Police Report San Diego Form


What is the Police Report San Diego
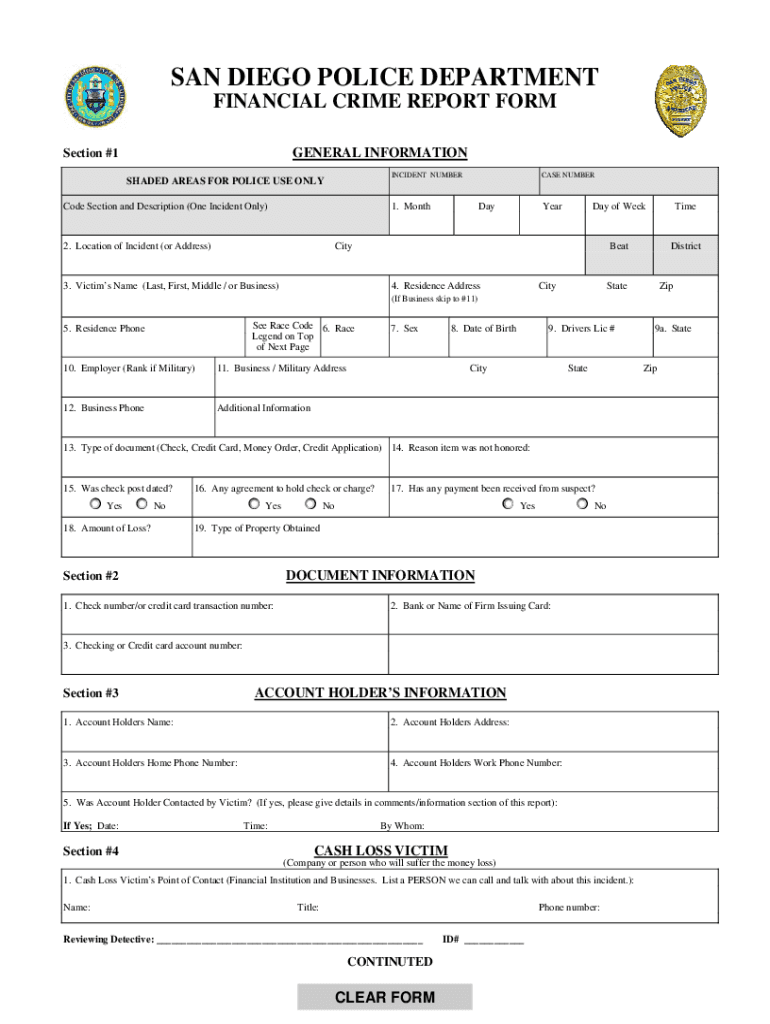
The San Diego police incident report is a formal document created by law enforcement to record details about a specific incident, such as a crime or traffic accident. It serves as an official account of events and includes vital information such as the date, time, location, and nature of the incident. Additionally, it may contain statements from witnesses, descriptions of involved parties, and any evidence collected. This report is crucial for investigations, legal proceedings, and public records.
How to Obtain the Police Report San Diego
To obtain a San Diego police incident report, individuals can request it through the San Diego Police Department. This can typically be done online, by mail, or in person. When making a request, it is essential to provide specific details about the incident, such as the case number, date, and location. There may be a nominal fee associated with obtaining the report, and processing times can vary based on the department's workload and the complexity of the request.
Steps to Complete the Police Report San Diego
Completing a San Diego police incident report involves several steps to ensure accuracy and thoroughness. First, gather all relevant information, including the incident details and any witness statements. Next, fill out the report form, ensuring that all sections are completed clearly and concisely. It is important to review the report for any errors before submission. Once completed, submit the report to the appropriate department, either online or in person, depending on the guidelines provided by the San Diego Police Department.
Key Elements of the Police Report San Diego
A San Diego police incident report typically includes several key elements that provide a comprehensive overview of the incident. These elements often include:
- Date and Time: When the incident occurred.
- Location: The precise location of the incident.
- Involved Parties: Names and contact information of victims, suspects, and witnesses.
- Description of Incident: A narrative detailing what transpired.
- Evidence Collected: Any physical evidence or documentation related to the incident.
