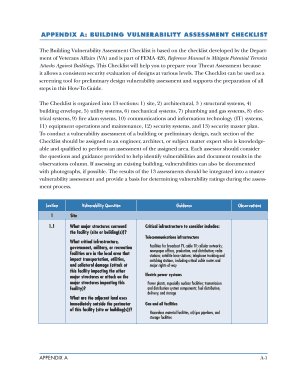
Building Vulnerability Assessment Checklist Form


What is the Building Vulnerability Assessment Checklist
The Building Vulnerability Assessment Checklist is a comprehensive tool designed to evaluate the security and safety of a building. It helps identify potential weaknesses in various areas, including physical security, emergency preparedness, and compliance with safety regulations. This checklist serves as a guide for property managers, safety officers, and business owners to systematically assess vulnerabilities and implement necessary improvements. By addressing these vulnerabilities, organizations can enhance their overall security posture and ensure the safety of occupants.
How to Use the Building Vulnerability Assessment Checklist
Using the Building Vulnerability Assessment Checklist involves several steps to ensure a thorough evaluation. Begin by gathering relevant information about the building, including blueprints, previous assessments, and any existing security measures. Next, walk through the premises and examine each area against the checklist criteria. This includes assessing entry points, surveillance systems, and emergency exits. Document findings meticulously, noting any vulnerabilities identified. Finally, prioritize the vulnerabilities based on risk and develop an action plan to address them effectively.
Key Elements of the Building Vulnerability Assessment Checklist
The Building Vulnerability Assessment Checklist comprises several key elements that are crucial for a comprehensive evaluation. These elements typically include:
- Access Control: Evaluate the effectiveness of locks, security personnel, and entry systems.
- Surveillance: Assess the placement and functionality of cameras and monitoring systems.
- Emergency Preparedness: Review emergency exits, evacuation plans, and safety drills.
- Physical Barriers: Inspect fences, gates, and barriers that deter unauthorized access.
- Lighting: Ensure adequate lighting in and around the building to enhance visibility.
Steps to Complete the Building Vulnerability Assessment Checklist
Completing the Building Vulnerability Assessment Checklist involves a systematic approach. Follow these steps for an effective assessment:
- Gather necessary documentation and materials.
- Conduct a physical walkthrough of the building.
- Evaluate each area against the checklist criteria.
- Document findings and highlight vulnerabilities.
- Prioritize vulnerabilities based on their potential impact.
- Develop an action plan to address identified issues.
Legal Use of the Building Vulnerability Assessment Checklist
Utilizing the Building Vulnerability Assessment Checklist can have legal implications, especially in terms of compliance with safety regulations and liability. It is essential to ensure that the assessment aligns with local, state, and federal laws. Proper documentation of the assessment process can serve as evidence of due diligence in case of legal disputes. Additionally, maintaining compliance with relevant safety standards can help mitigate risks associated with potential liabilities.
Examples of Using the Building Vulnerability Assessment Checklist
Examples of using the Building Vulnerability Assessment Checklist can vary across different sectors. For instance, a school may use the checklist to evaluate safety measures for student protection, while a corporate office might focus on securing sensitive information and assets. In healthcare facilities, the checklist can help ensure compliance with health regulations and patient safety. Each example highlights the checklist's versatility in addressing specific vulnerabilities tailored to the unique needs of various organizations.
Quick guide on how to complete building vulnerability assessment checklist
Complete Building Vulnerability Assessment Checklist effortlessly on any device
Digital document management has gained traction among businesses and individuals. It offers an ideal environmentally friendly alternative to traditional printed and signed documents, enabling you to access the necessary form and securely store it online. airSlate SignNow equips you with all the tools required to create, modify, and eSign your documents quickly without interruptions. Manage Building Vulnerability Assessment Checklist on any device using the airSlate SignNow Android or iOS applications and enhance any document-driven process today.
How to modify and eSign Building Vulnerability Assessment Checklist with ease
- Locate Building Vulnerability Assessment Checklist and select Get Form to begin.
- Employ the tools we offer to fill out your document.
- Emphasize pertinent parts of your documents or omit sensitive details with tools provided by airSlate SignNow specifically for that purpose.
- Create your signature using the Sign feature, which takes seconds and holds the same legal significance as a traditional wet ink signature.
