Firewall Change Request Form


What is the firewall change request?
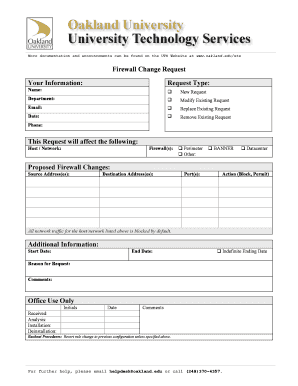
The firewall change request is a formal document used to propose modifications to an organization's firewall settings. This request ensures that any changes are documented, reviewed, and approved by the appropriate personnel before implementation. The purpose of the firewall change request is to maintain security protocols while allowing necessary adjustments to be made for operational efficiency. It typically includes details such as the reason for the change, the specific configurations to be altered, and the potential impact on network security.
Steps to complete the firewall change request
Completing a firewall change request involves several key steps to ensure clarity and compliance. First, clearly define the purpose of the change, including the specific firewall rules or settings that need modification. Next, gather all relevant information, such as the potential risks associated with the change and the expected outcomes. After that, fill out the firewall change request form, ensuring all fields are accurately completed. Finally, submit the form to the designated authority for review and approval, and keep a copy for your records.
Legal use of the firewall change request
To ensure the legal validity of a firewall change request, it must adhere to specific regulations and standards. In the United States, compliance with laws such as the Electronic Signatures in Global and National Commerce Act (ESIGN) and the Uniform Electronic Transactions Act (UETA) is essential. These laws establish that electronic signatures and documents are legally binding if certain criteria are met. Using a secure electronic signature platform can help ensure that the request is legally recognized and protected against unauthorized changes.
Key elements of the firewall change request
A well-structured firewall change request includes several critical elements. These typically consist of the requester's information, a detailed description of the proposed changes, the rationale behind the request, and an assessment of potential risks. Additionally, it should outline the expected timeline for implementation and any necessary testing procedures. Including an approval section, where designated personnel can sign off on the request, is also important to formalize the process.
Examples of using the firewall change request
Examples of scenarios where a firewall change request may be necessary include updating firewall rules to allow new applications, modifying access permissions for specific user groups, or implementing new security protocols in response to emerging threats. Each of these situations requires careful consideration and documentation to ensure that changes do not compromise network security. By using a structured firewall change request form, organizations can systematically address these needs while maintaining compliance with security policies.
Form submission methods
Submitting a firewall change request can be done through various methods, depending on the organization's policies. Common submission methods include online forms, which can streamline the process and ensure quicker approvals, and traditional methods such as mail or in-person delivery. Each method has its advantages; online submissions often allow for easier tracking and management, while physical submissions may be preferred in environments with strict security protocols. Understanding the preferred method within your organization can facilitate a smoother request process.
Quick guide on how to complete firewall change request
Effortlessly prepare Firewall Change Request on any device
Digital document management has become increasingly favored by businesses and individuals alike. It offers an excellent environmentally friendly substitute for traditional printed and signed paperwork, as you can easily find the appropriate form and securely store it online. airSlate SignNow provides you with all the tools you need to create, modify, and electronically sign your documents quickly without delays. Manage Firewall Change Request on any device with the airSlate SignNow applications for Android or iOS and enhance any document-related process today.
How to modify and electronically sign Firewall Change Request effortlessly
- Find Firewall Change Request and click Get Form to initiate the process.
- Utilize the tools we provide to complete your form.
- Emphasize important sections of your documents or redact sensitive information with tools specifically designed by airSlate SignNow for that purpose.
- Generate your signature using the Sign feature, which takes only seconds and carries the same legal validity as a traditional handwritten signature.
- Review all the details and then click the Done button to save your modifications.
- Choose your method of delivery for the form, whether by email, text message (SMS), or invitation link, or download it to your computer.
Eliminate the hassle of lost or misplaced documents, searching for forms, or errors that necessitate printing new copies. airSlate SignNow meets your document management needs in just a few clicks from any device you prefer. Modify and electronically sign Firewall Change Request to ensure outstanding communication throughout the document preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the firewall change request
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a firewall request form and why is it important?
