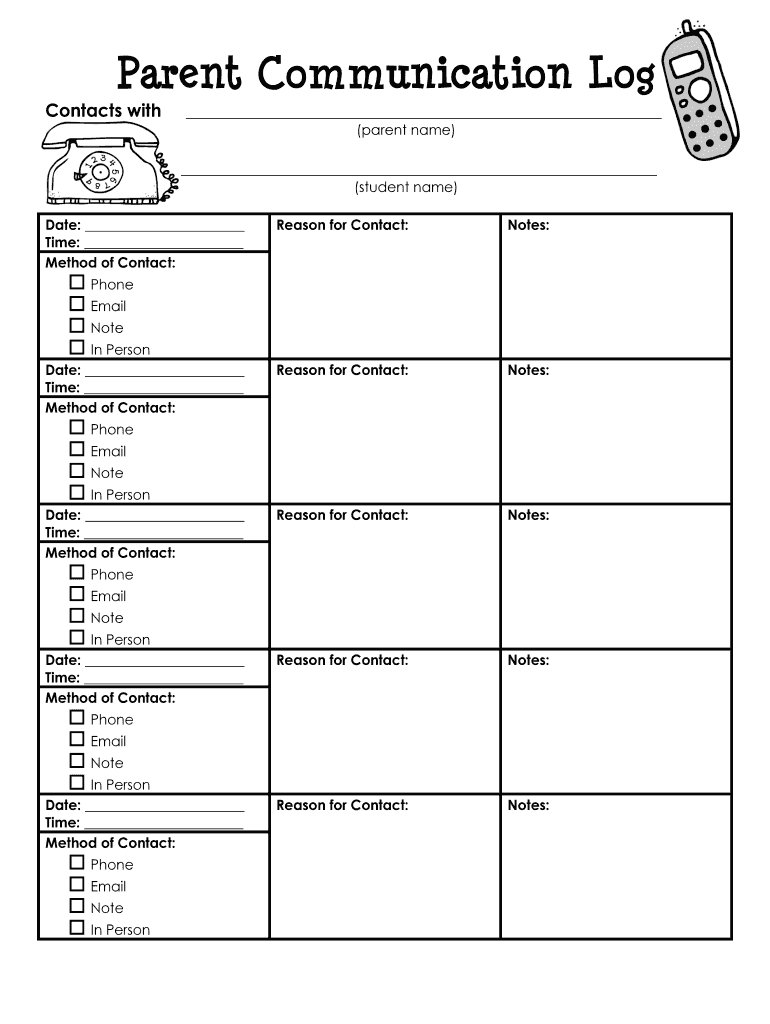
Example of a Permission Form


Understanding the Permission Document Template
A permission document template serves as a formalized way to grant consent for specific actions, such as sharing information or allowing access to certain resources. This template is particularly useful in various contexts, such as educational settings, healthcare, and business transactions. By utilizing a permission document template, individuals can ensure that their consent is documented clearly and legally, minimizing misunderstandings and protecting their rights.
Key Elements of the Permission Document Template
When creating a permission document template, certain key elements must be included to ensure its effectiveness and legality. These elements typically consist of:
- Title: Clearly state that the document is a permission form.
- Parties Involved: Identify the individuals or entities granting and receiving permission.
- Purpose: Specify the reason for the permission being granted.
- Duration: Indicate how long the permission is valid.
- Signatures: Provide space for signatures of all parties involved, along with dates.
Including these elements ensures that the permission document template is comprehensive and legally binding.
Steps to Complete the Permission Document Template
Filling out a permission document template involves several straightforward steps. Begin by gathering all necessary information about the parties involved and the purpose of the permission. Follow these steps to complete the template:
- Fill in the title: Clearly label the document as a permission form.
- Identify the parties: List the names and contact information of those granting and receiving permission.
- State the purpose: Clearly articulate what permission is being granted and for what reason.
- Specify the duration: Indicate how long the permission remains valid.
- Sign and date: Ensure all parties sign the document and include the date of signing.
By following these steps, individuals can create a thorough and effective permission document.
Legal Use of the Permission Document Template
The legal validity of a permission document template hinges on several factors. To ensure that the document is legally binding, it must comply with relevant laws and regulations. In the United States, electronic signatures are recognized under the ESIGN Act and UETA, which provide the framework for the legality of eSignatures. Additionally, the document should:
- Be clear and unambiguous in its terms.
- Include all necessary signatures from the involved parties.
- Be stored securely to maintain its integrity.
By adhering to these legal standards, individuals can confidently use a permission document template in various situations.
Examples of Using the Permission Document Template
Permission document templates can be utilized in numerous scenarios. Some common examples include:
- Educational settings: Parents granting permission for their children to participate in school activities.
- Healthcare: Patients authorizing medical professionals to share their health information.
- Business transactions: Companies allowing third parties to access proprietary information for specific purposes.
