Bomb Threat Checklist Form


What is the Bomb Threat Checklist
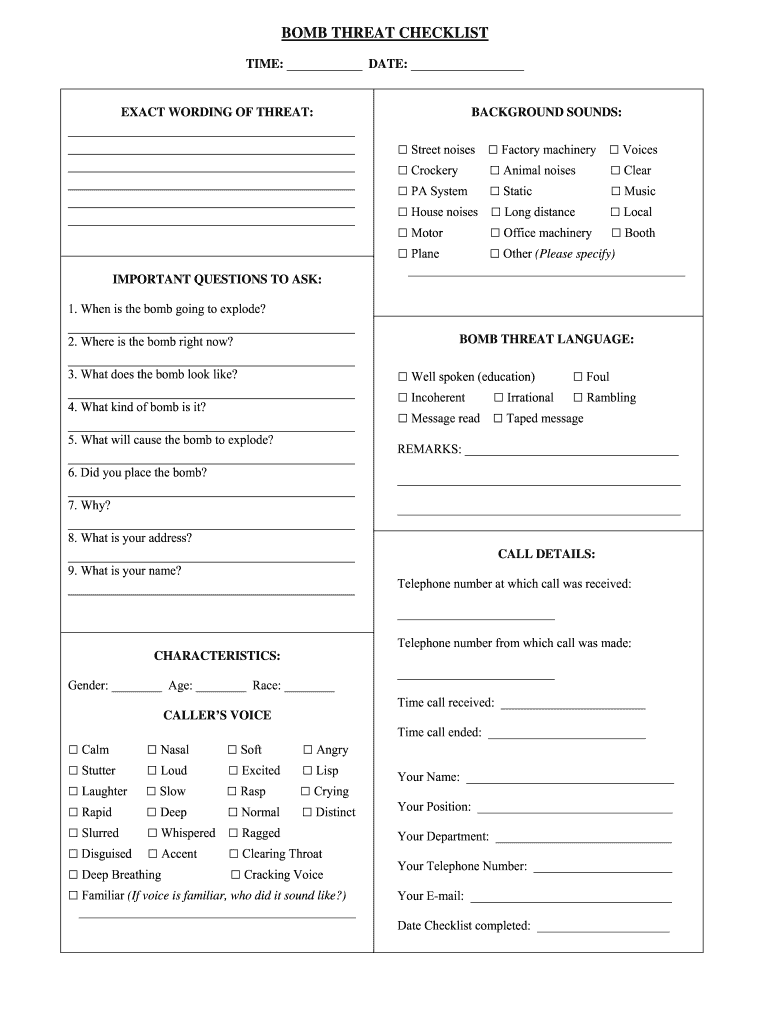
The Bomb Threat Checklist is a crucial document designed to assist individuals in responding effectively to bomb threats. It provides a structured approach to gathering essential information during such emergencies, ensuring that all necessary details are recorded. This checklist typically includes sections for noting the caller's identity, the nature of the threat, and specific instructions given by the caller. By following this checklist, individuals can enhance their response to bomb threats and ensure that vital information is communicated to authorities.
How to Use the Bomb Threat Checklist
Using the Bomb Threat Checklist involves a systematic approach to documenting information during a bomb threat situation. When a threat is received, the individual should remain calm and follow these steps:
- Start by recording the date and time of the call.
- Note the caller's voice characteristics, such as gender and tone.
- Document the exact words of the threat, including any specific locations mentioned.
- Ask questions if possible, such as the reason for the threat or the type of bomb.
- End the call as soon as possible and notify authorities immediately.
This structured approach ensures that all relevant details are captured, which is essential for law enforcement and emergency responders.
Steps to Complete the Bomb Threat Checklist
Completing the Bomb Threat Checklist requires attention to detail and a methodical approach. Here are the steps to follow:
- Begin by filling in the date and time of the incident.
- Record the caller's information, including any identifiable features.
