Investigate Form


What is the Investigate Form
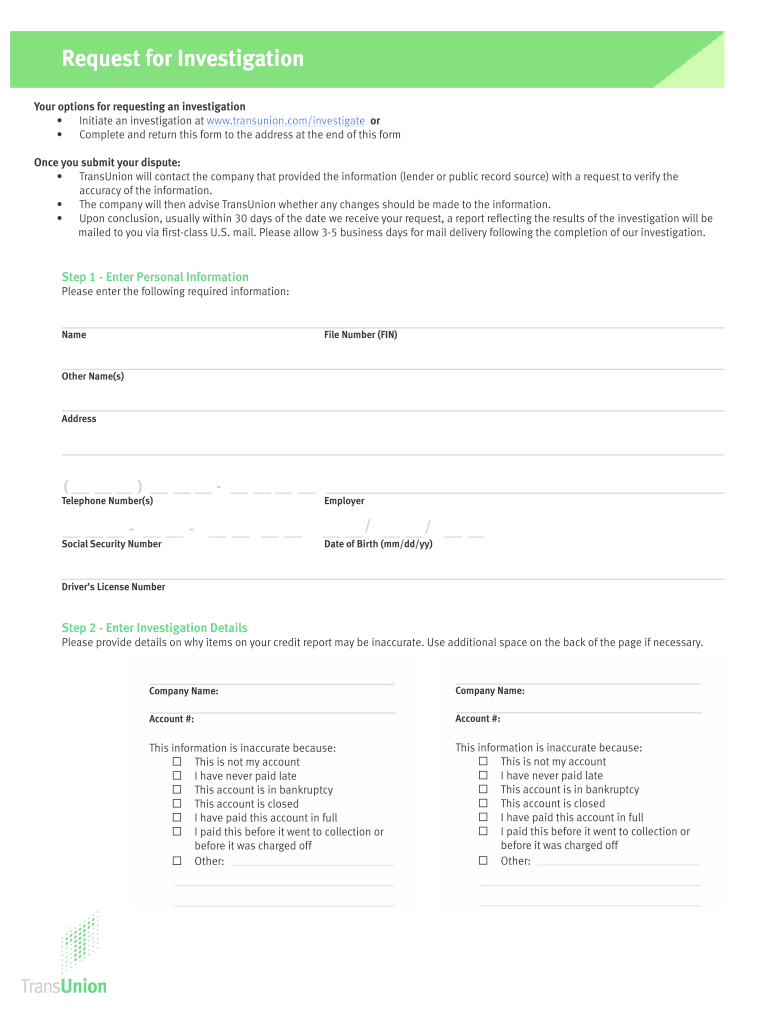
The investigation investigate form is a document used to formally request an inquiry into specific issues or disputes. This form is essential for individuals or businesses seeking to clarify or resolve matters related to personal or financial information, such as credit reports or account discrepancies. It serves as a structured means to communicate the details of the investigation request, ensuring that all necessary information is included for proper handling.
How to use the Investigate Form
Using the investigation investigate form involves several straightforward steps. First, gather all relevant information that pertains to your request, including personal identification details and specifics about the issue at hand. Next, accurately fill out the form, ensuring that all fields are completed. Once completed, you can submit the form electronically or via traditional mail, depending on the requirements of the entity handling the investigation. Be sure to keep a copy of the submitted form for your records.
Steps to complete the Investigate Form
Completing the investigation investigate form requires attention to detail. Follow these steps:
- Identify the purpose of your request and gather supporting documentation.
- Fill out your personal information, including your name, address, and contact details.
- Clearly describe the issue or dispute you are investigating.
- Include any relevant account numbers or identifiers.
- Review the form for accuracy and completeness.
- Submit the form through the designated method, ensuring you retain a copy.
Legal use of the Investigate Form
The investigation investigate form must comply with various legal standards to ensure its validity. This includes adherence to regulations such as the Fair Credit Reporting Act (FCRA) and other applicable laws governing consumer rights. When used correctly, the form can serve as a legally binding request that mandates a response from the entity being investigated. It is crucial to understand your rights and the legal implications of submitting this form.
Key elements of the Investigate Form
Several key elements are essential for the investigation investigate form to be effective:
- Personal Information: Accurate identification details of the individual submitting the form.
