Stalking Incident Log Form


What is the Stalking Incident Log
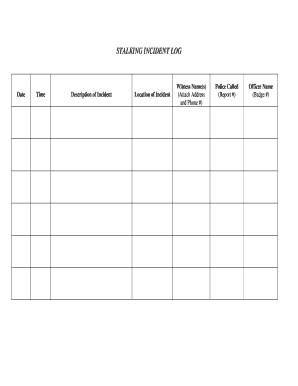
The stalking incident log is a formal document used to record instances of stalking behavior. This log serves as a crucial tool for individuals who experience unwanted attention or harassment. By documenting each incident, victims can create a clear timeline that may be essential for legal action or obtaining protective orders. The log typically includes details such as the date, time, location, description of the incident, and any witnesses present. Maintaining an accurate and detailed log can help victims articulate their experiences when seeking assistance from law enforcement or legal professionals.
How to Use the Stalking Incident Log
Using the stalking incident log effectively involves several steps. First, ensure that you have a dedicated space to record incidents as they occur. Each entry should include specific information, such as the nature of the stalking behavior, any communication received, and your emotional response. It's important to be as detailed as possible, as this information can be valuable in legal contexts. Regularly reviewing your log can help you identify patterns in the stalker's behavior, which can be crucial when discussing your situation with authorities or legal counsel.
Steps to Complete the Stalking Incident Log
Completing the stalking incident log requires careful attention to detail. Follow these steps to ensure your log is thorough:
- Record the Date and Time: Note when each incident occurs to establish a timeline.
- Describe the Incident: Provide a clear and concise account of what happened, including any threats or harassment.
- Include Location: Specify where the incident took place, as this can be relevant for law enforcement.
- List Witnesses: If others witnessed the incident, include their names and contact information.
- Document Your Feelings: Note how the incident affected you emotionally, as this can support your case.
Legal Use of the Stalking Incident Log
The stalking incident log can play a significant role in legal proceedings. Courts often require evidence of repeated stalking behavior to issue restraining orders or take other legal actions. By maintaining a detailed log, victims can provide evidence of harassment, which can strengthen their case. Additionally, the log may be used to demonstrate a pattern of behavior, which is often necessary for law enforcement intervention. It is advisable to consult with a legal professional to understand how best to use the log in your specific situation.
Key Elements of the Stalking Incident Log
Several key elements are essential for an effective stalking incident log. These include:
- Date and Time: Essential for establishing a timeline of events.
- Description of Incident: A thorough account of what occurred, including any threats or harassment.
- Location: The specific place where the incident happened, which can be important for legal considerations.
- Witness Information: Details of any witnesses who can corroborate your account.
- Emotional Impact: A record of how the incidents have affected you, which can be relevant for legal and therapeutic purposes.
Examples of Using the Stalking Incident Log
Utilizing the stalking incident log can vary based on individual circumstances. For example, a victim may use the log to document repeated unwanted communications from an ex-partner, noting each instance of contact. Another example could involve recording instances of being followed or approached by a stranger, detailing the times and locations of these encounters. These documented examples can then be presented to law enforcement or legal representatives to illustrate the severity and persistence of the stalking behavior.
Quick guide on how to complete stalking incident log
Complete Stalking Incident Log effortlessly on any device
Managing documents online has become increasingly popular among businesses and individuals. It serves as an ideal eco-friendly substitute for conventional printed and signed materials, as you can access the correct form and securely store it online. airSlate SignNow equips you with all the necessary tools to create, modify, and eSign your documents swiftly without delays. Handle Stalking Incident Log on any platform with airSlate SignNow's Android or iOS applications and enhance any document-oriented process today.
How to modify and eSign Stalking Incident Log with ease
- Locate Stalking Incident Log and click on Get Form to begin.
- Utilize the tools we provide to complete your form.
- Highlight signNow sections of your documents or obscure sensitive information using the tools that airSlate SignNow specifically provides for that purpose.
- Create your eSignature with the Sign tool, which takes just seconds and holds the same legal validity as a traditional handwritten signature.
- Review the details and click on the Done button to save your modifications.
- Select your preferred method to send your form, whether by email, SMS, invitation link, or download it to your computer.
