- The SignNow MCP Server provides AI agents with safe, structured access to SignNow API features, including templates, invites, embedded signing, status checks, and downloads.
- You can run it locally (STDIO) or remotely (Streamable HTTP), including Docker and Docker Compose. STDIO is ideal for desktop dev; HTTP is best for containers and remote hosts.
- Common agent tasks: list templates, create documents from templates, send email invites or generate embedded signing links, track status, pre-fill fields, and download the final signed PDFs.
- Security is handled through environment variables, OAuth 2.0 options, and RSA keys for production token signing. Keep secrets in a secure store and persist your private key in production.
- Quick start:
pip install signnow-mcp-server→sn-mcp serve(orsn-mcp http) → point your MCP-capable client (e.g., VS Code Agent Mode, Claude Desktop) to the server and start using the SignNow tools.
As development teams integrate artificial intelligence into their workflows, AI agents require a secure and reliable means of interacting with external services. This article explains how developers can use the SignNow MCP Server to empower AI agents to securely manage eSignature workflows, automate document processes, and enhance productivity.
What is the SignNow MCP Server?
A Model Context Protocol (MCP) server enables AI agents to operate SignNow eSignature workflows in a controlled and auditable manner. It exposes the most commonly used SignNow API tools—templates, invites, embedded experiences, status checks, and downloads—via a well-defined interface. It supports both STDIO (local) and Streamable HTTP (remote) transports.
Why this matters: Instead of granting a general-purpose model broad API access, MCP lets you scope actions to approved tools. This reduces risk, standardizes inputs/outputs, and makes agent behavior easier to monitor.
Learn more about the SignNow MCP Server on GitHub.
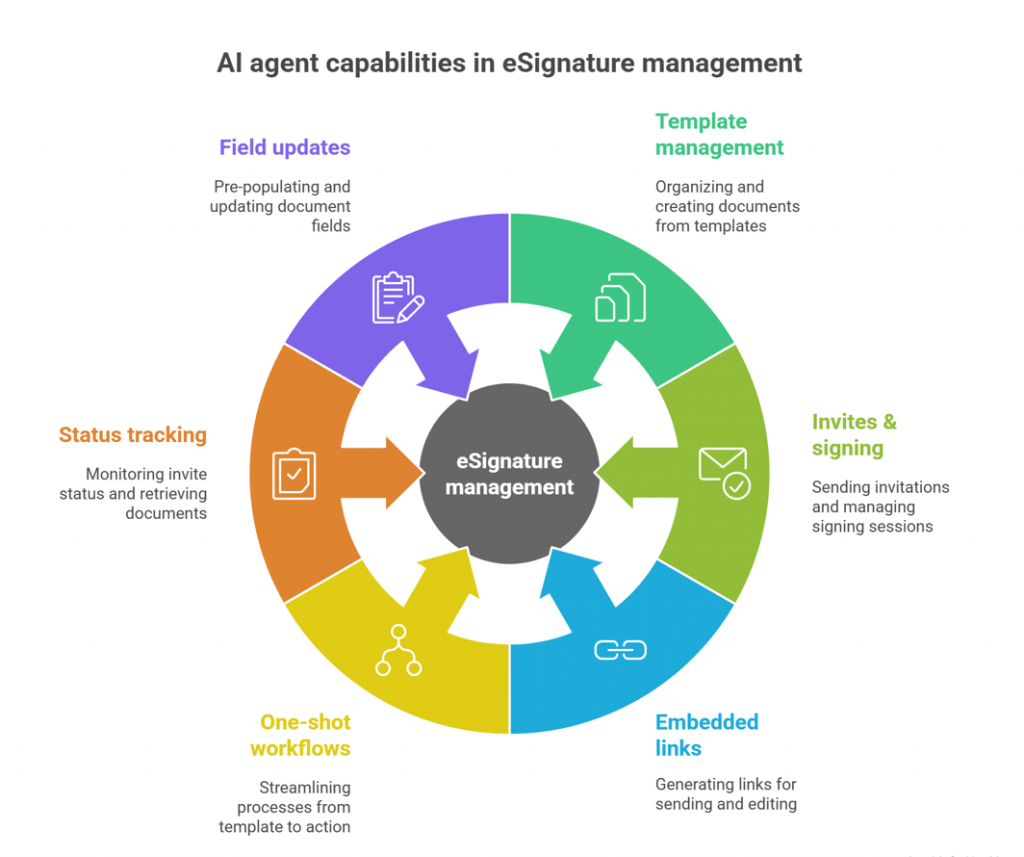
What can AI agents do with this server?
