Get Your Bootstrap Invoice Template for Security Streamlined
See airSlate SignNow eSignatures in action
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
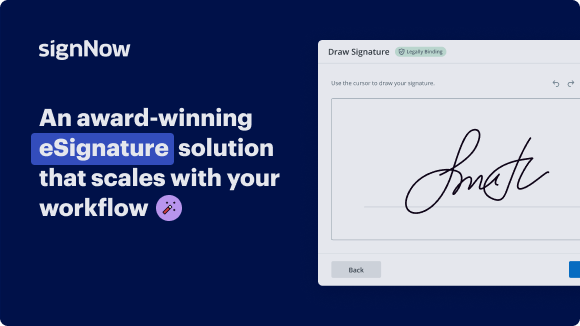
Add your legally binding signature
Integrate via API
Send conditional documents
Share documents via an invite link
Save time with reusable templates
Improve team collaboration
Our user reviews speak for themselves






airSlate SignNow solutions for better efficiency
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Bootstrap invoice template for security
Creating digital documents has never been easier with airSlate SignNow, especially when using a bootstrap invoice template for security. This platform allows users to sign, send, and manage documents efficiently while maintaining a secure environment. Whether you're a small business or part of a mid-sized organization, these features ensure that you can streamline your workflows confidently.
Using a bootstrap invoice template for security
- 1. Visit the airSlate SignNow official website in your web browser.
- 2. Create a new account with a free trial or log in if you already have one.
- 3. Choose a document you wish to sign or send out for signatures.
- 4. If you plan to use this document in the future, convert it into a reusable template.
- 5. Open the document to make necessary changes: add fillable fields or include additional information.
- 6. Apply your signature and designate signature fields for recipients.
- 7. Proceed by clicking 'Continue' to arrange and send an eSignature request.
With airSlate SignNow, businesses experience exceptional returns on investment thanks to its rich feature set at a reasonable cost. It's specifically designed to be user-friendly and scale effectively for small to mid-sized businesses.
Experience seamless document management with airSlate SignNow. Explore the platform today to elevate your digital signing process!
How it works
Get legally-binding signatures now!
FAQs
-
What is a bootstrap invoice template for security?
A bootstrap invoice template for security is a customizable invoice design that leverages the Bootstrap framework, ensuring both aesthetic appeal and functionality. This template helps businesses present their billing in a professional manner while enhancing security features to protect sensitive information. Utilizing such templates can streamline your invoicing process. -
Why should I use a bootstrap invoice template for security?
Using a bootstrap invoice template for security ensures that your invoices are not only visually appealing but also secure from unauthorized access. This template integrates advanced security features, allowing your clients to feel confident when handling sensitive billing information. It's an efficient way to maintain professionalism while safeguarding your data. -
What features are included in the bootstrap invoice template for security?
The bootstrap invoice template for security typically includes customizable fields, responsive design for mobile compatibility, and built-in security features such as password protection. Additionally, it may offer options for electronic signatures and integration with payment gateways. These features make it an excellent choice for businesses looking to streamline their billing process. -
How much does the bootstrap invoice template for security cost?
Pricing for a bootstrap invoice template for security can vary depending on the provider and the level of customization you require. Many templates are offered at reasonable prices, often including one-time purchase options or subscription-based models. It's important to compare offerings to find the best solution that fits your budget. -
Can the bootstrap invoice template for security be integrated with other software?
Yes, the bootstrap invoice template for security is designed to facilitate integration with various software applications. This could include accounting software, CRM systems, and payment platforms, enhancing the overall efficiency of your invoicing process. Integration options allow for seamless data transfer and management. -
Is it easy to customize the bootstrap invoice template for security?
Absolutely! The bootstrap invoice template for security is built with user-friendliness in mind, allowing for easy customization. Users can modify fonts, colors, and layouts according to their branding needs without extensive technical skills. This flexibility enables businesses to create a personalized invoice that reflects their identity. -
What benefits can businesses expect from using a bootstrap invoice template for security?
Businesses using a bootstrap invoice template for security can expect reduced billing errors, improved cash flow, and enhanced client trust due to better security measures. An organized and professional invoice fosters positive relationships with clients, while the template’s security features protect sensitive data. This ultimately promotes efficiency in invoicing operations.
What active users are saying — bootstrap invoice template for security
Get more for bootstrap invoice template for security
- Discover the best email address service for seamless document signing
- Create your unique email alias with our email alias creator
- Simplify email creation with airSlate SignNow
- Elevate your productivity with our email creation platform
- Create stunning emails effortlessly with airSlate SignNow email creator
- Create a professional email domain for business to enhance your brand
- Enhance your business communication with email for business
- Create your perfect documents with our email generator
Find out other bootstrap invoice template for security
- Discover the best free PDF document sign tool for your ...
- Download free bulk PDF signer for seamless document ...
- Streamline your workflow with our online document ...
- Experience seamless resman portal sign-up for ...
- Effortlessly access signmaster software file download
- Discover the best HIPAA-compliant digital signature ...
- Discover the best PDF reader for multiple signatures
- Discover the best PDF sign tool free online for your ...
- Discover electronic signature solutions for lawyers ...
- Sign and fill online your free PDF document ...
- Discover the best electronic signing software for your ...
- Experience the best free web PDF editor for signatures
- Discover the top free document signing tools for ...
- Sign documents effortlessly with our Word free ...
- Easily add electronic signature to Google Docs for ...
- How to use Google Docs for signing documents with ease
- How to add a digital signature to a Google form easily ...
- Discover HIPAA-compliant electronic signature solutions ...
- Discover our HIPAA-compliant signature solution for ...
- Effortless online signature login for streamlined ...