These examples illustrate the versatility of permission document templates across different fields and contexts.
How to Obtain the Permission Document Template
Obtaining a permission document template can be done through various means. Many organizations provide customizable templates that can be downloaded or filled out online. Additionally, individuals can create their own templates based on specific needs. Here are some ways to obtain a permission document template:
- Visit reputable websites that offer free or paid templates.
- Consult with legal professionals who may provide tailored templates.
- Create a custom template using word processing software, ensuring all key elements are included.
By exploring these options, individuals can easily find or create a permission document template that meets their requirements.
Quick guide on how to complete example of a permission form
Effortlessly prepare Example Of A Permission Form on any device
Managing documents online has gained immense popularity among organizations and individuals alike. It serves as an ideal eco-friendly alternative to conventional printed and signed documents, allowing you to locate the appropriate form and securely store it online. airSlate SignNow equips you with all the necessary tools to create, edit, and electronically sign your documents swiftly and without delays. Manage Example Of A Permission Form on any device using airSlate SignNow Android or iOS applications and enhance any document-based process today.
The easiest way to modify and electronically sign Example Of A Permission Form with ease
- Find Example Of A Permission Form and click on Get Form to begin.
- Utilize the tools we offer to finalize your document.
- Emphasize pertinent sections of your documents or redact sensitive information using tools that airSlate SignNow provides specifically for that purpose.
- Generate your signature with the Sign feature, which takes mere seconds and holds the same legal validity as a traditional wet ink signature.
- Review all the information and click on the Done button to save your changes.
- Choose how you wish to send your form, whether by email, SMS, invitation link, or download it to your computer.
Eliminate concerns about lost or misplaced files, tedious form searches, or mistakes that necessitate printing new document copies. airSlate SignNow fulfills all your document management requirements in just a few clicks from a device of your preference. Modify and electronically sign Example Of A Permission Form and ensure seamless communication at any stage of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
FAQs
-
How many things can you name (without looking at the link) that are more difficult to purchase in Florida than guns are (and does that situation make any sense to you)?
I can name no items because no other consumer product in the United States requires FBI approval to purchase and take home beforehand.Let me repeat that: Guns are the only consumer product in the USA that requires Federal government permission to be obtained prior to taking possession of it.The article conflates lack of licensing and registration with age limits and showing ID, both of which apply to guns as well as cold medicine. I don’t recall going into any pharmacy in the USA and having to fill out a Federal drug background check form checking to see if I’ve been convicted of possession before buying Sudafed.The linked article is a classic example of the exemplary fact-checking and integrity that passes for journalism these days.
-
What are the prerequisites for a Catholic marriage?
I'm getting married in August and I did not realize the process was so arduous.I was raised Catholic but have not practiced for about a decade. I wanted to have a Catholic wedding because my parents are Catholic and I think they'd appreciate it.I live in San Francisco and the wedding is in Cleveland. We contacted a priest in Cleveland to preside over the ceremony, and he mentioned that we needed to get permission from our church in San Francisco. Here's the checklist the church in San Francisco sent our way [1], and my interpretation of what we need to do to have a wedding recognized by the Catholic church.1) We need my "home church", in the Archdiocese of San Francisco, to give me permission to get married in the Archdiocese of Cleveland. To grant me that permission, the Archdiocese of San Francisco requires:Baptismal recordsFreedom to Marry (Form A)Witness to the Freedom to Marry (Form B)In the presence of a priest or deacon, I have to reaffirm my faith in Jesus Christ and promises to live that faith in the Catholic Church and do all in my power to raise the children Catholic.I need to attend an Engaged Encounter Weekend, Saturday For the Engaged or a parish marriage preparation program (this appears to be their approach to the Pre-Cana [2] course). Note that the Saturday encounter will cost us $200.Additionally, because my fiancé is not Catholic, they also require:A dispensation from the Archbishop in San Francisco to marry a non-baptized person (Disparity of Cult)Specific to the Archdiocese of San Francisco, I believe, is an exam and counseling session devoted to communication for the couples:FOCCUS premarital inventoryFOCCUS(c) follow-up session2) At the rehearsal:Marriage license3) At the wedding:Wedding rings[1] http://www.oldsaintmarys.org/htm...[2] http://en.wikipedia.org/wiki/Pre...
-
How do I fill out my FAFSA?
The FAFSA isn't as scary as it seems, but it's helpful to have the documents you'll need handy before you fill it out. It's available starting January 1 of the year you'll attend school, and it's best to complete it as early as possible so you get the most aid you'll qualify for. Be especially mindful of school and state deadlines that are earlier than the federal deadline of June 2017. Check out NerdWallet's 5 Hacks to Save Time on Your 2016 FAFSA. These are the basic steps: Gather the documents you'll need to complete the form by following this checklist.Log in to the FAFSA with your Federal Student Aid ID. You'll need an FSA ID to sign and submit the form electronically, and your parent will need one too if you're a dependent student. Create one here. Follow the prompts to fill out the FAFSA. This guide will help you fill it out according to your family situation. You'll be able to save time by importing income information from the IRS starting Feb. 7, 2016. Many families don't file their 2015 income taxes until closer to the deadline of April 18. But it's a good idea to fill out your FAFSA earlier than that. Use your parents' 2014 tax information to estimate their income, then go back in and update your FAFSA using the IRS Data Retrieval Tool once they've filed their taxes. More info here: Filling Out the FAFSA.
