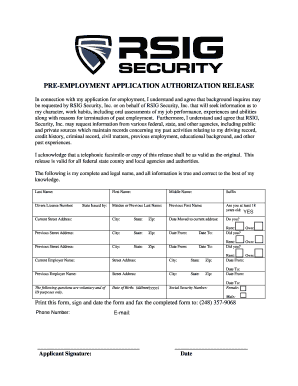
Rsig Security Application Form


What is the Rsig Security Application
The Rsig Security Application is a formal document used to assess and manage security risks within an organization. This application is essential for businesses that prioritize the protection of sensitive information and compliance with regulatory standards. By completing this form, organizations can identify potential vulnerabilities and outline the necessary measures to mitigate risks effectively. The application typically includes sections for detailing security policies, procedures, and the roles of personnel responsible for maintaining security protocols.
How to use the Rsig Security Application
Using the Rsig Security Application involves several key steps. First, gather all necessary information regarding your organization's current security measures and policies. Next, fill out the application accurately, ensuring that all sections are completed with relevant details. It is important to involve key stakeholders in the process to provide insights and validate the information. Once completed, submit the application to the designated authority within your organization for review and approval. Regular updates to the application may be necessary to reflect changes in security practices or regulations.
Steps to complete the Rsig Security Application
Completing the Rsig Security Application can be streamlined by following these steps:
- Gather Information: Collect data on existing security measures, policies, and any previous assessments.
- Fill Out the Application: Carefully complete each section of the application, providing detailed and accurate information.
- Review with Stakeholders: Collaborate with relevant team members to ensure all information is correct and comprehensive.
- Submit for Approval: Present the completed application to the appropriate authority for review and approval.
- Maintain and Update: Regularly revisit the application to incorporate any changes in security practices or compliance requirements.
Legal use of the Rsig Security Application
The legal use of the Rsig Security Application is grounded in compliance with various regulations and standards that govern data protection and security practices. Organizations must ensure that the information provided in the application adheres to legal requirements, such as those outlined by the Federal Information Security Management Act (FISMA) or the General Data Protection Regulation (GDPR) when applicable. Properly completing the application not only helps in mitigating security risks but also demonstrates due diligence in protecting sensitive information, which can be crucial in legal contexts.
Eligibility Criteria
Eligibility to use the Rsig Security Application typically depends on the nature of the organization and its operations. Generally, any business or entity that handles sensitive information or is subject to regulatory compliance can apply. This includes, but is not limited to, corporations, non-profits, and government agencies. It is essential for applicants to have a clear understanding of their security needs and the specific requirements outlined in the application to ensure they meet the necessary criteria.
Required Documents
To successfully complete the Rsig Security Application, several documents may be required. These can include:
- Current Security Policies: Documentation of existing security protocols and measures.
- Risk Assessment Reports: Previous assessments that identify vulnerabilities and risks.
- Compliance Certifications: Evidence of compliance with relevant regulations and standards.
- Incident Reports: Documentation of any past security incidents and responses.
Application Process & Approval Time
The application process for the Rsig Security Application typically involves several stages. After submission, the application is reviewed by designated personnel, who may request additional information or clarification. The approval time can vary based on the complexity of the application and the organization's internal review processes. Generally, organizations should allow several weeks for the review and approval phase, particularly if there are multiple stakeholders involved. Keeping open lines of communication during this process can facilitate a smoother approval experience.
Quick guide on how to complete rsig security application
Complete Rsig Security Application effortlessly on any gadget
Digital document management has gained traction among businesses and individuals alike. It offers an ideal eco-friendly substitute for conventional printed and signed documents, allowing you to locate the necessary form and securely store it online. airSlate SignNow provides all the tools you require to create, modify, and eSign your documents quickly without any holdups. Manage Rsig Security Application on any gadget using airSlate SignNow Android or iOS applications and enhance any document-oriented process today.
The simplest method to alter and eSign Rsig Security Application with ease
- Locate Rsig Security Application and then click Get Form to initiate.
- Employ the tools we offer to complete your form.
- Emphasize pertinent sections of the documents or redact sensitive details using tools provided by airSlate SignNow specifically for this purpose.