- Write down the threat verbatim, ensuring accuracy in the wording.
- Include any background noises that may provide context, such as traffic or voices.
- Conclude by noting the time the call ended and the actions taken afterward.
Each step is vital for creating a comprehensive record that can aid in investigations and enhance safety protocols.
Legal Use of the Bomb Threat Checklist
The Bomb Threat Checklist is not only a practical tool but also has legal implications. It serves as an official record that can be used in investigations and legal proceedings. To ensure its legal validity, it is important to:
- Complete the checklist accurately and promptly after the threat is received.
- Maintain confidentiality and handle the information with care.
- Store the completed checklists securely to protect sensitive information.
By adhering to these guidelines, individuals can ensure that the checklist holds up in legal contexts and contributes to safety measures.
Key Elements of the Bomb Threat Checklist
The Bomb Threat Checklist includes several key elements that are essential for effective documentation. These elements typically consist of:
- The date and time of the threat.
- Details about the caller, including voice characteristics and any identifiable accents.
- The exact wording of the threat.
- Specific instructions or demands made by the caller.
- Background noises that may provide additional context.
Incorporating these elements ensures comprehensive documentation, which is vital for law enforcement and emergency response teams.
Examples of Using the Bomb Threat Checklist
Utilizing the Bomb Threat Checklist effectively can vary based on the circumstances. Here are a few examples of how it can be applied:
- In a school setting, a teacher receiving a bomb threat can use the checklist to document the call and alert school authorities.
- In a corporate environment, a receptionist can follow the checklist to ensure all details are recorded before contacting security personnel.
- During public events, event staff can utilize the checklist to maintain a record of any threats, assisting law enforcement in their response.
These examples illustrate the versatility of the Bomb Threat Checklist in various settings, emphasizing its importance in emergency preparedness.
Quick guide on how to complete bomb threat checklist form
Discover how to smoothly navigate the Bomb Threat Checklist completion with this simple guide
Utilizing electronic filing and document completion is becoming more widespread and is the preferred choice for many clients. It presents various benefits over outdated printed documents, such as convenience, time savings, enhanced precision, and security.
With applications like airSlate SignNow, you can locate, edit, authenticate, enhance, and dispatch your Bomb Threat Checklist without getting bogged down in endless printing and scanning. Follow this concise tutorial to initiate and implement your form.
Utilize these steps to obtain and complete Bomb Threat Checklist
- Begin by clicking the Get Form button to access your document in our editor.
- Follow the green label on the left that highlights mandatory fields so you don’t overlook them.
- Leverage our professional features to annotate, edit, sign, secure, and enhance your document.
- Protect your file or convert it into a fillable form using the appropriate tab functions.
- Review the document and check for errors or inconsistencies.
- Select DONE to complete the editing process.
- Change the name of your form or leave it as is.
- Choose the storage option where you want to keep your document, send it via USPS, or click the Download Now button to save your document.
If Bomb Threat Checklist isn’t what you are searching for, you can explore our extensive library of pre-uploaded forms that require minimal input. Experience our platform today!
Create this form in 5 minutes or less
FAQs
-
Do military members have to pay any fee for leave or fiancee forms?