- Issue Description: A clear and concise explanation of the matter being investigated.
- Supporting Documentation: Any evidence or documents that support the request.
- Submission Method: Information on how the form will be submitted, whether electronically or by mail.
Form Submission Methods
The investigation investigate form can be submitted in various ways, depending on the requirements of the organization handling the request. Common submission methods include:
- Online Submission: Many organizations allow electronic submission through their websites, which can expedite the process.
- Mail: Traditional postal service can be used for submitting physical copies of the form.
- In-Person: Some entities may accept forms submitted directly at their offices, providing an opportunity for immediate clarification if needed.
Quick guide on how to complete request investigation form
Discover how to sail through the Investigation Form completion with this uncomplicated guide
eFiling and filling out forms digitally is becoming more prevalent and the preferred option for many users. It provides numerous benefits over traditional printed papers, such as convenience, time savings, enhanced precision, and security.
With tools like airSlate SignNow, you can find, modify, sign, and enhance your Investigate Form without getting bogged down in endless printing and scanning. Follow this short tutorial to initiate and complete your form.
Utilize these instructions to access and complete Investigate Form
- Begin by clicking the Get Form button to launch your form in our editor.
- Follow the green indicator on the left that highlights mandatory fields so you don’t miss them.
- Employ our advanced features to annotate, modify, sign, secure, and enhance your form.
- Protect your document or transform it into a fillable form using the options in the right panel.
- Review the form and verify it for mistakes or inconsistencies.
- Click on DONE to complete the editing process.
- Rename your form or leave it as is.
- Select the storage option you prefer to save your form, send it via USPS, or click the Download Now button to save your form.
If Investigate Form isn’t what you were after, you can explore our extensive library of pre-uploaded templates that you can fill out with minimal effort. Visit our platform today!
Create this form in 5 minutes or less
FAQs
-
Have you ever had the pleasure of proving a customer very wrong? What happened?
I was working as a Systems Engineer for a major computer company (3-letter name) and our marketing team had sold a very expensive mainframe computer to an oil refinery. The “MIS Manager” at that plant was someone wholly unqualified for the job, lacking even basic computing skills, and with zero understanding of how computers work in the first place. A few weeks after the installation, I received a call from him, telling me their computer was broken, and that I had to get it fixed immediately. Repeated attempts to get him to tell me what was wrong got me nowhere, so I drove the 60 miles to the refinery to figure out what was wrong.Upon arriving at the plant, I was ushered into the General Manager’s office, where the MIS Manager actually accused us (the 3-letter major computer company) of intentionally sabotaging the performance of the computer so that he (the customer) would have to buy a larger computer to get the work done. I learned that the computer itself was fine, but one of their programs was taking roughly 14 hours to print out a shipping label. This did seem to be totally unacceptable performance, but his claims that the computer was broken were clearly bogus.Maintaining my professionalism, I asked if I could view the program in question – the one that printed the labels. He loudly proclaimed that the program could not possibly be the issue, because they had hired someone away from NASA to do the programming, and had paid him over $100,000 for the program. Therefore, the problem had to be the computer itself. Eventually, the GM ordered the MIS guy to give me a couple of hours access to the software, after which we would re-convene the meeting in the GM’s office to hear my assessment.The application was actually a good bit more involved than just printing labels. It was printing hazardous materials handling instructions (several pages long) for HazMat shipments originating from the plant. This involved various database lookups to obtain the ingredients, their chemical formulae, and finally the handling instructions each for those components. The application itself was written in a very high-level scripting language (REXX, for those of you who know what that is), which I found very surprising, since this type of application would typically be written in a compiled language of some kind, for performance reasons. Then, after looking at the code for only a few minutes, I realized the programmer who wrote it knew very little about programming in general, or about mainframe programming in particular. (I eventually learned that the “NASA contractor” was not actually a computer programmer when he worked there – he was actually a project manager.)After a half-hour reviewing the code, I spent the next 1.5 hours re-writing it, removing obvious performance bottlenecks, and then we tested it. My “quick hack” version took 90 seconds to print a label (vs 14 hours previously). At the follow-up meeting in the GM’s office, I explained what I had done, demonstrated the performance improvement, and stated that I was still extremely dissatisfied with the performance, but it would take more than a 2-hour quick and dirty re-write of the existing code to truly optimize it. The GM was blown away by the results, and was clearly looking at his MIS Manager in a new light.PS - After returning to our office, another gentleman and I re-wrote the application in PL/1 (a compiled language used by the customer’s IT group), and the time to print a label went to under 3 seconds. That’s the version I delivered back to them, with the explanation that a really good programmer could probably achieve even better performance, but this was the best I could do without charging them for the service. The GM was quite happy with the results, whereas the MIS Manager was still claiming that we had rigged the computer to perform poorly so they would have to upgrade to a bigger, more expensive model.By the way, the next time I visited the refinery, the GM introduced me to their new MIS Manager…
-
How often do candidates fail background checks?
