Collaborate on Customize Invoice for Security with Ease Using airSlate SignNow
See how it works!Click here to sign a sample doc
See airSlate SignNow eSignatures in action
be ready to get more
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
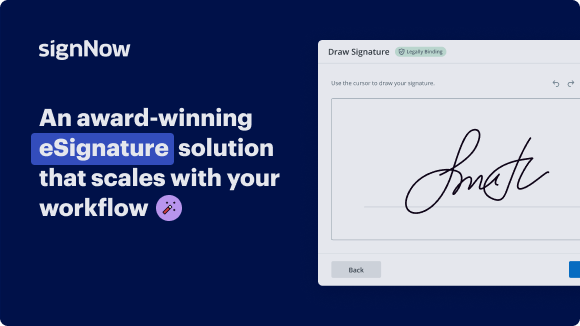
Add your legally binding signature
Create your signature in seconds on any desktop computer or mobile device, even while offline. Type, draw, or upload an image of your signature.
Integrate via API
Deliver a seamless eSignature experience from any website, CRM, or custom app — anywhere and anytime.
Send conditional documents
Organize multiple documents in groups and automatically route them for recipients in a role-based order.
Share documents via an invite link
Collect signatures faster by sharing your documents with multiple recipients via a link — no need to add recipient email addresses.
Save time with reusable templates
Create unlimited templates of your most-used documents. Make your templates easy to complete by adding customizable fillable fields.
Improve team collaboration
Create teams within airSlate SignNow to securely collaborate on documents and templates. Send the approved version to every signer.
Our user reviews speak for themselves






Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
airSlate SignNow solutions for better efficiency
Keep contracts protected
Enhance your document security and keep contracts safe from unauthorized access with dual-factor authentication options. Ask your recipients to prove their identity before opening a contract to customize invoice for security.
Stay mobile while eSigning
Install the airSlate SignNow app on your iOS or Android device and close deals from anywhere, 24/7. Work with forms and contracts even offline and customize invoice for security later when your internet connection is restored.
Integrate eSignatures into your business apps
Incorporate airSlate SignNow into your business applications to quickly customize invoice for security without switching between windows and tabs. Benefit from airSlate SignNow integrations to save time and effort while eSigning forms in just a few clicks.
Generate fillable forms with smart fields
Update any document with fillable fields, make them required or optional, or add conditions for them to appear. Make sure signers complete your form correctly by assigning roles to fields.
Close deals and get paid promptly
Collect documents from clients and partners in minutes instead of weeks. Ask your signers to customize invoice for security and include a charge request field to your sample to automatically collect payments during the contract signing.
be ready to get more
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Learn how to simplify your process on the customize invoice for Security with airSlate SignNow.
Looking for a way to simplify your invoicing process? Look no further, and adhere to these simple guidelines to effortlessly work together on the customize invoice for Security or request signatures on it with our easy-to-use platform:
- Set up an account starting a free trial and log in with your email sign-in information.
- Upload a document up to 10MB you need to eSign from your device or the cloud.
- Continue by opening your uploaded invoice in the editor.
- Execute all the necessary steps with the document using the tools from the toolbar.
- Press Save and Close to keep all the modifications made.
- Send or share your document for signing with all the required recipients.
Looks like the customize invoice for Security process has just become easier! With airSlate SignNow’s easy-to-use platform, you can easily upload and send invoices for eSignatures. No more printing, signing by hand, and scanning. Start our platform’s free trial and it enhances the entire process for you.
How it works
Access the cloud from any device and upload a file
Edit & eSign it remotely
Forward the executed form to your recipient
be ready to get more
Get legally-binding signatures now!
FAQs
-
How can I customize invoices for security with airSlate SignNow?
With airSlate SignNow, you can easily customize invoices for security by adding specific fields, templates, and branding elements that align with your business needs. This ensures that all sensitive information is protected and that the invoice reflects your corporate identity. The user-friendly interface allows you to make these adjustments swiftly, enhancing both security and aesthetics. -
What are the key features for customizing invoices for security?
The key features for customizing invoices for security in airSlate SignNow include document encryption, customizable fields, and the ability to set access permissions. These features ensure that only authorized individuals can view or alter critical invoice data, boosting your overall security. Additionally, the template options allow you to design invoices that meet compliance regulations. -
Is there a cost associated with customizing invoices for security?
Yes, there is a cost associated with using airSlate SignNow's features to customize invoices for security, depending on the subscription plan you choose. Each plan offers varying levels of access to customization tools and security features. You can explore our pricing page for detailed information concerning the features included in each plan. -
Can I integrate airSlate SignNow with other tools to enhance invoice security?
Absolutely! airSlate SignNow integrates with various business applications, allowing you to enhance invoice security further. By connecting with tools like CRM systems and accounting software, you can streamline processes while ensuring sensitive invoice data stays protected. Check our integrations page to see all the compatible software. -
What benefits can I expect when I customize invoices for security?
Customizing invoices for security with airSlate SignNow provides multiple benefits, including improved data protection and compliance with industry standards. You can also enhance your brand image by presenting professional, tailored invoices. Additionally, this customization fosters trust with clients, as they see you take security seriously. -
How can I ensure the security of customized invoices?
To ensure the security of customized invoices, airSlate SignNow employs advanced encryption technologies and allows you to set user permission levels. By restricting access to sensitive data and using secure electronic signing processes, you can safeguard your invoices. Regularly reviewing your security settings is also advisable to maintain high security standards. -
Is customer support available for help with customizing invoices for security?
Yes, airSlate SignNow offers customer support to assist you with customizing invoices for security. Our support team is knowledgeable about all features and can help you utilize the tools effectively to enhance your invoice security. You can signNow out through our support channels for timely and efficient assistance.
What active users are saying — customize invoice for security
Get more for customize invoice for security
- Create a Free Online Petition Maker for Administration
- Free Online Petition Maker for Customer Service
- Free Online Petition Maker for Customer Support
- Free Online Petition Maker for Technical Support
- Create Free Online Petition Maker for Marketing
- Free Online Petition Maker for Logistics
- Free Online Petition Maker for Operations
- Free Online Petition Maker for Planning
Find out other customize invoice for security
- Digital Signature Legitimacy for Procurement in United ...
- Unlock Digital Signature Legitimateness for Procurement ...
- Electronic Signature Legality for IT in Canada - ...
- Unlocking the Power of Electronic Signature Legality ...
- Electronic Signature Legality for Sales in United ...
- Electronic Signature Legality for Quality Assurance in ...
- Unlock the Power of Electronic Signature Lawfulness for ...
- Unlock Electronic Signature Legitimacy for Accounting ...
- Boost Sales with Electronic Signature Legitimateness in ...
- Electronic Signature Legitimateness for Logistics in ...
- Unlock Electronic Signature Legitimateness for ...
- Unlock the Power of Online Signature Legality for ...
- Enhance Online Signature Lawfulness for Technical ...
- Unlocking the Power of Online Signature Legitimacy for ...
- Unlock the Power of Online Signature Legitimateness for ...
- Boost Your Procurement Process with Legitimate Online ...
- Boost Your Business with eSignature Legitimateness in ...
- Unlock Electronic Signature Legitimateness for ...
- Electronic signature licitness for small businesses in ...
- Unlock the Power of Electronic Signature Licitness for ...