File Investigation Request Form


What is the request for investigation form?
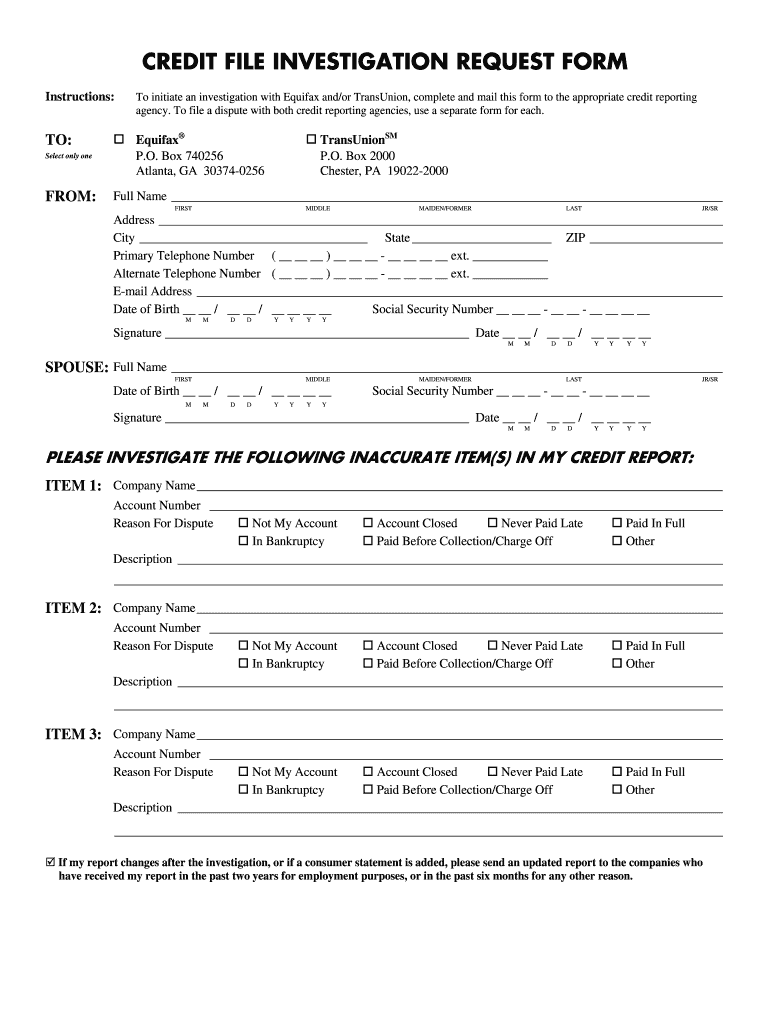
The request for investigation form is a crucial document used to initiate a formal inquiry into specific matters, such as background checks or compliance investigations. This form serves as a means to collect pertinent information from individuals or organizations seeking an investigation. It typically includes fields for personal details, the nature of the request, and any relevant documentation that may support the investigation process. Understanding the purpose of this form is essential for ensuring that all necessary information is provided to facilitate a thorough and efficient investigation.
How to use the request for investigation form
Using the request for investigation form involves several straightforward steps. First, gather all necessary information that may be required, such as identification details and the specifics of the investigation. Next, fill out the form accurately, ensuring that all fields are completed as required. If applicable, attach any supporting documents that may strengthen your request. After completing the form, review it for accuracy before submitting it through the designated method, whether online, by mail, or in person. This careful approach helps ensure that your request is processed without delays.
Key elements of the request for investigation form
The request for investigation form typically includes several key elements that are essential for processing the inquiry effectively. These elements may include:
- Requester Information: Name, address, and contact details of the individual or entity making the request.
- Subject Information: Details about the individual or matter being investigated, including identification numbers if applicable.
- Nature of the Request: A clear description of the reason for the investigation, outlining specific concerns or issues.
- Supporting Documentation: Any additional documents that may provide context or evidence relevant to the investigation.
- Signature: A signature to validate the request, confirming the authenticity of the information provided.
Steps to complete the request for investigation form
Completing the request for investigation form involves a series of methodical steps to ensure accuracy and compliance. Follow these steps:
- Gather Information: Collect all necessary details about the subject of the investigation and your own information.
- Fill Out the Form: Carefully enter all required information in the designated fields.
- Attach Supporting Documents: Include any relevant documents that support your request.
- Review the Form: Double-check all entries for accuracy and completeness.
- Submit the Form: Send the completed form through the appropriate channel, ensuring it reaches the right department.
Legal use of the request for investigation form
The request for investigation form must be used in accordance with applicable laws and regulations. It is essential to ensure that the information provided is accurate and that the request complies with privacy laws and organizational policies. Misuse of this form can lead to legal repercussions, including potential penalties for providing false information. Understanding the legal framework surrounding the use of this form is vital for both the requester and the entity conducting the investigation.
Form submission methods
Submitting the request for investigation form can typically be done through various methods, depending on the organization or agency handling the request. Common submission methods include:
- Online Submission: Many organizations offer a secure online portal for submitting the form electronically.