NOOOOOOO. You are talking to a military romance scammer. I received an email from the US Army that directly answers your question that is pasted below please keep reading.I believe you are the victim of a military Romance Scam whereas the person you are talking to is a foreign national posing as an American Soldier claiming to be stationed overseas on a peacekeeping mission. That's the key to the scam they always claim to be on a peacekeeping mission.Part of their scam is saying that they have no access to their money that their mission is highly dangerous.If your boyfriend girlfriend/future husband/wife is asking you to do the following or has exhibited this behavior, it is a most likely a scam:Moves to private messaging site immediately after meeting you on Facebook or SnapChat or Instagram or some dating or social media site. Often times they delete the site you met them on right after they asked you to move to a more private messaging siteProfesses love to you very quickly & seems to quote poems and song lyrics along with using their own sort of broken language, as they profess their love and devotion quickly. They also showed concern for your health and love for your family.Promises marriage as soon as he/she gets to state for leave that they asked you to pay for.They Requests money (wire transfers) and Amazon, iTune ,Verizon, etc gift cards, for medicine, religious practices, and leaves to come home, internet access, complete job assignments, help sick friend, get him out of trouble, or anything that sounds fishy.The military does provide all the soldier needs including food medical Care and transportation for leave. Trust me, I lived it, you are probably being scammed. I am just trying to show you examples that you are most likely being connned.Below is an email response I received after I sent an inquiry to the US government when I discovered I was scammed. I received this wonderful response back with lots of useful links on how to find and report your scammer. And how to learn more about Romance Scams.Right now you can also copy the picture he gave you and do a google image search and you will hopefully see the pictures of the real person he is impersonating. this doesn't always work and take some digging. if you find the real person you can direct message them and alert them that their image is being used for scamming.Good Luck to you and I'm sorry this may be happening to you. please continue reading the government response I received below it's very informative. You have contacted an email that is monitored by the U.S. Army Criminal Investigation Command. Unfortunately, this is a common concern. We assure you there is never any reason to send money to anyone claiming to be a Soldier online. If you have only spoken with this person online, it is likely they are not a U.S. Soldier at all. If this is a suspected imposter social media profile, we urge you to report it to that platform as soon as possible. Please continue reading for more resources and answers to other frequently asked questions: How to report an imposter Facebook profile: Caution-https://www.facebook.com/help/16... < Caution-https://www.facebook.com/help/16... > Answers to frequently asked questions: - Soldiers and their loved ones are not charged money so that the Soldier can go on leave. - Soldiers are not charged money for secure communications or leave. - Soldiers do not need permission to get married. - Soldiers emails are in this format: john.doe.mil@mail.mil < Caution-mailto: john.doe.mil@mail.mil > anything ending in .us or .com is not an official email account. - Soldiers have medical insurance, which pays for their medical costs when treated at civilian health care facilities worldwide – family and friends do not need to pay their medical expenses. - Military aircraft are not used to transport Privately Owned Vehicles. - Army financial offices are not used to help Soldiers buy or sell items of any kind. - Soldiers deployed to Combat Zones do not need to solicit money from the public to feed or house themselves or their troops. - Deployed Soldiers do not find large unclaimed sums of money and need your help to get that money out of the country. Anyone who tells you one of the above-listed conditions/circumstances is true is likely posing as a Soldier and trying to steal money from you. We would urge you to immediately cease all contact with this individual. For more information on avoiding online scams and to report this crime, please see the following sites and articles: This article may help clarify some of the tricks social media scammers try to use to take advantage of people: Caution-https://www.army.mil/article/61432/< Caution-https://www.army.mil/article/61432/> CID advises vigilance against 'romance scams,' scammers impersonating Soldiers Caution-https://www.army.mil/article/180749 < Caution-https://www.army.mil/article/180749 > FBI Internet Crime Complaint Center: Caution-http://www.ic3.gov/default.aspx< Caution-http://www.ic3.gov/default.aspx> U.S. Army investigators warn public against romance scams: Caution-https://www.army.mil/article/130...< Caution-https://www.army.mil/article/130...> DOD warns troops, families to be cybercrime smart -Caution-http://www.army.mil/article/1450...