- Officer Information: The name and badge number of the responding officer.
Legal Use of the Police Report San Diego
The San Diego police incident report serves various legal purposes. It can be used as evidence in court proceedings, aiding in criminal cases or civil litigation. Additionally, the report may be referenced during investigations by law enforcement and can be crucial for insurance claims related to accidents or damages. Understanding the legal implications of the report is important for all parties involved, as it may impact the outcome of legal matters.
Examples of Using the Police Report San Diego
There are several scenarios in which a San Diego police incident report may be utilized. For instance, if an individual is involved in a traffic accident, they may need the report to file an insurance claim. In cases of theft or vandalism, the report can support claims made to insurance companies or assist in police investigations. Additionally, the report may be used by legal representatives to build a case for clients involved in criminal proceedings. Each of these examples highlights the report's importance in both personal and legal contexts.
Quick guide on how to complete san diego police department financial crimes unit form
Complete Police Report San Diego effortlessly on any device
Digital document management has gained popularity among businesses and individuals alike. It serves as an ideal eco-friendly alternative to conventional printed and signed documents, allowing you to access the necessary forms and securely store them online. airSlate SignNow equips you with all the tools necessary to create, modify, and eSign your documents swiftly without any delays. Handle Police Report San Diego on any platform using airSlate SignNow's Android or iOS applications and enhance any document-related process today.
How to modify and eSign Police Report San Diego with ease
- Locate Police Report San Diego and click Get Form to begin.
- Utilize the tools at your disposal to complete your document.
- Emphasize important sections of your documents or conceal sensitive information using tools specifically designed for that purpose by airSlate SignNow.
- Generate your eSignature with the Sign tool, which only takes a few seconds and carries the same legal significance as a traditional ink signature.
- Review the details and click on the Done button to finalize your changes.
- Choose your desired method of delivering your form, whether it's through email, text message (SMS), an invitation link, or by downloading it to your computer.
Eliminate the hassle of lost or misplaced documents, tedious searches for forms, and errors that necessitate reprinting new copies. airSlate SignNow meets your document management needs in just a few clicks from any device of your choice. Modify and eSign Police Report San Diego while ensuring clear communication throughout your document preparation journey with airSlate SignNow.
Create this form in 5 minutes or less
FAQs
-
How do I get a good sample of people, only from specific cities like Los Angeles, New York, or San Diego, to vote on my online poll or fill out my short survey online?
What about posting in their local Craigslist?
-
How does one run for president in the united states, is there some kind of form to fill out or can you just have a huge fan base who would vote for you?
If you’re seeking the nomination of a major party, you have to go through the process of getting enough delegates to the party’s national convention to win the nomination. This explains that process:If you’re not running as a Democrat or Republican, you’ll need to get on the ballot in the various states. Each state has its own rules for getting on the ballot — in a few states, all you have to do is have a slate of presidential electors. In others, you need to collect hundreds or thousands of signatures of registered voters.
-
How common is it for US police departments to have an intelligence unit, like in Black Klansman, that monitors the local community's reaction and mood even when a crime hasn't occurred?
Law enforcement intelligence is a growing field. If your agency has to comply with 28 CFR Part 23, you have to have reasonable suspicion of criminal activity to retain information though. You don't need a crime report to tie them to, but you need to have some reason to believe there is some kind of a tie to crime.Home Page 28CFR Program
-
What forms do I need to fill out to sue a police officer for civil rights violations? Where do I collect these forms, which court do I submit them to, and how do I actually submit those forms? If relevant, the state is Virginia.
What is relevant, is that you need a lawyer to do this successfully. Civil rights is an area of law that for practical purposes cannot be understood without training. The police officer will have several experts defending if you sue. Unless you have a lawyer you will be out of luck. If you post details on line, the LEO's lawyers will be able to use this for their purpose. You need a lawyer who knows civil rights in your jurisdiction.Don't try this by yourself.Get a lawyer. Most of the time initial consultations are free.
-
How did you go to start your journey to the United States? What forms did you fill out? How long did it take? My best friend wants to come here and I will help him until he gets his green card.
