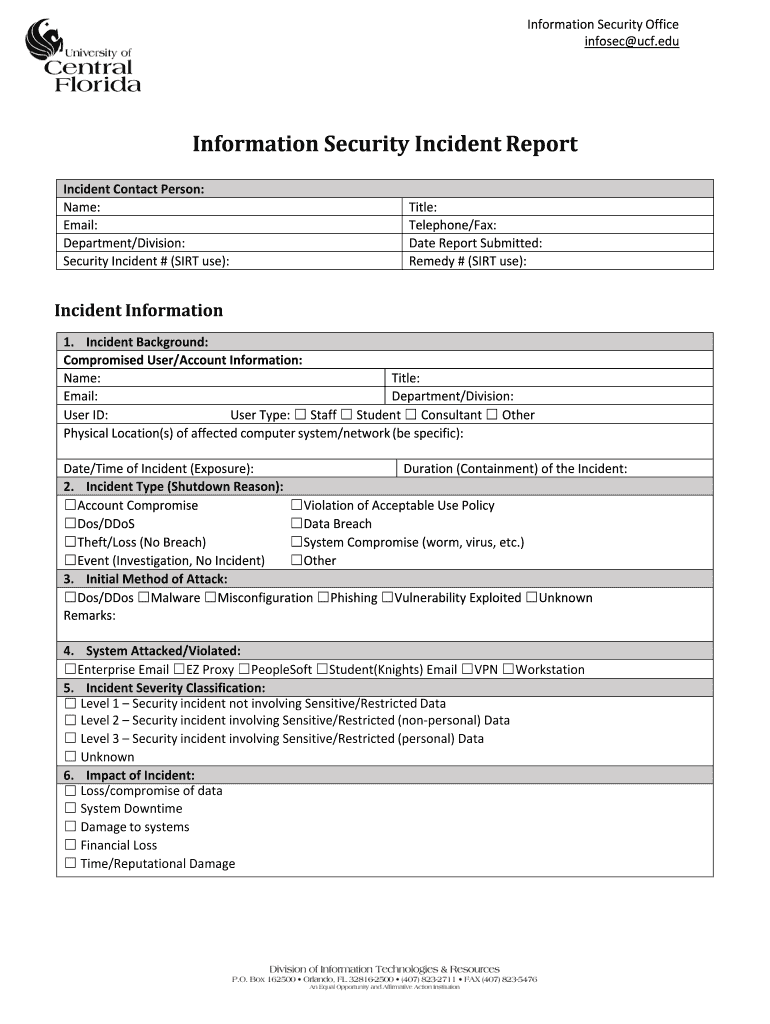
Information Security Office


What is the Information Security Office
The Information Security Office is a dedicated entity within an organization responsible for safeguarding sensitive information and ensuring compliance with relevant security regulations. This office plays a crucial role in protecting data integrity, confidentiality, and availability. It develops policies and procedures to manage risks associated with information security, including data breaches and unauthorized access. The office also provides training and awareness programs to employees about best practices in information security.
How to use the Information Security Office
Utilizing the Information Security Office involves engaging with its resources and services to enhance your organization's security posture. This can include consulting with security professionals for risk assessments, implementing security frameworks, and utilizing tools for monitoring and protecting sensitive information. Employees can also report security incidents or seek guidance on secure practices through the office. Regular communication with the Information Security Office ensures that all team members are aligned with the organization's security goals.
Steps to complete the Information Security Office
Completing the Information Security Office's requirements typically involves several key steps:
- Identify and assess the types of sensitive information handled by the organization.
- Develop a comprehensive information security policy that outlines security measures and protocols.
- Implement security controls, such as encryption and access management, to protect sensitive data.
- Conduct regular training sessions for employees to raise awareness about information security threats.
- Establish a process for reporting and responding to security incidents.
- Regularly review and update security measures to adapt to new threats and compliance requirements.
Legal use of the Information Security Office
The Information Security Office must operate within the framework of various legal and regulatory requirements. Compliance with laws such as the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Act (GLBA), and the Federal Information Security Management Act (FISMA) is essential. These regulations dictate how sensitive information must be handled, stored, and protected. The office also ensures that the organization adheres to industry standards and best practices for information security.
Key elements of the Information Security Office
Several key elements define the effectiveness of the Information Security Office:
- Risk Management: Identifying, assessing, and mitigating risks to sensitive information.
- Policy Development: Creating and enforcing security policies that govern information handling.
- Incident Response: Establishing protocols for responding to security breaches and incidents.
- Compliance Monitoring: Regularly reviewing practices to ensure adherence to legal and regulatory standards.
- Training and Awareness: Educating employees about security threats and safe practices.
Examples of using the Information Security Office
Organizations utilize the Information Security Office in various ways, including:
- Conducting security audits to identify vulnerabilities in systems and processes.
- Implementing data encryption solutions to protect sensitive information during transmission.
- Establishing access controls to restrict unauthorized personnel from accessing critical data.
- Providing ongoing training programs to keep employees informed about the latest security threats.
