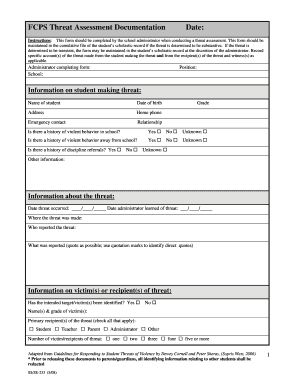
Threat Assessment Template Form


What is the threat assessment template?
The threat assessment template is a structured document designed to evaluate potential risks and threats within an organization, particularly in educational settings. This template serves as a comprehensive tool for identifying, assessing, and mitigating threats to ensure a safe environment for students and staff. It typically includes sections for detailing the nature of the threat, the individuals involved, and the necessary steps to address the situation. By utilizing a standardized format, schools and organizations can streamline their assessment processes and enhance communication among stakeholders.
Key elements of the threat assessment template
A well-constructed threat assessment template incorporates several critical components to ensure thorough evaluation and response. Key elements often include:
- Description of the threat: A detailed account of the specific threat being assessed, including context and potential impact.
- Identification of individuals involved: Information about the individuals who may pose a threat or be affected by it.
- Assessment of risk factors: Analysis of behavioral indicators and environmental factors that contribute to the threat.
- Recommended actions: Suggested interventions or strategies to mitigate the identified threat.
- Follow-up procedures: Guidelines for monitoring the situation and evaluating the effectiveness of implemented measures.
Steps to complete the threat assessment template
Completing a threat assessment template involves a systematic approach to ensure all relevant information is captured accurately. The following steps outline the process:
- Gather information: Collect data from various sources, including reports, interviews, and observations.
- Fill out the template: Input the collected information into the designated sections of the template, ensuring clarity and precision.
- Analyze the data: Evaluate the information to identify patterns, risk factors, and potential threats.
- Develop action plans: Based on the analysis, outline specific actions to address the identified threats.
- Review and finalize: Conduct a thorough review of the completed template to ensure accuracy before distribution.
Legal use of the threat assessment template
When utilizing a threat assessment template, it is essential to adhere to legal standards and regulations to ensure the document's validity and effectiveness. Compliance with laws such as the Family Educational Rights and Privacy Act (FERPA) is crucial when handling sensitive information. Additionally, organizations should be aware of state-specific regulations that may impact how threat assessments are conducted and documented. By following legal guidelines, institutions can protect themselves from liability while promoting a safe environment.
Examples of using the threat assessment template
Practical applications of the threat assessment template can vary across different scenarios. Examples include:
- School incidents: Assessing threats related to bullying, violence, or mental health concerns among students.
- Workplace evaluations: Identifying potential risks related to employee behavior or external threats to staff safety.
- Community assessments: Evaluating threats that may impact public safety, such as natural disasters or criminal activities.
How to obtain the threat assessment template
Organizations can obtain a threat assessment template through various means. Many educational institutions provide standardized templates that can be adapted to specific needs. Additionally, templates may be available through professional organizations, government resources, or online platforms that specialize in educational safety. It is advisable to choose a template that aligns with the unique requirements of the institution and complies with relevant legal standards.
Quick guide on how to complete threat assessment template
Prepare Threat Assessment Template effortlessly on any device
Digital document management has become increasingly popular among businesses and individuals. It serves as an ideal eco-friendly alternative to traditional printed and signed documents, allowing you to access the correct form and securely store it online. airSlate SignNow equips you with all the necessary tools to create, modify, and eSign your documents quickly without delays. Manage Threat Assessment Template on any device with the airSlate SignNow Android or iOS applications and enhance any document-oriented workflow today.
The easiest method to modify and eSign Threat Assessment Template without any hassle
- Locate Threat Assessment Template and click on Get Form to commence.
- Take advantage of the tools we offer to complete your document.
- Emphasize pertinent parts of the documents or obscure sensitive information with tools that airSlate SignNow provides specifically for that purpose.
- Create your signature using the Sign tool, which takes mere seconds and carries the same legal validity as a conventional wet ink signature.
- Verify the details and click on the Done button to save your changes.
- Select your preferred method to deliver your form—by email, text message (SMS), or invitation link, or download it to your computer.
Eliminate concerns about lost or misfiled documents, tedious form searches, or errors that necessitate printing new document copies. airSlate SignNow addresses all your needs in document management with just a few clicks from any device you prefer. Modify and eSign Threat Assessment Template and ensure excellent communication at every stage of the form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the threat assessment template
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a threat assessment template?
A threat assessment template is a structured document that helps organizations identify and evaluate potential threats to their operations. This template guides users through various stages of threat analysis, allowing them to systematically assess risks and implement necessary safeguards.
-
How can I create a custom threat assessment template using airSlate SignNow?
Creating a custom threat assessment template in airSlate SignNow is straightforward. Simply use our user-friendly interface to design a tailored template that meets your organization's specific needs, and you can add form fields, checklists, and even e-signature requirements to streamline the process.
-
Is airSlate SignNow secure for managing threat assessment templates?
Yes, airSlate SignNow prioritizes security and compliance. Our platform utilizes advanced encryption and authentication protocols to ensure that your threat assessment template and all associated data are protected from unauthorized access.
-
What are the benefits of using a threat assessment template?
Using a threat assessment template helps organizations save time and enhance accuracy in identifying potential threats. It promotes a systematic approach to risk management, ensuring that all necessary factors are considered in your evaluations.
-
Can the threat assessment template integrate with other tools?
Absolutely! airSlate SignNow supports integrations with various tools and software that you may already be using, allowing a seamless workflow for managing your threat assessment templates alongside other business processes.
-
What features are included in the threat assessment template offered by airSlate SignNow?
The threat assessment template from airSlate SignNow includes customizable sections, e-signature capabilities, real-time collaboration features, and analytics tools. These features ensure that your threat assessments are not only comprehensive but also efficiently managed.
-
How much does it cost to use the threat assessment template?
The cost to use the threat assessment template in airSlate SignNow varies based on your selected plan. We offer several pricing tiers, all designed to provide a cost-effective solution for businesses of any size aiming to manage their threat assessment processes.
Get more for Threat Assessment Template
Find out other Threat Assessment Template
- Electronic signature Construction Form California Fast
- Help Me With Electronic signature Colorado Construction Rental Application
- Electronic signature Connecticut Construction Business Plan Template Fast
- Electronic signature Delaware Construction Business Letter Template Safe
- Electronic signature Oklahoma Business Operations Stock Certificate Mobile
- Electronic signature Pennsylvania Business Operations Promissory Note Template Later
- Help Me With Electronic signature North Dakota Charity Resignation Letter
- Electronic signature Indiana Construction Business Plan Template Simple
- Electronic signature Wisconsin Charity Lease Agreement Mobile
- Can I Electronic signature Wisconsin Charity Lease Agreement
- Electronic signature Utah Business Operations LLC Operating Agreement Later
- How To Electronic signature Michigan Construction Cease And Desist Letter
- Electronic signature Wisconsin Business Operations LLC Operating Agreement Myself
- Electronic signature Colorado Doctors Emergency Contact Form Secure
- How Do I Electronic signature Georgia Doctors Purchase Order Template
- Electronic signature Doctors PDF Louisiana Now
- How To Electronic signature Massachusetts Doctors Quitclaim Deed
- Electronic signature Minnesota Doctors Last Will And Testament Later
- How To Electronic signature Michigan Doctors LLC Operating Agreement
- How Do I Electronic signature Oregon Construction Business Plan Template