Cyber Security Incident Reporting Form


Understanding Cyber Security Incident Reporting
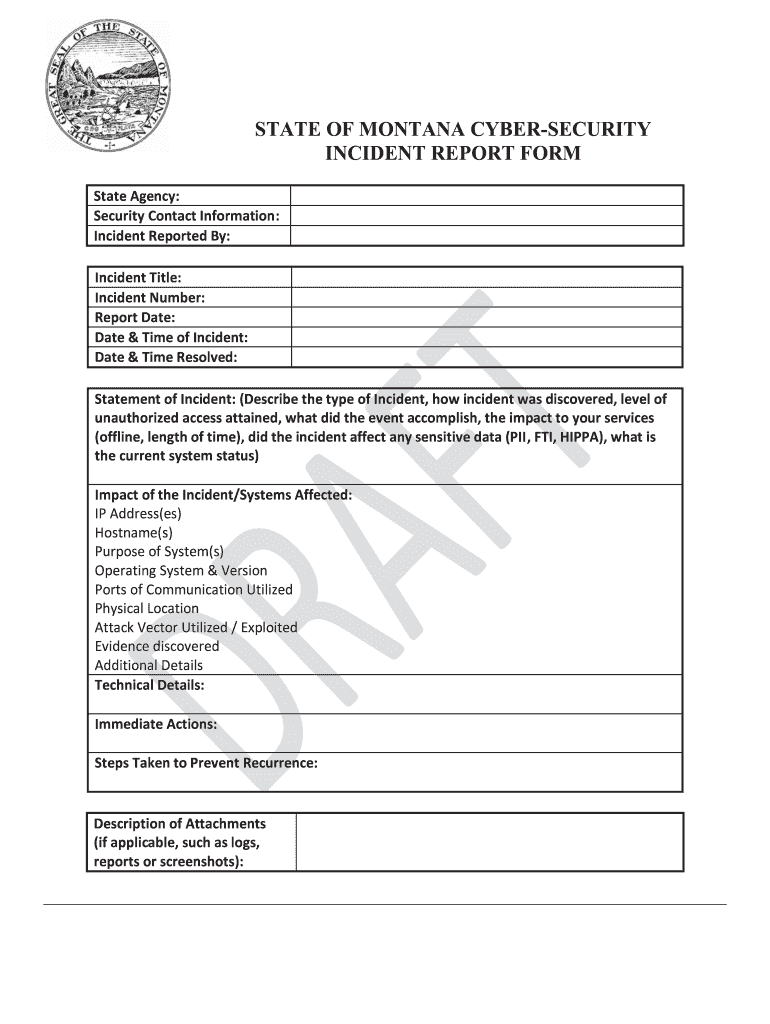
A cyber security incident report is a formal document that outlines a security breach or incident affecting an organization. This report serves as a critical tool for documenting the specifics of the incident, including the nature of the breach, the systems affected, and the response taken. It is essential for compliance with legal and regulatory requirements, as well as for internal review and improvement of security measures. Organizations often use a cyber security incident report template to ensure that all relevant information is captured systematically and consistently.
Steps to Complete the Cyber Security Incident Reporting
Completing a cyber security incident report involves several key steps to ensure thorough documentation and effective response. Start by gathering all relevant details about the incident, including the date and time it occurred, the systems or data affected, and the individuals involved. Next, document the nature of the incident, such as unauthorized access, data breaches, or malware infections. After that, outline the immediate response actions taken, including containment measures and notifications to stakeholders. Finally, review the report for accuracy and completeness before submitting it to the appropriate authorities within your organization.
Legal Use of the Cyber Security Incident Reporting
The legal validity of a cyber security incident report hinges on compliance with relevant regulations and standards. In the United States, organizations must adhere to frameworks such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare data or the General Data Protection Regulation (GDPR) for personal data protection. Ensuring that the report is completed accurately and submitted in a timely manner is crucial for legal protection and can help mitigate potential liabilities. Using a digital tool that maintains compliance with the ESIGN Act and UETA can further enhance the report's legal standing.
Key Elements of the Cyber Security Incident Reporting
A comprehensive cyber security incident report should include several key elements to ensure it serves its purpose effectively. Essential components include a detailed description of the incident, the timeline of events, the impact on the organization, and any data compromised. Additionally, the report should outline the response actions taken, including any remediation steps and follow-up measures. Including a section on lessons learned and recommendations for future prevention can also be beneficial for organizational learning and improvement.
How to Use the Cyber Security Incident Reporting
Using a cyber security incident report effectively involves understanding its purpose and the context in which it is utilized. Organizations typically use these reports to analyze incidents, improve security protocols, and comply with regulatory requirements. The report can be shared with internal stakeholders, such as management and IT teams, as well as external parties, including legal counsel and regulatory bodies, if necessary. Properly utilizing the report can help organizations identify vulnerabilities and enhance their overall security posture.
Examples of Using the Cyber Security Incident Reporting
Examples of cyber security incident reporting can vary widely depending on the nature of the incident. For instance, a company may document a phishing attack that compromised employee credentials, detailing how the attack occurred, the response initiated, and the outcome. Another example could involve a data breach where customer information was accessed, requiring a detailed account of the breach, notifications sent to affected individuals, and steps taken to prevent future incidents. These examples illustrate the importance of thorough documentation in understanding and addressing security incidents.
