Cg 3029 2016


What is the Cg 3029
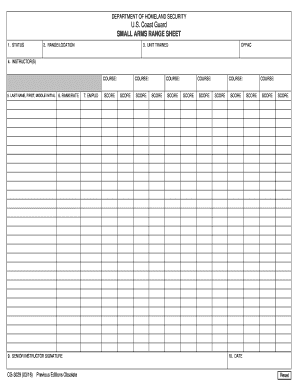
The Cg 3029, also known as the Coast Guard Marks Template, is a crucial document used by the United States Coast Guard for recording and managing small arms and ammunition. This form is essential for maintaining accurate records of firearms and related equipment within the Coast Guard's inventory. The Cg 3029 ensures compliance with federal regulations and helps in tracking the usage and maintenance of these assets. Properly completing this form is vital for operational readiness and accountability.
How to use the Cg 3029
Using the Cg 3029 involves several key steps. First, gather all necessary information regarding the small arms and ammunition you need to document. This includes details such as the type, quantity, and serial numbers. Next, access the Cg 3029 template, which can be filled out electronically or printed for manual completion. Ensure that all fields are accurately filled to avoid any discrepancies. Once completed, the form should be submitted to the appropriate authority within the Coast Guard for processing and record-keeping.
Steps to complete the Cg 3029
Completing the Cg 3029 requires careful attention to detail. Follow these steps to ensure accuracy:
- Gather all relevant information about the small arms and ammunition.
- Access the Cg 3029 template and review the required fields.
- Fill in the details, ensuring that all information is accurate and complete.
- Review the form for any errors or omissions before submission.
- Submit the completed form to the designated Coast Guard authority.
Legal use of the Cg 3029
The legal use of the Cg 3029 is governed by federal regulations that mandate accurate record-keeping for firearms within the Coast Guard. This form must be completed in accordance with these regulations to ensure compliance and avoid potential legal issues. It serves as an official record for inspections and audits, making it essential for maintaining the integrity of the Coast Guard's operations.
Key elements of the Cg 3029
Several key elements are crucial when filling out the Cg 3029. These include:
- Identification of the firearms: This includes the make, model, and serial numbers.
- Quantity: The total number of each type of firearm or ammunition being recorded.
- Condition: The current state of the firearms, whether operational or needing maintenance.
- Location: Where the firearms are stored or assigned within the Coast Guard.
Form Submission Methods
The Cg 3029 can be submitted through various methods, depending on the guidelines set forth by the Coast Guard. These methods typically include:
- Online submission: If permitted, this is often the most efficient method.
- Mail: Completed forms can be sent via postal service to the appropriate authority.
- In-person submission: Some cases may require the form to be delivered directly to a designated office.
Quick guide on how to complete us coast guard small arms range sheet
Discover the easiest method to complete and sign your Cg 3029
Are you still investing time in preparing your official documents on paper instead of online? airSlate SignNow provides a superior way to finalize and sign your Cg 3029 and associated forms for public services. Our intelligent eSignature solution equips you with all the tools required to handle documents swiftly and in line with official standards - robust PDF editing, managing, securing, signing, and sharing functionalities all at your fingertips within an intuitive interface.
Only a few steps are necessary to successfully fill out and sign your Cg 3029:
- Upload the editable template to the editor using the Get Form button.
- Review the information required in your Cg 3029.
- Navigate through the fields using the Next option to ensure nothing is overlooked.
- Utilize Text, Check, and Cross tools to fill in the blanks with your information.
- Modify the content with Text boxes or Images from the top toolbar.
- Emphasize what is signNow or Conceal areas that are no longer relevant.
- Tap on Sign to produce a legally recognized eSignature using any method that suits you.
- Insert the Date alongside your signature and conclude your work with the Done button.
Store your completed Cg 3029 in the Documents folder within your account, download it, or transfer it to your chosen cloud storage. Our service also provides convenient file sharing options. There’s no need to print your templates when you can submit them directly to the relevant public office - do it via email, fax, or by requesting a USPS “snail mail” delivery from your account. Experience it now!
Create this form in 5 minutes or less
Find and fill out the correct us coast guard small arms range sheet
FAQs
-
U.S. Coast Guard: How do coastguards search for and recover bodies of individuals swept out to sea?
US Coast Guard search operations for persons in the water (PIW's) utilize software from a program called SAROP's which takes in historical water current patterns, on scene weather/winds/currents, time of day/illumination level, size of person, what the person is wearing, whether or not the person has a flotation device and the type of aircraft or vessel doing the search. Once on scene a Coast Guard asset can deploy a data marker Bouy which can then be relocated its drift can then be used to better create a search pattern. The amount of time the Coast Guard will search for a PIW depends on the water temperature and what the PIW is wearing. A PIW with a flotation device in the Caribbean might survive a couple of days while a PIW near Alaska with no survival gear will be hypothermic in under an hour. The success of these searches largely depends the accuracy of the time/location of where the person fell off the vessel/washed out to sea. If the original information isn't very accurate then the search plan will be an educated guess. In most cases the Coast Guard doesn't search for bodies. A search action plan will be executed through such a time as it would be reasonable to expect the PIW to still be alive. Also of note a person with a 406 emergency positioning radio beacon (Epirb) will be found very quickly also a person with a strobe light at night or a mirror during the day is very easy to locate if we are in the general vicinity!
-
How can I take my child (16yrs) to the U.S if my immigrant visa is approved? My husband, a US citizen, filled out form I 130 for me and mentioned this child as migrating in future.
Just petition using a I-130 yourself. Read the instructions very carefully. I am not sure but it’s possible that the affidavit of support will need to be filled by your husband since he is the citizen and he filled one for you - again, check the instructions very carefully. It should be a pretty clear, straightforward process.Your child is still well below the age limit and should be fine. If there are any problems, do the same thing you did with your own process - use the numbers you are given to check on the process and if you see it stuck call to make sure they have everything they need early.It is my understanding that the age limit of the child is based on the petition date, so go ahead and do it.You still have plenty of time at 16, just don’t delay.
-
Why should it be so complicated just figuring out how much tax to pay? (record keeping, software, filling out forms . . . many times cost much more than the amount of taxes due) The cost of compliance makes the U.S. uncompetitive and costs jobs and lowers our standard of living.