-
What is taught in Made Easy and IES Master Delhi that it gives maximum topper and other institutes in other cities can't give toppers or IES?
Hi! This is a very interesting question. Thanks for requesting.Now, just so that you can understand my point of view, a little about myself. I graduated from NIT Mizoram and then joined Made Easy Delhi center, I have taken several courses from them, general Classroom Course for both GATE and ESE , GS Course for ESE, ESE Mains Course. I have taken test series from both Ace Academy and Made Easy for both GATE and ESE. In addition to this, I practiced from GS workbooks of IES master and also studied their GS material.Also, as I don't know the quality of education being provided in other coachings, so, I cannot comment on that. But I have heard good words from my friends about some coaching institutes like Kreatryx, GATE Academy, GATEforum.Here I list the reasons that I believe are responsible for these coachings in producing (or claims at producing) most number of toppers -Competent faculties. Made Easy has some of the best faculties in the field. These include, IITians, ESE toppers, GATE toppers etc. Their credentials help them put up a good name for themselves in the coaching business.More outsignNow. Made Easy has a bigger presence in the country as it has several branches spread out in important cities, while other coaching institutes are confined to an area. The location of these branches are also important, as being near to a college gets them those students. So, naturally more number of students enroll for their courses.Seniors’ advice. Most students join a coaching not because they think it is good, but because their seniors have joined it. Now, Made Easy has been in this business from early 2000s. So, that pratha (tradition) continues.Test Series. The test series of Made Easy is very reputable. So naturally, all students join it. It doesn’t matter from where you are preparing or which coaching you have joined, but almost all students join its test series.Propaganda. This is the most important part. Not all toppers have actually studied at a certain coaching. They join certain courses, like test series or interview guidance program, and now when they get a good rank, the coaching institute claims him to be their student. Haven’t you ever noticed more than one coaching claiming a topper to be their student? One should check very carefully what course that student have taken from them.Now, I would also like to share my thoughts about coaching institutes so that future aspirants can take a well informed decision:Coaching is only necessary for a student with poor basics. We make a big mistake in college, we don’t focus on developing basics and just keep on studying courses over courses. So, if you are in college and have some time, then focus on basics and then practice from previous year papers and test series, then you won’t need coaching.I joined Made Easy classroom course in 2016, but in GATE 2017, I did not get a good rank. In 2017, I decided to do self study for ESE+GATE and got AIR 34 in ESE and AIR 1114 in GATE. So, it’s not true that after joining a coaching you will be able to clear an exam. It’s your work that matters more.It’s not like Made Easy provides some extraordinary quality teaching that every student who joins it becomes some brilliant engineer and now he/she can clear any exam. No! Thousands of people join it, only a few finally get jobs. My friend Aishwary Anand Singh very rightly said in one of his posts that, a coaching institute simply turns a below average student into an average student and that’s it. The rest of the work is to be done by the student as self study. This is where the magic happens.When you go for an IIT interview and mention that you have studied from some coaching, their attitude towards you will change entirely and not in a good way. This is because they expect you to have learned engineering in your college and not in a coaching. (P.S.- This was my friend’s experience and not mine!)Always remember, “Aapko job self study se milegi, na ki kisi Coaching join karne se” (You will get a job by self study, and not by joining any coaching!).Thanks for reading!!
-
How do I get permission to use a copyrighted work?
By contacting the copyright owner and getting permission.There are, of course, potential obstacles to doing this. For example, it may not be clear who controls copyrights. The author of a book published in, say, 1970 may be dead and his works in the hands of an estate which can be difficult to find. Once you do find whoever the owner is, they may not be interested in dealing with you. If I, a regular guy off the street, want to write and publish a Star Trek novel, it’s not hard to find addresses for Paramount’s legal department and if I bothered to go looking I might even find contact information for their licensing division, but if Paramount doesn’t see any profit in dealing with me, they may send me a curt refusal or simply ignore me altogether. And, of course, whoever grants permission may want to be paid for that permission, and I may not be able to afford those costs.So, then, there are reasonably well-worn legal channels for negotiating with an IP owner and getting permission to use material under copyright, but it requires the IP owner to agree, and the IP owner is under no obligation to grant that permission or even to seriously consider your proposal. So while it’s possible to get such permission, there’s no guaranteed way to get it.
-
How can I fill out Google's intern host matching form to optimize my chances of receiving a match?