< Caution-http://www.army.mil/article/1450...> Use caution with social networking Caution-https://www.army.mil/article/146...< Caution-https://www.army.mil/article/146...> Please see our frequently asked questions section under scams and legal issues. Caution-http://www.army.mil/faq/ < Caution-http://www.army.mil/faq/ > or visit Caution-http://www.cid.army.mil/ < Caution-http://www.cid.army.mil/ >. The challenge with most scams is determining if an individual is a legitimate member of the US Army. Based on the Privacy Act of 1974, we cannot provide this information. If concerned about a scam you may contact the Better Business Bureau (if it involves a solicitation for money), or local law enforcement. If you're involved in a Facebook or dating site scam, you are free to contact us direct; (571) 305-4056. If you have a social security number, you can find information about Soldiers online at Caution-https://www.dmdc.osd.mil/appj/sc... < Caution-https://www.dmdc.osd.mil/appj/sc... > . While this is a free search, it does not help you locate a retiree, but it can tell you if the Soldier is active duty or not. If more information is needed such as current duty station or location, you can contact the Commander Soldier's Records Data Center (SRDC) by phone or mail and they will help you locate individuals on active duty only, not retirees. There is a fee of $3.50 for businesses to use this service. The check or money order must be made out to the U.S. Treasury. It is not refundable. The address is: Commander Soldier's Records Data Center (SRDC) 8899 East 56th Street Indianapolis, IN 46249-5301 Phone: 1-866-771-6357 In addition, it is not possible to remove social networking site profiles without legitimate proof of identity theft or a scam. If you suspect fraud on this site, take a screenshot of any advances for money or impersonations and report the account on the social networking platform immediately. Please submit all information you have on this incident to Caution-www.ic3.gov < Caution-http://www.ic3.gov > (FBI website, Internet Criminal Complaint Center), immediately stop contact with the scammer (you are potentially providing them more information which can be used to scam you), and learn how to protect yourself against these scams at Caution-http://www.ftc.gov < Caution-http://www.ftc.gov > (Federal Trade Commission's website)
-
How can I fill out Google's intern host matching form to optimize my chances of receiving a match?
I was selected for a summer internship 2016.I tried to be very open while filling the preference form: I choose many products as my favorite products and I said I'm open about the team I want to join.I even was very open in the location and start date to get host matching interviews (I negotiated the start date in the interview until both me and my host were happy.) You could ask your recruiter to review your form (there are very cool and could help you a lot since they have a bigger experience).Do a search on the potential team.Before the interviews, try to find smart question that you are going to ask for the potential host (do a search on the team to find nice and deep questions to impress your host). Prepare well your resume.You are very likely not going to get algorithm/data structure questions like in the first round. It's going to be just some friendly chat if you are lucky. If your potential team is working on something like machine learning, expect that they are going to ask you questions about machine learning, courses related to machine learning you have and relevant experience (projects, internship). Of course you have to study that before the interview. Take as long time as you need if you feel rusty. It takes some time to get ready for the host matching (it's less than the technical interview) but it's worth it of course.
-
How do I fill out the form of DU CIC? I couldn't find the link to fill out the form.
Just register on the admission portal and during registration you will get an option for the entrance based course. Just register there. There is no separate form for DU CIC.
-
Why would an intelligent person send a fake bomb threat email to get out of finals at Harvard?
One reason is clear, to postpone the final exam. So, students can have more time to study and prepare for finals. In Eldo Kim case, assuming, he wasn't prepared for finals and want to take control to post-pone it. Hence, a strategy to pull a fake bomb. Now, the question I'd like to create in Quora is this, "What other safe strategy can Eldo Kim do in order to pull a postpone in finals?"
-
How do you know if you need to fill out a 1099 form?
Assuming that you are talking about 1099-MISC. Note that there are other 1099s.check this post - Form 1099 MISC Rules & RegulationsQuick answer - A Form 1099 MISC must be filed for each person to whom payment is made of:$600 or more for services performed for a trade or business by people not treated as employees;Rent or prizes and awards that are not for service ($600 or more) and royalties ($10 or more);any fishing boat proceeds,gross proceeds of $600, or more paid to an attorney during the year, orWithheld any federal income tax under the backup withholding rules regardless of the amount of the payment, etc.
Create this form in 5 minutes!