Taxes can be viewed as having 4 uses (or purposes) in our (and most) governments:Revenue generation (to pay for public services).Fiscal policy control (e.g., If the government wishes to reduce the money supply in order to reduce the risk of inflation, they can raise interest rates, sell fewer bonds, burn money, or raise taxes. In the last case, this represents excess tax revenue over the actual spending needs of the government).Wealth re-distribution. One argument for this is that the earnings of a country can be perceived as belonging to all of its citizens since the we all have a stake in the resources of the country (natural resources, and intangibles such as culture, good citizenship, civic duties). Without some tax policy complexity, the free market alone does not re-distribute wealth according to this "shared" resources concept. However, this steps into the boundary of Purpose # 4...A way to implement Social Policy (and similar government mandated policies, such as environmental policy, health policy, savings and debt policy, etc.). As Government spending can be use to implement policies (e.g., spending money on public health care, environmental cleanup, education, etc.), it is equivalent to provide tax breaks (income deductions or tax credits) for the private sector to act in certain ways -- e.g., spend money on R&D, pay for their own education or health care, avoid spending money on polluting cars by having a higher sales tax on these cars or offering a credit for trade-ins [ref: Cash for Clunkers]).Uses # 1 & 2 are rather straight-forward, and do not require a complex tax code to implement. Flat income and/or consumption (sales) taxes can easily be manipulated up or down overall for these top 2 uses. Furthermore, there is clarity when these uses are invoked. For spending, we publish a budget. For fiscal policy manipulation, the official economic agency (The Fed) publishes their outlook and agenda.Use # 3 is controversial because there is no Constitutional definition for the appropriate level of wealth re-distribution, and the very concept of wealth re-distribution is considered by some to be inappropriate and unconstitutional. Thus, the goal of wealth re-distribution is pretty much hidden in with the actions and policies of Use #4 (social policy manipulation).Use # 4, however, is where the complexity enters the Taxation system. Policy implementation through taxation (or through spending) occurs via legislation. Legislation (law making) is inherently complex and subject to gross manipulation by special interests during formation and amendments. Legislation is subject to interpretation, is prone to errors (leading to loopholes) and both unintentional or intentional (criminal / fraudulent) avoidance.The record keeping and forms referred to in the question are partially due to the basic formula for calculating taxes (i.e., percentage of income, cost of property, amount of purchase for a sales tax, ...). However, it is the complexity (and associated opportunities for exploitation) of taxation legislation for Use # 4 (Social Policy implementation) that naturally leads to complexity in the reporting requirements for the tax system.
-
If every state of the USA declared war against each other, which would win?
The things I’m taking into consideration are the following: -Access to military hardware stationed within a state-Access to oil and oil refineries-Access to ports on defensible waterways for supplies coming from abroad (I’m assuming the lack of foreign intervention is limited to military action; trade is still constant, as in previous US domestic wars)-Domestic agriculture and water supplies-Natural barriers After all of this, a matter of prime importance I take from Alexander Hamilton is the ability to borrow money. Credit is of prime importance to a war effort. Fiat currency would collapse overnight, and the ability to establish new capital and monetary markets to get lending moving again would be of major importance. I’ll start from my own home state of WA. The first thing to do would be for WA to hit AK. They're the only state in position to do so, and they would need to get a hold of the oil resources to remain standing. WA is home to three supercarriers, while CA only has one now. So taking Alaska would be fairly straight forward, especially given the reliance of Alaska on shipping to survive and the high proportion of the population near the coasts. This would put WA in position to quickly seize HI and its naval resources--an onslaught that HI could not resist--and thus put WA in position to gain control of all naval assets in the Pacific, including the supercarrier George Washington based in Japan. Controlling Oregon would only be valuable insofar as it was necessary to take control of the Columbia River, but Idaho is a second consideration after the short-term goal of domination of naval fleets. Idaho expands arable land, and covers a border with a major population center on it. California's biggest first concern would be controlling its water supply, so the bulk of its immediate effort in the outset should be directed to the Colorado river, with strategic interest in taking nuclear and petrochemical resources in NV, UT, and CO, with Arizona subdued to protect the Colorado River access. The big power that I feel is underestimated is Virginia. It has massive naval resources, including the best shipyards and the Pentagon with all of its resources. Their navy would very quickly subdue the massive coastal exposure of MD, and WV would be an obvious and relatively easy way to secure coal--those would both go quickly. It would then turn its attention to control of the Delaware river, where it would easily put the squeeze on Philly. Taking PA would be a good access of manpower, agriculture, industrial capacity, and natural gas. All would be important. Expansion to the south includes the tough nuts of NC and SC (with Fort Bragg, Camp Lejune, and the Naval Weapons Station). Fighting inland means trying to trek across the Appalachian Mtns. But most signNowly, no VA military would choose to fight southerners over shooting Yankees. So north it is. Meanwhile, NY, for all its strengths, is very, very vulnerable. NYC is a huge indefensible liability. Their interest would rapidly turn to two thinks: taking the low-hanging fruit of Vermont to secure the Hudson/Lake Champlain before Mass does, and getting the oil refineries of New Jersey. They may cross with MA a bit taking CT and RI to make sure Long Island is less exposed, but they'd win if Mass tried. MA may be better off taking the short-term gains of NH and ME (ME was once a part of MA, after all). But NY could not defend the shipping lanes to NJ very long. VA would move up the Delaware and perhaps the Susquehanna, and with PA secure, would put the squeeze on NJ by first striking the Capitol on the Delaware. NY would hit NJ from across the sound. NY would start sending children and seniors upstate out of NYC, and use its massive manpower for a land strike against VA by invading PA from the north. NY would also be able to use its massive gold deposits for collateral to get international financing. At about this point, VA would start sending its navy up the coast and begin a blockade of NY Harbor. NY would not last long. Further inland, Kentucky has two great resources (Ft Campbell and Ft Knox) but two huge liabilities (low population and landlocked). First they’d sucker-punch Tennessee to swell their ranks, then they’d go after Ohio to get access to shipping and lending from abroad. It would be brutal, but when Kentucky won, they’d be ready to start hammering at Indiana and Michigan immediately. Texas would consolidate by first hitting NOLA (as described by others). Succeeding there, they’d use their air force and conventional army forces in a grand march north to pick up all of those square states that always go red. With oil and oil refineries and both a solid harbor and international border, when the US currency collapsed under the scenario (a guarantee), few would be able to get financing from abroad. Texas would be an early favorite and have solid credit. So they’d push all the way up, seeking to secure both grain and the grand prize of the northern plains: the Bakken formation of oil in the MT/ND region. Bakken would also be Colorado’s goal. With NORAD, air force strength, and mountain seclusion, oil would be one of its biggest concerns. TX wouldn’t strike straight into the