I was selected for a summer internship 2016.I tried to be very open while filling the preference form: I choose many products as my favorite products and I said I'm open about the team I want to join.I even was very open in the location and start date to get host matching interviews (I negotiated the start date in the interview until both me and my host were happy.) You could ask your recruiter to review your form (there are very cool and could help you a lot since they have a bigger experience).Do a search on the potential team.Before the interviews, try to find smart question that you are going to ask for the potential host (do a search on the team to find nice and deep questions to impress your host). Prepare well your resume.You are very likely not going to get algorithm/data structure questions like in the first round. It's going to be just some friendly chat if you are lucky. If your potential team is working on something like machine learning, expect that they are going to ask you questions about machine learning, courses related to machine learning you have and relevant experience (projects, internship). Of course you have to study that before the interview. Take as long time as you need if you feel rusty. It takes some time to get ready for the host matching (it's less than the technical interview) but it's worth it of course.
-
What are some good examples of psychological principles applied to websites, social media and internet technologies?
1. Gestalt PsychologyGestalt psychology or gestaltism (German: Gestalt – “essence or shape of an entity’s complete form”) of the Berlin School is a theory of mind and brain positing that the operational principle of the brain is holistic, parallel, and analog, with self-organizing tendencies. The Gestalt effect is the form-generating capability of our senses, particularly with respect to the visual recognition of figures and whole forms instead of just a collection of simple lines and curves. In psychology, gestaltism is often opposed to structuralism and Wundt. The phrase “The whole is greater than the sum of the parts” is often used when explaining Gestalt theory.The Gestalt Six RulesAs said, the Gestalt Principles are a way to organize visual perception. Gestaltists have found how different elements in a field re-organize themselves in a solidarity system by following certain rules.Here following the list of the six rules they have found:ProximityThe distance plays a key-role in determining the elements perception. Things that are close among them are perceived to be more related than things that are scattered apart. The concept underlying the concept of proximity is the group.SimilarityThere is a natural tendency in put in relation similar elements more than dissimilar ones. They can be, for example, similar for shape, color or dimension.Perceiving similarities not only helps us to assume what elements are related to one another, it also implies a structure based on an emerging pattern. Those kinds of objects which share some characteristics create cohesion in the design because our brains automatically search for patterns. Humans like symmetry but obviously also like breaking rules so also its contrary is inspiring.ClosureLooking at a complex arrangement of individual elements, humans tend to first look for a single shape obtained from recognizable outlines. Closed shapes can be obtained by real lines, color or contrast or even lack of them. Closure Law occurs when an object is incomplete or a space is not completely enclosed and the brain activates some mechanisms to complete the figure by filling in the missing information.The figure below is called the Necker Cube. What you can see? Can you see a white outlined cube? As a matter of fact the cube is no there, we only have eight black circles with some area missing. The cube is implicit because our mind put in relation these white lines filling in and completing the cube shape.Common FateElements moving in the same direction are perceived as a group more than those which are a steady group because they show more coherence.A collection of distinct objects in a layoutthat seem to move all together toward a common goal, definition, conclusion or direction are generally perceived to be each other related.In the example the dots look like they are moving in the top right direction and they looks more coherent than those simply aligned in equal rows.Law of Prägnanz alias Figure Ground RelationshipHuman brain tends to interpret ambiguous or complex images as simple and complete. In an image the composing elements are perceived as either figures or ground. Background and foreground can be exchanged and in both case they assume a precise meaning.The most famous example of figure/ground image is that of the vase of Rubin.The surrounded object is seen as figure. Shapes are overriding and you can perceive a black vase on a white background or, vice versa, two profiles on a black background.This visual illusion is produced by the tendency of ambiguous perceptual between two or more alternative interpretations. In order to clear the image it needs to balance the figure/ground area.Good ContinuationAll elements are perceived as part of a coherent object so, for example if they are arranged in a line they are considered more related than detached elements. In the image the “line” created from the circles on the left “continues”, vice versa the other is interrupted.Gestalt Principles and Visual IdentitiesHere examples of how these rules and principles have affected more than one corporate identity construction.ProximityAs we said, element which are close are perceived as a shape.We can see, as example here below, the logo Mistery Island created by Gert van Duinen. In an easy and brilliant way the designer use the proximity law to create a shape of an island and its reflection on the sea. This is the perfect combination of the brand name and the customer activity, dance music producer. The lines creating the island are clearly recognizable as equalizer lines.Again in the Foodmobile logo (Designer: ru_ferret) we found a group of single objects, representing foods (bread, fish, vegetables are clearly recognizable) which grouped for proximity create a car shape.SimilarityIn the Capture logo, created by Quadrika, the Similarity Law is clearly applied. The Gestalt Principle of Similarity works well when designing logos because it is based on repetition of shape, size, color, texture, value or orientation.The logo is featured by colors and shape similarity. The visual part of the Capture logo shares with the textual part a kind of viewfinder which is the same of the C and E letters.Prägnanz (Figure-Ground)By following the Figure-Ground Law in the Feathers & Fur logo, designed for a pet store fromLumo, the observer can recognize a parrot and a dog’s face into the mark.SymmetryThe Hatimeria logo, from Midgar is a clear example of symmetry law. The software house here represented wants stress the great attention they put in building long-lasting partnerships with customers. The logo symbols are two hands joined together.The two hands are symmetrical designed to form stairs leading upwards.Symmetry creates a redundancy and predictability of visual information.Another good example can be Antarctic Voice from Austronaut Design where the two symmetric pikes represent both an iceberg and a vice equalizer.Humans like symmetry but obviously also like breaking rules so also its contrary is inspiring and is called anomaly.