Cyber Security Incident Report Form PDF DSD


Key elements of the cyber security incident report form PDF
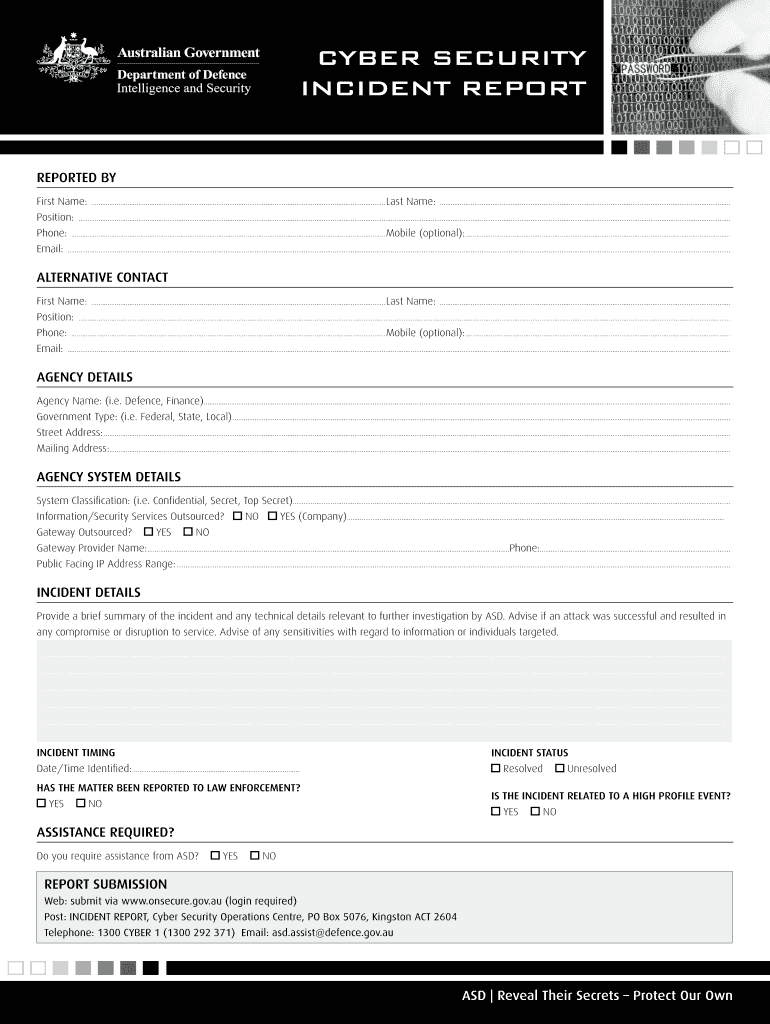
The cyber security incident report form PDF is designed to capture essential information about a security incident. Understanding its key elements is crucial for effective documentation. Important components typically include:
- Incident description: A detailed account of what occurred, including the nature of the incident and its impact.
- Date and time: When the incident happened, which helps in tracking and analysis.
- Location: The physical or digital location where the incident took place.
- Involved parties: Identification of individuals or departments affected by the incident.
- Response actions: Steps taken immediately following the incident to mitigate damage.
- Reporting individual: Name and contact information of the person filling out the report.
Steps to complete the cyber security incident report form PDF
Completing the cyber security incident report form PDF involves several clear steps to ensure accuracy and comprehensiveness. Follow these guidelines:
- Gather information: Collect all relevant details about the incident, including timelines, involved parties, and any preliminary findings.
- Fill out the form: Start entering the information into the report, ensuring each section is completed thoroughly.
- Review for accuracy: Double-check the information provided to ensure it is correct and complete.
- Submit the form: Follow the designated submission process, whether online, via email, or in person, as required by your organization.
How to use the cyber security incident report form PDF
The cyber security incident report form PDF serves as a vital tool for documenting security breaches or incidents. To use it effectively:
- Understand the purpose: Recognize that this form is a formal record meant to aid in the investigation and response to security incidents.
- Ensure confidentiality: Handle the form with care, as it may contain sensitive information.
- Follow organizational protocols: Adhere to your organization’s specific guidelines for reporting incidents and using the form.
Legal use of the cyber security incident report form PDF
Understanding the legal implications of the cyber security incident report form PDF is essential for compliance and accountability. Key points include:
- Documentation standards: Ensure that the form meets any relevant legal requirements for documentation in your industry.
- Retention policies: Be aware of how long the report must be kept according to federal or state regulations.
- Potential legal implications: Recognize that this report may be used in legal proceedings, making accuracy and thoroughness vital.
Examples of using the cyber security incident report form PDF
Real-world scenarios can illustrate how the cyber security incident report form PDF is utilized. Examples include:
- Data breach incidents: Documenting unauthorized access to sensitive customer information.
- Phishing attacks: Recording incidents where employees received fraudulent emails that compromised security.
- Malware infections: Reporting instances of malware affecting company systems and the subsequent response actions.
