find individual courses on pretty much anything maybe you want a class on cryptography security Python programming networking maybe Java you name it and they probably have it I can genuinely say that Pluralsight helped me advance my skills and my career I'll leave a referral link in the description go check it out so this kind of scoops together all of the information we've talked about in my cryptography crash course or micro series or whatever you want to call it and it's related to this and it uses a lot of these principles but it's not exactly the same thing so we've talked about cryptography now we're talking about digital signatures which is a little bit different than cryptography but uses a lot of the same concepts and works in a similar way it's different in its purpose what we're gonna be talking about in this video is how to verify if a message came from the intended sender or if the the message has been tampered with that is different than cryptography which is to make a message secret in in delivery so very similar but just a tiny bit different and it's probably just going to take these things that we've talked about and just flip it around just a little bit so that we're working in a different direction and you know exactly what I mean in just a second but first let's take a look at this image which is an illustration of public key encryption or another word would be asymmetric encryption where we have two keys a public key and a private key and the the public key is used to encrypt so Bob can encrypt a message designed to be sent to Elise and the only person that can read this message is elise because she actually uses her private key to decrypt it digital signing and confirmation is going to flip this around a little bit such that it looks like this elise is now going to use her private key to sign a message and then bob is going to use her public key to verify that that message came from her so let's take a little moment to talk about the top part we have a message we have a private key and we mix these together and that goes to Bob but it goes to him in such a...
Show more