“Common Fate”In the Melbourne 2010 Cycling Championship logo the spots are affected by a common fate. The lines created by the colors move in the same direction creating a dynamism which let the observer perceive a common fate of movement.ClosureThe closure rule is of very common use in logo creation to create memorable design.An extremely famous logo based on closure is the WWF Panda.The logo IBM too, composed by eight solid lines, separated by empty space,is based on closure law. The three letters are not really there. Our brain perceives it by closing the letters shape.Applying the Gestalt Principle to the Web Design WorkflowBelow are a few web examples and their respective layout silhouettes. The silhouette view is what the brain identifies as the page shape. Trying to change anything other than the main shape will result, more or less, in the same design... and going back to your client with the same design after they've requested changes will make the client feel that nothing has been done....the design will look the same until you've changes the structural gestalt.You’ll be surprised at how many designers make this mistake and wonder why the client still hates a design or feel nothing has been changed or added, even though they've worked tirelessly on improving the individual elements.Alright, let's peek at a few designs and their silhouettes:Usually, sticking to the safe and generally square-like design (as in the 4 bottom layouts from the examples above) will result in an ordinary design, nothing very creative. Try to always experiment with the “containing shell” of your design. Try rotating the box a few degrees or cutting out and changing one of the corners... all of this adds to your design’s uniqueness and creativity.You should always start with the container, or the overall structural shell of a design; Forget the details and individual components for now.When that is done and you and the client are satisfied with the structure, grab your wireframes and start working on the details. You will be surprised at how many times a design ends up as a neatly colored wireframe when you start from the inside out. I’ve seen several designers working on the header and navigation first, then start laying out the components, and before you know it you have a neatly packed and nicely colored page full of content which may be from a usability perspective well placed and correct, however from a design perspective it would never be creative or stand out.Think of your design as a chocolate covered peanut, if you start with the peanut, from the inside out, the outer layer which everyone sees (the chocolate layer) will always depend on the peanut shape and you will have little control on the result.However if you treat your design like a chocolate egg, working on the outer layer first, and shape it as you desire – fitting your inner content to match the shell, then it really doesn’t matter what you fill it with, the design will always be the egg-shape that you intended.Sources: The Gestalt Principle: Design Theory for Web Designers - Tuts+ Web Design ArticleThe Close Relationship Between Gestalt Principles and DesignOther resources:Gestalt Principles: How Are Your Designs Perceived?The designer’s guide to Gestalt Theory2. Principle of ReciprocityThe reciprocity principle is one of the basic laws of social psychology: It says that in many social situations we pay back what we received from others.A simple evolutionist explanation of reciprocity is that in a group of protohumans it paid off to behave nicely and cooperate: those who obeyed this principle were probably less likely to get enemies and thus more likely to survive and pass on their genes. (This explanation is however not universally agreed upon by scientists, as it assumes that people behave consistently over time, that is, it assumes that one act of cooperation predicts further acts of cooperation.)Reciprocity works in a variety of situations; businesses use it in advertising, marketing, and propaganda. For instance, it’s been shown that a free sample encourages people to buy the corresponding product because they feel that they have to return the favor of being given something for free.Reciprocity is a principle that you can also use to your advantage (but also to your users’ advantage) in user-interface design (see our class on credibility and persuasion in web design). The bottom line is simple: give your users something before you ask for anything from them.Giving Information Away for FreeFree content is the digital counterpart of the free samples from the physical world and is an ingrained use of the reciprocity principle on the web. That’s why newsletters, social media content, and articles such as this one are popular with many companies — as proven by our own studies, users appreciate these kinds of sources when they are informative and relevant. Later on, these same users are more likely to reciprocate by doing business with the company.Many websites that offer white papers or other information will ask users to fill in a form before they can get access to the content of interest. The thinking there is that users will first work for the paper (fill in the form) and then they will get rewarded with the content. comScore (below) takes exactly this approach when it asks people to enter their information before downloading a free report.comScore asks users to enter their information before accessing a free report.This may seem like a simple case of quid pro quo. But the problem is that the two steps don’t happen simultaneously. Users are asked for the “quid” right now, in the hope that they will later find some value from the “quo.” This annoys users and makes them likely to abandon the site.The Nielsen Company takes a slightly different approach. When people click on View Full Report, instead of showing a form that asks users to fill in contact information, the site takes them to a brief article about the report. Users can read the article and then they can decide if they want to fill in the information to get the entire report. (Note that we are not affiliated with The Nielsen Company.)The Nielsen Company lets users read an article about a free report. If they want to download the whole document, they need to fill in a contact-information form.This second approach is better. First, it is respectful of users’ time and effort — it allows them to make a more informed decision of whether they want to take the time to fill in the form and load the report. Second, it also takes advantage of the law of reciprocity. Users will appreciate being able to read the summary and will be more likely to fill in the information because they were given something interesting in advance. But even those users who may have decided that the report is not for them will appreciate the honest approach, will form a positive impression of The Nielsen Company, and probably pay back in kind when asked (for instance, by returning to the site for more information). And they may also be more willing to fill in the form in an honest and meaningful way by providing extra information about their request or giving email addresses and contact information that they actually use.