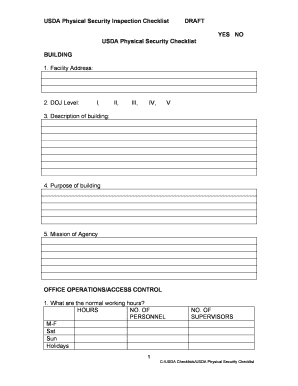
Usda Physical Security Checklist Form


What is the USDA Physical Security Checklist
The USDA Physical Security Checklist is a comprehensive tool designed to ensure that facilities meet the necessary security standards set by the United States Department of Agriculture. This checklist helps organizations assess their physical security measures, identify vulnerabilities, and implement improvements to safeguard their assets. It covers various aspects, including access control, surveillance systems, and emergency response protocols, ensuring that all critical areas are addressed.
How to Use the USDA Physical Security Checklist
Using the USDA Physical Security Checklist involves several key steps. First, gather all relevant information about your facility's current security measures. Next, systematically go through each item on the checklist, evaluating your existing protocols against the recommended standards. Document any areas that require enhancement or compliance adjustments. Finally, develop an action plan to address identified gaps and improve your overall security posture.
Key Elements of the USDA Physical Security Checklist
The USDA Physical Security Checklist includes several essential elements that organizations must consider. These elements typically encompass:
- Access Control: Procedures for managing who can enter specific areas of the facility.
- Surveillance: The presence and effectiveness of cameras and monitoring systems.
- Emergency Response: Plans for responding to security breaches or other emergencies.
- Training: Ensuring staff are trained in security protocols and emergency procedures.
Steps to Complete the USDA Physical Security Checklist
Completing the USDA Physical Security Checklist involves a systematic approach. Start by reviewing each section of the checklist thoroughly. For each item, assess your current security measures and determine if they meet the outlined standards. If discrepancies are found, note them for further action. After completing the checklist, prioritize the areas needing improvement based on risk assessment and available resources.
Legal Use of the USDA Physical Security Checklist
The USDA Physical Security Checklist serves as a legal document that can support compliance with federal regulations. When properly completed, it can demonstrate an organization's commitment to maintaining a secure environment. It is essential to ensure that all information documented is accurate and reflects the current state of security measures, as this can be critical in audits or legal inquiries.
Examples of Using the USDA Physical Security Checklist
Organizations can utilize the USDA Physical Security Checklist in various scenarios. For instance, a food processing plant may use it to evaluate their security measures before a federal inspection. Similarly, a research facility could implement the checklist to enhance their security protocols following a recent incident. By applying the checklist, organizations can ensure they meet industry standards and protect their operations effectively.
Quick guide on how to complete usda physical security checklist
Prepare Usda Physical Security Checklist effortlessly on any device
Online document management has become increasingly favored by businesses and individuals. It serves as an ideal environmentally friendly alternative to traditional printed and signed paperwork, allowing you to easily locate the correct form and safely store it online. airSlate SignNow equips you with all the tools necessary to create, modify, and electronically sign your documents rapidly without interruptions. Manage Usda Physical Security Checklist on any device using the airSlate SignNow Android or iOS applications and simplify any document-related processes today.
How to modify and electronically sign Usda Physical Security Checklist with ease
- Find Usda Physical Security Checklist and click Get Form to begin.
- Utilize the tools available to fill out your form.
- Mark important sections of the documents or obscure sensitive information with the tools provided by airSlate SignNow specifically for that purpose.
- Create your electronic signature using the Sign feature, which takes seconds and holds the same legal validity as a traditional handwritten signature.
- Review all the details and click the Done button to save your modifications.
- Choose how you wish to send your form, whether by email, text message (SMS), invite link, or download it to your computer.
Eliminate concerns about lost or misplaced documents, tedious form searches, or mistakes that necessitate printing new document copies. airSlate SignNow addresses all your document management needs in just a few clicks from any chosen device. Alter and electronically sign Usda Physical Security Checklist and guarantee outstanding communication at every step of your form preparation journey with airSlate SignNow.