- Mail: The form can often be printed and sent via postal service to the appropriate address.
- In-Person: Some entities may allow individuals to submit the form in person at designated locations.
Quick guide on how to complete file investigation request form
The simplest method to obtain and endorse File Investigation Request Form
Across the entirety of your enterprise, cumbersome procedures related to paper approvals can take up signNow working hours. Endorsing documents such as File Investigation Request Form is an integral aspect of activities in any organization, which is why the efficacy of each contract’s lifecycle is crucial to the overall effectiveness of the business. With airSlate SignNow, endorsing your File Investigation Request Form is as straightforward and quick as possible. This platform provides you with the latest version of nearly any document. Even better, you can endorse it immediately without the need to download external software on your computer or print anything as hard copies.
Steps to obtain and endorse your File Investigation Request Form
- Explore our collection by category or use the search bar to locate the document you require.
- Examine the form preview by clicking on Learn more to confirm it is the correct one.
- Press Get form to begin editing right away.
- Fill out your form and include any required information using the toolbar.
- Once finished, click the Sign tool to endorse your File Investigation Request Form.
- Choose the signature method that works best for you: Draw, Create initials, or upload a picture of your handwritten signature.
- Click Done to finalize editing and proceed to document-sharing options as necessary.
With airSlate SignNow, you possess everything you need to manage your documents effectively. You can find, complete, modify, and even send your File Investigation Request Form in one tab effortlessly. Enhance your procedures by utilizing a single, intelligent eSignature solution.
Create this form in 5 minutes or less
FAQs
-
Have you ever had the pleasure of proving a customer very wrong? What happened?
I was working as a Systems Engineer for a major computer company (3-letter name) and our marketing team had sold a very expensive mainframe computer to an oil refinery. The “MIS Manager” at that plant was someone wholly unqualified for the job, lacking even basic computing skills, and with zero understanding of how computers work in the first place. A few weeks after the installation, I received a call from him, telling me their computer was broken, and that I had to get it fixed immediately. Repeated attempts to get him to tell me what was wrong got me nowhere, so I drove the 60 miles to the refinery to figure out what was wrong.Upon arriving at the plant, I was ushered into the General Manager’s office, where the MIS Manager actually accused us (the 3-letter major computer company) of intentionally sabotaging the performance of the computer so that he (the customer) would have to buy a larger computer to get the work done. I learned that the computer itself was fine, but one of their programs was taking roughly 14 hours to print out a shipping label. This did seem to be totally unacceptable performance, but his claims that the computer was broken were clearly bogus.Maintaining my professionalism, I asked if I could view the program in question – the one that printed the labels. He loudly proclaimed that the program could not possibly be the issue, because they had hired someone away from NASA to do the programming, and had paid him over $100,000 for the program. Therefore, the problem had to be the computer itself. Eventually, the GM ordered the MIS guy to give me a couple of hours access to the software, after which we would re-convene the meeting in the GM’s office to hear my assessment.The application was actually a good bit more involved than just printing labels. It was printing hazardous materials handling instructions (several pages long) for HazMat shipments originating from the plant. This involved various database lookups to obtain the ingredients, their chemical formulae, and finally the handling instructions each for those components. The application itself was written in a very high-level scripting language (REXX, for those of you who know what that is), which I found very surprising, since this type of application would typically be written in a compiled language of some kind, for performance reasons. Then, after looking at the code for only a few minutes, I realized the programmer who wrote it knew very little about programming in general, or about mainframe programming in particular. (I eventually learned that the “NASA contractor” was not actually a computer programmer when he worked there – he was actually a project manager.)After a half-hour reviewing the code, I spent the next 1.5 hours re-writing it, removing obvious performance bottlenecks, and then we tested it. My “quick hack” version took 90 seconds to print a label (vs 14 hours previously). At the follow-up meeting in the GM’s office, I explained what I had done, demonstrated the performance improvement, and stated that I was still extremely dissatisfied with the performance, but it would take more than a 2-hour quick and dirty re-write of the existing code to truly optimize it. The GM was blown away by the results, and was clearly looking at his MIS Manager in a new light.PS - After returning to our office, another gentleman and I re-wrote the application in PL/1 (a compiled language used by the customer’s IT group), and the time to print a label went to under 3 seconds. That’s the version I delivered back to them, with the explanation that a really good programmer could probably achieve even better performance, but this was the best I could do without charging them for the service. The GM was quite happy with the results, whereas the MIS Manager was still claiming that we had rigged the computer to perform poorly so they would have to upgrade to a bigger, more expensive model.By the way, the next time I visited the refinery, the GM introduced me to their new MIS Manager…
-
How do I respond to a request for a restraining order? Do I need to fill out a form?