(Our studies of B2B website use show that users frequently enter made-up information when they encounter overly aggressive lead-generation forms before the website has established its credibility. Unless you want your sales force to make a lot of calls to Mickey Mouse, it’s a bad idea to ask for user information too soon.)In a study published in 2007, Luciano Gamberini and his colleagues at University of Padova investigated exactly this issue: how likely web users are to fill in contact information to access free content. Gamberini had two conditions in his experiment that mimic the Comcast and Nielsen examples above: in one condition users were asked to first fill in the form and then, as a reward, they got access to a set of guidelines. In the second condition, users got access to the guidelines first, and then they were asked to fill in the form. Users gave out more information in the contact form in the reciprocity condition than in the reward condition. They were, however, more likely to submit the form in the reward condition.So what does that mean? If you decide to force your users to fill in the form before they get the content, you may get more submissions. But if you want to establish meaningful, long-term relationships with your customers, then you’re better off showing at least part of the information upfront, with no request upon users.Permissions and Tutorials on MobileMobile apps and sites would also benefit from using the reciprocity principle. Too often they require users to cross login walls, read complicated instructions, accept the use of the current location, or give permission to receive notifications before these same users have received even the slightest glimpse of the app’s offerings. Starting the initial experience with requests of any kind puts the load onto the user, creates suspicion, and makes the user reluctant to cooperate. It’s much better if, instead, the app focuses on making it easy for the users to get started right away. Once users find value in the app, the will be more likely to trust it and reciprocate by accepting requests of any kind.For instance, often after downloading an app, iOS users will get an alert box prompting them to accept push notifications. Wrong! At this point, the user has no idea whether they like the app, whether they will be using it, or whether the type of content that they will be notified about will be relevant in any way. Asking them to accept push notifications is too much — the users’ first reaction will often be “No” at this stage. The user needs to first establish a relationship with the app, see what it is about, and then she can decide that she can trust it with push notifications.Evernote asks permission for sending push notifications before the user has gotten a chance to use the app.Once users have explored the app, you can ask them if they want to be notified of specific events. (But be as explicit as you can and tell people what they will be notified about; otherwise, you risk annoying and alienating the users with notifications that they don’t need.)Many apps also request permission to use the current location before actually needing it. For instance, there is no reason for Expedia to ask for the current location on their home page, before the user has initiated a search. It’s possible that users need to search in a different location than their own, and asking for this information when it’s unnecessary will diminish their trust in the app. (Particularly in these days of constant privacy scandals, users worry that any snooping question is for nefarious purposes.)Expedia asks for permission to use the current location before the user has initiated a search.Epicurious rightly asks for permissions to use the microphone only when the user taps the Voice Control button. In that context, it is logical for the user to say yes, since it’s clear why the app needs that permission. Should the app have asked for it on the first screen, before the user had gotten a chance to form a mental model of how this app works, it would have looked unnecessary and the app’s request would have been likely rejected.Epicurious only asks for permission to use the microphone when it needs it to enable voice control (that is, immediately after the user has tapped the Voice Control button).Another practice popular with apps is showing a tutorial when they are first launched. We can count on the fingers of one hand the number of users who have actually sat through these initial tutorials after they have just downloaded the app. Even when the tutorial seemed fun (like the comic-reader tutorial which was designed to look like a comic book), users did not have the patience to sit through it. (And if they had sat through it, they would not have remembered all the information that was poured over them.) It’s much better to use a quick tip page if you must instruct your users. But even better: don’t make your users feel like they have to study in order to use your app. Create an interface that is simple and usable and that doesn’t need any instruction. It’s again a simple instantiation of the reciprocity principle: in the user–app relationship, the app should put in most effort, especially in the beginning.Clear, a todo list app, starts with a 7-page tutorial. That’s bad because it requires users to work upfront: they have to patiently read all the information and try to commit it to their memory.ConclusionThe reciprocity principle says that people respond in kind to nice behavior. If you want your users to trust you with their information and come back to you repeatedly, plant the reciprocity seed by being nice to them upfront and minimizing their interaction cost. Ask as little of your users as possible. On the web and elsewhere, start by giving before taking, and people will reciprocate.Source: http://www.nngroup.com/articles/...