Create this form in 5 minutes or less
Create this form in 5 minutes!
How to create an eSignature for the usda physical security checklist
How to create an electronic signature for a PDF online
How to create an electronic signature for a PDF in Google Chrome
How to create an e-signature for signing PDFs in Gmail
How to create an e-signature right from your smartphone
How to create an e-signature for a PDF on iOS
How to create an e-signature for a PDF on Android
People also ask
-
What are the key features of the security checklist in the Pega platform?
The security checklist feature of the Pega platform is designed to help users understand and implement necessary security measures. Which two statements describe the security checklist feature of Pega platform choose two: it provides a structured approach to enhancing security and outlines compliance requirements to safeguard business data.
-
How does airSlate SignNow integrate with the Pega platform?
AirSlate SignNow offers seamless integration with the Pega platform, enabling businesses to manage eSignatures and document workflows efficiently. This integration ensures that users can utilize the security checklist feature by leveraging the insights provided to enhance their overall security posture.
-
Is the Pega platform's security checklist customizable?
Yes, the Pega platform's security checklist can be customized to fit specific organizational needs. Companies can refine which two statements describe the security checklist feature of Pega platform choose two by modifying the standard guidelines to suit their regulatory requirements and operational contexts.
-
What are the benefits of using the security checklist feature of the Pega platform?
Using the security checklist feature of the Pega platform helps organizations ensure comprehensive data protection. Which two statements describe the security checklist feature of Pega platform choose two: it promotes adherence to industry standards and simplifies the audit processes for security compliance.
-
How does airSlate SignNow support compliance with the Pega platform?
AirSlate SignNow aids compliance efforts when used alongside the Pega platform by providing secure eSigning options. By utilizing features like the security checklist, businesses can easily implement the necessary protocols to ensure alignment with legal and regulatory standards.
-
What is the pricing structure for the Pega platform security features?
The pricing structure for the Pega platform's security features varies by the specific solutions and integrations required. Prospective users should consult with Pega representatives to understand costs associated with using the security checklist feature and how it can benefit their organization.
-
Can the security checklist feature be accessed on mobile devices?
Yes, the security checklist feature of the Pega platform is accessible on mobile devices, allowing users to review, apply, and monitor security measures on the go. This flexibility ensures that team members can frequently engage with which two statements describe the security checklist feature of Pega platform choose two from anywhere.
Get more for Usda Physical Security Checklist
- Transfare form
- Teacher leadership gace form
- Diabetes foot screen saskatoon health region saskatoonhealthregion form
- Akron general financial assistance form
- 1022 prior authorization maryland physicians care medica id medicaid this fax machine is located in a secure location as form
- Form g 45 periodic general exciseuse tax return rev
- 2 give exact time of accident date day and hour form
- Schedule ge form g 45g 49 rev general exciseuse tax schedule of exemptions and deductions
Find out other Usda Physical Security Checklist
- How Can I Electronic signature Massachusetts Sports Presentation
- How To Electronic signature Colorado Courts PDF
- How To Electronic signature Nebraska Sports Form
- How To Electronic signature Colorado Courts Word
- How To Electronic signature Colorado Courts Form
- How To Electronic signature Colorado Courts Presentation
- Can I Electronic signature Connecticut Courts PPT
- Can I Electronic signature Delaware Courts Document
- How Do I Electronic signature Illinois Courts Document
- How To Electronic signature Missouri Courts Word
- How Can I Electronic signature New Jersey Courts Document
- How Can I Electronic signature New Jersey Courts Document
- Can I Electronic signature Oregon Sports Form
- How To Electronic signature New York Courts Document
- How Can I Electronic signature Oklahoma Courts PDF
- How Do I Electronic signature South Dakota Courts Document
- Can I Electronic signature South Dakota Sports Presentation
- How To Electronic signature Utah Courts Document
- Can I Electronic signature West Virginia Courts PPT
- Send Sign PDF Free