Quick guide on how to complete cyber security incident reporting
Complete Cyber Security Incident Reporting effortlessly on any device
Online document management has gained traction among businesses and individuals. It offers an ideal eco-friendly substitute for conventional printed and signed papers, allowing you to find the correct form and safely store it online. airSlate SignNow provides you with all the tools necessary to create, modify, and eSign your documents swiftly without delays. Handle Cyber Security Incident Reporting on any platform using airSlate SignNow Android or iOS applications and enhance any document-centric operation today.
The easiest way to modify and eSign Cyber Security Incident Reporting without hassle
- Locate Cyber Security Incident Reporting and click Get Form to begin.
- Utilize the tools we offer to fill out your form.
- Mark pertinent sections of the documents or obscure sensitive information with tools specifically provided by airSlate SignNow for that purpose.
- Create your signature using the Sign tool, which takes mere seconds and carries the same legal validity as a conventional wet ink signature.
- Review the details and click the Done button to save your modifications.
- Choose how you want to send your form, via email, text message (SMS), invite link, or download it to your computer.
Forget about lost or misplaced documents, tedious form searching, or mistakes that necessitate printing new document copies. airSlate SignNow addresses all your document management needs in just a few clicks from any device of your choice. Modify and eSign Cyber Security Incident Reporting and ensure excellent communication at every step of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the cyber security incident reporting
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a cyber security incident report?
A cyber security incident report is a formal document that outlines the details of a security bsignNow or cyber attack, including the nature of the incident, the data affected, and the response actions taken. It is crucial for understanding vulnerabilities and improving security measures. Utilizing airSlate SignNow to eSign such reports streamlines documentation and ensures compliance.
-
How does airSlate SignNow support creating cyber security incident reports?
airSlate SignNow streamlines the process of creating cyber security incident reports by providing a user-friendly platform for document creation, editing, and eSigning. This enables teams to quickly collaborate on reports and ensure that all parties have access to the most up-to-date information. The ease of use enhances the speed and efficiency of incident reporting.
-
What are the pricing options for airSlate SignNow?
airSlate SignNow offers flexible pricing plans to accommodate businesses of all sizes looking to enhance their cyber security incident reporting process. Users can choose from monthly or annual subscriptions, with various tiers that provide different features and levels of support. This cost-effective solution aims to meet your document management and security needs.
-
Can I integrate airSlate SignNow with other tools for cyber security incident reporting?
Yes, airSlate SignNow offers integrations with popular tools like Google Drive, Microsoft Office, and various CRM systems, enhancing your workflow for cyber security incident reports. These integrations help centralize document management and improve collaboration among teams. Efficiently connecting your tools ensures that you have all the necessary resources for effective incident response.
-
What are the benefits of using airSlate SignNow for incident reports?
Using airSlate SignNow for cyber security incident reports offers several benefits, including enhanced document security, improved collaboration, and quick turnaround for eSigning. Its cloud-based platform ensures that your reports are easily accessible while maintaining the highest security standards. This reliability helps businesses respond swiftly and effectively to cyber incidents.
-
Is airSlate SignNow compliant with data protection regulations?
Absolutely! airSlate SignNow is designed to comply with various data protection regulations, ensuring that your cyber security incident reports meet necessary legal standards. The platform utilizes encryption and other security measures to protect sensitive data. This compliance helps businesses maintain trust and accountability during incident management.
-
How secure is airSlate SignNow when handling sensitive information in incident reports?
airSlate SignNow prioritizes security, employing advanced encryption protocols and strict access controls to safeguard information in cyber security incident reports. The platform is regularly audited to ensure that it meets the highest security standards. This level of security allows organizations to confidently manage and share sensitive incident data.
Get more for Cyber Security Incident Reporting
- Application for registration of radiation generating equipment form
- Kontrollplan form
- Board of optometry livescan form
- Sf 424 ms word form
- Grammar test for beginners form
- Notice to end tenancy for unpaid rent or utilities form rtb 30
- Yukon nominee program bnpsection 1 applicationb form
- Fillable online burnaby electrical contractor form
Find out other Cyber Security Incident Reporting
- eSignature Missouri Banking IOU Simple
- eSignature Banking PDF New Hampshire Secure
- How Do I eSignature Alabama Car Dealer Quitclaim Deed
- eSignature Delaware Business Operations Forbearance Agreement Fast
- How To eSignature Ohio Banking Business Plan Template
- eSignature Georgia Business Operations Limited Power Of Attorney Online
- Help Me With eSignature South Carolina Banking Job Offer
- eSignature Tennessee Banking Affidavit Of Heirship Online
- eSignature Florida Car Dealer Business Plan Template Myself
- Can I eSignature Vermont Banking Rental Application
- eSignature West Virginia Banking Limited Power Of Attorney Fast
- eSignature West Virginia Banking Limited Power Of Attorney Easy
- Can I eSignature Wisconsin Banking Limited Power Of Attorney
- eSignature Kansas Business Operations Promissory Note Template Now
- eSignature Kansas Car Dealer Contract Now
- eSignature Iowa Car Dealer Limited Power Of Attorney Easy
- How Do I eSignature Iowa Car Dealer Limited Power Of Attorney
- eSignature Maine Business Operations Living Will Online
- eSignature Louisiana Car Dealer Profit And Loss Statement Easy
- How To eSignature Maryland Business Operations Business Letter Template