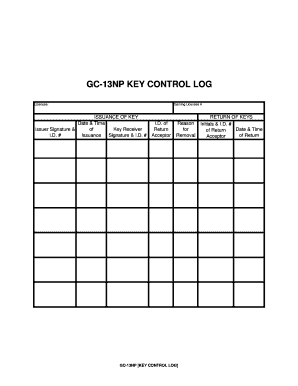
Key Control Log Form


What is the key control log?
The key control log is a crucial document used to track the issuance and return of keys within an organization. It serves as a formal record that helps maintain security and accountability by documenting who has access to specific keys and when they were issued or returned. This log is particularly important in environments where security is paramount, such as military installations, government buildings, and corporate offices. By keeping an accurate key control log, organizations can minimize the risk of unauthorized access and ensure that all keys are accounted for.
How to use the key control log
Using the key control log effectively involves several steps. First, ensure that the log is easily accessible to authorized personnel. Each entry in the log should include essential information such as the key number, the name of the person receiving the key, the date of issuance, and the expected return date. When a key is returned, the log should be updated to reflect this information, including the return date. Regular audits of the key control log can help identify any discrepancies and ensure that all keys are accounted for.
Steps to complete the key control log
Completing the key control log requires attention to detail and consistency. Follow these steps for accurate documentation:
- Start with a clear format that includes columns for key number, user name, date issued, date returned, and any additional notes.
- When issuing a key, fill in the user’s name, the date of issuance, and the key number.
- Upon return, update the log with the return date and verify that the key is in good condition.
- Regularly review the log for any missing keys or discrepancies and address them promptly.
Legal use of the key control log
The legal use of the key control log is essential for ensuring compliance with security regulations and internal policies. A well-maintained log can serve as evidence in legal proceedings if there are disputes regarding access to facilities or assets. It is important to ensure that the log meets any applicable legal standards, such as those related to data protection and privacy. By adhering to these standards, organizations can protect themselves from liability and maintain a secure environment.
Key elements of the key control log
A comprehensive key control log should include several key elements to ensure its effectiveness:
- Key Number: A unique identifier for each key to prevent confusion.
- User Information: The name and contact details of the individual receiving the key.
- Issuance Date: The date when the key is issued to the user.
- Return Date: The date when the key is returned, if applicable.
- Condition of Key: Notes on the condition of the key upon return to track any wear or damage.
Examples of using the key control log
There are various scenarios in which a key control log can be utilized effectively:
- Military Installations: To track access to sensitive areas and ensure that only authorized personnel have keys.
- Corporate Offices: For managing access to secure areas, such as server rooms or executive offices.
- Event Venues: To control access to different parts of the venue during events, ensuring that only staff can access restricted areas.
Quick guide on how to complete key control log
Prepare Key Control Log effortlessly on any device
Web-based document management has become increasingly popular among businesses and individuals alike. It serves as an ideal eco-friendly alternative to traditional printed and signed documents, allowing you to access the correct form and securely save it online. airSlate SignNow provides you with all the tools necessary to create, modify, and electronically sign your documents quickly and without delays. Manage Key Control Log on any device with airSlate SignNow's Android or iOS applications and streamline any document-related tasks today.
The easiest way to modify and electronically sign Key Control Log with ease
- Locate Key Control Log and click on Get Form to begin.
- Utilize the tools we offer to complete your form.
- Emphasize relevant sections of your documents or obscure confidential information with tools specifically provided by airSlate SignNow for this purpose.
- Create your signature using the Sign feature, which takes mere seconds and holds the same legal validity as a standard wet ink signature.
- Review all the details and click on the Done button to save your changes.
- Choose your preferred method to send your form, whether by email, SMS, invitation link, or download it to your computer.
Eliminate worries about lost or misplaced documents, tedious form navigation, or errors that necessitate printing new document copies. airSlate SignNow fulfills all your document management needs in just a few clicks from your chosen device. Modify and electronically sign Key Control Log and ensure effective communication throughout any phase of your document preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the key control log
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a key control log example and how does it work?
A key control log example is a document that tracks the issuance and return of keys within an organization. This log helps maintain security by ensuring that all access points are monitored and accounted for. By using a key control log example, businesses can prevent unauthorized access and easily identify any discrepancies.
-
How can airSlate SignNow help manage a key control log?
airSlate SignNow allows you to create, manage, and securely share key control logs digitally. By using electronic signatures, you can streamline the process of signing out and returning keys, making it more efficient. The platform's user-friendly interface and automation features enhance the management of your key control log example.
-
What are the benefits of using a digital key control log example?
Using a digital key control log example provides numerous benefits including increased security, easy access, and simplified record-keeping. Digital logs can be backed up and searched quickly, helping organizations maintain accurate records without the hassle of paper logs. Additionally, with airSlate SignNow, the log can be integrated with other management tools for better functionality.
-
Is there a cost associated with using airSlate SignNow for a key control log example?
Yes, airSlate SignNow offers a variety of pricing plans tailored to different business needs. The costs are competitive and reflect the comprehensive features provided, including the ability to manage key control logs effectively. By investing in this solution, businesses can save time and resources in managing key access.
-
Can I integrate airSlate SignNow with other applications for my key control log example?
Absolutely! airSlate SignNow supports multiple integrations with popular applications, enhancing the functionality and efficiency of your key control log example. Whether it’s a project management tool or a CRM, integrating your key control log workflow with other systems can streamline operations.
-
Who can benefit from a key control log example?
Various organizations, including schools, offices, and facilities management companies, can benefit from implementing a key control log example. By using this log, they can efficiently track key distribution, reduce the risk of loss, and improve overall security and accountability. airSlate SignNow's solutions are specifically designed to cater to different industries.
-
How does airSlate SignNow ensure the security of a key control log example?
AirSlate SignNow prioritizes security with features like encrypted document storage and two-factor authentication. This ensures that your key control log example is safe from unauthorized access. By utilizing these robust security measures, businesses can trust that their sensitive information is protected.
Get more for Key Control Log
- Johns hopkins hospital medical records form
- Downloadable printable anger management certificate form
- Electrical permit application king city oregon form
- Check into cash pdf application form
- Indexing in nursing form
- Coccfr cuyahogacounty us form
- Senior citizen certification of eligibility for tuition nvcc form
- Application for index number fee 210 00 nycourts form
Find out other Key Control Log
- Can I eSign Colorado Real Estate Form
- How To eSign Florida Real Estate Form
- Can I eSign Hawaii Real Estate Word
- How Do I eSign Hawaii Real Estate Word
- How To eSign Hawaii Real Estate Document
- How Do I eSign Hawaii Real Estate Presentation
- How Can I eSign Idaho Real Estate Document
- How Do I eSign Hawaii Sports Document
- Can I eSign Hawaii Sports Presentation
- How To eSign Illinois Sports Form
- Can I eSign Illinois Sports Form
- How To eSign North Carolina Real Estate PDF
- How Can I eSign Texas Real Estate Form
- How To eSign Tennessee Real Estate Document
- How Can I eSign Wyoming Real Estate Form
- How Can I eSign Hawaii Police PDF
- Can I eSign Hawaii Police Form
- How To eSign Hawaii Police PPT
- Can I eSign Hawaii Police PPT
- How To eSign Delaware Courts Form