-
Do military members have to pay any fee for leave or fiancee forms?
NOOOOOOO. You are talking to a military romance scammer. I received an email from the US Army that directly answers your question that is pasted below please keep reading.I believe you are the victim of a military Romance Scam whereas the person you are talking to is a foreign national posing as an American Soldier claiming to be stationed overseas on a peacekeeping mission. That's the key to the scam they always claim to be on a peacekeeping mission.Part of their scam is saying that they have no access to their money that their mission is highly dangerous.If your boyfriend girlfriend/future husband/wife is asking you to do the following or has exhibited this behavior, it is a most likely a scam:Moves to private messaging site immediately after meeting you on Facebook or SnapChat or Instagram or some dating or social media site. Often times they delete the site you met them on right after they asked you to move to a more private messaging siteProfesses love to you very quickly & seems to quote poems and song lyrics along with using their own sort of broken language, as they profess their love and devotion quickly. They also showed concern for your health and love for your family.Promises marriage as soon as he/she gets to state for leave that they asked you to pay for.They Requests money (wire transfers) and Amazon, iTune ,Verizon, etc gift cards, for medicine, religious practices, and leaves to come home, internet access, complete job assignments, help sick friend, get him out of trouble, or anything that sounds fishy.The military does provide all the soldier needs including food medical Care and transportation for leave. Trust me, I lived it, you are probably being scammed. I am just trying to show you examples that you are most likely being connned.Below is an email response I received after I sent an inquiry to the US government when I discovered I was scammed. I received this wonderful response back with lots of useful links on how to find and report your scammer. And how to learn more about Romance Scams.Right now you can also copy the picture he gave you and do a google image search and you will hopefully see the pictures of the real person he is impersonating. this doesn't always work and take some digging. if you find the real person you can direct message them and alert them that their image is being used for scamming.Good Luck to you and I'm sorry this may be happening to you. please continue reading the government response I received below it's very informative. You have contacted an email that is monitored by the U.S. Army Criminal Investigation Command. Unfortunately, this is a common concern. We assure you there is never any reason to send money to anyone claiming to be a Soldier online. If you have only spoken with this person online, it is likely they are not a U.S. Soldier at all. If this is a suspected imposter social media profile, we urge you to report it to that platform as soon as possible. Please continue reading for more resources and answers to other frequently asked questions: How to report an imposter Facebook profile: Caution-https://www.facebook.com/help/16... < Caution-https://www.facebook.com/help/16... > Answers to frequently asked questions: - Soldiers and their loved ones are not charged money so that the Soldier can go on leave. - Soldiers are not charged money for secure communications or leave. - Soldiers do not need permission to get married. - Soldiers emails are in this format: john.doe.mil@mail.mil < Caution-mailto: john.doe.mil@mail.mil > anything ending in .us or .com is not an official email account. - Soldiers have medical insurance, which pays for their medical costs when treated at civilian health care facilities worldwide – family and friends do not need to pay their medical expenses. - Military aircraft are not used to transport Privately Owned Vehicles. - Army financial offices are not used to help Soldiers buy or sell items of any kind. - Soldiers deployed to Combat Zones do not need to solicit money from the public to feed or house themselves or their troops. - Deployed Soldiers do not find large unclaimed sums of money and need your help to get that money out of the country. Anyone who tells you one of the above-listed conditions/circumstances is true is likely posing as a Soldier and trying to steal money from you. We would urge you to immediately cease all contact with this individual. For more information on avoiding online scams and to report this crime, please see the following sites and articles: This article may help clarify some of the tricks social media scammers try to use to take advantage of people: Caution-https://www.army.mil/article/61432/< Caution-https://www.army.mil/article/61432/> CID advises vigilance against 'romance scams,' scammers impersonating Soldiers Caution-https://www.army.mil/article/180749 < Caution-https://www.army.mil/article/180749 > FBI Internet Crime Complaint Center: Caution-http://www.ic3.gov/default.aspx< Caution-http://www.ic3.gov/default.aspx> U.S. Army investigators warn public against romance scams: Caution-https://www.army.mil/article/130...< Caution-https://www.army.mil/article/130...> DOD warns troops, families to be cybercrime smart -Caution-http://www.army.mil/article/1450...< Caution-http://www.army.mil/article/1450...> Use caution with social networking Caution-https://www.army.mil/article/146...< Caution-https://www.army.mil/article/146...