It happens, but not all that often. I work with professionals and executives who are rarely in any kind of trouble with the law, but it does happen from time to time. The failures that I run across are usually in the form of dishonesty when writing a resume — omitting a short-term job that didn’t work out, claiming a college degree that wasn’t earned, inflating accomplishments, or claiming someone else’s accomplishments as their own, or covering employment gaps with “consulting” work (OK, fine. Give me references from a few of your clients). It’s just way too easy to check these things, and there are lots of third-party reference checking firms that are really, really good at it.There have been a couple of times when someone who claimed to be a member of Mensa turned out not to have ever been a member at all. It was pretty easy to check since all I have to do is check the member directory, then ask the person to explain why he wasn’t listed there. One even tried to tell me that he “was asked to join” (no, Mensa doesn’t do that), and he “turned them down”.Criminal records, and even driving records, are also sometimes important. One of the strangest was a candidate who was about to be offered a six-figure position that would include a lot of travel and would require the use of a company vehicle. He didn’t think it was important to mention losing his driver’s license due to several DUIs. An he also didn’t think it was important to tell me that his “current” job had ended with his firing several months earlier due to — you guessed it — being involved in a serious accident driving a company vehicle while intoxicated, driving without a license, and leaving the scene of an accident. Sorry. No offer for you.Now and then we see a credit check derail a promising candidate. Whenever access to company funds is a part of the job, it’s important to not have a lot of charge-offs and court judgements on your record. Some otherwise really good candidates have been shot down over just that kind of thing.When it comes to background checks, just remember that honesty is the best policy. Employers can sometimes forgive a mistake or two, but they won’t forgive you trying to lie. If you’re not honest with them from the start, how can they ever trust you on the job?
-
How do I get a report for a 5 year old murder case?
This is going to vary by state. Florida, for instance, has one of the nation's toughest public records laws. FS 119 and the state's constitution presume everything is public record unless a statutory exception exists. A demand for production of police records is made to the custodian of those records, defined as anyone in possession. An exception can be claimed for an "open" case. Police, however, can be required to demonstrate the existence of "an ongoing investigation which is continuing with a reasonable, good faith anticipation of securing an arrest or prosecution in the foreseeable future." Section 119.011(3)(d)2. Referencing Rick Bruno's answer, in Florida there are no "requests" for public records. They are demands for production. And if a cop happens to have that record in his desk drawer, it's mine. No written form is required. Demands may be made verbally, and most often are. Police may not ask your name or question your purpose for demanding the record. It's fair to say cops aren't all that fond of the law as contained in FS 119. But that's what it is. The law. Under Florida's statutory definition of "ongoing investigation," police would likely have a difficult time convincing a judge that "a reasonable, good faith anticipation of securing an arrest or prosecution in the foreseeable future" suddenly exists in a murder case that has otherwise languished for five years. Which doesn't mean they won't try. Before making your demand for production, research your state's open records laws. Know where you stand, what the law requires and allows, and all available remedies.
-
What is one thing that shocked you when you attended an Ivy League or a highly prestigious school like Stanford or MIT?