As asked of me specifically;The others are right, you will likely need a lawyer. But to answer your question, there is a response form to respond to a restraining order or order of protection. Worst case the form is available at the courthouse where your hearing is set to be heard in, typically at the appropriate clerk's window, which may vary, so ask any of the clerk's when you get there.You only have so many days to respond, and it will specify in the paperwork.You will also have to appear in court on the date your hearing is scheduled.Most courts have a department that will help you respond to forms at no cost. I figure you are asking because you can't afford an attorney which is completely understandable.The problem is that if you aren't represented and the other person is successful in getting a temporary restraining order made permanent in the hearing you will not be allowed at any of the places the petitioner goes, without risking arrest.I hope this helps.Not given as legal advice-
-
Do military personnel need money to fill out a leave request form?
It’s great that you asked. The answer is NO. Also, whatever you are doing with this person, STOP!Bloody hell, how many of these “I need your money to see you sweetheart” scammers are there? It’s probably that or someone totally misunderstood something.All military paperwork is free! However, whether their commander or other sort of boss will let them return or not depends on the nature of duty, deployment terms, and other conditions. They can’t just leave on a whim, that would be desertion and it’s (sorry I don’t know how it works in America) probably punishable by firing (as in termination of job) or FIRING (as in execution)!!!Soldiers are generally paid enough to fly commercial back to home country.Do not give these people any money or any contact information! If you pay him, you’ll probably get a receipt from Nigeria and nothing else.
-
How do I store form values to a JSON file after filling the HTML form and submitting it using Node.js?
//on submit you can do like this
Create this form in 5 minutes!
How to create an eSignature for the file investigation request form
How to make an electronic signature for the File Investigation Request Form in the online mode
How to generate an electronic signature for your File Investigation Request Form in Google Chrome
How to make an eSignature for signing the File Investigation Request Form in Gmail
How to create an electronic signature for the File Investigation Request Form straight from your mobile device
How to create an electronic signature for the File Investigation Request Form on iOS
How to create an electronic signature for the File Investigation Request Form on Android OS
People also ask
-
What is a File Investigation Request Form?
A File Investigation Request Form is a document used to formally request an investigation into certain files or records. With airSlate SignNow, you can easily create, send, and eSign this form, streamlining your request process. This ensures that all necessary information is captured efficiently and securely.
-
How can I create a File Investigation Request Form using airSlate SignNow?
Creating a File Investigation Request Form with airSlate SignNow is simple. You can start from scratch or use a customizable template that fits your needs. Our intuitive interface allows you to add fields, include instructions, and designate signers, making the process quick and user-friendly.
-
What are the benefits of using airSlate SignNow for my File Investigation Request Form?
Using airSlate SignNow for your File Investigation Request Form offers numerous benefits. It enhances efficiency by reducing paperwork and manual handling, ensures secure electronic signatures, and provides tracking for your requests. Additionally, you can access your forms anytime, anywhere, making it convenient for your business.
-
Is there a cost associated with using airSlate SignNow for a File Investigation Request Form?
airSlate SignNow offers various pricing plans tailored to meet different business needs. Whether you're a small business or a large enterprise, you can find a plan that fits your budget for managing File Investigation Request Forms. Our cost-effective solution ensures you get the best value for your investment.
-
Can I integrate airSlate SignNow with other tools for my File Investigation Request Form?
Yes, airSlate SignNow offers integration with various applications and platforms, enhancing your workflow for the File Investigation Request Form. You can connect it with CRM systems, cloud storage solutions, and other productivity tools. This integration helps centralize your operations and improve efficiency.
-
How does airSlate SignNow ensure the security of my File Investigation Request Form?
Security is a top priority at airSlate SignNow. We employ industry-standard encryption and authentication protocols to protect your File Investigation Request Form and any associated data. This ensures that all sensitive information remains confidential and secure throughout the signing process.
-
What features does airSlate SignNow provide for managing File Investigation Request Forms?
airSlate SignNow provides a range of features for managing your File Investigation Request Forms, including customizable templates, automated reminders, and real-time tracking. You can also access analytics to monitor the performance of your forms, ensuring you stay informed about the status of your requests.
Get more for File Investigation Request Form
Find out other File Investigation Request Form
- How Do I eSign Alaska Car Dealer Form
- How To eSign California Car Dealer Form
- Can I eSign Colorado Car Dealer Document
- How Can I eSign Colorado Car Dealer Document
- Can I eSign Hawaii Car Dealer Word
- How To eSign Hawaii Car Dealer PPT
- How To eSign Hawaii Car Dealer PPT
- How Do I eSign Hawaii Car Dealer PPT
- Help Me With eSign Hawaii Car Dealer PPT
- How Can I eSign Hawaii Car Dealer Presentation
- How Do I eSign Hawaii Business Operations PDF
- How Can I eSign Hawaii Business Operations PDF
- How To eSign Hawaii Business Operations Form
- How Do I eSign Hawaii Business Operations Form
- Help Me With eSign Hawaii Business Operations Presentation
- How Do I eSign Idaho Car Dealer Document
- How Do I eSign Indiana Car Dealer Document
- How To eSign Michigan Car Dealer Document
- Can I eSign Michigan Car Dealer PPT
- How Can I eSign Michigan Car Dealer Form