Quick guide on how to complete cyber security incident report form pdf dsd
Effortlessly Prepare Cyber Security Incident Report Form PDF DSD on Any Device
The management of online documents has become increasingly favored by enterprises and individuals alike. It offers an ideal environmentally friendly alternative to traditional printed and signed documents, allowing you to find the correct form and securely store it online. airSlate SignNow equips you with all the necessary tools to swiftly create, modify, and eSign your documents without delays. Handle Cyber Security Incident Report Form PDF DSD on any device using the airSlate SignNow apps for Android or iOS and enhance any document-oriented process today.
How to Modify and eSign Cyber Security Incident Report Form PDF DSD Effortlessly
- Find Cyber Security Incident Report Form PDF DSD and click on Get Form to begin.
- Make use of the tools we provide to complete your document.
- Highlight signNow sections of your documents or redact sensitive information with the specific tools offered by airSlate SignNow.
- Create your signature using the Sign feature, which takes only seconds and carries the same legal validity as a conventional wet ink signature.
- Review the information and click on the Done button to save your changes.
- Choose your preferred method for delivering your form—via email, SMS, invite link, or download it to your computer.
Eliminate concerns over lost or misplaced documents, tedious form hunting, or mistakes that necessitate reprinting new copies. airSlate SignNow fulfills your document management needs with just a few clicks from any device you prefer. Modify and eSign Cyber Security Incident Report Form PDF DSD and maintain excellent communication throughout every stage of your form preparation with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the cyber security incident report form pdf dsd
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is an incident report sample pdf and why is it important?
An incident report sample pdf is a template used to document details about workplace incidents, ensuring all necessary information is captured accurately. Utilizing a well-structured report can help businesses analyze incidents and prevent future occurrences, enhancing workplace safety and compliance.
-
How can airSlate SignNow help in creating an incident report sample pdf?
airSlate SignNow provides a user-friendly platform to create, customize, and eSign incident report sample pdfs efficiently. With its intuitive interface, users can quickly generate reports that suit their specific needs while also ensuring compliance with legal requirements.
-
Are there any costs associated with using airSlate SignNow for incident reports?
While airSlate SignNow offers a range of pricing plans, many users find it a cost-effective solution for creating and managing incident report sample pdfs. We provide flexible subscription options that allow businesses to choose the best plan based on their document signing needs.
-
What features does airSlate SignNow offer for incident reporting?
With airSlate SignNow, users benefit from features such as customizable templates, easy document sharing, and secure electronic signatures for incident report sample pdfs. These features streamline the reporting process, making it easier and faster to document and follow up on incidents.
-
Can I integrate airSlate SignNow with other software for better incident management?
Yes, airSlate SignNow offers integrations with various applications, enhancing your incident management workflow. By connecting with platforms like Google Drive and Dropbox, users can seamlessly access and manage their incident report sample pdfs alongside other essential documents.
-
What are the benefits of using an electronic incident report sample pdf?
Using an electronic incident report sample pdf allows for faster completion, improved accuracy, and better record-keeping. Additionally, eSigning the document ensures that necessary approvals are gathered electronically, helping to expedite response times and maintain a thorough audit trail.
-
How secure is my data when using airSlate SignNow for incident reports?
airSlate SignNow prioritizes data security, using advanced encryption to protect your incident report sample pdfs. With industry-standard security measures in place, users can be confident that their sensitive information is safe during the document handling process.
Get more for Cyber Security Incident Report Form PDF DSD
- Procedure checklist chapter 22 bathing providing a form
- Loyola jesuit college checklist 246619781 form
- Atto di assenso 474823779 form
- Firefighter time report 288 form
- Tka over the counter medication permission form
- Form 154
- Final inspection checklist form
- Does a stock photography agencys copyright registration form
Find out other Cyber Security Incident Report Form PDF DSD
- Can I Electronic signature Michigan Lease agreement for house
- How To Electronic signature Wisconsin Landlord tenant lease agreement
- Can I Electronic signature Nebraska Lease agreement for house
- eSignature Nebraska Limited Power of Attorney Free
- eSignature Indiana Unlimited Power of Attorney Safe
- Electronic signature Maine Lease agreement template Later
- Electronic signature Arizona Month to month lease agreement Easy
- Can I Electronic signature Hawaii Loan agreement
- Electronic signature Idaho Loan agreement Now
- Electronic signature South Carolina Loan agreement Online
- Electronic signature Colorado Non disclosure agreement sample Computer
- Can I Electronic signature Illinois Non disclosure agreement sample
- Electronic signature Kentucky Non disclosure agreement sample Myself
- Help Me With Electronic signature Louisiana Non disclosure agreement sample
- How To Electronic signature North Carolina Non disclosure agreement sample
- Electronic signature Ohio Non disclosure agreement sample Online
- How Can I Electronic signature Oklahoma Non disclosure agreement sample
- How To Electronic signature Tennessee Non disclosure agreement sample
- Can I Electronic signature Minnesota Mutual non-disclosure agreement
- Electronic signature Alabama Non-disclosure agreement PDF Safe