Collaborate on Architect Invoice Template for Security with Ease Using airSlate SignNow
See how it works!Click here to sign a sample doc
See airSlate SignNow eSignatures in action
be ready to get more
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
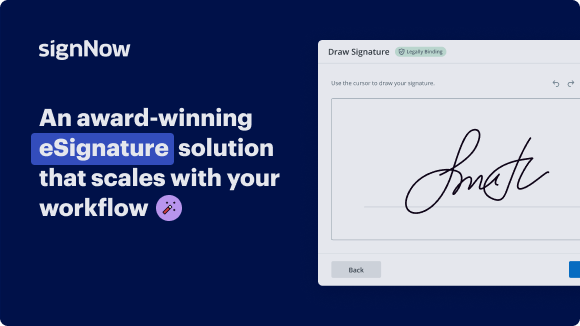
Add your legally binding signature
Create your signature in seconds on any desktop computer or mobile device, even while offline. Type, draw, or upload an image of your signature.
Integrate via API
Deliver a seamless eSignature experience from any website, CRM, or custom app — anywhere and anytime.
Send conditional documents
Organize multiple documents in groups and automatically route them for recipients in a role-based order.
Share documents via an invite link
Collect signatures faster by sharing your documents with multiple recipients via a link — no need to add recipient email addresses.
Save time with reusable templates
Create unlimited templates of your most-used documents. Make your templates easy to complete by adding customizable fillable fields.
Improve team collaboration
Create teams within airSlate SignNow to securely collaborate on documents and templates. Send the approved version to every signer.
Our user reviews speak for themselves






Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
airSlate SignNow solutions for better efficiency
Keep contracts protected
Enhance your document security and keep contracts safe from unauthorized access with dual-factor authentication options. Ask your recipients to prove their identity before opening a contract to architect invoice template for security.
Stay mobile while eSigning
Install the airSlate SignNow app on your iOS or Android device and close deals from anywhere, 24/7. Work with forms and contracts even offline and architect invoice template for security later when your internet connection is restored.
Integrate eSignatures into your business apps
Incorporate airSlate SignNow into your business applications to quickly architect invoice template for security without switching between windows and tabs. Benefit from airSlate SignNow integrations to save time and effort while eSigning forms in just a few clicks.
Generate fillable forms with smart fields
Update any document with fillable fields, make them required or optional, or add conditions for them to appear. Make sure signers complete your form correctly by assigning roles to fields.
Close deals and get paid promptly
Collect documents from clients and partners in minutes instead of weeks. Ask your signers to architect invoice template for security and include a charge request field to your sample to automatically collect payments during the contract signing.
be ready to get more
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Explore how to ease your workflow on the architect invoice template for Security with airSlate SignNow.
Searching for a way to streamline your invoicing process? Look no further, and follow these quick steps to conveniently work together on the architect invoice template for Security or request signatures on it with our easy-to-use service:
- Set up an account starting a free trial and log in with your email sign-in information.
- Upload a document up to 10MB you need to sign electronically from your computer or the online storage.
- Continue by opening your uploaded invoice in the editor.
- Take all the required actions with the document using the tools from the toolbar.
- Click on Save and Close to keep all the modifications made.
- Send or share your document for signing with all the needed recipients.
Looks like the architect invoice template for Security workflow has just turned more straightforward! With airSlate SignNow’s easy-to-use service, you can easily upload and send invoices for electronic signatures. No more generating a printout, signing by hand, and scanning. Start our platform’s free trial and it optimizes the entire process for you.
How it works
Access the cloud from any device and upload a file
Edit & eSign it remotely
Forward the executed form to your recipient
be ready to get more
Get legally-binding signatures now!
FAQs
-
What is an architect invoice template for security?
An architect invoice template for security is a customizable document designed to streamline billing processes for architectural services related to security projects. It includes designated areas for project details, client information, and itemized costs, making it easier for architects to communicate their services and payment terms. -
How can the architect invoice template for security benefit my business?
Using an architect invoice template for security can improve your billing efficiency and professionalism. By having a well-structured invoice, you can enhance client trust and ensure timely payments, which is essential for maintaining cash flow in your architectural firm. -
Are there any costs associated with using the architect invoice template for security?
The architect invoice template for security is often included in the airSlate SignNow subscription plan, which provides cost-effective options to suit different business needs. You can choose a plan that fits your budget and enjoy the benefits of unlimited access to our templates and features. -
Can I customize the architect invoice template for security?
Yes, the architect invoice template for security is fully customizable. You can easily alter the design, add your branding, and modify the layout and fields to suit your specific requirements, allowing you to create an invoice that reflects your unique business style. -
What features are included in the architect invoice template for security?
The architect invoice template for security includes essential features such as customizable fields, digital signature options, and automated payment reminders. These tools help simplify the billing process and enhance transaction efficiency, ensuring you can focus on your core architectural tasks. -
Is the architect invoice template for security compatible with other software?
Yes, the architect invoice template for security can be easily integrated with various accounting and project management software. This compatibility allows for seamless data transfer and minimizes the chance of errors in your invoicing process. -
How do I send invoices created with the architect invoice template for security?
Invoicing with the architect invoice template for security is straightforward. You can send your completed invoices directly via email or share a secure link for your clients to review and sign, all done within the airSlate SignNow platform for maximum convenience.
What active users are saying — architect invoice template for security
Get more for architect invoice template for security
- Guest house bill format for Communications & Media
- Guest House Bill Format for Construction Industry
- Guest house bill format for Financial Services
- Guest House Bill Format for Government
- Guest house bill format for Healthcare
- Guest House Bill Format for Higher Education
- Guest house bill format for Insurance Industry
- Guest House Bill Format for Legal Services
Find out other architect invoice template for security
- Experience the power of a virtual signature online
- Effortless iPad digital signature app for seamless ...
- Create your unique signature maker for PDF effortlessly
- Access your e-signature account login with ease and ...
- Sign PDF documents online in Chrome effortlessly
- Digitize my signature easily with airSlate SignNow
- Discover our free PDF viewer with digital signature
- Discover the best online signature analysis tool for ...
- Discover HIPAA-compliant electronic signature software ...
- Streamline your workflow with our easy sign application ...
- Discover the best free PDF document sign tool for your ...
- Download free bulk PDF signer for seamless document ...
- Streamline your workflow with our online document ...
- Experience seamless resman portal sign-up for ...
- Effortlessly access signmaster software file download
- Discover the best HIPAA-compliant digital signature ...
- Discover the best PDF reader for multiple signatures
- Discover the best PDF sign tool free online for your ...
- Discover electronic signature solutions for lawyers ...
- Sign and fill online your free PDF document ...