Agents can handle the full eSignature lifecycle while you retain control:
- Template & document management
List templates and groups, and create documents or groups from templates. - Invites & embedded signing
Send email invites with ordered recipients or create embedded signing sessions without email delivery. - Embedded sending and editing
Generate embedded links for document sending/management and for field editing experiences. - One-shot workflows
Go from template to action in a single call (e.g., template → invite, template → embedded signing). - Status tracking & retrieval
Get invite status (with step-level details), retrieve normalized document structures, and download signed files. - Field prefill & updates
Pre-populate text fields or update field values before sending.
Core tools you’ll use include:
list_all_templatescreate_from_templatesend_invitecreate_embedded_invitecreate_embedded_sendingcreate_embedded_editorget_invite_statusget_document_download_linkget_documentupdate_document_fields- plus “one-shot” variants that chain document creation and action together
How does the SignNow MCP Server keep AI agents secure?
- Scoped, structured tools: Agents call specific, typed tools—no raw, arbitrary API access. You decide which tools are available.
- Environment-based secrets: Credentials are supplied via environment variables; you can rotate and vault them according to your organization’s policy.
- OAuth 2.0 options: For hosted scenarios, enable OAuth with proper issuer, TTLs, and allowed redirects. Use RSA keys to sign tokens.
- Production key management: Persist your RSA private key in production to avoid invalidating tokens on restarts.
- Separation of transports: Use STDIO for local dev; use Streamable HTTP for remote/MCP clients in containerized environments.
Best practice: Treat the MCP server like any internal service. Limit network access, store secrets in a secret manager, and log agent tool calls for audit.
How do I set it up quickly?
Prerequisites: Python 3.11 or later, SignNow credentials, and environment variables configured.
Install and run (recommended):
|
1 2 3 4 |
pip install signnow-mcp-server sn-mcp serve # STDIO (local dev) # or sn-mcp http # Streamable HTTP (remote/Docker) |
To customize host/port for HTTP:
|
1 |
sn-mcp http --host 0.0.0.0 --port 8000 |
Default MCP HTTP path is /mcp (e.g., https://localhost:8000/mcp).
Using uvx (no local install):
|
1 |
uvx --from signnow-mcp-server sn-mcp serve |
Docker basics:
|
1 2 |
docker build -t sn-mcp-server . docker run --env-file .env -p 8000:8000 sn-mcp-server sn-mcp http --host 0.0.0.0 --port 8000 |
Prefer HTTP transport inside containers; STDIO in containers can be unreliable with many clients.
Docker Compose:
|
1 2 3 |
docker-compose up sn-mcp-server # or compose up all defined services docker-compose up |
Which connection method should I choose: STDIO or HTTP?
STDIO (local) — choose this when:
- You’re developing on a desktop with VS Code/Cursor or an MCP Inspector locally.
- You want the simplest path and minimal network surface.
- You need quick iteration without container networking.
HTTP (remote/containers) — choose this when:
- You deploy in Docker or on a remote host/orchestrator.
- Multiple clients need to connect to the same MCP endpoint.
- You want explicit host/port control and reverse proxy options.
How do I connect it to my AI tooling?
VS Code — GitHub Copilot Agent Mode / Cursor
Create .vscode/mcp.json or .cursor/mcp.json:
STDIO (local):
|
1 2 3 4 5 6 7 8 9 |
"signnow": { "command": "uvx", "args": ["--from", "signnow-mcp-server", "sn-mcp", "serve"], "env": { "SIGNNOW_USER_EMAIL": "${SIGNNOW_USER_EMAIL}", "SIGNNOW_PASSWORD": "${SIGNNOW_PASSWORD}", "SIGNNOW_API_BASIC_TOKEN": "${SIGNNOW_API_BASIC_TOKEN}" } } |
HTTP (remote):
|
1 2 3 4 5 6 7 8 |
{ "servers": { "signnow": { "type": "http", "url": "https://localhost:8000/mcp" } } } |
Then enable the signnow tools in Agent Mode and use them in prompts.
