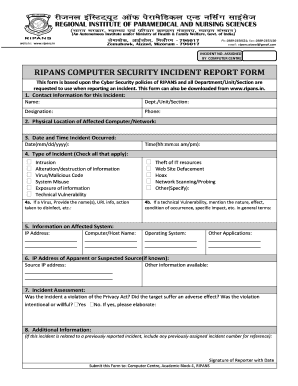
Security Incident Report Form


What is the Security Incident Report
A Security Incident Report is a formal document used to record details of any security-related incidents, such as theft, vandalism, or unauthorized access. This report serves as a critical tool for organizations to evaluate security breaches, identify vulnerabilities, and implement corrective measures. It typically includes information about the incident's nature, location, time, individuals involved, and any actions taken in response.
How to use the Security Incident Report
Using a Security Incident Report involves several steps to ensure that all relevant information is captured accurately. First, gather all necessary details about the incident, including witness statements and any physical evidence. Next, fill out the report with clear and concise descriptions of the events. Ensure that all involved parties sign the report to validate its authenticity. Finally, store the report securely and share it with relevant stakeholders for further analysis and action.
Key elements of the Security Incident Report
Key elements of a Security Incident Report include:
- Date and time: When the incident occurred.
- Location: Where the incident took place.
- Description of the incident: A detailed account of what happened.
- Individuals involved: Names and roles of those present during the incident.
- Actions taken: Immediate responses to the incident.
- Follow-up actions: Recommendations for future prevention and security improvements.
Steps to complete the Security Incident Report
Completing a Security Incident Report involves a systematic approach:
- Identify the incident and gather all pertinent information.
- Document the details in a clear and organized manner.
- Include signatures from all relevant parties to authenticate the report.
- Review the report for accuracy and completeness.
- Distribute copies to necessary personnel and store the original securely.
Legal use of the Security Incident Report
The legal use of a Security Incident Report is crucial for compliance and liability purposes. This document can serve as evidence in legal proceedings or insurance claims. To ensure its legal standing, the report must be completed accurately, signed by involved parties, and maintained in accordance with relevant laws and regulations. Familiarity with state and federal guidelines regarding incident reporting is essential for organizations to protect themselves legally.
Quick guide on how to complete security incident report
Effortlessly Prepare Security Incident Report on Any Device
Digital document management has gained traction among organizations and individuals. It serves as an excellent environmentally friendly alternative to conventional printed and signed documents, as you can easily locate the necessary form and securely save it online. airSlate SignNow provides all the tools you need to create, edit, and electronically sign your documents quickly and without delays. Manage Security Incident Report on any platform with airSlate SignNow’s Android or iOS applications and enhance any document-oriented procedure today.
The easiest way to edit and electronically sign Security Incident Report with ease
- Find Security Incident Report and click on Get Form to begin.
- Utilize the tools we offer to fill out your document.
- Emphasize important sections of your documents or obscure sensitive information with tools that airSlate SignNow provides specifically for that purpose.
- Create your signature using the Sign tool, which takes just seconds and holds the same legal validity as a traditional wet ink signature.
- Review all the details and click on the Done button to preserve your updates.
- Choose how you want to send your form, via email, text message (SMS), or invite link, or download it to your computer.
Forget about lost or misplaced papers, tedious form searching, or errors that require printing new document copies. airSlate SignNow fulfills your document management needs in just a few clicks from a device of your preference. Edit and electronically sign Security Incident Report and ensure outstanding communication at every stage of the document preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the security incident report
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is a SIA incident report example?
A SIA incident report example is a template used for documenting incidents related to security and safety. This structured format helps organizations to efficiently record details such as the nature of the incident, actions taken, and outcomes. Utilizing an effective incident report can lead to improved safety protocols and a better understanding of potential risks.
-
How can airSlate SignNow assist with SIA incident report examples?
airSlate SignNow simplifies the process of creating and eSigning SIA incident report examples by providing customizable templates. With our platform, you can ensure that all necessary information is captured accurately and swiftly. Additionally, seamless eSigning capabilities mean that stakeholders can quickly approve and act on reports.
-
Is there a cost associated with using airSlate SignNow for incident reports?
Yes, airSlate SignNow offers a range of pricing plans tailored to fit businesses of all sizes. This includes options for enhanced features such as custom templates and advanced integrations for SIA incident report examples. A detailed pricing guide is available on our website to help you find the best solution for your needs.
-
Can I import my own SIA incident report example into airSlate SignNow?
Absolutely! airSlate SignNow allows you to import your own SIA incident report example templates. This feature enables you to maintain your existing workflows while enjoying the benefits of our platform’s eSigning and automation capabilities.
-
What features does airSlate SignNow offer for incident reporting?
AirSlate SignNow provides a variety of features that enhance incident reporting, including customizable templates for SIA incident report examples, automated workflows, and real-time tracking. These tools help streamline the documentation process and ensure that reports are completed efficiently and accurately.
-
Are there integrations available with airSlate SignNow for SIA incident report example handling?
Yes, airSlate SignNow integrates seamlessly with numerous applications, facilitating easy data sharing and enhanced functionality for managing SIA incident report examples. You can connect with CRM systems, cloud storage, and other software solutions to keep your incident reports organized and accessible.
-
What are the benefits of using airSlate SignNow for incident reports?
Using airSlate SignNow for your incident reports provides several benefits, including improved accuracy and efficiency in handling SIA incident report examples. The platform's easy-to-use interface and eSigning capabilities simplify the approval process and reduce paperwork, allowing your team to focus on resolving incidents.
Get more for Security Incident Report
- Certificate of authority form cm 06 final no comas 101512dotx cityofboston
- Special dispensation form california dmv
- Ferdinand police department indiana form
- Application for alarm business license city of indianapolis indy form
- Application for hotelmotel license city of indianapolis indy form
- Cfa 4 form
- What is a domestic relations appearance form in indiana
- Form 103 n indy
Find out other Security Incident Report
- How To Sign Wyoming Plumbing Form
- Help Me With Sign Idaho Real Estate PDF
- Help Me With Sign Idaho Real Estate PDF
- Can I Sign Idaho Real Estate PDF
- How To Sign Idaho Real Estate PDF
- How Do I Sign Hawaii Sports Presentation
- How Do I Sign Kentucky Sports Presentation
- Can I Sign North Carolina Orthodontists Presentation
- How Do I Sign Rhode Island Real Estate Form
- Can I Sign Vermont Real Estate Document
- How To Sign Wyoming Orthodontists Document
- Help Me With Sign Alabama Courts Form
- Help Me With Sign Virginia Police PPT
- How To Sign Colorado Courts Document
- Can I eSign Alabama Banking PPT
- How Can I eSign California Banking PDF
- How To eSign Hawaii Banking PDF
- How Can I eSign Hawaii Banking Document
- How Do I eSign Hawaii Banking Document
- How Do I eSign Hawaii Banking Document