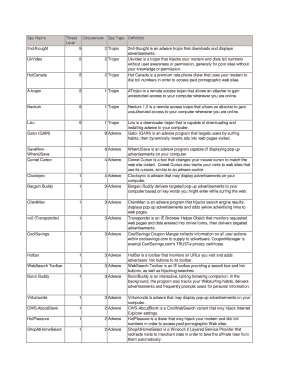
Spy Name Threat Level Occurences Spy Type Definition 2nd Dowling Form


What is the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
The Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling is a specialized document used to categorize and assess various espionage threats. This form provides a framework for identifying the level of risk associated with specific spy names, detailing occurrences linked to each individual, and defining the type of espionage activity involved. It serves as a critical tool for intelligence agencies and security organizations in evaluating potential threats and developing appropriate responses.
How to use the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
Using the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling involves several steps. First, gather all relevant information about the spy names in question, including historical data and known activities. Next, fill out the form by categorizing each spy according to their threat level, which may range from low to high. Document any occurrences associated with each spy, providing context for their activities. Finally, submit the completed form to the appropriate authorities for further analysis and action.
Key elements of the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
Key elements of this form include the following:
- Spy Name: The name of the individual under investigation.
- Threat Level: An assessment of the risk posed by the individual, categorized as low, medium, or high.
- Occurrences: A record of any notable activities or incidents involving the spy.
- Spy Type: Classification of the espionage activities, such as industrial espionage, state-sponsored spying, or cyber espionage.
- Definition: A detailed description of the spy's activities and their implications for national security.
Legal use of the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
The legal use of the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling is governed by federal and state laws regarding intelligence and national security. Organizations must ensure that the information collected and reported adheres to privacy regulations and does not violate individual rights. Proper handling of this form is essential to maintain legal compliance and protect sensitive information from unauthorized disclosure.
Examples of using the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
Examples of using this form include:
- Assessing a foreign national suspected of industrial espionage against a U.S. corporation.
- Evaluating the threat level of an individual linked to a series of cyber attacks on government agencies.
- Documenting the activities of a known spy operating within a sensitive political environment.
Steps to complete the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling
Completing the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling involves the following steps:
- Collect relevant data on the spy, including aliases and known associates.
- Assess the threat level based on the individual's history and current activities.
- Document occurrences that provide insight into the spy's actions.
- Classify the type of espionage activity associated with the spy.
- Review the completed form for accuracy before submission.
Quick guide on how to complete spy name threat level occurences spy type definition 2nd dowling
Complete [SKS] with ease on any device
Digital document management has gained traction among businesses and individuals alike. It serves as a green alternative to traditional printed and signed documents, allowing you to access the correct forms and securely store them online. airSlate SignNow equips you with all the necessary tools to create, edit, and eSign your documents swiftly without interruptions. Handle [SKS] on any device using the airSlate SignNow Android or iOS applications and simplify any document-related process today.
Steps to modify and eSign [SKS] effortlessly
- Find [SKS] and click on Get Form to initiate the process.
- Utilize the available tools to complete your form.
- Emphasize important sections of the documents or conceal sensitive information with tools that airSlate SignNow specifically provides for this task.
- Create your eSignature using the Sign feature, which takes only seconds and holds the same legal standing as a conventional wet ink signature.
- Review the information and click on the Done button to save your changes.
- Choose your preferred method to submit your form, whether by email, SMS, invitation link, or download it to your computer.
Eliminate concerns about lost or misplaced documents, tedious form searches, or errors that require new document prints. airSlate SignNow fulfills all your document management needs in just a few clicks from any device you prefer. Modify and eSign [SKS] and ensure superb communication at every step of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Related searches to Spy Name Threat Level Occurences Spy Type Definition 2nd Dowling
Create this form in 5 minutes!
How to create an eSignature for the spy name threat level occurences spy type definition 2nd dowling
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature in airSlate SignNow?
The Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature helps organizations assess the risk levels associated with specific documents and actions. This ensures that your e-signature process remains secure and compliant. By understanding threat levels, businesses can make informed decisions about their document workflows.
-
How does airSlate SignNow ensure the security of documents related to Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling?
airSlate SignNow employs advanced encryption and security protocols to protect documents, including those identified through the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature. This means your sensitive information remains confidential and safe from unauthorized access, giving you peace of mind.
-
What are the pricing options for airSlate SignNow with Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling?
airSlate SignNow offers various pricing tiers that can accommodate businesses of all sizes. Each plan includes access to the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature, allowing you to choose a solution that fits your budget while ensuring comprehensive document security.
-
Can I integrate airSlate SignNow with other software tools while utilizing the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling?
Yes, airSlate SignNow seamlessly integrates with popular software tools, allowing you to enhance your document management processes. This includes utilizing the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature alongside your existing applications for streamlined workflows and better security.
-
What are the key benefits of using Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling in airSlate SignNow?
The primary benefits include enhanced document security, compliance with regulations, and better risk management. By incorporating the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature, businesses can proactively address potential threats and ensure their digital signatures are safe.
-
Is airSlate SignNow suitable for large enterprises wanting to implement Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling?
Absolutely! airSlate SignNow is designed to support large enterprises with comprehensive features, including the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling functionality. This makes it an ideal solution for organizations needing robust e-signature capabilities combined with advanced security measures.
-
How can I get started with airSlate SignNow and the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature?
Getting started with airSlate SignNow is easy. You can sign up for a free trial to explore the platform and test the functionalities, including the Spy Name Threat Level Occurrences Spy Type Definition 2nd Dowling feature. Once you're ready, you can choose a plan that aligns with your business needs.
Get more for Spy Name Threat Level Occurences Spy Type Definition 2nd Dowling
Find out other Spy Name Threat Level Occurences Spy Type Definition 2nd Dowling
- eSignature South Dakota Education Confidentiality Agreement Later
- eSignature South Carolina Education Executive Summary Template Easy
- eSignature Michigan Doctors Living Will Simple
- How Do I eSignature Michigan Doctors LLC Operating Agreement
- How To eSignature Vermont Education Residential Lease Agreement
- eSignature Alabama Finance & Tax Accounting Quitclaim Deed Easy
- eSignature West Virginia Education Quitclaim Deed Fast
- eSignature Washington Education Lease Agreement Form Later
- eSignature Missouri Doctors Residential Lease Agreement Fast
- eSignature Wyoming Education Quitclaim Deed Easy
- eSignature Alaska Government Agreement Fast
- How Can I eSignature Arizona Government POA
- How Do I eSignature Nevada Doctors Lease Agreement Template
- Help Me With eSignature Nevada Doctors Lease Agreement Template
- How Can I eSignature Nevada Doctors Lease Agreement Template
- eSignature Finance & Tax Accounting Presentation Arkansas Secure
- eSignature Arkansas Government Affidavit Of Heirship Online
- eSignature New Jersey Doctors Permission Slip Mobile
- eSignature Colorado Government Residential Lease Agreement Free
- Help Me With eSignature Colorado Government Medical History