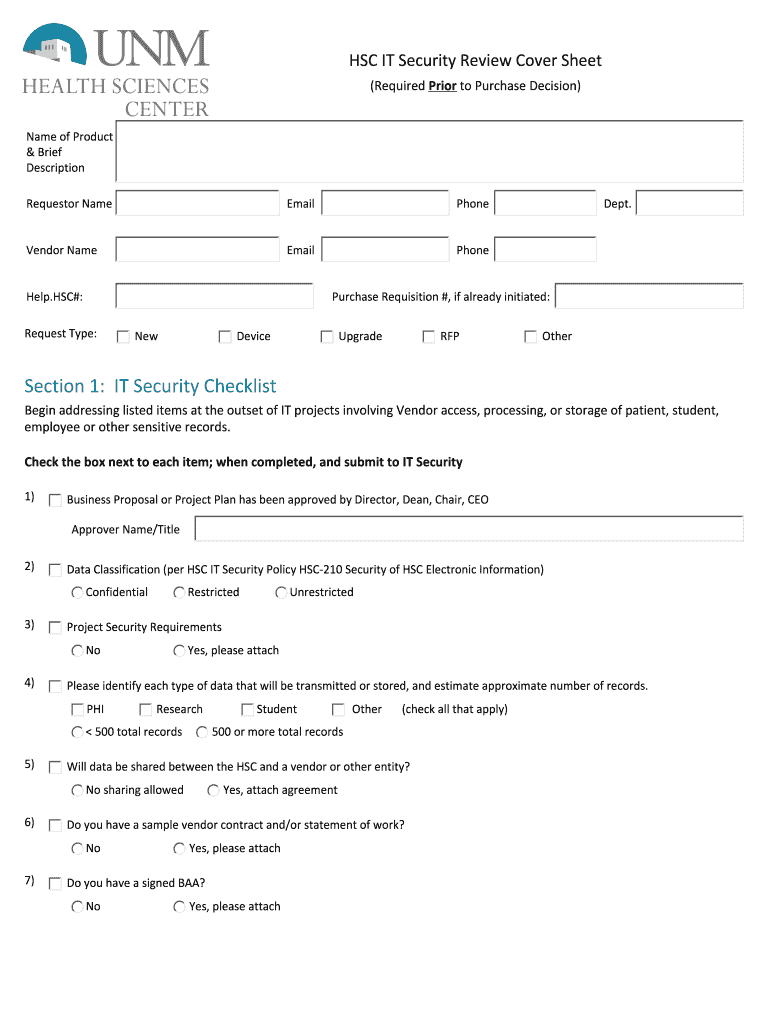
Section 1 it Security Checklist Form


What is the IT Security Checklist?
The IT security checklist serves as a comprehensive tool designed to help organizations evaluate their security posture. It outlines essential security measures and practices that should be in place to protect sensitive information and systems. This checklist typically includes various categories such as access control, data protection, network security, and incident response. By following this checklist, businesses can identify vulnerabilities and ensure compliance with relevant regulations.
How to Use the IT Security Checklist
Utilizing the IT security checklist involves a systematic approach to assess an organization’s security measures. Start by reviewing each item on the checklist to determine if current practices meet the outlined standards. Engage relevant stakeholders, such as IT personnel and management, to discuss findings and prioritize areas for improvement. Regularly updating the checklist is crucial to adapt to evolving threats and compliance requirements.
Key Elements of the IT Security Checklist
The key elements of an IT security checklist include:
- Access Control: Ensure that only authorized personnel can access sensitive data.
- Data Protection: Implement encryption and data loss prevention measures.
- Network Security: Maintain firewalls and intrusion detection systems.
- Incident Response: Establish protocols for responding to security breaches.
These elements form the backbone of a robust security framework, enabling organizations to safeguard their assets effectively.
Steps to Complete the IT Security Checklist
Completing the IT security checklist involves several key steps:
- Gather relevant documentation and resources related to current security practices.
- Review each item on the checklist, marking those that are fully implemented, partially implemented, or not implemented.
- Identify gaps and areas needing improvement based on the review.
- Develop an action plan to address identified vulnerabilities.
- Assign responsibilities for implementing the action plan and set timelines for completion.
Following these steps ensures a thorough evaluation of an organization’s security measures.