Rockies, because it would be a waste of resource. So as Colorado succeeds in taking WY and UT (also having petroleum plus cattle and copper and coal), they’d try to hit MT and ND before TX could. That’d be hard, because TX would be surging up the plains. WA would hit California in its Achilles Heel, with control of the sea making an inability for CA to draw credit or protect its shipping lanes. Though they’d take NV and AZ fairly easily, and though they have some oil and many refineries, if WA took AK and HI, WA would be in the cat bird seat to secure US military resources in Japan and S. Korea, much of which they’d bring home. By putting pressure on CA, their oil would run dry and their military would come to a grinding halt. Knowing that trying to wait out a siege would waste valuable time while Texas was growing stronger and stronger, their resolve would wane. For the sake of avoiding a fall to Texas, CA would instead fall to WA. NM would be the no-man’s-land that everyone wouldn’t bother to touch. All liability, not much advantage. Given that we’re assuming a conventional war, the nuke resources wouldn’t be worth all that much. Illinois would strike first at Wisconsin and then at Indiana. They’d be at a point of fighting the Kentucky forces in the middle of Indiana when Texas would take them by storm—first securing MN, then taking WI from IL, and then moving low draft boats to Lake Michigan to start shelling Chicago. It wouldn’t take long for them to fall. Not yet mentioned is Florida, which is also far stronger than is properly appreciated: air force, lots of navy, open supply lines, ability to drill in the Gulf. They’d be the only ones in a position to try to strangle TX at NOLA, but there’d be no point in the early rounds. First they’d bypass Georgia and hit the Carolinas for their military capacities, then hit the boggy Mississippi and Alabama (more difficult for Texas than its worth this early), and Georgia would be crushed easily by encirclement. So consolidating: WA takes basically everything west of the Rockies, Texas takes the full plains and Mississippi river, CO has the northern Rockies with WY and UT with skirmishes against TX in MT and ND, KY takes OH, TN, IN, and MI, FL takes MI, AL, GE, NC, and SC, and Virginia subdues NY to take everything else. Texas now loses its main advantage by having borders exposed to all major players except VA. They fight WA for CO, WY, and MT, with WA quickly taking UT from CO once they begin to press inland. Texas also fights KY for control of the Ohio River Valley, and they’ve been drained by their first major fight in subduing IL. KY and FL strike a détente (because FL has all the strength and knows VA will take care of KY for them), and while KY puts pressure on IL (now controlled by TX), FL strikes at MO to cut the Mississippi and disrupt the flow of control, all while finally launching its blockade of NOLA. Now VA is ready to press inland, and they start in OH. KY is overextended already, and VA’s northern block presses east, quickly consuming the remnants of KY. TX briefly makes headway in Indiana, but can’t consolidate—FL and WA are increasing the pressure. At about the time that TX makes a major victory and secures most of CO, they lose NOLA to FL, and MO falls shortly afterward. It’s a devastating blow. But it isn’t long before VA antagonizes FL and draws them into a full naval confrontation. TX rapidly regains what it had, and starts the long overland push through the Deep South. WA has good consolidation, but can’t make inroads past the Rockies. TX makes headway in WY and MT, while dog fighting occurs over NM between the rival air forces of CA (controlled by WA) and TX. As VA manages supremacy over FL (the battle to take Florida becomes among the bloodiest and most devastating of any in the war), the remainder of the South quickly falls under its control. It now has the full eastern seaboard. Final result: VA. Both WA and VA hammer TX, and once weakened, only VA has the clear route to subdue TX completely and regain the states. After that, the WA Pacific theater is doomed. The East has control of more money, more forces, more oil, more everything. It’s a long and bitter war of attrition, but the peaceniks on the West Coast don’t have the fight in them. VA wins. And so ironically we see that the battle was won when Jefferson sat Hamilton and Madison down to dinner to negotiate an agreement to help resolve the impasse in Hamilton’s move to have the Federal government assume all Revolutionary War debt held by the states, with Hamilton agreeing to bargain the nation’s capital for the sake of the funding scheme. It was agreed that night that the capital should have a temporary home in Philadelphia for 10 years, then move to a permanent site on the Potomac. Madison would free up some votes to pass the assumption initiative. The Virginians had the goal that the southern sensibilities of the region should dominate the Federal government and shape its character—a stark reversal of what the nation seemed to be developing into under Hamilton’s vigorous administration in which he essentially assumed the role of a Prime Minister under the generally aloof Washington. And for the next half century and some change, the Federal Government did fall under the sway of the South. The Bank that Hamilton had founded did not see its charter renewed, and the Jackson Democrats became the major drivers of the early 19th century. But in time, the direction of influence reversed. Today, rather than VA imparting a Southern perspective on DC, DC asserts a Federal character and national sensibilities to the Old Dominion. It is now the natural seat of power for the nation.
-
How reliable was the M1 Thompson in combat in WW2?
In essence, the Thompson was reliable.Thompson submachine gunHowever, the Thompson is a rather unique case as Its creator, General Thompson, initially thought that the different metals used in the gun would eventually adhere to each other due to static friction, a theory created by John Blish after looking at naval guns.General ThompsonJohn BlishJohn Blish’s solution to his theory, known as the Blish’s Principle, was to create a new delay-blowback mechanism known as the Blish lock, which was then used in the Thompson sub-machine gun later on.Blish LockThis meant that unlike other guns, the Thompson was built in mind with the possibility that due to Its rate of fire, the Thompson could jam easily.Alas, this precaution was not needed as Savage arms, when designing the simplified M1 variant, found that the Thompson worked just as well using a simple blow-back system[1].BlowbackM1 ThompsonAnother reason why the WW2 Thompson was reliable was due to the fact that It had Its capacity reduced signNowly, with Its infamous 50 round drum magazine being completely removed from the M1 and M1A1 models.Thompson drumThis high capacity drum meant that the Thompson would have to fire longer before It ran out of ammo and while this may not have been an issue on other guns, bear in mind that the Thompson had an RPM of 830 in the original variant[2].Original ThompsonThis was why the original Thompson had cooling fins to help disperse the heat when the Thompson was fired.Cooling fins on an original Thompson barrelThis meant that the WW2 variant of the Thompson was operating at a heat level far lower than what was seen in the original variant, which was why it had no cooling fins and was thus more durable and reliable.This is further helped by the fact that the WW2 variant of the Thompson is detuned to an RPM of only 625, which is far lower than the 830 seen in the originalAnd finally, another reason why the Thompson is reliable is due to Its construction.It isn’t a secret that most US-made guns were of considerably higher quality than other allied or axis counterparts, as the US was one of the few countries in the war to be completely untouched.US during the warHence, the US had better access to better materials and better machining, which are two key components in ensuring that a design would be more durable and reliable for Its intended application.Since these Thompsons are made out of more durable and reliable parts, the chances of them malfunctioning are signNowly lower.Hence, this was why the Thompson was reliable during WW2.That’s all folks!Footnotes[1] Thompson submachine gun - Wikipedia[2] Thompson submachine gun - Wikipedia
-
What are some of the greatest deceptions ever achieved in military battle?