Quick guide on how to complete information security office
Complete Information Security Office effortlessly on any device
Online document administration has gained popularity among businesses and individuals. It offers an ideal eco-friendly substitute to conventional printed and signed documents, as you can obtain the right form and securely save it online. airSlate SignNow provides all the tools you need to create, edit, and eSign your documents swiftly without delays. Manage Information Security Office on any platform with airSlate SignNow Android or iOS applications and enhance any document-centric task today.
The easiest method to edit and eSign Information Security Office without hassle
- Find Information Security Office and then click Get Form to begin.
- Utilize the tools we offer to complete your document.
- Highlight important sections of the documents or redact confidential information with tools that airSlate SignNow provides specifically for that purpose.
- Create your eSignature with the Sign feature, which takes mere seconds and has the same legal validity as a traditional wet ink signature.
- Verify the information and then click on the Done button to save your updates.
- Choose how you wish to share your form, via email, SMS, or invitation link, or download it to your PC.
Forget about lost or misplaced files, tedious form searching, or errors that necessitate printing new document copies. airSlate SignNow fulfills all your document management needs in just a few clicks from any device you prefer. Edit and eSign Information Security Office and ensure excellent communication at every step of your form preparation process with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the information security office
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What is the role of the Information Security Office in airSlate SignNow?
The Information Security Office at airSlate SignNow is responsible for overseeing all security measures related to document signing and storage. This office ensures that all user data is protected against unauthorized access and adheres to industry-standard security protocols. With a dedicated team, the Information Security Office continuously monitors and improves our security framework to safeguard client information.
-
How does airSlate SignNow ensure compliance with information security standards?
airSlate SignNow’s Information Security Office conducts regular audits and adheres to strict compliance standards such as GDPR, HIPAA, and SOC 2. This commitment ensures that our eSigning solutions are not only user-friendly but also meet critical legal and regulatory requirements. Our team is continuously trained on compliance to provide the best security practices.
-
Are my documents safe with airSlate SignNow's eSigning service?
Yes, your documents are safe with airSlate SignNow, thanks to the protocols established by our Information Security Office. We use encryption, secure servers, and multifactor authentication to protect sensitive information during the signing process. Our security measures are robust and regularly updated to combat emerging threats.
-
How much does it cost to use airSlate SignNow, and are there different pricing plans?
airSlate SignNow offers multiple pricing plans to fit various business needs, with options tailored for small to large organizations. Information about our plans can be found on our website, where the features of each tier are clearly outlined. You can also contact our sales team for custom solutions designed to meet your specific requirements.
-
What features does airSlate SignNow provide to enhance information security?
airSlate SignNow incorporates several features to enhance information security, including advanced encryption and secure cloud storage managed by our Information Security Office. Additional features such as customizable access controls, real-time tracking, and audit trails ensure that you retain control over your documents and their security.
-
Can airSlate SignNow integrate with other applications while maintaining security?
Absolutely! airSlate SignNow easily integrates with various applications while still upholding the highest security standards. Our Information Security Office ensures that each integration is secure and does not compromise user data. This makes it simple to streamline your workflow without sacrificing information security.
-
How does airSlate SignNow maintain privacy throughout the eSigning process?
Privacy is a top priority at airSlate SignNow. Our Information Security Office implements strict access controls and encryption to protect your data during eSigning. Furthermore, we do not sell user information to third parties, ensuring that your sensitive documents remain confidential.
Get more for Information Security Office
- Hcs forms and montana
- Trustee letter to beneficiaries sample form
- Patient feedback form
- Uniformly accelerated particle model review sheet
- Hsbc safeguard kyc form
- Cash voucher online form
- Modello rapporto di intervento manutenzione word form
- I 212 application for consent to reapply for admission to form
Find out other Information Security Office
- Sign Alabama Real Estate Quitclaim Deed Free
- How Can I Sign Alabama Real Estate Affidavit Of Heirship
- Can I Sign Arizona Real Estate Confidentiality Agreement
- How Do I Sign Arizona Real Estate Memorandum Of Understanding
- Sign South Dakota Plumbing Job Offer Later
- Sign Tennessee Plumbing Business Letter Template Secure
- Sign South Dakota Plumbing Emergency Contact Form Later
- Sign South Dakota Plumbing Emergency Contact Form Myself
- Help Me With Sign South Dakota Plumbing Emergency Contact Form
- How To Sign Arkansas Real Estate Confidentiality Agreement
- Sign Arkansas Real Estate Promissory Note Template Free
- How Can I Sign Arkansas Real Estate Operating Agreement
- Sign Arkansas Real Estate Stock Certificate Myself
- Sign California Real Estate IOU Safe
- Sign Connecticut Real Estate Business Plan Template Simple
- How To Sign Wisconsin Plumbing Cease And Desist Letter
- Sign Colorado Real Estate LLC Operating Agreement Simple
- How Do I Sign Connecticut Real Estate Operating Agreement
- Sign Delaware Real Estate Quitclaim Deed Secure
- Sign Georgia Real Estate Business Plan Template Computer