Legal Use of the IT Security Checklist
The legal use of the IT security checklist is essential for compliance with various regulations such as HIPAA, PCI DSS, and GDPR. Organizations must ensure that their security practices align with these legal frameworks to avoid penalties and protect sensitive information. Utilizing the checklist not only helps in meeting legal requirements but also demonstrates a commitment to maintaining a secure environment for data handling.
Examples of Using the IT Security Checklist
Examples of utilizing the IT security checklist include:
- Conducting annual security assessments to align with compliance requirements.
- Implementing new security measures based on identified vulnerabilities from the checklist.
- Training employees on security best practices as outlined in the checklist.
These practical applications help organizations maintain a proactive security posture and mitigate risks effectively.
Quick guide on how to complete section 1 it security checklist
Effortlessly Prepare Section 1 IT Security Checklist on Any Device
Digital document management has gained traction among businesses and individuals. It offers an ideal environmentally-friendly alternative to traditional printed and signed materials, allowing you to access the appropriate form and securely store it online. airSlate SignNow equips you with all the tools necessary to create, edit, and eSign your documents quickly and without delays. Manage Section 1 IT Security Checklist on any platform using airSlate SignNow apps for Android or iOS, streamlining any document-related process today.
The Easiest Way to Edit and eSign Section 1 IT Security Checklist with Ease
- Find Section 1 IT Security Checklist and click Get Form to begin.
- Utilize the tools we offer to fill out your form.
- Select relevant sections of your documents or obscure sensitive information with the tools that airSlate SignNow specifically offers for that purpose.
- Create your signature using the Sign tool, which takes mere seconds and holds the same legal authority as a traditional wet ink signature.
- Review the information carefully and then click the Done button to save your changes.
- Choose how you wish to send your form—via email, text message (SMS), invitation link, or download it to your computer.
Say goodbye to lost or misplaced documents, tedious form searches, or mistakes that necessitate printing new document copies. airSlate SignNow addresses all your document management needs in just a few clicks from any device you prefer. Edit and eSign Section 1 IT Security Checklist and ensure excellent communication at every stage of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
FAQs
-
What will be the appropriate section to choose while filling out the ITR 1 form online?
Please find details of return filed under sectionSection 139(1) – Original return filed before the last due date for filing returnOriginal returnfiling for the first time in an assessment yearSection 139(4) – Belated returnOriginal returnFiling for the first time after the due date of filing the return for the assessment yearSection 139(5) – Revised returnRevised return filed subsequent to original returnThis will be revised returnVoluntarily filing the revised returnInfo needed is:Acknowledgement numberdate of filing originalSection 139(9) – Defective returnWhen due to an error, the return is considered as defective (as if no return has been filed)The department may issue notice to correct the errors and file the returnSo the return filed subsequent to the intimation u/s 139(9) will be original returnYou have to provide following info while filing the return in response to noticeReceipt No: i.e Acknowledgement number of Original (Defective in this case) returnDate of filing the original (Defective in this case) returnNotice no. (Eg. CPC/1415/G5/1421417689)Date of NoticeSection 142(1) – Notice to assessee for filing the returnWhen a person has not filed the return, he may receive notice u/s 142(1) asking him to file the returnThis will be the original returnYou need to mention the notice date only while filing the return subsequent to the notice u/s 142(1)Section 148 – Issue of notice for reassessment (Income escaping assessment)Department can issue a notice to a person for filing the income tax return u/s 148This will be the original returnYou need to mention the notice date only while filing the return subsequent to the notice u/s 148Section 153A – Fresh assessment pursuance of an orderDepartment can issue a notice u/s 153A to a person for filing the income tax returnThis will be the original returnYou need to mention the notice date only while filing the return subsequent to the notice u/s 153ASection 153C – Fresh assessment pursuance of an orderDepartment can issue a notice u/s 153C to a person for filing the income tax returnThis will be the original returnYou need to mention the notice date only while filing the return subsequent to the notice u/s 153CBe Peaceful !!!
-
If we fill out all the details in the IBPS Clerk form and want to do the payment section the next day, can it happen?
Yeah ,you can do payment not only in the next day ,it is enough to pay at the last date (I am not telling to do so)but you have time upto the last date ,once u enter the basic details ,in the first page your login id will be created ,you can also enter those details after few days also… ALL THE BEST
Create this form in 5 minutes!