Claude Desktop
Open Settings → Developer → Edit config and add a new server entry (same values as above, STDIO only) under mcpServers. Save and restart Claude Desktop.
Glama (hosted MCP)
Provide credentials, deploy, and use the generated /mcp endpoint with your clients.
MCP Inspector (testing)
Run the server and connect via STDIO or https://localhost:8000/mcp to list tools, inspect schemas, and test calls.
What does a typical AI-driven eSignature workflow look like?
Goal: Create a document from a template → pre-fill fields → route to multiple recipients in a pre-defined order → monitor status → download the final document (all without leaving your chat or IDE).
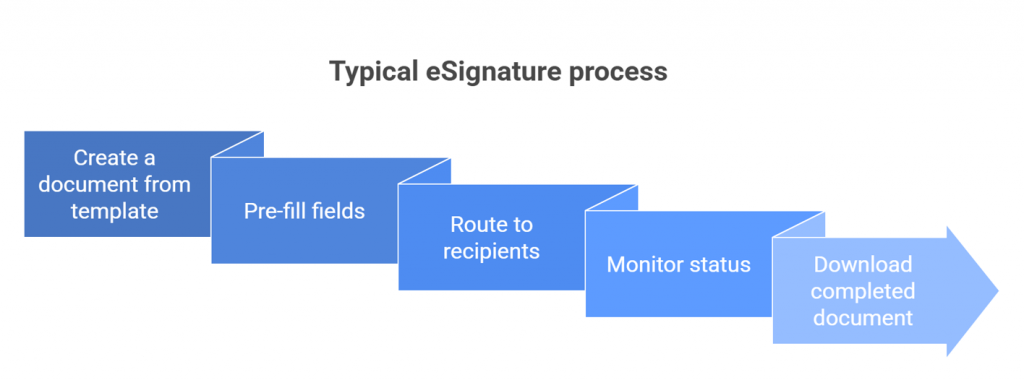
Suggested flow:
- Discover templates
The agent callslist_all_templatesto find the right template or group. - Create a document from the template
Usecreate_from_template(or the one-shot*_from_templatevariants). - Prefill fields (optional)
Callupdate_document_fieldsto write text values before sending. - Send invites or generate an embedded session
- Email route:
send_invitewith ordered recipients. - Embedded route:
create_embedded_inviteto sign in-app without email.
- Email route:
- Track progress
Pollget_invite_statusto confirm where each signer stands. - Retrieve the final document
Useget_document_download_link(merged outputs for groups are supported).
Pro tip: If you already know the template and action you want, use a one-shot tool like send_invite_from_template or create_embedded_invite_from_template to reduce steps and complexity.
Which invite method should I use for my use case?
- Email invites
Best for standard external workflows and compliance traceability. Supports ordered recipients and doesn’t require your app to host the signing UI. - Embedded signing
Best for product-led onboarding and in-app experiences. You create a signing link and control the session within your product. No email required. - Embedded sending & editor
Ideal when internal teams need to prepare documents in your app and adjust fields before routing to signers. - One-shot flows
Ideal for predictable, high-volume use cases where a single command should create a document from a template and take the next action immediately.
How do I configure environment variables safely?