I worked hard at school to get good grades, went to university, studied hard, graduated, got a series of better and better jobs, and finally transferred across as an international manager under an L1-A visa (executive management).After a year my lawyer submitted my green card paperwork, and a few months later I was approved.Your friends experience may differ - there are MANY ways of ending up with a green card - hard work, education, and business success is one of the easiest, but not the only way.You can be lucky (diversity lottery), rich (investment), talented (internationally recognised artists, athletes and scientists), or have family in the USA.ALL these options require you to either pay a lawyer, or actually learn the process yourself.Your friend should start by obtaining a visa which allows them to legally reside and work in the USA - that’s the first step in the process.Simply “wanting to come to the USA” isn’t enough - it’s a start. Now your friend needs to learn the process and apply themselves.U.S. Visas
-
What’s the title of a person who can take a complex Excel spreadsheet and turn it into a user friendly, intuitive form that’s easy to fill out? How can I hire someone with those skills? It contains , financial, quoting & engineering data.
Look for an SaaS developer, someone with JavaScript, PHP, and MySQL skills to create Cloud-hosted browser-based forms and reports who also has a modicum of financial analysis background.Dumping obsolete Excel client server architecture as soon as you can will be the best thing you can do to bring your operation into the 21st Century.
-
How do the police build a criminal case against you?
Since I was a2a, how a case is built is dependent upon the type of crime (fraud, drug trafficking, money laundering, violence, etc.). Discovery of fraud generally involves a report of suspicious activity, a victim’s report, or review of records. Fraud investigations are primarily conducted through collection of pertinent financial records, identifying those involved and their documented activities. Fraud commonly involves a convoluted manipulation of circumstances that requires extensive knowledge of law and applicable regulations.Drug trafficking and associated money laundering generally involve informant information, with the informant commonly being someone arrested for an observed drug violation who turns on their confederates in order to limit their own punishment. That process could lead to an undercover operation and/or involve extensive surveillance of suspects, identification of drug and money stash locations, trash collection at identified locations, and collection of sufficient information to establish probable cause for a search warrant (http://www.quora.com/What-constitutes-probable-cause-for-a-police-officer-to-be-able-to-search-a-car-without-a-warrant/answer/Dan-Robb-2). The search warrant could lead to recovery of evidence, identification of suspects, and seizure of illegal substances or large quantities of currency for which there is no viable explanation.Investigations of crimes against persons are commonly initiated based on a report of what is claimed to be criminal behavior by a witness. The next common step involves interviews indicating where evidence may reside or where other witnesses may be located. Such information is evaluated and corroborated if possible; in that not even all eyewitness testimony is reliable (Robb, 2011). Crime scenes are identified and search is initiated, based either on immediate probable cause or through search warrants. Evidence is collected if possible, then processed for possible identification of suspects (e.g., DNA and/or fingerprints identifiable from data bases of prior offenders, or for comparison with future suspects), and indicators of events are theorized (e.g., accidental versus criminal actions).If no suspects are identifiable, or even if there are possible suspects, how the crime was committed may provide clues linking that crime to a past suspect or past crimes, even without physical evidence with regard to a suspect; or, if a serious crime, investigation may involve more extensive evaluation in a criminal profiling process:Modus Operandi and SignatureD. RobbCMRJ531In 1838, Sir Frederick Roe, a magistrate in London, argued for the employment of specialized police officers to detect crimes (as cited in Dilnot, 1927). The successes of the privately employed Bow Street Runners were cited as an example of the historical presence of recognizing modus operandi, and what could be interpreted as recognition of the value of criminal profiling.Sir Peter Laurie, a City magnate, was positive that the Metropolitan Police could not supersede the runners. ... "These men have been thief catchers all their lives, and know almost every thief in London, and of what he is capable. ... If you take them to a house, and show them that a robbery has been committed, they will tell you directly, by inspection, whether it has been done by an old or by an inexperienced thief." (as cited in Dilnot, 