In his seminal tome “The Art of War”, Chinese author Sun Tzu laid out the basic tenets of winning any conflict. At the top of Sun Tzu's list was the delicate but powerful art of deception. Misleading the enemy through camouflage, troop maneuvers, disinformation, or any other means can lead your opponents to believe that you're not where you say you are, or even who you say you are.Almost all successful defense tactics and strategies involve some degree of deception, a concept which most people learn early in life. If you've ever heard the old axioms, "surprise is your best weapon" or "keep your cards close to your chest," then you've already got some rudimentary education on the importance of deception in battle.This list contains some of the greatest deceptions in military history. These truly groundbreaking, history-making moments managed to turn probable loss into crushing victory. Without a doubt, almost every grand-scale conflict in the history of human civilization contains at least a few great deceptions, but this particular set of well-crafted lies really changed the world.Cannae, 216 B.C. – HannibalThis legendary battle is the one that both put Hannibal into the history books, and reportedly resulted in a word most of us have used at least once.After Rome's crushing defeat at Lake Trasimine, and after growing impatient with the brilliant Fabian strategy of simply waiting out Hannibal's next strike, the empire made what might be the worst mistake in the history of war: they sent an 80,000-strong army out to meet Hannibal's force of 50,000 in all-out battle. After selecting the battlefield himself, Hannibal deployed his outnumbered troops in a long, thin line that bowed out in the center. He placed his huge cavalry forces in blocks at either end, though to the Romans, the line looked perfectly straight.They hit Hannibal's center hard, and the bowed line was pushed back; the edges, however, held their ground. Thinking they were inching towards victory, Rome pushed forward until Hannibal's bow inverted and his flanks began wrapping around Rome's. Eventually, the Romans were boxed in on three sides, and Hannibal sent his cavalry around behind them to close the box and attack from the rear. This was history's very first use of the classic "double envelopment."Hannibal had reduced Rome's military to nothing, or ad nihil in Latin. The French later adapted ad nihil into the word "annihilate."Lake Trasimene, 217 B.C. – HannibalHannibal is undoubtedly a top contender for the title of history's greatest commander. The Battle of Trasimene was history's first use of the strategic turning movement, and remains to date the largest and most lethal ambush of all time. Hannibal began the ambush by baiting Roman general Flaminius to chase his force through the countryside. Hannibal's first tactic was to move between Flaminius and his supply lines to Rome, getting behind his defensive line and forcing his army to move.They chased Hannibal to the North shore of Lake Trasimene and into a narrow pass between the lake and surrounding hills. Earlier in the night, Hannibal had sent men miles ahead to light campfires, causing Flaminius to believe Hannibal's forces were still distant. Using the early morning fog of the lake for cover, his entire force took advantage of Flaminius' ignorance to sorround his ranks, taking them in the flank and trapping them on all sides. Hannibal wiped out half of Flaminius' 30,000-man army while losing only 2,500 soldiers of his own.Battle of the Hydaspes, 326 B.C. – Alexander the GreatThe Hydaspes river is the largest and westernmost river of the Punjab, and was, in ancient times, effectively the western border of India. On the Indian side was an area called Paurava, ruled over by King Porus. On the European side lay the expanded domain of Persia, now ruled over by Alexander the Great. Alexander had already proven his might by conquering the entire known world from his home in the small Greek town of Macedonia. Having accomplished his goal and proven his genius, Alexander decided to push East past the mighty Hydaspes to conquer whatever lay on the other side.Porus saw Alexander's massive army coming, however, and lay in wait on the other side of the river, watching the opposing army like a hawk; if Alexander moved up the river, Porus moved on the opposite shore. If Alexander moved down, Porus moved with him.But Alexander watched Porus as well. Seeing how Porus followed him, Alexander instructed small groups of his army to march up and down the river banks every day, making as much noise as possible. Eventually, Porus's troops became accustomed to the practice, and stopped paying close attention to the clanking coming from the other side. Quietly, Alexander began withdrawing his main force back and away from the river, leaving the noisy cavalry on its shore to march back and forth every day.Porus assumed he was looking at the front of Alexander's entire force; he didn't know that the main body of his enemy's infantry was stealthily sneaking toward the only crossing upstream. Porus finally deduced the situation but was too late to act. Alexander had crossed the river, and whipped around behind Porus's army. As Porus turned to face him, Alexander's mounted cavalry charged across the river and attacked Porus from behind.Porus lost 23,000, compared to less than 1,000 of Alexander's troops.D-Day Landing at Normandy, 1944 – AlliesThe many deceptions involved in the Normandy landings are legendary in both American and global history.Hitler knew the Allied invasion of Europe was coming, but he didn't know exactly where his enemy would land, rendering the proper positioning of his troops practically impossible. Prior to the invasion, British intelligence fed the Germans misinformation about where the invasion would land through a number of double agents. Probably the most influential of these, Garbo, managed to convince Hitler that the invasion would land a hundred miles from Normandy. The allied generals, including future president Dwight Eisenhower, fed that delusion with false radio traffic, misleading messages, and armies of decoy tanks and trucks that looked legitimate from more than 50 feet away.This pattern of deception enabled the allied troops to attack German forces with enormous success.The D-Day campaign stands as perhaps the greatest and most successful use of deliberate deception in 20th-century warfare.Battle of the Kalka River, 1223 A.D. – Ghengis KhanThis battle took place along the Kalka River in Ukraine between 80,000 Russians (or Kievan Rus, as they were known at the time) and 20,000 of Genghis Khan's mounted raiders. After years of terrorizing the Russians, one of Khan's raiding parties resulted in the death of the king of the former Byzantine vassal state of Georgia. The Russians assembled an army and took off in pursuit of Ghenghis' raiders. They easily knocked back the raiders, who broke off into a panicked retreat. The Mongols' 1,000-strong rear guard bought them some time, but eventually, they too ran away, keeping just ahead of the Russians' advance.Russia chased after them, right into Khan’s trap. Khan had reassembled his main force and hidden it near a narrow pass by the river. This was almost exactly the same strategy Hannibal had employed at Lake Trasimene a thousand years before, but in this instance, the feigned retreat was what drew the Russians into their own killbox. One group of Russians panicked, and turned back to run away. This left a gaping hole