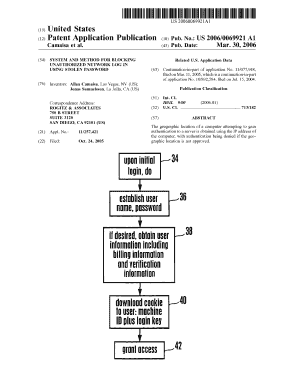
System and Method for Blocking Unauthorized Network Log in Using Books Google Co Form


What is the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
The System and Method for Blocking Unauthorized Network Log In Using Books Google Co is designed to enhance security measures for online platforms. This system employs advanced algorithms to detect and prevent unauthorized access attempts to sensitive networks. By utilizing a combination of user authentication protocols and real-time monitoring, it ensures that only authorized users can log in, thereby protecting valuable information from potential breaches. This system is particularly relevant for businesses that manage sensitive data and require robust security measures to safeguard their operations.
How to Use the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
Using the System and Method for Blocking Unauthorized Network Log In involves several straightforward steps. First, organizations must integrate the system into their existing network infrastructure. This includes configuring user authentication settings and establishing security protocols. Next, administrators should regularly monitor access logs to identify any suspicious activity. Training staff on recognizing potential security threats is also essential. By following these steps, organizations can effectively utilize the system to maintain secure access to their networks.
Key Elements of the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
Several key elements define the effectiveness of the System and Method for Blocking Unauthorized Network Log In. These include:
- User Authentication: Multi-factor authentication is a critical component that adds an extra layer of security.
- Real-Time Monitoring: Continuous surveillance of network activity helps in promptly identifying unauthorized access attempts.
- Access Control Policies: Clearly defined policies determine who can access specific network resources.
- Incident Response Protocols: Established procedures for responding to security breaches ensure quick action can be taken to mitigate risks.
Examples of Using the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
Practical applications of the System and Method for Blocking Unauthorized Network Log In can be seen in various industries. For instance, financial institutions utilize this system to protect customer data from cyber threats. Educational institutions also implement it to secure student information systems against unauthorized access. Additionally, healthcare providers use the system to comply with regulations regarding patient data protection, ensuring that only authorized personnel can access sensitive health records.
Legal Use of the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
Legal considerations are paramount when implementing the System and Method for Blocking Unauthorized Network Log In. Organizations must ensure compliance with federal and state regulations concerning data protection and privacy. This includes adhering to laws such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare entities and the Gramm-Leach-Bliley Act (GLBA) for financial institutions. By following these legal guidelines, organizations can effectively use the system while minimizing the risk of legal repercussions.
Steps to Complete the System and Method for Blocking Unauthorized Network Log In Using Books Google Co
Completing the implementation of the System and Method for Blocking Unauthorized Network Log In involves a series of steps:
- Assessment: Evaluate current security measures and identify vulnerabilities.
- Integration: Incorporate the system into existing network architecture.
- Configuration: Set up user authentication protocols and access control measures.
- Training: Educate staff on security practices and system usage.
- Monitoring: Continuously track network activity for unauthorized access attempts.
Quick guide on how to complete system and method for blocking unauthorized network log in using books google co
Handle [SKS] effortlessly on any device
Digital document management has become increasingly favored by businesses and individuals alike. It offers an ideal environmentally-friendly substitute for conventional printed and signed documents, as you can easily find the necessary form and securely keep it online. airSlate SignNow provides you with all the resources you require to create, adjust, and electronically sign your documents quickly without any delays. Manage [SKS] on any device with the airSlate SignNow Android or iOS applications and simplify any document-related procedure today.
The easiest way to modify and electronically sign [SKS] with ease
- Find [SKS] and click Get Form to begin.
- Use the tools we provide to complete your form.
- Highlight important sections of your documents or conceal sensitive information with tools that airSlate SignNow offers specifically for that purpose.
- Generate your electronic signature using the Sign tool, which only takes a few seconds and has the same legal standing as a traditional handwritten signature.
- Review the details and click on the Done button to save your revisions.
- Choose your preferred method to share your form, via email, SMS, or invite link, or download it to your computer.
Forget about lost or misplaced documents, tedious form searches, or mistakes that necessitate printing new document copies. airSlate SignNow fulfills all your document management needs with just a few clicks from any device you choose. Modify and electronically sign [SKS] to ensure exceptional communication at every stage of the document preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the system and method for blocking unauthorized network log in using books google co
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is the System And Method For Blocking Unauthorized Network Log In Using Books Google Co.?
The System And Method For Blocking Unauthorized Network Log In Using Books Google Co. is a robust security solution designed to prevent unauthorized access to your network. It employs advanced algorithms to detect and block suspicious login attempts, ensuring that your sensitive information remains protected.
-
How does the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. enhance security?
This system enhances security by continuously monitoring login attempts and employing real-time analytics to identify potential threats. By blocking unauthorized logins, it signNowly reduces the risk of data bsignNowes and enhances overall network integrity.
-
What are the pricing options for the System And Method For Blocking Unauthorized Network Log In Using Books Google Co.?
Pricing for the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. varies based on the size of your organization and specific needs. We offer flexible plans that cater to businesses of all sizes, ensuring you get the best value for your investment.
-
Can the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. integrate with other security tools?
Yes, the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. is designed to seamlessly integrate with various security tools and platforms. This allows for a comprehensive security strategy that enhances your existing infrastructure.
-
What are the key features of the System And Method For Blocking Unauthorized Network Log In Using Books Google Co.?
Key features include real-time monitoring, automated threat detection, and customizable security settings. These features work together to provide a comprehensive solution that effectively blocks unauthorized access and protects your network.
-
How can the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. benefit my business?
Implementing the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. can signNowly enhance your business's security posture. By preventing unauthorized access, you protect sensitive data, maintain customer trust, and ensure compliance with industry regulations.
-
Is the System And Method For Blocking Unauthorized Network Log In Using Books Google Co. easy to use?
Absolutely! The System And Method For Blocking Unauthorized Network Log In Using Books Google Co. is designed with user-friendliness in mind. Its intuitive interface allows users to easily navigate and manage security settings without requiring extensive technical knowledge.
Get more for System And Method For Blocking Unauthorized Network Log In Using Books Google Co
Find out other System And Method For Blocking Unauthorized Network Log In Using Books Google Co
- eSign Louisiana Non-Profit Quitclaim Deed Safe
- How Can I eSign Maryland Non-Profit Credit Memo
- eSign Maryland Non-Profit Separation Agreement Computer
- eSign Legal PDF New Jersey Free
- eSign Non-Profit Document Michigan Safe
- eSign New Mexico Legal Living Will Now
- eSign Minnesota Non-Profit Confidentiality Agreement Fast
- How Do I eSign Montana Non-Profit POA
- eSign Legal Form New York Online
- Can I eSign Nevada Non-Profit LLC Operating Agreement
- eSign Legal Presentation New York Online
- eSign Ohio Legal Moving Checklist Simple
- How To eSign Ohio Non-Profit LLC Operating Agreement
- eSign Oklahoma Non-Profit Cease And Desist Letter Mobile
- eSign Arizona Orthodontists Business Plan Template Simple
- eSign Oklahoma Non-Profit Affidavit Of Heirship Computer
- How Do I eSign Pennsylvania Non-Profit Quitclaim Deed
- eSign Rhode Island Non-Profit Permission Slip Online
- eSign South Carolina Non-Profit Business Plan Template Simple
- How Can I eSign South Dakota Non-Profit LLC Operating Agreement