One thing that shocked me when I attended an Ivy League school is the tolerance and encouragement for faculty plagiarism.Before I attended Ivy League graduate school, I believed that higher values of morality existed in the Ivory Towers. I believed that the most brilliant minds knew and acted to preserve what is good, right and true. I know better, now.I attended Yale University Graduate School from 1990–1993. I was shocked that my advisor, Hazel Carby, was allowed to send an unauthorized copy of my original scholarship to her friend at UCLA. The friend actually performed my work at the same conference I did in front of witnesses.The UCLA professor planned to do my work for her Yale Faculty Job Talk, too. A job talk is required for an application to teach at the university. She had to change her talk at the last minute because I had filed a report with an Assistant Dean of the Yale Graduate School, whose name I’ve forgotten, my other advisor, Robert Stepto, and my program Chairman, Gerald Jaynes.After that, I wrote an elaborate Fellowship Application to Harvard University. I didn’t know that Hazel Carby and Henry Louis Gates were friends.He stole my fellowship application ideas and gave them to a Motown family connection, Brent Edwards, currently plagiarizing at Columbia University.By the time Brent got in to Harvard to start working on my Fellowship book outline, I got in Complit at UMass, and out of the Ivy League grapevine. I was determined to keep trying, although I had been blackballed.Since I came in to UMass knowing exactly what I was doing, I had already ordered the one single solitary copy of microfiche in the United States with newspapers published by in France by African Diaspora journalists from the period between WW I and WW II.I was struggling to translate the newspapers without Harvard translators when a request from the now closed Central Repository Library in Illinois that had lent me the only copy of the microfiche sent me a demand to return it because another person wanted it.I was the first person in history to ever ask for that research material. Now, there’s a rush on it?Respecting the gift of a library to society, after talking to library representatives, I sent back the microfiche along with 50.00 USD and my written request for duplication of the material.Months later, they reported the microfiche was missing! They hadn’t had a chance to duplicate it before it went missing!It remained missing for six years or so, until the summer before Brent Edwards released his book using my outline and research materials as his guide.Before I attended an Ivy League School, I thought plagiarism was something for poor students doomed to lives as failures. Before I attended an Ivy League School, I had job prospects and a fine reputation, now, not so much.
-
How do I respond to a request for a restraining order? Do I need to fill out a form?
As asked of me specifically;The others are right, you will likely need a lawyer. But to answer your question, there is a response form to respond to a restraining order or order of protection. Worst case the form is available at the courthouse where your hearing is set to be heard in, typically at the appropriate clerk's window, which may vary, so ask any of the clerk's when you get there.You only have so many days to respond, and it will specify in the paperwork.You will also have to appear in court on the date your hearing is scheduled.Most courts have a department that will help you respond to forms at no cost. I figure you are asking because you can't afford an attorney which is completely understandable.The problem is that if you aren't represented and the other person is successful in getting a temporary restraining order made permanent in the hearing you will not be allowed at any of the places the petitioner goes, without risking arrest.I hope this helps.Not given as legal advice-
-
Do military personnel need money to fill out a leave request form?
It’s great that you asked. The answer is NO. Also, whatever you are doing with this person, STOP!Bloody hell, how many of these “I need your money to see you sweetheart” scammers are there? It’s probably that or someone totally misunderstood something.All military paperwork is free! However, whether their commander or other sort of boss will let them return or not depends on the nature of duty, deployment terms, and other conditions. They can’t just leave on a whim, that would be desertion and it’s (sorry I don’t know how it works in America) probably punishable by firing (as in termination of job) or FIRING (as in execution)!!!Soldiers are generally paid enough to fly commercial back to home country.Do not give these people any money or any contact information! If you pay him, you’ll probably get a receipt from Nigeria and nothing else.
-
Does a girlfriend have to fill out a leave request form for a US Army Soldier in Special Operations in Africa?
Let me guess, you've been contacted via email by somebody you’ve never met. they've told you a story about being a deployed soldier. At some stage in the dialogue they’ve told you about some kind of emotional drama, sick relative/kid etc. They tell you that because they are in a dangerous part of the world with no facilities they need you to fill in a leave application for them. Some part of this process will inevitably involve you having to pay some money on their behalf. The money will need to be paid via ‘Western Union’. Since you havent had much involvement with the military in the past you dont understand and are tempted to help out this poor soldier. they promise to pay you back once they get back from war.if this sounds familiar you are being scammed. There is no soldier just an online criminal trying to steal your money. If you send any money via Western Union it is gone, straight into the pockets of the scammer. you cant get it back, it is not traceable, this is why scammers love Western Union. They aernt going to pay you back, once they have your money you will only hear from them again if they think they can double down and squeeze more money out of you.Leave applications need to be completed by soldiers themselves. They are normally approved by their unit chain of command. If there is a problem the soldier’s commander will summon them internally to resolve the issue. This is all part of the fun of being a unit commander!! If the leave is not urgent they will wait for a convenient time during a rotation etc to work out the problems, if the leave is urgent (dying parent/spouse/kid etc) they will literally get that soldier out of an operational area ASAP. Operational requirements come first but it would need to be something unthinkable to prevent the Army giving immediate emergency leave to somebody to visit their dying kid in hospital etc.The process used by the scammers is known as ‘Advance fee fraud’ and if you want to read about the funny things people do to scam the scammers have a read over on The largest scambaiting community on the planet!