in the Russian lines, and Khan's mounted warriors poured through.The Russian casualties from the battle amounted to at least 75,000; likely the only people to escape Khan's clutches were those who had fled.The Battle of Stalingrad, 1942 – RussiaRussia has long been one of the great masters of military deception; they even developed a comprehensive system for it called "maskirovka" in the early 20th century. Maskirovka is a full suite of techniques including camouflage, disinformation, deceptive movements, decoys, feigned retreats, and deliberate losses, among other methods. Russia utilized these tactics in Operation Uranus, the setup for Hitler's crushing defeat at Stalingrad.Stalin used many of the same tactics as the Allies at Normandy, but added a few more. Playing on Hitler's ego and self-delusion, Stalin sent out fake radio messages in a code he knew the Germans had broken, saying that Russia's forces were weak and failing in the area. He ordered fake trenches to be dug around the city, feigning a desperate last stand of the infantry, and sent scores of his own troops on suicide missions to deliberately lose small skirmishes with the Germans outside of town. Once Hitler's confidence was at an all-time high, he committed almost his entire Russian-area force to storm Stalingrad in an overwhelming show of force.After Hitler's million-man force was comfortable within the quiet, empty city of Stalingrad, Russian tanks, artillery and troops sprung out of hiding all around them. Mimicking his predecessor, Hannibal, Stalin trapped the Germans in a classic double envelopment, accordingly annihilating them. The Germans suffered 850,000 casualties out of the one million troops committed, along with 900 aircraft, 500 tanks and 6,000 artillery pieces.Stalingrad is said to have been the single most decisive battle of WWII, having permanently ended Hitler's ambitions on the Eastern front.The Valley Campaign, 1862 – Thomas "Stonewall" JacksonRobert E. Lee gets his fair share of rightly deserved press for being an aggressive, intelligent commander, but objectively, Thomas "Stonewall" Jackson was most likely the more tactically gifted of the two Confederate generals. Jackson's 16,000 man force wasn't exactly small, but it paled in comparison to the 52,000 Union soldiers drawing down on the Shenandoah Valley in Virginia during the first major offensive Union movement. To compensate for this disparity, Jackson bluffed.Seeking to meet up with Lee in defense of Richmond, Jackson suddenly found the epicenter of convergence of both halves of the Union army. Had the Union known of Jackson's mere 16,000 men, they would have crushed Jackson forces; however, Jackson had sending infiltrators out among enemy lines, spreading rumors that his force numbered in the six digits. As the Union forces closed in on both sides, Jackson force-marched his army from one side of the Valley to the other, engaging the two halves in turn with his full force. After driving one army back, he'd force-march to the other side of the valley and fight the other.Eventually, the Union came to believe the whole area was swarming with hundreds of thousands of Confederate troops, never knowing it was just Jackson bouncing his smaller force back and forth. The Union withdrew, and began to flee until the side led by General Nathaniel Banks found Jackson waiting in front of them at their own Garrison at Front Royal. While Banks was running away from Jackson to resupply, Jackson had snuck around them on a train, joined up with another force, and captured Banks's own garrison.Lincoln eventually ordered a full-scale retreat from the area, believing that Stonewall Jackson's massive army was simply inescapable.Codebreaking and Counter-Intel, WWII – AlliesThe Allies have just broken Japan's most important and secure naval code, JN-25. In Europe, the British have used the Colossus computer to break Germany's Lorentz and Enigma cyphers. They're now reading the enemy's mail, accessing everything they're saying and doing, and everything they think about what the Allies themselves are doing. At this point, they find themselves in an ethical bind: they can't openly act on this information without risking the enemy changing the codes; however, they need to maximize the power they've gained through their discoveries to get an edge on both Germany and Japan.The great deception that solved this dilemma was counter-intelligence. When the Allies would find out that the Japanese fleet was going to be in a certain place at a certain time, they'd place ships at those predetermined coordinates to intercept them. They would then send out messages in a code they knew the Japanese had already broken, discussing how "lucky" they were that their Allied ships "happened to be in the right place at the right time."The Allies did the same in Europe, fabricating entire "missions" that "failed at their intended objective," but just so happened to be in the best possible position to keep a Panzer division from crossing a bridge. These messages were intended to be intercepted by the Nazis, who would never know that their code had been broken.The Trojan Horse, circa 1200 B.C. – OdysseusDuring the Trojan War, Odysseus famously crafted a giant, wooden horse – the emblem of the city of Troy – and filled it with thousands of armed men. He told the Trojan leaders that his gift was an offering to the goddess Athena, who's temple had been destroyed by the Greeks.They accepted the gift, and as soon as the horse was safely inside the city walls, Odysseus's men climbed out and massacred the city.Iwo Jima, 1945 – Japanese Armed ForcesIn the Marines' island-hopping campaign to signNow Japan's mainland, they instated a policy to capturing every single piece of land along the way, regardless of its strategic importance. The battles for most islands were difficult, especially against the Japanese. They were masters of camouflage, booby traps, and surprise attacks, and were known to dig tunnels through the concrete-like limestone rock of islands.The tiny island of Iwo Jima was no exception, but U.S. forces hugely underestimated the extent of Japan's fortifications. Iwo Jima wasn't a seemingly peaceful island with a few tunnels; it was a fortress carved into a rock. When the 110,000 men of the Allied forces landed, they expected to encounter several thousand Japanese and the usual assortment of artillery and arms. What they found instead was a well-armed hornet's nest bristling with gun emplacements, coastal artillery, 21,000 Japanese troops, and 11 miles of underground tunnels to move and supply them. This was all under a seemingly idyllic island barely two miles wide.The the Japanese were eventually defeated, the battle cost 7,000 American lives, 19,000 wounded, one sunken escort carrier ship, and two more carriers damaged. It is said that Iwo Jima was the final straw in Truman's decision to launch a nuclear attack on Hiroshima.Vietnam War, 1955 to 1975 – The Viet CongRight down the coast from China, and having learned tactics from the Japanese in WWII, the North Vietnamese who battled American and European forces were true believers in the power of deception. Like the Japanese at Iwo Jima, they tunneled underground to turn seemingly harmless swatches of jungle into invisible fortresses. Regularly using feigned retreats and feigned weakness, and often launching diversionary strikes as means to steer U.S. troops where they wanted them to go, the VC exploited every possible weakness of the American