- Create your eSignature with the Sign tool, which takes mere seconds and carries the same legal validity as a traditional wet ink signature.
- Review the information and then click the Done button to save your modifications.
- Choose your preferred method to send your form, whether by email, text message (SMS), invitation link, or download it to your computer.
Eliminate the worry of lost or misplaced documents, tedious form navigation, or errors that require printing new copies. airSlate SignNow meets all your document management needs in just a few clicks from any device you prefer. Modify and eSign Rsig Security Application and ensure effective communication at every stage of the form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the rsig security application
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is the rsig security application and how does it work?
The rsig security application is a robust solution designed to enhance the security of electronic signatures. It works by providing advanced encryption and authentication methods to ensure that documents are signed securely and that the identity of signers is verified. This level of security helps boost confidence in the validity of electronic transactions.
-
How does the rsig security application ensure data protection?
The rsig security application employs state-of-the-art encryption protocols to protect sensitive information during transmission and storage. It incorporates multi-factor authentication methods to further safeguard against unauthorized access. With these features, users can trust that their document security is a top priority.
-
What are the key features of the rsig security application?
Key features of the rsig security application include end-to-end encryption, automated audit trails, and secure cloud storage. Additionally, it offers user-friendly interfaces for document management and allows for seamless integrations with other software tools. These features collectively enhance the security and usability of electronic signatures.
-
Is the rsig security application suitable for businesses of all sizes?
Yes, the rsig security application is designed to cater to businesses of all sizes, from startups to large enterprises. Its scalable features allow it to grow with your business needs, maintaining high standards of security regardless of your team's size or document volume. This flexibility makes it an ideal choice for various business environments.
-
What pricing options are available for the rsig security application?
The rsig security application offers several pricing tiers to accommodate different budgets and requirements. Each plan includes essential features such as secure e-signature capabilities and comprehensive support options. To find the right fit, potential users can explore the pricing page or contact sales for personalized assistance.
-
Can the rsig security application integrate with other tools?
Absolutely! The rsig security application integrates seamlessly with popular business applications and systems. This capability enhances productivity by allowing users to manage documents and workflows across multiple platforms without compromising on security or functionality.
-
What are the benefits of using the rsig security application for document signing?
Using the rsig security application for document signing provides numerous benefits, including enhanced security, improved compliance, and increased efficiency. Businesses can reduce turnaround times while ensuring that all signed documents are legally compliant. This ensures a smoother signing process without sacrificing security.
Get more for Rsig Security Application
- Flood zone statement and authorization texas form
- Name affidavit of buyer texas form
- Name affidavit of seller texas form
- Non foreign affidavit under irc 1445 texas form
- Owners or sellers affidavit of no liens texas form
- Texas affidavit financial form
- Complex will with credit shelter marital trust for large estates texas form
- Texas married form
Find out other Rsig Security Application
- Can I Electronic signature Maryland High Tech RFP
- Electronic signature Vermont Insurance Arbitration Agreement Safe
- Electronic signature Massachusetts High Tech Quitclaim Deed Fast
- Electronic signature Vermont Insurance Limited Power Of Attorney Easy
- Electronic signature Washington Insurance Last Will And Testament Later
- Electronic signature Washington Insurance Last Will And Testament Secure
- Electronic signature Wyoming Insurance LLC Operating Agreement Computer
- How To Electronic signature Missouri High Tech Lease Termination Letter
- Electronic signature Montana High Tech Warranty Deed Mobile
- Electronic signature Florida Lawers Cease And Desist Letter Fast
- Electronic signature Lawers Form Idaho Fast
- Electronic signature Georgia Lawers Rental Lease Agreement Online
- How Do I Electronic signature Indiana Lawers Quitclaim Deed
- How To Electronic signature Maryland Lawers Month To Month Lease
- Electronic signature North Carolina High Tech IOU Fast
- How Do I Electronic signature Michigan Lawers Warranty Deed
- Help Me With Electronic signature Minnesota Lawers Moving Checklist
- Can I Electronic signature Michigan Lawers Last Will And Testament
- Electronic signature Minnesota Lawers Lease Termination Letter Free
- Electronic signature Michigan Lawers Stock Certificate Mobile