Create a .env (or use your secrets manager) with the required variables:
Username/password (desktop dev flows):
|
1 2 3 |
SIGNNOW_USER_EMAIL=<email> SIGNNOW_PASSWORD=<password> SIGNNOW_API_BASIC_TOKEN=<base64 basic token> |
OAuth 2.0 (hosted/advanced):
|
1 2 3 4 5 6 7 8 |
SIGNNOW_CLIENT_ID=<client_id> SIGNNOW_CLIENT_SECRET=<client_secret> OAUTH_ISSUER=<issuer> ACCESS_TTL=3600 REFRESH_TTL=2592000 ALLOWED_REDIRECTS=<comma,separated,uris> OAUTH_RSA_PRIVATE_PEM=<PEM content> OAUTH_JWK_KID=<kid> |
API endpoints (defaults shown, override if needed)
|
1 2 3 |
SIGNNOW_APP_BASE=https://app.signnow.com SIGNNOW_API_BASE=https://api.signnow.com SIGNNOW_TOKEN=<optional direct API token> |
All settings are validated at startup via Pydantic settings. In production, persist your RSA private key to prevent token invalidation across restarts.
What business outcomes can this unlock?
- Faster document turnaround
Agents can trigger end-to-end signing workflows directly from tickets, chats, or internal tools. - Lower operational overhead
Reusable templates plus one-shot flows minimize manual steps. - Better customer experience
Embedded signing and sending keep users in your product. - Higher accuracy
Agents can prefill fields and consistently follow your standard operating procedures. - Governance & control
MCP tool boundaries, environment-based secrets, and OAuth options keep access auditable and scoped.
What SignNow API capabilities support this?
The underlying SignNow API lets you:
- Send documents and groups for signature in role-based order
- Create reusable templates from documents
- Pre-fill fields before sending
- Collect payments within the signing workflow
- Embed sending, signing, and editing into your app
- Track status in real time and download completed documents
These are the foundation for the MCP server’s toolset and agent workflows.

Are there example integrations with popular agent frameworks?
Yes. The repository includes working examples for LangChain, LlamaIndex, and SmolAgents. Each shows how to start the MCP server as a subprocess, map MCP tools to framework tool formats, and run an agent end-to-end.
Install the example dependencies, set your .env, and run the sample scripts — they demonstrate the same flows covered above.
Final thoughts
The SignNow MCP Server brings the power of AI agents to your eSignature workflows—without sacrificing control. You define the tools, guard the credentials, and decide where agents can act. From templates to final PDFs, the journey is fast, repeatable, and auditable.
Start your free trial with SignNow API and ship your first AI-powered eSignature workflow today.
FAQs
Can I run this in production?
Yes. Use HTTP transport behind your standard proxy and secret manager. Enable OAuth 2.0, set token TTLs, and persist your RSA private key so restarts do not invalidate tokens. Log tool calls for audit.
What’s the difference between email invites and embedded signing?
Email invites route signers via email links and are great for external recipients. Embedded signing keeps the signer within your application, eliminating the need for email, making it ideal for guided, in-app experiences.
How do I avoid agents over-reaching?
Expose only the tools you need, and wrap them in clear instructions and guardrails in your client. MCP already scopes access to specific capabilities, reducing the blast radius compared to raw API keys.
Can I prefill data before sending?
Yes. Use update_document_fields to populate or adjust text fields before sending an invite or launching an embedded session.
Where do I see exact tool schemas?
Use MCP Inspector or your client’s “tool details” view to browse tool names, arguments, and response shapes.
Glossary
MCP (Model Context Protocol): A protocol that lets tools expose well-defined capabilities to AI agents over STDIO or HTTP. SignNow uses MCP to expose eSignature tools safely.
Embedded signing: An in-app signature experience you host, started by generating an embedded invite link.
One-shot flow: A single command that creates a document from a template and immediately takes an action (invite, embedded signing, sending, or editing).
Invite status: The current progress for a document or group, including step-level details per signer/recipient.Document group: A collection of documents sent and tracked together, often delivered and downloaded as a merged output.
- What is the SignNow MCP Server?
- What can AI agents do with this server?
- How does the SignNow MCP Server keep AI agents secure?
- How do I set it up quickly?
- Which connection method should I choose: STDIO or HTTP?
- How do I connect it to my AI tooling?
- What does a typical AI-driven eSignature workflow look like?
- Which invite method should I use for my use case?
- How do I configure environment variables safely?
- What business outcomes can this unlock?
- What SignNow API capabilities support this?
- Are there example integrations with popular agent frameworks?
- Final thoughts
- FAQs
- Glossary