troops.The VC set up networks of "American friendly" bars, restaurants and brothels to stay as close to the enemy as possible. Anyone the soldiers interacted with in these locations could have been a spy. While these infiltrators did often engage in acts of violence or sabotage, their function was mostly to listen to what the soldiers were saying to get advance notice of troop movements, tactics, and morale. Secondarily, they would feed misinformation back to trusting soldiers and commanders, setting them up for ambushes while chasing after shadow armies.The Exodus, Pillars of Smoke and Fire – MosesDuring the period in which Moses famously led the Israelites out of Egypt and across the Red Sea, commanders would usually keep their armies in line by walking ahead of them with a burning brazier. During the day, the army followed the brazier's smoke signal, and at night, the light of its open flame. These are most likely "the pillars of smoke by day and fire by night" mentioned in Exodus. The Hebrews may or may not have been following the Angel of the Lord, but they were almost certainly following Moses with a common signaling brazier.However, according to the biblical account "The angel of God who was going before the host of Israel moved and went behind them, and the pillar of cloud moved from before them and stood behind them, coming between the host of Egypt and the host of Israel." If this account is accurate, Moses moved the brazier behind his column instead of ahead of it. This undoubtedly confused the Egyptians, who, knowing what the signal meant, probably thought the column had reversed course after getting lost in the desert and started doubling back towards them.That night, the bright brazier light behind Moses' coterie blinded the Egyptians, preventing them from seeing the Hebrews on the other side. They believed the Hebrews had made camp, but in reality, they were stealthily sneaking across the now-dry tidal marsh. By the time Pharoh recognized the deception, it was too late. The tide had already come in, making it impossible for the Pharoah's men to follow them.The Exodus, Parting the Red (or Reed) Sea – MosesExodus states that Moses "stretched out his hand over the sea, and the Lord drove the sea back by a strong east wind all night, and made the sea dry land, and the waters were divided." Barring the theory of divine intervention, there may be another interesting explanation for these events. Moses knew the desert well; he also knew the habits of the Red Sea – or the "Reed Sea" as it was known then. This sea from the Bible may have actually been little more than a tidal swamp that regularly flooded during the day and dried out at night when the sea winds started blowing.Moses would have been aware of this cycle, and could have deduced that if the Hebrews simply waited overnight, the sea would "part" long enough for the Israelites to cross, closing in behind them when the tide returned. This would trap the Egyptians, as their heavy chariots would be stuck in the mud.Russia, Battle Of Kursk, World War IIMaskirovka is a broad military doctrine of Soviet deception developed throughout the early 20th century. Its primary focus is denial, deception, and surprise. The practice utilizes several means of fooling the enemy, ideally suggesting to them that a smaller force is awaiting them “over the hill.”It was most successfully employed at the Battle of Kursk during World War II, when a relatively large force of Germans unwittingly attacked what they believed to be a small force of Russian troops, which actually numbered more than four times their own. The Russian forces were able to achieve this, in part, by spreading rumors throughout their own ranks as to their capabilities and strength, which spread to the Germans through their counterintelligence collection means. Ammunition and supplies were moved only under the cover of darkness, while camouflage was utilized to conceal anything of military value. Additionally, the Soviets employed fake airfields, which enticed the Germans to bomb dummy aircraft, further confusing their assessment of the Soviet military strength and capabilities.Prior to the battle, the Germans underestimated the Russians’ strength, thinking that they had fewer than 1,500 tanks and 400,000 men ready to fight. Unfortunately for German intelligence, the Russians’ deception worked, and they confronted more than 1.3 million fighting men, more than twice the estimated number of tanks, and nearly 3,000 aircraft. The resulting battle destroyed the German offensive and earned the Soviets their first victory against the Germans along the Eastern Front. For the remainder of the war, the Germans would be on the defensive all the way to Berlin.The doctrine is still being used, most recently in the annexation of the Crimean Peninsula and the taking of Eastern Ukraine.England Bluffing: Battle Of Fishguard, War Of The First CoalitionIn 1797, during what has been called “The Last Invasion of Britain,” French Revolutionary forces crossed the North Sea and faced the British at the Battle of Fishguard, which wasn’t really a battle at all. Having previously landed successfully a few miles west of Fishguard with nearly 20 boatloads of troops, 47 barrels of powder, and 50 tons of cartridges and grenades, the French were ready to take the town.France’s Commodore Castagnier sent a single French ship to reconnoiter the bay while flying the British colors. As soon as the ship was spotted by the British, they fired a single blank from a 9-lb gun. While the port had eight of these large cannons, they were severely understocked and had only three rounds. The French ship immediately hoisted the French colors and fled the bay. The British may have fired the cannon to signal the ship in some way, but regardless of their intention, they caused the French to reconsider their target and turn away from Fishguard. Had they not fired the initial blank to bluff the French scout ship, the port would likely have been taken.Trojan Coffin. The Normans, Castle SiegeMany stories of the fabled 11th-century Norwegian King Harald Hardrada have been told throughout the years, detailing his bravery and ingenuity at combat. During his conquest on the road to becoming the king of Norway, Harald laid siege to an unnamed castle by camping outside and establishing his men for the upcoming battle. He also had erected a small tent a ways outside the main camp, where he lay sick and possibly dying. Before any battle took place, it was reported that the great king had perished from his illness, and his men ventured toward the castle to tell the news of their commander’s demise. They addressed a large gathering of priests and requested that they allow their fallen commander to be buried within the city.The priests believed that they would receive rich gifts for accommodating the bereaved fighting men and acquiesced. They formed a large procession and took Harald’s ornate coffin into their castle, along with a small group of his men. Once they’d crossed the threshold and entered the castle grounds, Harald’s men immediately barred the gate, called the remaining men to battle, and the good King Harald himself leaped from the coffin and declared that everyone be killed. The castle was taken, and Harald’s legendary exploits continued toward the conquest of England.Elaborate Hoax: Union Army, Reclamation Of The Indianola, US Civil WarAfter losing one of its most prized ships, the recently constructed ironclad USS Indianola, the