- Review the details and click on the Done button to record your modifications.
- Choose your preferred method for sending your form, whether via email, SMS, invitation link, or download it to your computer.
Eliminate worries about lost or misplaced documents, tedious form searching, or errors that necessitate printing new document copies. airSlate SignNow meets your document management needs in just a few clicks from any device of your preference. Modify and eSign Building Vulnerability Assessment Checklist and ensure effective communication at every stage of the form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the building vulnerability assessment checklist
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a vulnerability assessment checklist?
A vulnerability assessment checklist is a systematic tool that helps organizations identify, evaluate, and prioritize security weaknesses in their systems. By using a vulnerability assessment checklist, businesses can ensure they cover all critical areas that may pose risks to their data and operations.
-
How can I create a vulnerability assessment checklist using airSlate SignNow?
You can create a vulnerability assessment checklist with airSlate SignNow by utilizing our customizable templates and easy-to-use interface. Simply draft your checklist, add the necessary fields, and send it for e-signature to gather essential feedback and approvals securely.
-
Is airSlate SignNow affordable for small businesses looking for a vulnerability assessment checklist solution?
Yes, airSlate SignNow is a cost-effective solution for small businesses seeking a vulnerability assessment checklist. Our pricing plans are designed to accommodate varying budgets, ensuring that even small enterprises can effectively manage their documentation and security assessments.
-
What features does airSlate SignNow offer for managing a vulnerability assessment checklist?
AirSlate SignNow offers a range of features including document templates, e-signature capabilities, and secure cloud storage. These features streamline the management of your vulnerability assessment checklist, allowing for easier collaboration and tracking of document history.
-
Can I integrate airSlate SignNow with other tools to enhance my vulnerability assessment checklist process?
Absolutely! AirSlate SignNow supports various integrations with popular tools like Google Drive, Salesforce, and Zapier. These integrations allow you to enhance your vulnerability assessment checklist process by automating workflows and centralizing your security documentation.
-
What benefits does using a vulnerability assessment checklist in airSlate SignNow provide?
Using a vulnerability assessment checklist in airSlate SignNow helps streamline the assessment process, ensuring thorough evaluations are conducted. Additionally, the platform’s secure e-signature feature allows you to obtain approvals quickly and efficiently while maintaining compliance with industry standards.
-
How does airSlate SignNow ensure the security of my vulnerability assessment checklist documents?
AirSlate SignNow prioritizes the security of your documents by implementing advanced encryption protocols and compliance with regulations such as GDPR. Your vulnerability assessment checklist and associated data are protected throughout the submission and storage processes.
Get more for Building Vulnerability Assessment Checklist
- Hard money loan application noble mortgage form
- Association of diving contractors international medical history form
- Huerfano county building department form
- Personal financial summary form citibank
- Miami dade contractor complaint formpdf
- License ampamp rabies vaccination certificate form
- City of miramar form
- Forms bureau of cannabis control state of california
Find out other Building Vulnerability Assessment Checklist
- Electronic signature Michigan Government LLC Operating Agreement Online
- How To Electronic signature Minnesota Government Lease Agreement
- Can I Electronic signature Minnesota Government Quitclaim Deed
- Help Me With Electronic signature Mississippi Government Confidentiality Agreement
- Electronic signature Kentucky Finance & Tax Accounting LLC Operating Agreement Myself
- Help Me With Electronic signature Missouri Government Rental Application
- Can I Electronic signature Nevada Government Stock Certificate
- Can I Electronic signature Massachusetts Education Quitclaim Deed
- Can I Electronic signature New Jersey Government LLC Operating Agreement
- Electronic signature New Jersey Government Promissory Note Template Online
- Electronic signature Michigan Education LLC Operating Agreement Myself
- How To Electronic signature Massachusetts Finance & Tax Accounting Quitclaim Deed
- Electronic signature Michigan Finance & Tax Accounting RFP Now
- Electronic signature Oklahoma Government RFP Later
- Electronic signature Nebraska Finance & Tax Accounting Business Plan Template Online
- Electronic signature Utah Government Resignation Letter Online
- Electronic signature Nebraska Finance & Tax Accounting Promissory Note Template Online
- Electronic signature Utah Government Quitclaim Deed Online
- Electronic signature Utah Government POA Online
- How To Electronic signature New Jersey Education Permission Slip