Collaborate on Law Firm Invoice Template for Security with Ease Using airSlate SignNow
See how it works!Click here to sign a sample doc
See airSlate SignNow eSignatures in action
be ready to get more
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
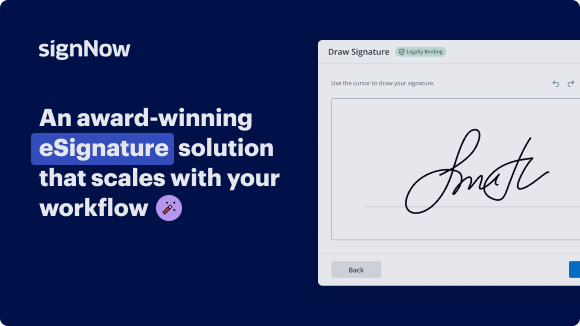
Add your legally binding signature
Create your signature in seconds on any desktop computer or mobile device, even while offline. Type, draw, or upload an image of your signature.
Integrate via API
Deliver a seamless eSignature experience from any website, CRM, or custom app — anywhere and anytime.
Send conditional documents
Organize multiple documents in groups and automatically route them for recipients in a role-based order.
Share documents via an invite link
Collect signatures faster by sharing your documents with multiple recipients via a link — no need to add recipient email addresses.
Save time with reusable templates
Create unlimited templates of your most-used documents. Make your templates easy to complete by adding customizable fillable fields.
Improve team collaboration
Create teams within airSlate SignNow to securely collaborate on documents and templates. Send the approved version to every signer.
Our user reviews speak for themselves






Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
airSlate SignNow solutions for better efficiency
Keep contracts protected
Enhance your document security and keep contracts safe from unauthorized access with dual-factor authentication options. Ask your recipients to prove their identity before opening a contract to law firm invoice template for security.
Stay mobile while eSigning
Install the airSlate SignNow app on your iOS or Android device and close deals from anywhere, 24/7. Work with forms and contracts even offline and law firm invoice template for security later when your internet connection is restored.
Integrate eSignatures into your business apps
Incorporate airSlate SignNow into your business applications to quickly law firm invoice template for security without switching between windows and tabs. Benefit from airSlate SignNow integrations to save time and effort while eSigning forms in just a few clicks.
Generate fillable forms with smart fields
Update any document with fillable fields, make them required or optional, or add conditions for them to appear. Make sure signers complete your form correctly by assigning roles to fields.
Close deals and get paid promptly
Collect documents from clients and partners in minutes instead of weeks. Ask your signers to law firm invoice template for security and include a charge request field to your sample to automatically collect payments during the contract signing.
be ready to get more
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Explore how to streamline your workflow on the law firm invoice template for Security with airSlate SignNow.
Seeking a way to simplify your invoicing process? Look no further, and follow these simple steps to easily work together on the law firm invoice template for Security or ask for signatures on it with our intuitive service:
- Set up an account starting a free trial and log in with your email sign-in information.
- Upload a document up to 10MB you need to eSign from your device or the cloud.
- Proceed by opening your uploaded invoice in the editor.
- Take all the required actions with the document using the tools from the toolbar.
- Press Save and Close to keep all the changes performed.
- Send or share your document for signing with all the needed recipients.
Looks like the law firm invoice template for Security workflow has just become easier! With airSlate SignNow’s intuitive service, you can easily upload and send invoices for eSignatures. No more producing a hard copy, manual signing, and scanning. Start our platform’s free trial and it simplifies the whole process for you.
How it works
Access the cloud from any device and upload a file
Edit & eSign it remotely
Forward the executed form to your recipient
be ready to get more
Get legally-binding signatures now!
FAQs
-
What is a law firm invoice template for security?
A law firm invoice template for security is a structured document designed specifically for law firms to itemize and present their fees clearly. This template ensures that billing is transparent and professional, helping to maintain trust with clients. Using such a template can streamline the invoicing process, allowing law firms to focus more on their legal services. -
How can the law firm invoice template for security improve billing efficiency?
The law firm invoice template for security can signNowly improve billing efficiency by providing a standardized format that can be easily filled out and modified. This eliminates the need for lawyers to create invoices from scratch, saving valuable time. It also reduces errors, ensuring clients receive accurate billing as per agreed terms. -
Is the law firm invoice template for security customizable?
Yes, the law firm invoice template for security is fully customizable to meet the specific needs of each law firm. You can add your firm’s branding, adjust items and services listed, and configure payment terms. Customization helps convey your firm's identity while maintaining professionalism in client communications. -
What features does the law firm invoice template for security offer?
The law firm invoice template for security typically includes features like itemized billing, summation of totals, tax calculations, and payment instructions. It may also provide options for digital signatures, making it easy for clients to approve invoices quickly. These features help ensure that the billing process is seamless and professional. -
How does using a law firm invoice template for security benefit clients?
Using a law firm invoice template for security benefits clients by providing clear and understandable billing statements. It ensures that clients can easily track the services provided and costs incurred, reducing confusion and disputes. Enhanced transparency reflects a law firm’s commitment to ethical practices, fostering trust with clients. -
Can the law firm invoice template for security integrate with other software?
Absolutely! The law firm invoice template for security can seamlessly integrate with various accounting and practice management software. This integration enables automatic syncing of billing information, which reduces administrative work and ensures consistency in financial records. Such compatibility enhances operational efficiency for law firms. -
What pricing options are available for the law firm invoice template for security?
Pricing for the law firm invoice template for security may vary depending on the provider and the features included. Many platforms offer subscription-based pricing or one-time purchase options. Assessing different plans will help you find the most cost-effective solution that meets your firm’s invoicing needs.
What active users are saying — law firm invoice template for security
Get more for law firm invoice template for security
- Credit Note Invoice Format for Nonprofit
- Credit note invoice format for Real Estate
- Credit Note Invoice Format for Retail Trade
- Credit note invoice format for Staffing
- Credit Note Invoice Format for Technology Industry
- Credit note invoice format for Animal science
- Credit Note Invoice Format for Banking
- Credit note invoice format for Hospitality
Find out other law firm invoice template for security
- ESignature Lawfulness for Cease and Desist Letter in ...
- Unlock the Power of eSignature Legitimateness for ...
- ESignature Legitimateness for Business Associate ...
- ESignature Legitimateness for Non-Compete Agreement in ...
- Enhance eSignature Legitimateness for Polygraph Consent ...
- Unlock the power of eSignature licitness for Stock ...
- Unlocking the Power of Digital Signature Legality for ...
- Ensuring Compliance with Australian Digital Signature ...
- Digital Signature Legitimacy for Sick Leave Policy in ...
- Enhance Digital Signature Legitimateness for Commercial ...
- Digital Signature Legitimateness for Addressing ...
- Ensuring digital signature licitness for Toll ...
- Understanding Electronic Signature Legality for ...
- Ensuring Electronic Signature Lawfulness for Contract ...
- Understanding the Lawfulness of Electronic Signatures ...
- Unlocking the Power of Electronic Signature Legitimacy ...
- Enhance Freelance Contract Legitimacy with Electronic ...
- Electronic Signature Legitimateness for Contracts in ...
- Ensuring Electronic Signature Legitimateness for ...
- Enhance Electronic Signature Legitimateness for Home ...