1927, p. 53)Holmes and Holmes (2002), in my opinion, do not adequately address the concepts of Modus Operandi (MO) and Signature. Therefore, further information is provided here. MO is not a new concept. Dilnot stated that "'Modus operandi' is obviously as old as detective work itself" (1927, p. 212). Dilnot did not comment of the exact origins of the position of detective, but he did say that detectives were employed by the Metropolitan Police, under the British Home Secretary, prior to 1845. The daguerreotype photographic process was patented in Europe in 1840, and,had come to America soon afterwards. ... None was more enthusiastic for this medium than Alan Pinkerton. Within a few years he had built up an impressive Rogues Gallery of mugshots and circulated copies of photographs to lawmen all over the country, together with detailed descriptions of physical features, dress, habits, mental characteristics, criminal specialties and mode of operation. (Mackay, 2007, p. 93)Pinkerton (1819-1884), a Scotch immigrant barrel maker and former Deputy Sheriff, headed the de facto national investigative agency (albeit private) in the U.S. during the pre- and post-Civil War era. The emergence of this private agency was apparently due the emergence of interstate commerce (i.e., railroads); the lack legal jurisdiction outside of the city, count, or state; an aversion to central governmental control; parochial thinking; and governmental financial considerations. In 1861, Pinkerton sent a letter to President Lincoln:I have in my Force from Sixteen to Eighteen persons on whose Courage, Skill and Devotion to their country I can rely. If they with myself at the head can be of service in the way of obtaining information of the movements of Traitors, or Safely conveying your letters or dispatches, on that class of Secret Service which is the most dangerous, I am at your command. (as cited in Mackay, 2007, p. 107)Fosdick (1915/1969), a former New York City Commissioner of Accounts, conducted one of the first cross-cultural studies of policing during 1913 and 1914. He was complimentary of the German system of criminal investigation, particularly with regard to the scholarly efforts of Dr. Hans Gross, an academic and criminal justice practitioner. Many European police agencies employed relatively sophisticated criminal classification and referencing systems, to the extent that in some countries, all foreigners were required to record their travels with the local police or face legal sanction. The use of dactyloscopy (fingerprinting) began for Scotland Yard in 1901, after use by English officials in India. And, classification of offenders according to method of operation (MO) by Scotland Yard was begun officially in 1896. However, at the request of London authorities in 1888, Dr. Thomas Bond was apparently cognizant of the concept based on his assessment of the crimes attributed to Jack the Ripper, based on his statement thatall five murders were no doubt committed by the same hand. … All the circumstances surrounding the murders lead me to form the opinion that the women must have been lying down when murdered. …In each case the mutilation was implicated by a person who had no scientific nor anatomical knowledge. …A man subject to periodical attacks of Homicidal and Erotic mania. The murderer in external appearance is quite likely to be a quiet inoffensive looking man, probably middle-aged and neatly and respectfully dressed. He would be solitary and eccentric in his habits, also he is most likely to be a man without regular occupation, but with a small income or pension. (as cited in Kocsis, 2006, p. 4)MO was at that time primarily used for burglary and theft crimes. Fosdick related:What is probably the most ambitious plan of crime classification by methods has been initiated in ... England. ... The so-called "M.O." or Modus Operandi system devised by Major L. W. Atcherley, Chief Constable of the West Riding of Yorkshire Constabulary.His system is more than an index for a single department. It is a cooperative arrangement by which habitual or traveling criminals can be traced from community to community by a comparison of their methods of work. (1915/1969, p. 344)Atcherley's system included 10 categories, and the tenth is somewhat consistent with the concept of signature:1—Classword; kind of property attacked, whether dwelling house, lodging house, hotel, etc.2—Entry; the actual point of entry, front window, back window, etc.3—Means; whether with implements or tools, such as a ladder, jimmy, etc.4—Object; kind of property taken.5—Time; not only time of day or night, but whether church time, market day, during meal hours, etc.6—Style; whether criminal to obtain entrance describes himself as mechanic, canvasser, agent, etc.7—Tale; any disclosure as to his alleged business or errand which the criminal may make.8—Pals; whether crime was committed with confederates, etc.9—Transport; whether bicycle or other vehicle was used in connection with crime.10—Trademark; whether criminal committed any