Union Navy conducted the most successful hoax operation of the US Civil War. The Indianola was a considerably formidable vessel, though it was plagued with problems during its construction, and it saw several successful combat operations.Attempting to pass the city of Vicksburg, the ship engaged in a battle against the Confederate Webb, which rammed the vessel, causing its starboard wheel and rudder to become inoperable. As the ship began to take on water, its captain, Lieutenant Commander George Brown, ordered it run ashore, where he quickly dumped the Union codebooks and surrendered to prevent a greater loss of life. The Confederates moved the Indianola to the eastern bank of the Mississippi and established a 100-man salvage crew accompanied by two pieces of field artillery in an attempt to salvage the valuable vessel.Deciding to attempt a recovery operation, Rear Admiral David D. Porter ordered that an old coal barge be made to look like a larger ironclad intent on taking the Confederates: “It was built of old boards in twelve hours, with porkbarrels on top of each other for smoke-stacks, and two old canoes for quarter-boats; her furnaces were built of mud, and only intended to make black smoke and not steam. Painted on the side was the taunting slogan: ‘”Delueded Rebels, cave in!” To ensure that the Confederates saw the vessel approaching, he launched it in broad daylight toward the Confederate defenses.Seeing the “formidable vessel” approaching, the salvage crew first attempted to raise the Indianola before finally deciding to blow its magazines, scuttling the ship. The Indianola was eventually resurfaced and returned to the North toward the end of the war.Fraudulent Document: Sultan Baybars, Capture Of Krak Des Chevaliers, The CrusadesSometimes all it takes is a well-executed bluff to confuse and capture the enemy. During the Crusades, following more than a year of what can only be described as a peaceful siege, wherein Sultan Baybars’s (also spelled Baibars) army camped outside the castle of Krak des Chevaliers, using its resources without engaging, the time had come to engage the formidable fortress.The castle was built to withstand long sieges. Its fortifications were almost twice the size of that of some European castles, and it featured a large moat, high walls, and a gate accessible only by a long, winding passage. While the sultan had a superior fighting force, which had successfully stood against the Mongols and won, the Hospitaller stronghold had the advantage of fortitude, and the fight would certainly be a bloody and costly one. Knowing this, Sultan Baybars, who by all accounts was a brilliant tactician, retreated and devised a plan that involved a single sheet of paper.Baybars finally got to implement his plan in the most spectacular way in 1271 during the Eighth Crusade, when he delivered a letter to his enemy—from his enemy. After a ten-day siege that took down a portion of the outer wall of the castle, a letter drafted from the leader of the Hospitaller ordered the men inside the castle to surrender. The knights immediately capitulated and followed the orders of their leader by sending a party out to meet the sultan and arrange conditions for their surrender. The deception worked, and the castle was taken without the need for further siege or bloodshed, all due to a falsified signature at the bottom of a piece of paper.Feigned Retreat: The Normans, Battle Of Hastings, Norman ConquestThe Norman Conquest of England in 1066 is a hotly debated battle in many historical circles. There is no consensus as to whether William II of Normandy, later called William the Conqueror, initiated a feigned retreat or an actual one. Whether or not the decision to withdraw his cavalry was made by William to engage the British doesn’t matter when you consider that no other feigned retreat has been as successful before or since that battle nearly 1,000 years ago.During the battle, the British shield wall was established by the best men available and continuously held the line against the onslaught of William’s cavalry until finally, the cavalry turned and fled. As they withdrew from the shield wall, the men holding the line broke and followed them in one of the biggest blunders in military history. As they engaged, the cavalry—now able to hold their ground against a sparse force without horses—quickly fell back on their pursuers and devastated their ranks. Simultaneously, the remaining forces were engaged, and due to their weakened lines, they were quickly destroyed. The successful feigned retreat by the cavalry won the battle and brought about the end of Anglo-Saxon rule in England.Baiting An Attack. US Army, Vietnam WarOftentimes, the best deception operations are carried out due to accurate and timely intelligence that helps commanders to make decisions to thwart an enemy’s attack. Other times, this information has been used to bait an attack so that a counterattack can be implemented to achieve a positive result for the defensive force. This occurred during the Vietnam War, when the commanders of the 2nd Battalion, 27th Infantry Division, learned through intelligence that the North Vietnamese Army (NVA) and elements of the People’s Army of Vietnam (PAVN) were planning to attack an unnamed firebase as a test or probing operation.Knowing this, the Americans established Diamond I Firebase 25 kilometers (16 mi) outside of Tay Ninh, an area that would make it enticing to attack. They placed ground sensors throughout the base and also reinforced it with a signNow amount of artillery. The result: “Rather than the PAVN and NVA regiment having an easy battle, it was twice repulsed [and] suffered heavy casualties.” The attack took place on February 24, 1969, and cost the Vietnamese 118 soldiers and two captured.Wolves In Sheep’s Clothing: British Royal Navy, World War IDuring World War I, the German Navy maintained a highly successful fleet of U-boats (aka Unterseeboots) that operated in the Atlantic Ocean. While submarines were technically invented and used as early as the US Civil War, they did not see widespread use in naval combat until 1914, and the Germans were quite adept at being sneaky under the sea. The biggest problem that a surface vessel faced during this time was a complete inability to locate a U-boat. Sonar was developed very early in the war, but it wasn’t anywhere near as effective or efficient as it is today, so navies like the British and French utilized hydrophones, which had a short range and weren’t very effective if a U-Boat’s crew was well-trained and quiet.Because of this, Q-boats were established. These were heavily armed vessels of all sorts that were “dressed” as merchant ships. Their job was to sail the seas and entice the U-boats to surface and attack only to find that their “prey” was much more skilled at defense than they originally thought. To further sell the deception, the ships would fly false colors would be flown, and when a U-boat approached, part of the crew, known as the “panic party,” would appear to abandon the ship. Once the submarine was in range, hidden guns were revealed, the White Ensign (the flag of the Royal Navy) raised, and the U-boat was sunk.The use of Q-boats led to the sinking of ten U-boats, so it was successful, although most of its success came by forcing Germany to completely change how it conducted naval warfare—albeit too late for them to effectively win the war.Left Hook: US And Allied Forces, Operation Desert StormOperation Desert