Download Your Sample Invoice PDF for Security Effortlessly
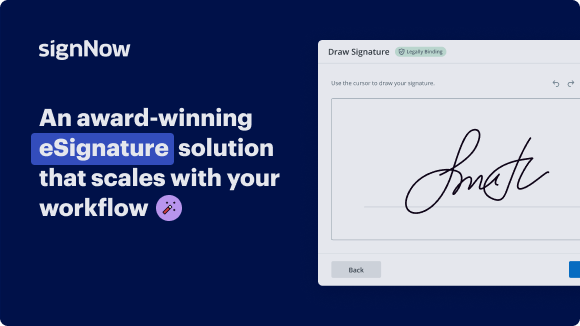
See airSlate SignNow eSignatures in action
Choose a better solution
Move your business forward with the airSlate SignNow eSignature solution
Add your legally binding signature
Integrate via API
Send conditional documents
Share documents via an invite link
Save time with reusable templates
Improve team collaboration
Our user reviews speak for themselves






airSlate SignNow solutions for better efficiency
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Sample invoice pdf download for security
Creating a sample invoice PDF can streamline the process of managing financial transactions and ensure security. With airSlate SignNow, businesses can efficiently send and eSign documents while enjoying robust features tailored for their needs. In this guide, we will walk you through the steps of obtaining a sample invoice PDF while leveraging the benefits of airSlate SignNow.
Sample invoice pdf download for security
- Access airSlate SignNow by opening its website in your browser.
- Create a free trial account or log in to your existing account.
- Upload the invoice document that requires a signature or distribution.
- If you plan to use this invoice format frequently, convert it into a reusable template.
- Open the uploaded document and customize it: add fillable fields or insert necessary information.
- Sign the invoice and add signature fields for the recipients' convenience.
- Click Continue to finalize the setup and invite others to eSign the document.
By utilizing airSlate SignNow, businesses gain an effective solution with high returns on investment. It is designed to be user-friendly and scalable, meeting the specific needs of small to mid-sized businesses. Moreover, the transparent pricing structure ensures no unexpected fees, allowing you to focus on your work.
Furthermore, airSlate SignNow offers comprehensive 24/7 support for all premium plans. Start your document management journey today and experience the efficiency of airSlate SignNow.
How it works
Get legally-binding signatures now!
FAQs
-
What is a sample invoice PDF download for security?
A sample invoice PDF download for security is a template that businesses can use to create invoices while ensuring sensitive information is safeguarded. It provides a practical example that can be downloaded and customized for individual security needs, ensuring financial transactions are both secure and efficient. -
How can I create a sample invoice PDF download for security?
Creating a sample invoice PDF download for security is easy with airSlate SignNow. Simply use our intuitive platform to customize the template according to your business requirements, ensuring that any sensitive data is adequately protected throughout the process. -
Is airSlate SignNow a cost-effective solution for sample invoice PDF download for security?
Yes, airSlate SignNow offers a cost-effective solution for businesses needing a sample invoice PDF download for security. Our pricing plans are designed to fit various budgets, allowing users to access essential features without compromising security or functionality. -
What features does airSlate SignNow offer for handling sample invoices?
airSlate SignNow provides numerous features for handling sample invoices, including electronic signatures, secure document storage, and customizable templates. These features ensure that your sample invoice PDF download for security is not only easy to use but also compliant with industry standards. -
Can I integrate airSlate SignNow with other tools for managing invoices?
Absolutely! airSlate SignNow can be easily integrated with various tools and platforms, enhancing your workflow for managing sample invoice PDF downloads for security. This integration helps streamline processes such as accounting, CRM, and project management. -
What are the benefits of using a sample invoice PDF download for security?
The benefits of using a sample invoice PDF download for security include improved organization, reduced errors, and enhanced data protection. With airSlate SignNow, businesses can ensure that all sensitive information is handled securely while streamlining their invoicing process. -
How does eSigning enhance the security of sample invoices?
eSigning enhances the security of sample invoices by providing a secure, verifiable method of approval that eliminates the risk of unauthorized access. airSlate SignNow’s electronic signature feature ensures that your sample invoice PDF download for security is protected and legally binding.
What active users are saying — sample invoice pdf download for security
Get more for sample invoice pdf download for security
- Experience the Qvidian Demo for Life Sciences
- Experience the qvidian demo for mortgage
- Get Your qvidian demo for nonprofit
- Qvidian demo for real estate
- Discover Qvidian Demo for Retail Trade
- Experience Qvidian Demo for Staffing
- Qvidian Demo for Technology Industry
- Get Qvidian Demo for Animal Science
Find out other sample invoice pdf download for security
- Unlocking the Power of eSignature Legality for Support ...
- Boost Your Procurement with Legitimate eSignatures in ...
- Unlock eSignature Legitimateness for Logistics in ...
- Ensuring Digital Signature Legality for Support in ...
- The Definitive Guide to Digital Signature Legality for ...
- Ensuring the Legality of Digital Signatures for ...
- Unlock the Power of Digital Signature Legality for ...
- Digital Signature Legality for Quality Assurance in ...
- Digital Signature Legitimacy for Procurement in United ...
- Unlock Digital Signature Legitimateness for Procurement ...
- Electronic Signature Legality for IT in Canada - ...
- Unlocking the Power of Electronic Signature Legality ...
- Electronic Signature Legality for Sales in United ...
- Electronic Signature Legality for Quality Assurance in ...
- Unlock the Power of Electronic Signature Lawfulness for ...
- Unlock Electronic Signature Legitimacy for Accounting ...
- Boost Sales with Electronic Signature Legitimateness in ...
- Electronic Signature Legitimateness for Logistics in ...
- Unlock Electronic Signature Legitimateness for ...
- Unlock the Power of Online Signature Legality for ...