Effective Software Development Invoice Example for Security
See how it works!Click here to sign a sample doc
See airSlate SignNow eSignatures in action
be ready to get more
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
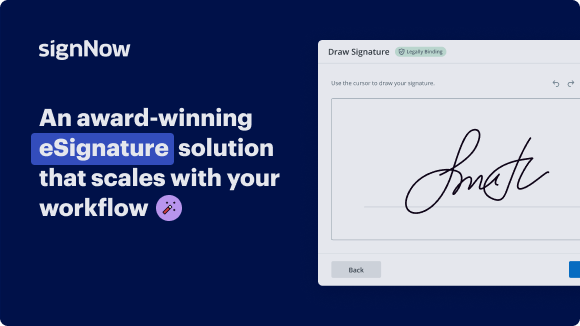
Add your legally binding signature
Create your signature in seconds on any desktop computer or mobile device, even while offline. Type, draw, or upload an image of your signature.
Integrate via API
Deliver a seamless eSignature experience from any website, CRM, or custom app — anywhere and anytime.
Send conditional documents
Organize multiple documents in groups and automatically route them for recipients in a role-based order.
Share documents via an invite link
Collect signatures faster by sharing your documents with multiple recipients via a link — no need to add recipient email addresses.
Save time with reusable templates
Create unlimited templates of your most-used documents. Make your templates easy to complete by adding customizable fillable fields.
Improve team collaboration
Create teams within airSlate SignNow to securely collaborate on documents and templates. Send the approved version to every signer.
Our user reviews speak for themselves






Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
airSlate SignNow solutions for better efficiency
Keep contracts protected
Enhance your document security and keep contracts safe from unauthorized access with dual-factor authentication options. Ask your recipients to prove their identity before opening a contract to software development invoice example for security.
Stay mobile while eSigning
Install the airSlate SignNow app on your iOS or Android device and close deals from anywhere, 24/7. Work with forms and contracts even offline and software development invoice example for security later when your internet connection is restored.
Integrate eSignatures into your business apps
Incorporate airSlate SignNow into your business applications to quickly software development invoice example for security without switching between windows and tabs. Benefit from airSlate SignNow integrations to save time and effort while eSigning forms in just a few clicks.
Generate fillable forms with smart fields
Update any document with fillable fields, make them required or optional, or add conditions for them to appear. Make sure signers complete your form correctly by assigning roles to fields.
Close deals and get paid promptly
Collect documents from clients and partners in minutes instead of weeks. Ask your signers to software development invoice example for security and include a charge request field to your sample to automatically collect payments during the contract signing.
be ready to get more
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Software development invoice example for Security
Creating and managing invoices for software development projects in the security sector can be streamlined using airSlate SignNow. This powerful tool not only facilitates document signing but also enables businesses to efficiently handle invoicing, thereby improving cash flow and project tracking.
Software development invoice example for Security
- Open your browser and navigate to the airSlate SignNow website.
- Create an account for a free trial or log in if you are an existing user.
- Choose the document that requires signing or distribution.
- Transform frequently used documents into reusable templates.
- Upload the selected document and customize it by adding necessary fields or information.
- Add your signature and designate fields for recipients' signatures.
- Proceed to finalize the document and send the eSignature invitation.
By adopting airSlate SignNow, businesses can benefit from a robust solution that enhances their document management efficiency. The platform is designed for scalability, making it especially suitable for small to medium-sized businesses.
With transparency in pricing and excellent customer support available 24/7 for all paid plans, airSlate SignNow is an investment that offers remarkable ROI. Start optimizing your invoicing process today!
How it works
Access the cloud from any device and upload a file
Edit & eSign it remotely
Forward the executed form to your recipient
be ready to get more
Get legally-binding signatures now!
FAQs
-
What is a software development invoice example for security?
A software development invoice example for security is a template that outlines the costs associated with developing secure software applications. It typically includes line items for development hours, security audits, and compliance measures. This example helps businesses ensure that they account for security in their budgeting. -
How can airSlate SignNow assist with creating a software development invoice example for security?
airSlate SignNow offers customizable templates that make it easy to create a software development invoice example for security. Users can quickly input their specific services, costs, and security-related items. This streamlines the invoicing process and ensures no critical security aspects are overlooked. -
Are there features in airSlate SignNow that enhance the security of my invoices?
Yes, airSlate SignNow includes features that enhance the security of your invoices, such as encryption and advanced user authentication. These features ensure that your software development invoice example for security is only accessible to authorized personnel. This added layer of protection can help prevent sensitive information from being compromised. -
What pricing plans does airSlate SignNow offer for using its invoicing tools?
airSlate SignNow offers flexible pricing plans that cater to various business needs. Users can choose plans that include unlimited eSignatures and access to templates like the software development invoice example for security. This ensures that businesses can find a plan that fits their budget and requirements. -
Can I integrate airSlate SignNow with other software tools for invoicing?
Yes, airSlate SignNow seamlessly integrates with several popular accounting and software management tools. This allows you to easily import your software development invoice example for security into your existing workflow. The integrations help streamline your financial processes, making management more efficient. -
What benefits does using a software development invoice example for security provide?
Using a software development invoice example for security ensures clarity and accuracy in billing clients for secure software development projects. This can help reduce disputes and improve cash flow. Additionally, it highlights security as a priority in your services, enhancing trust with clients. -
Is there customer support available for creating software development invoices?
Absolutely, airSlate SignNow offers robust customer support to assist you in creating a software development invoice example for security. Whether you have questions about template customization or need help with integrations, their team provides guidance. This support ensures you make the most of the invoicing tools.
What active users are saying — software development invoice example for security
Get more for software development invoice example for security
- Sign marriage contract template
- Sign owner operator contract agreement
- Sign photo booth rental contract template
- Sign printable caregiver contract template
- Sign printable personal training contract template
- Sign sample subcontractor agreement
- Sign subcontractor contract template
- Sign vendor contract agreement
Find out other software development invoice example for security
- Unlock Electronic Signature Legitimateness for ...
- Electronic signature licitness for small businesses in ...
- Unlock the Power of Electronic Signature Licitness for ...
- Unlock the Power of Online Signature Legality for ...
- Unlock the Power of eSignature Legality for Independent ...
- Unlock the Power of eSignature Legitimacy for Interview ...
- Boost eSignature legitimacy for Military Leave Policy
- Ensure eSignature Legality for Your Affidavit of ...
- Boost Your Memorandum of Understanding with airSlate ...
- Electronic Signature Legality for Storage Rental ...
- Ensure Electronic Signature Lawfulness for Profit ...
- Boost your Manufacturing and Supply Agreement ...
- ESignature Legality for General Power of Attorney in ...
- Unlock eSignature legality for Distributor Agreement in ...
- ESignature Legality for Property Inspection Report in ...
- The Legal Power of eSigning General Power of Attorney ...
- Unlock eSignature Legitimateness for Business Associate ...
- Unlock eSignature Legitimateness for Payroll Deduction ...
- ESignature Legality for Non-Compete Agreement in UAE
- Ensure eSignature Legality for Advertising Agreement in ...