unusual act in connection with crime, such as poisoning a dog, changing his clothes, leaving a note for the owner, etc. (Fosdick, 1915/1969, p. 346)MO and Signature are similar and may be easily confused, one for the other. MO involves those behaviors necessary for the successful commission of a crime; incorporating three elements: 1) success of the crime; 2) protection of identity; and, 3) successful escape (Gee & Belofastov, 2007).Signature is an aspect of a crime that fulfills an emotional need, which is not necessarily conscious. Signature could involve intentional crime scene configuration or taking of souvenirs, and generally remains consistent, due to the emotional element; or, may be as elemental as words used or the order in which acts are committed (Holmes & Holmes, 2002). Although, some variations of Signature can be expected, based on the recognition that each independent crime is subject to numerous influences (e.g., unexpected interruption, time constraints, physical limitations) (Douglas, Burgess, Burgess, & Ressler, 1992; Douglas & Olshaker, 1995; Turvey, 2001).Douglas et al. indicated that “signature does not always show up in every crime because of contingencies that might arise, such as interruptions or an unexpected victim response” (1992, p. 261). Turvey (2001) referred to this concept as the “X-factor,” unexpected events at the crime scene that may eliminate MO and Signature.MO is more affected by evolution and refinement, in response to environmental stimuli. For example, if one gets too close to being caught, one will probably improve their methods in the future. Or, as in the “DC Sniper” case, the press commented upon the fact that the shooter had targeted only adults, which was of course followed by the shooting of a young boy. And then, press statements highlighted the lack of demands by the DC Sniper, followed by demands from these spree killers for a large sum of money.Douglas and Olshaker (Douglas being a retired Federal Bureau of Investigation profiler) provided the following discussion of MO vs. Signature, and staging versus posing:The differences between MO and signature can be subtle. … (A) robber … made …captives undress, posed them in sexual positions, and took photographs…. That’s his signature. It was not necessary or helpful to the commission of a bank robbery.” Another robber forced disrobing “so the witnesses would be so preoccupied … that they … couldn’t make a positive ID. … This was MO. (1995, pp. 253-255)In a serial murder case, the defendant’s lawyer “was trying to show that it was unlikely these crimes were all committed by the same individual because so many details of the modus operandi varied. I made it clear that regardless of the MO, the common denominator in each of the murders was physical, sexual, and emotional torture. … So, though the methods of torture varied—the MO, if you will—the signature was the pleasure he received out of inflicting the pain” (Douglas & Olshaker, 1995, p. 255).Staging is an element of MO and involves placement or manipulation of a crime scene to mislead investigators, “such as when a rapist tries to make his intrusion look like a routine burglary” (Douglas & Olshaker, p. 256). Posing, (also) an element of signature, is infrequent and involves “treating the victim like a prop to leave a specific message. … These are crimes of anger, crimes of power(,) … it is the thrill of … beating the system” (p. 256).The Signature is sometimes referred to as a “calling card” or trademark of the offender, such as by Douglas et al. (1992). However, stating that the Signature is a calling card is inappropriate in my opinion. Such a label leads to the inference that it is an intentional act on the part of the perpetrator to mark the crime as his own; this may not be the case, since the perpetrator may not be conscious of the significance of the act and oblivious to how the evidence of his behavior will appear. Turvey (2001) also disagreed with such a label because crimes and the resulting crime scenes are inherently chaotic with numerous variables; therefore, a precise match of Signature and MO is unlikely. In addition, Turvey noted that interpretation of evidence may be faulty due to misinterpretation or destruction of evidence (intentional or accidental), leading to faulty conclusions.Signature and MO may be difficult to differentiate, and may even be indistinguishable in a crime scene. However, the concepts must be separated and the characteristics of each must be articulated.CR531 Criminal ProfilingD. L. RobbProfessor Comments Week 1Very few people would argue against the idea that the ways in which we present and maintain ourselves, our homes, and our workspaces reflect some very important aspects of our personalities. Certainly, from our studies in the humanities, archeology and anthropology, we know that even in the absence of a written history, the depictions of art, music, clothing, household artifacts, and architecture developed and left behind by a long-dead society can still clearly tell us a