> Please see our frequently asked questions section under scams and legal issues. Caution-http://www.army.mil/faq/ < Caution-http://www.army.mil/faq/ > or visit Caution-http://www.cid.army.mil/ < Caution-http://www.cid.army.mil/ >. The challenge with most scams is determining if an individual is a legitimate member of the US Army. Based on the Privacy Act of 1974, we cannot provide this information. If concerned about a scam you may contact the Better Business Bureau (if it involves a solicitation for money), or local law enforcement. If you're involved in a Facebook or dating site scam, you are free to contact us direct; (571) 305-4056. If you have a social security number, you can find information about Soldiers online at Caution-https://www.dmdc.osd.mil/appj/sc... < Caution-https://www.dmdc.osd.mil/appj/sc... > . While this is a free search, it does not help you locate a retiree, but it can tell you if the Soldier is active duty or not. If more information is needed such as current duty station or location, you can contact the Commander Soldier's Records Data Center (SRDC) by phone or mail and they will help you locate individuals on active duty only, not retirees. There is a fee of $3.50 for businesses to use this service. The check or money order must be made out to the U.S. Treasury. It is not refundable. The address is: Commander Soldier's Records Data Center (SRDC) 8899 East 56th Street Indianapolis, IN 46249-5301 Phone: 1-866-771-6357 In addition, it is not possible to remove social networking site profiles without legitimate proof of identity theft or a scam. If you suspect fraud on this site, take a screenshot of any advances for money or impersonations and report the account on the social networking platform immediately. Please submit all information you have on this incident to Caution-www.ic3.gov < Caution-http://www.ic3.gov > (FBI website, Internet Criminal Complaint Center), immediately stop contact with the scammer (you are potentially providing them more information which can be used to scam you), and learn how to protect yourself against these scams at Caution-http://www.ftc.gov < Caution-http://www.ftc.gov > (Federal Trade Commission's website)
Create this form in 5 minutes!
How to create an eSignature for the example of a permission form
How to create an eSignature for the Example Of A Permission Form online
How to make an eSignature for the Example Of A Permission Form in Chrome
How to create an electronic signature for signing the Example Of A Permission Form in Gmail
How to create an eSignature for the Example Of A Permission Form right from your smartphone
How to generate an eSignature for the Example Of A Permission Form on iOS
How to generate an eSignature for the Example Of A Permission Form on Android devices
People also ask
-
What is an Example Of A Permission Form?
An Example Of A Permission Form is a standardized document used to obtain consent from individuals before proceeding with certain actions, such as using their image or information. This type of form can be easily created and customized using airSlate SignNow, ensuring you have the necessary approvals for your projects.
-
How can airSlate SignNow help me create an Example Of A Permission Form?
With airSlate SignNow, you can quickly create an Example Of A Permission Form using our intuitive document editor. The platform allows you to customize templates, add fields for signatures, and streamline the approval process, making it simple to gather consent efficiently.
-
Is there a cost associated with using airSlate SignNow to create an Example Of A Permission Form?
airSlate SignNow offers various pricing plans to accommodate different business needs, including affordable options for creating an Example Of A Permission Form. You can choose a plan that fits your budget while accessing robust features that enhance your document signing experience.
-
What features does airSlate SignNow offer for managing an Example Of A Permission Form?
airSlate SignNow provides numerous features for managing an Example Of A Permission Form, including customizable templates, automated reminders, and real-time tracking of document status. These features ensure you can efficiently handle permissions and stay organized throughout the process.
-
Can I integrate airSlate SignNow with other applications for my Example Of A Permission Form?
Yes, airSlate SignNow supports integrations with various applications, allowing you to connect your Example Of A Permission Form with tools you already use, such as CRM systems and cloud storage services. This seamless integration enhances workflow efficiency and document management.
-
What are the benefits of using airSlate SignNow for an Example Of A Permission Form?
Using airSlate SignNow for an Example Of A Permission Form offers numerous benefits, including faster document turnaround times, enhanced security for sensitive information, and a user-friendly interface for both senders and signers. These advantages help streamline your consent processes and improve overall productivity.
-
How secure is my Example Of A Permission Form when using airSlate SignNow?
airSlate SignNow prioritizes security, ensuring that your Example Of A Permission Form is protected with industry-standard encryption and compliance with privacy regulations. This means your documents are safe from unauthorized access, giving you peace of mind when handling sensitive information.
Get more for Example Of A Permission Form
Find out other Example Of A Permission Form
- How To Integrate Sign in Banking
- How To Use Sign in Banking
- Help Me With Use Sign in Banking
- Can I Use Sign in Banking
- How Do I Install Sign in Banking
- How To Add Sign in Banking
- How Do I Add Sign in Banking
- How Can I Add Sign in Banking
- Can I Add Sign in Banking
- Help Me With Set Up Sign in Government
- How To Integrate eSign in Banking
- How To Use eSign in Banking
- How To Install eSign in Banking
- How To Add eSign in Banking
- How To Set Up eSign in Banking
- How To Save eSign in Banking
- How To Implement eSign in Banking
- How To Set Up eSign in Construction
- How To Integrate eSign in Doctors
- How To Use eSign in Doctors