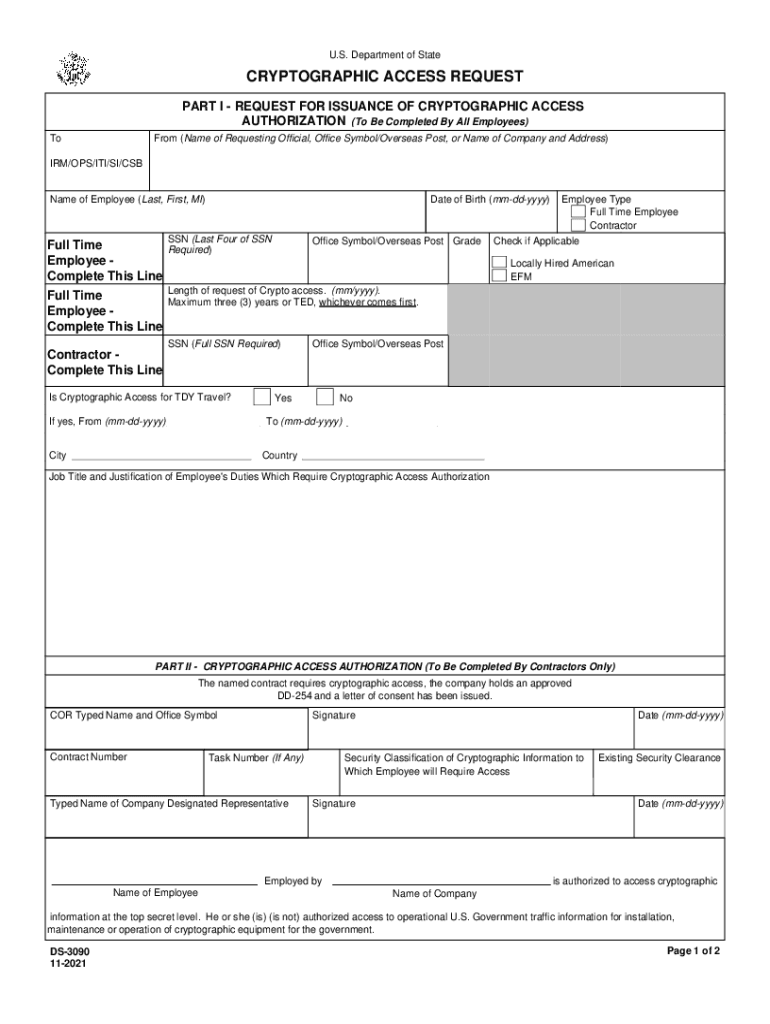
Cryptographic Form


What is the cryptographic form
The cryptographic form is a digital document designed to ensure the secure transmission and verification of information. It incorporates advanced encryption techniques to protect sensitive data and maintain the integrity of the document. This form is commonly used in various applications, including legal agreements, tax submissions, and other official paperwork where authenticity is crucial. By utilizing cryptographic methods, the form guarantees that the information contained within cannot be altered without detection, thus providing a reliable means of communication in a digital environment.
How to use the cryptographic form
Using the cryptographic form involves several straightforward steps. First, ensure you have access to a digital platform that supports cryptographic signatures. Next, fill out the required fields within the form, providing accurate and complete information. After completing the form, apply your digital signature, which is typically generated through a secure authentication process. This signature confirms your identity and the integrity of the document. Finally, submit the form through the designated electronic submission method, ensuring it is transmitted securely to the intended recipient.
Steps to complete the cryptographic form
Completing the cryptographic form requires careful attention to detail. Follow these steps for a successful submission:
- Access the cryptographic form through a secure digital platform.
- Enter all required information accurately, ensuring there are no errors.
- Review the form for completeness and accuracy before proceeding.
- Apply your digital signature, which may involve a two-factor authentication process.
- Submit the form electronically, ensuring it is sent to the correct recipient.
Legal use of the cryptographic form
The legal use of the cryptographic form is governed by various regulations that recognize electronic signatures as valid. In the United States, the ESIGN Act and UETA provide the legal framework for electronic signatures, ensuring that documents signed digitally hold the same weight as traditional handwritten signatures. To ensure compliance, it is essential to use a platform that adheres to these legal standards, thereby guaranteeing that the cryptographic form is recognized in legal proceedings and by governmental agencies.
Key elements of the cryptographic form
Several key elements define the effectiveness and security of the cryptographic form. These include:
- Encryption: Protects the data during transmission, preventing unauthorized access.
- Digital signatures: Authenticate the identity of the signer and ensure the document's integrity.
- Audit trails: Provide a record of all actions taken on the document, including timestamps and IP addresses.
- Compliance with regulations: Ensures the form meets legal standards for electronic documentation.