Storm saw one of the most successful uses of deception via radio signals ever employed in warfare. The Iraqis’ attention was on an amphibious training maneuver by the United States Marine Corps, leading them to strongly believe that the Americans would invade along their coastline. They subsequently prepared for this eventuality.Additionally, the 18th and 5th Corps Headquarters began their maneuvers through the desert in a massive flanking maneuver known as a “left hook,” where they were able to effectively outflank the Iraqis and attack while also blocking any avenue of retreat back into Iraqi territory from Kuwait. During these maneuvers, the Corps’s signals units broadcasted mimicked signals, which effectively made the Iraqis believe that the units were completely stationary.As the units continued to move toward the Iraqi lines, the Iraqi forces moved away from them toward the coastline in order to repel their invaders. The result was a ground war that lasted only three days and caused the Iraqis to completely withdraw from Iraqi-occupied Kuwait. Most of their army surrendered to the Americans and Allied troops who had cut off their escape. After 100 hours of combat on the ground, President Bush declared a cease-fire and the successful liberation of Kuwait on February 27, 1991.False Flag: Germany, Operation Himmler, World War IIFollowing Germany’s successful expansion into the neighboring countries of Austria and Czechoslovakia in 1938 and 1939, Hitler needed to continue to create Lebensraum (“Living Space”) for his idealized expansion of Germany. Hitler knew that he couldn’t easily get away with such expansion into the likes of Poland without the rest of the world raising a eyebrow, so he devised a false flag operation to allow for his entrance into the bordering nation.Along the border town of Gleiwitz, several Jews were taken from a concentration camp and dressed in German border guard uniforms. They were taken to a nearby radio tower in Germany and shot and killed just outside the border of Poland. This action, which could become known as the Gleiwitz incident, along with 20 other less serious matters, were then used by the fuhrer’s propaganda campaign to forward his cause to take Poland.Hitler immediately cited Polish aggression and invaded Poland on September 1, 1939, saying, “This night for the first time Polish regular soldiers fired on our own territory. Since 5:45 AM, we have been returning the fire [ . . . ] I will continue this struggle, no matter against whom, until the safety of the Reich and its rights are secured.” While it is certainly true that German aggression was ongoing up to this point, the war can be said to have officially begun with the invasion of Poland, since two days following the attack, Great Britain and France declared war on Germany.SOURCES:The Greatest Deceptions in Military HistoryAmazing And Successful Military Deception OperationsMilitary Deception Tactics of the World Wars | Historical Spotlight | News | WargamingLatimer, John: “Military deception in war” Download the book for free here http://www.lander.odessa.ua/doc/...Surprise Attacks That Changed HistoryPhotos: The Department of History, United States Military Academy /Public Domain
Create this form in 5 minutes!
How to create an eSignature for the us coast guard small arms range sheet
How to generate an eSignature for your Us Coast Guard Small Arms Range Sheet in the online mode
How to create an eSignature for your Us Coast Guard Small Arms Range Sheet in Google Chrome
How to create an electronic signature for putting it on the Us Coast Guard Small Arms Range Sheet in Gmail
How to make an electronic signature for the Us Coast Guard Small Arms Range Sheet right from your mobile device
How to make an electronic signature for the Us Coast Guard Small Arms Range Sheet on iOS
How to create an electronic signature for the Us Coast Guard Small Arms Range Sheet on Android devices
People also ask
-
What is Cg 3029 and how does it relate to airSlate SignNow?
Cg 3029 refers to a specific feature set within airSlate SignNow that enhances document management and e-signature capabilities. This designation encompasses the tools and functionalities designed to streamline workflows and improve efficiency in signing documents electronically.
-
Is there a pricing plan for Cg 3029 with airSlate SignNow?
Yes, airSlate SignNow offers competitive pricing plans that include access to the features associated with Cg 3029. These plans are designed to be cost-effective, allowing businesses of all sizes to utilize advanced document signing solutions without breaking the bank.
-
What features are included in Cg 3029 on airSlate SignNow?
Cg 3029 includes a range of features such as customizable templates, secure e-signatures, and advanced document tracking. These features are designed to enhance user experience, ensuring that businesses can efficiently manage their document workflows.
-
How can Cg 3029 benefit my business?
The Cg 3029 features in airSlate SignNow can signNowly boost your business's productivity by simplifying the document signing process. With these tools, you can reduce turnaround times, improve accuracy, and enhance collaboration among team members.
-
Does airSlate SignNow integrate with other software when using Cg 3029?
Absolutely! Cg 3029 on airSlate SignNow seamlessly integrates with various software applications, including CRMs, project management tools, and cloud storage solutions. This integration capability allows for a more cohesive workflow across different platforms.
-
Is Cg 3029 suitable for small businesses?
Yes, Cg 3029 is particularly advantageous for small businesses looking for an affordable yet powerful e-signature solution. With its user-friendly interface and cost-effective pricing, small businesses can easily implement Cg 3029 to streamline their document processes.
-
What security measures are in place for Cg 3029 users?
airSlate SignNow takes security seriously, especially for users utilizing Cg 3029. The platform employs advanced encryption, secure cloud storage, and compliance with industry standards to ensure that your documents remain safe and confidential.
Get more for Cg 3029
Find out other Cg 3029
- How To Electronic signature Nevada Acknowledgement Letter
- Electronic signature New Jersey Acknowledgement Letter Free
- Can I eSignature Oregon Direct Deposit Enrollment Form
- Electronic signature Colorado Attorney Approval Later
- How To Electronic signature Alabama Unlimited Power of Attorney
- Electronic signature Arizona Unlimited Power of Attorney Easy
- Can I Electronic signature California Retainer Agreement Template
- How Can I Electronic signature Missouri Unlimited Power of Attorney
- Electronic signature Montana Unlimited Power of Attorney Secure
- Electronic signature Missouri Unlimited Power of Attorney Fast
- Electronic signature Ohio Unlimited Power of Attorney Easy
- How Can I Electronic signature Oklahoma Unlimited Power of Attorney
- How Do I Electronic signature South Carolina Unlimited Power of Attorney
- How Can I Electronic signature Alaska Limited Power of Attorney
- How To Electronic signature Massachusetts Retainer Agreement Template
- Electronic signature California Limited Power of Attorney Now
- Electronic signature Colorado Limited Power of Attorney Now
- Electronic signature Georgia Limited Power of Attorney Simple
- Electronic signature Nevada Retainer Agreement Template Myself
- Electronic signature Alabama Limited Partnership Agreement Online