Create this form in 5 minutes!
How to create an eSignature for the request investigation form
How to make an eSignature for the Request Investigation Form online
How to make an eSignature for the Request Investigation Form in Google Chrome
How to generate an electronic signature for signing the Request Investigation Form in Gmail
How to make an eSignature for the Request Investigation Form from your smartphone
How to make an electronic signature for the Request Investigation Form on iOS
How to make an electronic signature for the Request Investigation Form on Android devices
People also ask
-
What is the purpose of the Investigate Form in airSlate SignNow?
The Investigate Form in airSlate SignNow allows users to streamline the process of collecting information and signatures for various documents. This feature simplifies the workflow by enabling users to easily send and eSign forms, ensuring that all necessary data is captured efficiently.
-
How does airSlate SignNow's Investigate Form enhance document management?
The Investigate Form enhances document management by providing a centralized platform for handling eSignatures and form submissions. With features like customizable templates and automated reminders, users can effectively track the status of their documents and improve overall productivity.
-
What are the pricing options for using the Investigate Form feature?
airSlate SignNow offers flexible pricing plans that cater to different business needs, including options for using the Investigate Form feature. You can choose from monthly or annual subscriptions, ensuring that you find a solution that fits your budget while maximizing your document management capabilities.
-
Can I integrate the Investigate Form with other applications?
Yes, the Investigate Form in airSlate SignNow can be easily integrated with various third-party applications. This allows users to connect their existing tools and streamline workflows, making it easier to collect information and manage documents across different platforms.
-
What are the key benefits of using the Investigate Form for my business?
Using the Investigate Form can signNowly improve your business efficiency by reducing the time spent on paperwork and enhancing communication. It ensures that all signatures and necessary information are collected in a single, organized manner, which can lead to faster decision-making and improved customer satisfaction.
-
Is the Investigate Form feature user-friendly for non-technical users?
Absolutely! The Investigate Form feature in airSlate SignNow is designed with user-friendliness in mind, making it accessible even for non-technical users. With an intuitive interface and straightforward setup process, anyone can create and send forms without requiring advanced technical skills.
-
What types of documents can I create with the Investigate Form?
You can create a variety of documents with the Investigate Form, including contracts, agreements, surveys, and questionnaires. This versatility makes it an ideal solution for businesses looking to streamline their document processes while ensuring compliance and security.
Get more for Investigate Form
Find out other Investigate Form
- eSignature Oklahoma Insurance Warranty Deed Safe
- eSignature Pennsylvania High Tech Bill Of Lading Safe
- eSignature Washington Insurance Work Order Fast
- eSignature Utah High Tech Warranty Deed Free
- How Do I eSignature Utah High Tech Warranty Deed
- eSignature Arkansas Legal Affidavit Of Heirship Fast
- Help Me With eSignature Colorado Legal Cease And Desist Letter
- How To eSignature Connecticut Legal LLC Operating Agreement
- eSignature Connecticut Legal Residential Lease Agreement Mobile
- eSignature West Virginia High Tech Lease Agreement Template Myself
- How To eSignature Delaware Legal Residential Lease Agreement
- eSignature Florida Legal Letter Of Intent Easy
- Can I eSignature Wyoming High Tech Residential Lease Agreement
- eSignature Connecticut Lawers Promissory Note Template Safe
- eSignature Hawaii Legal Separation Agreement Now
- How To eSignature Indiana Legal Lease Agreement
- eSignature Kansas Legal Separation Agreement Online
- eSignature Georgia Lawers Cease And Desist Letter Now
- eSignature Maryland Legal Quitclaim Deed Free
- eSignature Maryland Legal Lease Agreement Template Simple