A firewall request form is a critical document that outlines the necessary permissions and configurations required to access specific applications through a firewall. It ensures that security protocols are upheld while allowing necessary communication. Submitting a firewall request form properly helps maintain corporate data integrity and security.
-
How can airSlate SignNow streamline the firewall request form process?
airSlate SignNow simplifies the firewall request form process by providing an easy-to-use platform for eSigning and document management. Users can quickly create, send, and track their firewall request forms, ensuring that all signatures are collected efficiently. This reduces delays and speeds up the approval process.
-
What are the pricing options for using airSlate SignNow for firewall request forms?
airSlate SignNow offers a range of pricing plans tailored to meet different business needs, including options for individuals and teams. Each plan provides full access to eSigning features, including the handling of firewall request forms. Pricing is competitive, making it an affordable solution for organizations of all sizes.
-
Are there any integrations available for airSlate SignNow related to firewall request forms?
Yes, airSlate SignNow integrates with various applications, allowing users to streamline their workflow for firewall request forms. Integrations with platforms like Salesforce, Google Workspace, and others enable seamless data transfer and document management, enhancing efficiency. This connectivity helps users manage their firewall request forms more effectively within their existing applications.
-
What are the key features of airSlate SignNow for managing firewall request forms?
Key features of airSlate SignNow for managing firewall request forms include customizable templates, secure cloud storage, and team collaboration tools. Users can create specific templates tailored to their firewall requests, ensuring consistency. Additionally, real-time tracking allows managers to monitor the status of each request form easily.
-
Is airSlate SignNow compliant with data protection regulations for firewall request forms?
Yes, airSlate SignNow is committed to data protection and complies with various regulations, including GDPR and HIPAA. This ensures that all your firewall request forms are handled with the highest level of security and privacy. Businesses can confidently manage sensitive information knowing their data is protected.
-
How does airSlate SignNow handle the security of firewall request forms?
airSlate SignNow employs advanced security measures including encryption and secure cloud storage to safeguard firewall request forms. All documents are protected during transmission and at rest, ensuring that only authorized users can access critical data. This focus on security helps prevent unauthorized access and data bsignNowes.
Get more for Firewall Change Request
- Taking a lump sum from a plan already in drawdown form
- Ventura county coroner release form isoc
- Individual indian monies iim us department of the interior doi form
- Alon financial services form
- Homeschool transcript form xavier
- How to fill late registration of birth application form
- 1310 affidavit new york form
- Salvage dealer licensedsd 10a 0325applicat form
Find out other Firewall Change Request
- Electronic signature Wisconsin Business Operations LLC Operating Agreement Myself
- Electronic signature Colorado Doctors Emergency Contact Form Secure
- How Do I Electronic signature Georgia Doctors Purchase Order Template
- Electronic signature Doctors PDF Louisiana Now
- How To Electronic signature Massachusetts Doctors Quitclaim Deed
- Electronic signature Minnesota Doctors Last Will And Testament Later
- How To Electronic signature Michigan Doctors LLC Operating Agreement
- How Do I Electronic signature Oregon Construction Business Plan Template
- How Do I Electronic signature Oregon Construction Living Will
- How Can I Electronic signature Oregon Construction LLC Operating Agreement
- How To Electronic signature Oregon Construction Limited Power Of Attorney
- Electronic signature Montana Doctors Last Will And Testament Safe
- Electronic signature New York Doctors Permission Slip Free
- Electronic signature South Dakota Construction Quitclaim Deed Easy
- Electronic signature Texas Construction Claim Safe
- Electronic signature Texas Construction Promissory Note Template Online
- How To Electronic signature Oregon Doctors Stock Certificate
- How To Electronic signature Pennsylvania Doctors Quitclaim Deed
- Electronic signature Utah Construction LLC Operating Agreement Computer
- Electronic signature Doctors Word South Dakota Safe