Put an end to lost or misplaced documents, tedious form navigation, or errors that require new document copies to be printed out. airSlate SignNow meets all your document management needs in just a few clicks from any device you choose. Edit and eSign Stalking Incident Log to ensure seamless communication at every stage of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the stalking incident log
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a stalking incident log and why is it important?
A stalking incident log is a detailed record of occurrences related to stalking behavior, helping victims document incidents for legal purposes. It's crucial for gathering evidence and ensuring that law enforcement can take appropriate action. By maintaining this log, individuals can begin to establish patterns of behavior that may lead to protective measures or legal interventions.
-
How can airSlate SignNow help in creating a stalking incident log?
airSlate SignNow offers a user-friendly platform to create, sign, and store your stalking incident log securely. With customizable templates, users can easily fill out their logs and get them signed to maintain authenticity. This solution simplifies the documentation process while ensuring that your records are legally binding and easily accessible.
-
Is airSlate SignNow affordable for creating a stalking incident log?
Yes, airSlate SignNow provides a cost-effective solution for creating and managing a stalking incident log. The pricing plans cater to different needs, ensuring that users can benefit from powerful document management features without breaking the bank. Consider a trial to explore features and assess value for your specific requirements.
-
What features does airSlate SignNow offer for my stalking incident log?
Key features of airSlate SignNow include electronic signatures, document tracking, and secure storage. These functionalities simplify the process of maintaining a stalking incident log while ensuring that all documentation remains encrypted and compliant with legal standards. Users can also integrate notes or images to enhance their logs.
-
Can I integrate airSlate SignNow with other services for my stalking incident log?
Absolutely! airSlate SignNow integrates seamlessly with a variety of applications, enhancing how you handle your stalking incident log. Whether you need to connect with cloud storage services or email platforms, these integrations improve your workflow and ensure that all related documentation is well-organized and easily retrievable.
-
What are the benefits of using airSlate SignNow for a stalking incident log?
Using airSlate SignNow for your stalking incident log presents numerous benefits, including increased efficiency, security, and ease of access. The platform allows for instant signing and sharing, making it easier to involve authorities or legal counsel when needed. Additionally, the secure storage ensures that your logs remain confidential and protected.
-
Is it safe to store my stalking incident log on airSlate SignNow?
Yes, your stalking incident log is safe on airSlate SignNow. The platform employs advanced security protocols, including encryption and continuous monitoring, to ensure that your sensitive information is protected from unauthorized access. This peace of mind allows you to focus on documenting incidents without worrying about privacy concerns.
Get more for Stalking Incident Log
- Behavioral health forms printable
- Wgt teltow form
- Second grade reading log reminder read a chapter book 3 sacredheartschoolventura form
- Philadelphia case management memo 88153635 form
- Ks irp application schedule c 448540182 form
- Rehabilitation review application and instructions wisconsin form
- South carolina waste tire hauler registration form
- How do i file a complaint against dss in sc form
Find out other Stalking Incident Log
- eSignature Delaware Time Off Policy Online
- Help Me With Electronic signature Indiana Direct Deposit Enrollment Form
- Electronic signature Iowa Overtime Authorization Form Online
- Electronic signature Illinois Employee Appraisal Form Simple
- Electronic signature West Virginia Business Ethics and Conduct Disclosure Statement Free
- Electronic signature Alabama Disclosure Notice Simple
- Electronic signature Massachusetts Disclosure Notice Free
- Electronic signature Delaware Drug Testing Consent Agreement Easy
- Electronic signature North Dakota Disclosure Notice Simple
- Electronic signature California Car Lease Agreement Template Free
- How Can I Electronic signature Florida Car Lease Agreement Template
- Electronic signature Kentucky Car Lease Agreement Template Myself
- Electronic signature Texas Car Lease Agreement Template Easy
- Electronic signature New Mexico Articles of Incorporation Template Free
- Electronic signature New Mexico Articles of Incorporation Template Easy
- Electronic signature Oregon Articles of Incorporation Template Simple
- eSignature Montana Direct Deposit Enrollment Form Easy
- How To Electronic signature Nevada Acknowledgement Letter
- Electronic signature New Jersey Acknowledgement Letter Free
- Can I eSignature Oregon Direct Deposit Enrollment Form