State-specific rules for the cryptographic form
Each state may have specific regulations regarding the use of cryptographic forms. It is important to familiarize yourself with these rules to ensure compliance. Some states may have additional requirements for electronic signatures, such as specific authentication methods or record-keeping practices. Always verify the state-specific guidelines before submitting a cryptographic form to avoid potential legal issues.
Quick guide on how to complete cryptographic form
Effortlessly Prepare Cryptographic Form on Any Device
Digital document management has gained popularity among businesses and individuals. It offers an excellent eco-conscious alternative to conventional printed and signed documents, as you can easily find the right template and securely preserve it online. airSlate SignNow equips you with all the tools necessary to create, modify, and electronically sign your documents promptly, without any delays. Manage Cryptographic Form on any platform using airSlate SignNow’s Android or iOS applications and simplify your document-driven tasks today.
The easiest way to modify and electronically sign Cryptographic Form with ease
- Obtain Cryptographic Form and click on Get Form to initiate.
- Utilize the tools we offer to fill out your document.
- Emphasize important sections of your documents or obscure sensitive details with the tools that airSlate SignNow provides specifically for that purpose.
- Create your signature with the Sign tool, which takes just seconds and carries the same legal validity as a traditional handwritten signature.
- Review the information and click on the Done button to save your modifications.
- Choose your preferred method to send your form, whether by email, SMS, or invitation link, or download it to your computer.
Forget about lost or misplaced documents, tedious form searches, or errors that necessitate printing additional copies. airSlate SignNow addresses all your document management needs in just a few clicks from any device you choose. Edit and electronically sign Cryptographic Form to ensure exceptional communication at every stage of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
People also ask
-
What is a cryptographic form in the context of airSlate SignNow?
A cryptographic form refers to a digital document secured with encryption technology, ensuring that the information is tamper-proof and confidential. In airSlate SignNow, cryptographic forms are used to authenticate signatures and protect sensitive data during eSigning.
-
How does airSlate SignNow ensure the security of cryptographic forms?
airSlate SignNow employs advanced encryption methods to secure cryptographic forms, which include both SSL encryption during transmission and AES encryption for stored data. This layered security approach safeguards documents against unauthorized access and alterations.
-
Can I integrate airSlate SignNow with other applications while using cryptographic forms?
Yes, airSlate SignNow supports integrations with major platforms like Google Workspace, Salesforce, and others. This allows you to use cryptographic forms seamlessly within your existing workflows and applications, enhancing productivity and security.
-
Is it possible to track changes in cryptographic forms with airSlate SignNow?
Absolutely! airSlate SignNow provides an audit trail that logs every action taken on cryptographic forms, including who signed and when. This feature is essential for compliance and can help resolve any disputes regarding document integrity.
-
What are the pricing options for using airSlate SignNow with cryptographic forms?
airSlate SignNow offers a variety of pricing plans to suit different business needs, whether you require basic eSigning features or advanced capabilities involving cryptographic forms. You can choose from monthly or annual subscriptions, with discounts available for long-term commitments.
-
What benefits does using cryptographic forms provide in airSlate SignNow?
Using cryptographic forms in airSlate SignNow enhances document security, ensures authenticity, and complies with regulations for electronic signatures. This not only builds trust with clients but also streamlines your business processes by reducing paper usage and manual errors.
-
Are cryptographic forms legally binding when signed through airSlate SignNow?
Yes, cryptographic forms signed through airSlate SignNow are legally binding in accordance with the ESIGN Act and UETA. The platform's use of cryptography ensures the signatures' integrity, making them enforceable in courts.
Get more for Cryptographic Form
Find out other Cryptographic Form
- How To Electronic signature Tennessee Franchise Contract
- Help Me With Electronic signature California Consulting Agreement Template
- How To Electronic signature Kentucky Investment Contract
- Electronic signature Tennessee Consulting Agreement Template Fast
- How To Electronic signature California General Power of Attorney Template
- eSignature Alaska Bill of Sale Immovable Property Online
- Can I Electronic signature Delaware General Power of Attorney Template
- Can I Electronic signature Michigan General Power of Attorney Template
- Can I Electronic signature Minnesota General Power of Attorney Template
- How Do I Electronic signature California Distributor Agreement Template
- eSignature Michigan Escrow Agreement Simple
- How Do I Electronic signature Alabama Non-Compete Agreement
- How To eSignature North Carolina Sales Receipt Template
- Can I Electronic signature Arizona LLC Operating Agreement
- Electronic signature Louisiana LLC Operating Agreement Myself
- Can I Electronic signature Michigan LLC Operating Agreement
- How Can I Electronic signature Nevada LLC Operating Agreement
- Electronic signature Ohio LLC Operating Agreement Now
- Electronic signature Ohio LLC Operating Agreement Myself
- How Do I Electronic signature Tennessee LLC Operating Agreement