great deal about the beliefs, attitudes and lifestyles of its inhabitants. Similarly, it is the contention of practitioners of Criminal Profiling, that the actual commission of crimes may also reflect key personality and lifestyle characteristics of those who committed the crimes.The commission of a crime requires that the offender make a series of choices, decisions, responses, and reactions. The resulting dynamics of the crime, as revealed through crime scene investigation, will then necessarily reflect the intelligence, competence, composure, experience, needs, wants, fantasies, motivation, and many other key characteristics of the offender’s personality. This has probably been obvious to those charged with finding and apprehending offenders from the outset of such positions. …Profiling is rooted in the belief that an offender’s thinking directs the offender’s behavior. If the crime scene reveals to us the offender’s behavior, we should be able to examine the scene to make some assumptions about the offender’s thinking. “Elementary,” as Sherlock might say, probably not. Profiling is a complex function that requires investigative experience and insights gained from years of exposure to various crimes, individuals, and personality types.Criminal profiling is a criminological/sociological, psychological, biosociological, and forensic analysis process that attempts to make investigative sense of apparent crime scene dynamics, in order to gain an understanding of behavior, motivation characteristics of offenders, and personality. Profilers analyze the totality of the known crime circumstances, make inferences of offender behavior from that analysis, and create a profile of the offender based on inferences of the offender's behavior (what would appear to be inferences based on inferences).Profiling is, in fact, a form of retroclassification, or classification that works backward. Profilers recognize crime scene dynamics that are associated to criminal personality types who commit similar offences. Typically we classify a known entity into a discrete category, based on presenting characteristics that translate into criteria for assignment to that category. (Douglas, Burgess, Burgess, & Ressler, 2006, p. 97)In this course, you will be prompted to examine the research on criminal profiling. We will try to make sense of these acts of violence, which so often confront us in our contemporary life, and cull out of the acts, some comprehensible threads that will permit us to find similarities amongst offenders’ personalities and to formulate a rationale for the differences between them, as well. However, as we continue our inquiries into the field, we will discover that, as in almost all studies of human behavior, the discipline is filled with contradictory theories, opposing beliefs about the best way to study and construct criminal profiles, and many social, legal, and ethical issues that must be considered.References:Dilnot, G. (1927). The story of Scotland Yard. New York: Houghton Mifflin.Douglas, J. E., Burgess, A. W., Burgess, A. G., & Ressler, R. K. (Eds.). (2006). Crime classification manual: A standard system for investigating and classifying violent crimes (2nd ed.). San Francisco: Josey-Bass.ReferencesDilnot, G. (1927). The story of Scotland Yard. New York: Houghton Mifflin.Douglas, J. E., Burgess, A. W., Burgess, A. G., & Ressler, R. K. (1992). Crime classification manual: A standard system for investigating and classifying violent crimes. San Francisco: Josey-Bass.Douglas, J., & Olshaker, M. (1995). Mind hunter: Inside the FBI’s elite crime unit. New York: Pocket Books.Fosdick, R. B. (1969). European police systems. Montclair, NJ: Patterson Smith. (Original work published 1915)Gee, D., & Belofastov, A. (2007). Profiling sexual fantasy: Fantasy in sexual offending and the implications for criminal profiling. In R. N. Kocsis (ed.). Criminal profiling: International theory, research, and practice. Totowa, NJ: Humana Press.Holmes, R. M., & Holmes, S. T. (2002). Profiling violent crimes: An investigative tool (3rd ed.). Thousand Oaks, CA: Sage Publications.Kocsis, R. N. (2006). Criminal profiling: Principles and practice. Totowa, NJ: Humana Press.Mackay, J. (2007). Allan Pinkerton: The first private eye. Edison, NJ: Castle Books.Turvey, B. E. (2001). Criminal profiling: An introduction to behavioral evidence analysis (2nd ed.). San Diego, CA: Elsevier Academic Press.Once sufficient evidence is collected and corroborated to the extent thought necessary by investigators, the case is presented to prosecutors who assess the evidence with regard to the necessity for proving the allegation beyond a reasonable doubt in court. Additional investigation may be requested, prosecution may be declined, or accepted for prosecution.Reference:Robb, D. L. (2011, November). Eyewitness identification in photographic lineups: A case study. Presented at the Texas Association for Investigative Hypnosis Training Conference, November 2011. Retrieved from: https://www.academia.edu/2662993...
