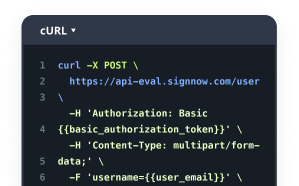
Boost R&D Efficiency with Digital Signature Legitimacy in Canada
- Quick to start
- Easy-to-use
- 24/7 support
Simplified document journeys for small teams and individuals



We spread the word about digital transformation
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.







Your complete how-to guide - digital signature legitimacy for rd in canada
Digital Signature Legitimacy for R&D in Canada
In today's fast-paced world, ensuring the legitimacy of digital signatures is crucial, especially for research and development purposes in Canada. By following the steps below, you can utilize airSlate SignNow to streamline your document signing process with confidence in the authenticity of your signatures.
How to Utilize airSlate SignNow for Secure Document Signing:
- Launch the airSlate SignNow web page in your browser.
- Sign up for a free trial or log in.
- Upload a document you want to sign or send for signing.
- If you're going to reuse your document later, turn it into a template.
- Open your file and make edits: add fillable fields or insert information.
- Sign your document and add signature fields for the recipients.
- Click Continue to set up and send an eSignature invite.
airSlate SignNow empowers businesses to send and eSign documents with an easy-to-use, cost-effective solution. It offers great ROI with a rich feature set, scalability tailored for SMBs and Mid-Market, transparent pricing without hidden fees, and superior 24/7 support for all paid plans.
Experience the benefits of airSlate SignNow today and enhance your document signing process seamlessly.
How it works
Rate your experience
What is the digital signature legitimacy for rd in canada
The digital signature legitimacy for rd in Canada refers to the legal recognition and acceptance of electronic signatures within the regulatory framework governing electronic documents. In Canada, digital signatures are considered valid under the Personal Information Protection and Electronic Documents Act (PIPEDA) and various provincial laws. This legitimacy ensures that documents signed electronically carry the same weight as those signed with traditional handwritten signatures, provided they meet specific criteria set forth by the law.
How to use the digital signature legitimacy for rd in canada
To utilize the digital signature legitimacy for rd in Canada, users must ensure that their electronic signatures comply with legal standards. This involves using a secure eSignature platform, such as airSlate SignNow, to create and manage digital signatures. Users can fill out the required documents online, apply their eSignature, and send them for signature to other parties. The process is straightforward, allowing for efficient document management while ensuring compliance with legal requirements.
Steps to complete the digital signature legitimacy for rd in canada
Completing the digital signature legitimacy for rd in Canada involves several key steps:
- Access the document that requires a digital signature.
- Use airSlate SignNow to fill out the necessary fields within the document.
- Apply your eSignature by selecting the designated area for signing.
- Send the document for signature to other parties, if needed.
- Once all signatures are collected, securely store the completed document for your records.
Legal use of the digital signature legitimacy for rd in canada
The legal use of digital signatures in Canada is governed by both federal and provincial legislation. These laws stipulate that digital signatures must be created using secure methods that ensure authenticity and integrity. Users must also maintain proper records of the signing process, including timestamps and any relevant metadata, to support the validity of the signature in case of disputes. By following these legal guidelines, users can confidently utilize digital signatures in their transactions.
Security & Compliance Guidelines
When using digital signatures, it is essential to adhere to security and compliance guidelines to protect sensitive information. Users should choose an eSignature solution that offers encryption, secure access controls, and audit trails. These features help ensure that documents are signed securely and that any changes made to the document after signing are tracked. Compliance with applicable laws, such as PIPEDA, is crucial to maintain the legitimacy of digital signatures.
Examples of using the digital signature legitimacy for rd in canada
Digital signatures can be applied in various scenarios in Canada, including:
- Signing contracts and agreements between businesses.
- Submitting tax documents electronically.
- Approving HR documents, such as employment contracts and policy acknowledgments.
- Completing real estate transactions, including purchase agreements.
These examples illustrate the versatility and efficiency of digital signatures in streamlining workflows while ensuring legal compliance.
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
FAQs
-
What is the digital signature legitimacy for rd in Canada?
Digital signature legitimacy for rd in Canada refers to the legal recognition of electronic signatures in the context of remote document signing. In Canada, digital signatures are governed by the Personal Information Protection and Electronic Documents Act (PIPEDA), ensuring that they hold the same legal weight as traditional handwritten signatures.
-
How does airSlate SignNow ensure digital signature legitimacy for rd in Canada?
airSlate SignNow ensures digital signature legitimacy for rd in Canada by adhering to the legal standards set forth by Canadian law. Our platform employs advanced encryption and authentication methods, ensuring that every signed document is secure and legally binding.
-
What are the pricing options for airSlate SignNow?
airSlate SignNow offers flexible pricing plans to accommodate various business needs. Our plans are designed to provide cost-effective solutions while ensuring compliance with digital signature legitimacy for rd in Canada, making it accessible for businesses of all sizes.
-
What features does airSlate SignNow offer for digital signatures?
airSlate SignNow offers a range of features including customizable templates, real-time tracking, and secure cloud storage. These features enhance the user experience while ensuring digital signature legitimacy for rd in Canada, allowing businesses to streamline their document workflows.
-
What are the benefits of using airSlate SignNow for digital signatures?
Using airSlate SignNow for digital signatures provides numerous benefits, including increased efficiency, reduced paper usage, and enhanced security. By ensuring digital signature legitimacy for rd in Canada, businesses can confidently transition to a paperless environment.
-
Can airSlate SignNow integrate with other software?
Yes, airSlate SignNow can seamlessly integrate with various software applications, including CRM and project management tools. This integration supports the digital signature legitimacy for rd in Canada, allowing businesses to incorporate eSigning into their existing workflows effortlessly.
-
Is airSlate SignNow compliant with Canadian regulations?
Absolutely, airSlate SignNow is fully compliant with Canadian regulations regarding digital signatures. Our commitment to maintaining digital signature legitimacy for rd in Canada ensures that all signed documents are legally valid and enforceable.