How to create an eSignature for the section 1 it security checklist
How to create an electronic signature for the Section 1 It Security Checklist online
How to generate an eSignature for your Section 1 It Security Checklist in Google Chrome
How to make an electronic signature for signing the Section 1 It Security Checklist in Gmail
How to create an electronic signature for the Section 1 It Security Checklist straight from your smartphone
How to create an eSignature for the Section 1 It Security Checklist on iOS
How to make an eSignature for the Section 1 It Security Checklist on Android devices
People also ask
-
What is the Section 1 IT Security Checklist offered by airSlate SignNow?
The Section 1 IT Security Checklist provided by airSlate SignNow is a comprehensive guide designed to help businesses assess their IT security measures. It includes essential security protocols and best practices to ensure the safe handling of electronic signatures and documents. By following this checklist, organizations can enhance their data protection and compliance efforts.
-
How does airSlate SignNow ensure compliance with the Section 1 IT Security Checklist?
airSlate SignNow is committed to compliance by integrating the guidelines from the Section 1 IT Security Checklist into its platform. This includes robust encryption, secure user authentication, and regular audits to ensure that all security protocols are met. Our dedication to maintaining high security standards helps protect sensitive information.
-
What features does airSlate SignNow offer in relation to the Section 1 IT Security Checklist?
airSlate SignNow offers a variety of features that align with the Section 1 IT Security Checklist, including secure document storage, customizable workflows, and advanced user permissions. These features are designed to enhance security while providing a seamless eSigning experience. Additionally, our platform allows for real-time tracking and alerts for any unauthorized access.
-
Is there a free trial available for airSlate SignNow to test the Section 1 IT Security Checklist?
Yes, airSlate SignNow offers a free trial that allows users to explore our platform and see how it aligns with the Section 1 IT Security Checklist. During the trial, you can test our features, including security measures, to understand how they can benefit your organization. This hands-on experience ensures you can assess our solution before committing to a subscription.
-
What is the pricing structure for airSlate SignNow services related to the Section 1 IT Security Checklist?
airSlate SignNow offers flexible pricing plans that cater to different business needs, including those focused on the Section 1 IT Security Checklist. Our plans vary based on features and the number of users, ensuring you can find an option that fits your budget while maintaining high security standards. For detailed pricing, you can visit our website or contact our sales team.
-
How can airSlate SignNow integrate with other software while maintaining the Section 1 IT Security Checklist standards?
airSlate SignNow supports various integrations with other software applications, all while adhering to the Section 1 IT Security Checklist standards. We ensure that integrations maintain data integrity and security through secure APIs and compliance with industry regulations. This allows businesses to streamline their processes without compromising on security.
-
What are the benefits of using airSlate SignNow in relation to the Section 1 IT Security Checklist?
Using airSlate SignNow provides numerous benefits concerning the Section 1 IT Security Checklist, including enhanced security measures, improved compliance, and efficient document management. Our platform is designed for ease of use, which helps businesses adopt secure practices without extensive training. Ultimately, this leads to increased productivity and reduced risk of data bsignNowes.
Get more for Section 1 IT Security Checklist
Find out other Section 1 IT Security Checklist
- How To eSign Rhode Island Overtime Authorization Form
- eSign Florida Payroll Deduction Authorization Safe
- eSign Delaware Termination of Employment Worksheet Safe
- Can I eSign New Jersey Job Description Form
- Can I eSign Hawaii Reference Checking Form
- Help Me With eSign Hawaii Acknowledgement Letter
- eSign Rhode Island Deed of Indemnity Template Secure
- eSign Illinois Car Lease Agreement Template Fast
- eSign Delaware Retainer Agreement Template Later
- eSign Arkansas Attorney Approval Simple
- eSign Maine Car Lease Agreement Template Later
- eSign Oregon Limited Power of Attorney Secure
- How Can I eSign Arizona Assignment of Shares
- How To eSign Hawaii Unlimited Power of Attorney
- How To eSign Louisiana Unlimited Power of Attorney
- eSign Oklahoma Unlimited Power of Attorney Now
- How To eSign Oregon Unlimited Power of Attorney
- eSign Hawaii Retainer for Attorney Easy
- How To eSign Texas Retainer for Attorney
- eSign Hawaii Standstill Agreement Computer