Create this form in 5 minutes!
How to create an eSignature for the san diego police department financial crimes unit form
How to generate an eSignature for the San Diego Police Department Financial Crimes Unit Form in the online mode
How to generate an electronic signature for the San Diego Police Department Financial Crimes Unit Form in Google Chrome
How to create an electronic signature for signing the San Diego Police Department Financial Crimes Unit Form in Gmail
How to generate an electronic signature for the San Diego Police Department Financial Crimes Unit Form straight from your smartphone
How to create an eSignature for the San Diego Police Department Financial Crimes Unit Form on iOS devices
How to create an eSignature for the San Diego Police Department Financial Crimes Unit Form on Android OS
People also ask
-
What is a Police Report San Diego and how can I obtain one?
A Police Report San Diego is an official document created by law enforcement that details incidents, arrests, or accidents. To obtain a Police Report San Diego, you can request it online or visit the local police department in person. Using airSlate SignNow, you can easily eSign any required forms to streamline the process.
-
How does airSlate SignNow facilitate obtaining a Police Report San Diego?
airSlate SignNow simplifies the process of obtaining a Police Report San Diego by allowing you to eSign necessary documents quickly and securely. Our platform ensures that your requests are processed efficiently, minimizing the time spent on paperwork. This way, you can focus on more important matters while we handle the documentation.
-
What features does airSlate SignNow offer for managing Police Reports in San Diego?
With airSlate SignNow, you can easily manage your Police Reports in San Diego through our intuitive eSigning and document management features. You can send, receive, and store your reports securely, all in one platform. Additionally, our user-friendly interface allows you to track the status of your requests effortlessly.
-
Is airSlate SignNow a cost-effective solution for handling Police Reports San Diego?
Yes, airSlate SignNow is a cost-effective solution for handling Police Reports San Diego. We offer competitive pricing plans that cater to both individual users and businesses. By using our platform, you can reduce costs associated with paper handling and streamline your workflows.
-
Can I integrate airSlate SignNow with other tools for processing Police Reports San Diego?
Absolutely! airSlate SignNow integrates seamlessly with various applications and tools commonly used for processing Police Reports San Diego. Whether you need to connect with your existing CRM or document management system, our integrations facilitate a smoother workflow and enhance your overall efficiency.
-
What benefits can I expect from using airSlate SignNow for Police Reports San Diego?
Using airSlate SignNow for Police Reports San Diego offers numerous benefits, including increased efficiency, reduced paperwork, and enhanced security. Our platform allows for quick eSigning and document sharing, ensuring that you receive your reports faster. Plus, our robust security measures protect your sensitive information throughout the process.
-
How secure is the eSigning process for Police Reports San Diego with airSlate SignNow?
The eSigning process for Police Reports San Diego with airSlate SignNow is highly secure, utilizing advanced encryption and authentication protocols. We prioritize the safety of your documents and personal information, ensuring compliance with legal standards. You can trust our platform to handle your sensitive reports with care.
Get more for Police Report San Diego
Find out other Police Report San Diego
- How Do I eSign New Mexico Healthcare / Medical Word
- How To eSign Washington High Tech Presentation
- Help Me With eSign Vermont Healthcare / Medical PPT
- How To eSign Arizona Lawers PDF
- How To eSign Utah Government Word
- How Can I eSign Connecticut Lawers Presentation
- Help Me With eSign Hawaii Lawers Word
- How Can I eSign Hawaii Lawers Document
- How To eSign Hawaii Lawers PPT
- Help Me With eSign Hawaii Insurance PPT
- Help Me With eSign Idaho Insurance Presentation
- Can I eSign Indiana Insurance Form
- How To eSign Maryland Insurance PPT
- Can I eSign Arkansas Life Sciences PDF
- How Can I eSign Arkansas Life Sciences PDF
- Can I eSign Connecticut Legal Form
- How Do I eSign Connecticut Legal Form
- How Do I eSign Hawaii Life Sciences Word
- Can I eSign Hawaii Life Sciences Word
- How Do I eSign Hawaii Life Sciences Document