How to create an eSignature for the bomb threat checklist form
How to make an electronic signature for the Bomb Threat Checklist Form online
How to create an electronic signature for the Bomb Threat Checklist Form in Google Chrome
How to generate an electronic signature for signing the Bomb Threat Checklist Form in Gmail
How to create an eSignature for the Bomb Threat Checklist Form straight from your smart phone
How to create an electronic signature for the Bomb Threat Checklist Form on iOS
How to make an electronic signature for the Bomb Threat Checklist Form on Android devices
People also ask
-
What is a bomb threat checklist?
A bomb threat checklist is a tool designed to help individuals and organizations effectively respond to a bomb threat. It outlines critical steps to take when receiving a threat, ensuring safety and proper communication with authorities. Utilizing a bomb threat checklist can enhance your preparedness and response strategies.
-
How can airSlate SignNow help in managing a bomb threat checklist?
airSlate SignNow allows businesses to create, manage, and eSign customizable bomb threat checklists efficiently. The platform’s user-friendly interface simplifies the process of updating and sharing your checklist with team members. This ensures that everyone is informed and can act quickly if a bomb threat is received.
-
Is there a cost associated with using the bomb threat checklist feature in airSlate SignNow?
Pricing for airSlate SignNow is competitive and includes access to a variety of features, including the bomb threat checklist. You can choose from multiple subscription plans tailored to your needs, making it a cost-effective solution for businesses of all sizes. Visit our pricing page for detailed information.
-
What are the key features of the bomb threat checklist in airSlate SignNow?
The bomb threat checklist in airSlate SignNow includes customizable templates, eSignature capability, and secure document storage. These features ensure that your checklist not only meets legal requirements but is also easily accessible and updateable. This allows for a streamlined response during emergencies.
-
Can I integrate airSlate SignNow with other tools for my bomb threat checklist?
Yes, airSlate SignNow offers integrations with various business tools and platforms, allowing for a seamless workflow with your bomb threat checklist. You can connect it with communication tools, project management software, and more. These integrations help enhance collaboration and effectiveness during emergencies.
-
How does using a bomb threat checklist improve workplace safety?
Using a bomb threat checklist ensures that all employees know the correct procedures to follow in an emergency. It helps streamline communication and actions to minimize confusion and panic. Implementing such procedures can greatly improve overall workplace safety and preparedness.
-
How often should I update my bomb threat checklist?
Your bomb threat checklist should be reviewed and updated regularly, ideally at least once a year or whenever there are changes in personnel or procedures. Keeping the checklist current ensures that all staff are familiar with their roles during a bomb threat. airSlate SignNow makes it easy to update and distribute the latest version.
Get more for Bomb Threat Checklist
Find out other Bomb Threat Checklist
- eSign Arkansas Legal LLC Operating Agreement Simple
- eSign Alabama Life Sciences Residential Lease Agreement Fast
- How To eSign Arkansas Legal Residential Lease Agreement
- Help Me With eSign California Legal Promissory Note Template
- eSign Colorado Legal Operating Agreement Safe
- How To eSign Colorado Legal POA
- eSign Insurance Document New Jersey Online
- eSign Insurance Form New Jersey Online
- eSign Colorado Life Sciences LLC Operating Agreement Now
- eSign Hawaii Life Sciences Letter Of Intent Easy
- Help Me With eSign Hawaii Life Sciences Cease And Desist Letter
- eSign Hawaii Life Sciences Lease Termination Letter Mobile
- eSign Hawaii Life Sciences Permission Slip Free
- eSign Florida Legal Warranty Deed Safe
- Help Me With eSign North Dakota Insurance Residential Lease Agreement
- eSign Life Sciences Word Kansas Fast
- eSign Georgia Legal Last Will And Testament Fast
- eSign Oklahoma Insurance Business Associate Agreement Mobile
- eSign Louisiana Life Sciences Month To Month Lease Online
- eSign Legal Form Hawaii Secure