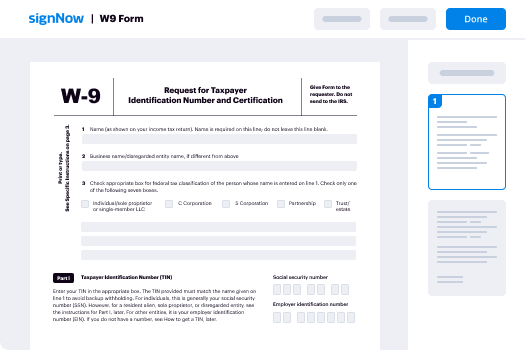
Help Me With Implement Sign in SalesForce
Contact Sales
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Discover the easiest way to Implement Sign in SalesForce with our powerful tools that go beyond eSignature. Sign documents and collect data, signatures, and payments from other parties from a single solution.
Robust integration and API capabilities
Enable the airSlate SignNow API and supercharge your workspace systems with eSignature tools. Streamline data routing and record updates with out-of-the-box integrations.
Advanced security and compliance
Set up your eSignature workflows while staying compliant with major eSignature, data protection, and eCommerce laws. Use airSlate SignNow to make every interaction with a document secure and compliant.
Various collaboration tools
Make communication and interaction within your team more transparent and effective. Accomplish more with minimal efforts on your side and add value to the business.
Enjoyable and stress-free signing experience
Delight your partners and employees with a straightforward way of signing documents. Make document approval flexible and precise.
Extensive support
Explore a range of video tutorials and guides on how to Implement Sign in SalesForce. Get all the help you need from our dedicated support team.
Keep your eSignature workflows on track
Make the signing process more streamlined and uniform
Take control of every aspect of the document execution process. eSign, send out for signature, manage, route, and save your documents in a single secure solution.
Add and collect signatures from anywhere
Let your customers and your team stay connected even when offline. Access airSlate SignNow to Implement Sign in SalesForce from any platform or device: your laptop, mobile phone, or tablet.
Ensure error-free results with reusable templates
Templatize frequently used documents to save time and reduce the risk of common errors when sending out copies for signing.
Stay compliant and secure when eSigning
Use airSlate SignNow to Implement Sign in SalesForce and ensure the integrity and security of your data at every step of the document execution cycle.
Enjoy the ease of setup and onboarding process
Have your eSignature workflow up and running in minutes. Take advantage of numerous detailed guides and tutorials, or contact our dedicated support team to make the most out of the airSlate SignNow functionality.
Benefit from integrations and API for maximum efficiency
Integrate with a rich selection of productivity and data storage tools. Create a more encrypted and seamless signing experience with the airSlate SignNow API.
Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
Our user reviews speak for themselves






How to access your airSlate SignNow account with Salesforce credentials
Accessing your airSlate SignNow account through Salesforce credentials is a simple procedure that enables you to effectively oversee your document signing requirements. With airSlate SignNow, companies can utilize a strong tool crafted for smooth electronic signatures and document management, boosting productivity and collaboration.
Procedure to log in to airSlate SignNow using Salesforce credentials
- Launch your web browser and go to the airSlate SignNow homepage.
- Select the option to log in and choose Salesforce as your login option.
- If asked, provide your Salesforce details to verify your account.
- After logging in, you can upload a document that needs to be signed or distributed.
- For documents you intend to use frequently, create a reusable template.
- Open your document to make essential modifications, like adding fillable fields or other details.
- Insert signature fields for your own signature and for signers who need to sign.
- Click 'Continue' to set up and send an eSignature invitation.
In summary, airSlate SignNow streamlines the e-signature workflow, offering businesses a budget-friendly solution that maximizes return on investment. Its intuitive interface and strong features are specifically designed to meet the needs of small and medium-sized enterprises.
Ready to improve your document signing experience? Log in to airSlate SignNow today and explore the advantages of seamless e-signatures!
How it works
Upload & open your document in the editor
Fill it out and eSign it in minutes
Save the signed document or share it with others
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is the airSlate SignNow Salesforce integration?
The airSlate SignNow Salesforce integration allows users to streamline their document signing processes directly within Salesforce. By using this integration, you can send and eSign documents without leaving the Salesforce environment, enhancing efficiency and collaboration. Accessing your airSlate SignNow account through your Salesforce login simplifies workflows for your team.
-
How do I access airSlate SignNow with my Salesforce login?
To access airSlate SignNow using your Salesforce login, simply navigate to the SignNow app within Salesforce after installation. You will be prompted to log in with your existing Salesforce credentials, allowing for seamless access to eSigning features and document management tools. This integration ensures that your experience remains smooth and user-friendly.
-
What are the pricing options for airSlate SignNow with Salesforce?
airSlate SignNow offers flexible pricing plans that cater to different business sizes and needs. You can choose from various subscription options, providing access to essential features, including the Salesforce integration. For detailed pricing information, visit our website or contact our sales team and explore how you can maximize the value of your Salesforce login.
-
Can I customize documents in airSlate SignNow with Salesforce?
Yes, airSlate SignNow allows users to customize documents before sending them for eSignature through Salesforce. You can add fields, merge data from Salesforce records, and create templates that suit your business needs. This level of customization enhances your document workflows and ensures that every document is tailored correctly.
-
What are the benefits of using airSlate SignNow with Salesforce?
Using airSlate SignNow with Salesforce provides signNow benefits, including increased efficiency in document handling and improved team collaboration. By integrating these platforms, you reduce time spent on manual tasks and enhance the eSigning experience for your clients. Your Salesforce login gives you direct access to powerful tools that streamline your business processes.
-
Is airSlate SignNow secure for eSigning documents?
Absolutely! airSlate SignNow prioritizes security and compliance, ensuring that all documents signed via the platform are protected. With features like encryption and audit trails, you can trust that your eSigning processes through Salesforce login meet industry standards and regulations.
-
How can I troubleshoot login issues with airSlate SignNow and Salesforce?
If you encounter issues logging into airSlate SignNow using your Salesforce login, first check your credentials for accuracy. Ensure that you have the necessary permissions set in Salesforce to access the SignNow integration. If problems persist, consider signNowing out to our support team for assistance in resolving any technical difficulties.
-
How does the Salesforce system work?
Salesforce is a cloud-based Customer Relationship Management (CRM) platform. In terms of market share, it is the #1 CRM platform today across the globe. Salesforce says that more than 150,000 companies are using their technology. Several industries use Salesforce which includes the retail, manufacturing, finance, and hospitality industries.As an advanced CRM, Salesforce manages the relationships of companies to their prospects or customers. Salesforce enhances these relationships by helping companies in their sales, marketing, and support processes. Think of Salesforce as a storage of relevant customer data. This pieces of information are then used by businesses to provide a personalized and efficient service to their customers.Salesforce has a Customer Success Platform made up of different apps and products such as:Sales CloudMarketing CloudService CloudCommunity CloudAnalytics CloudApp CloudData CloudIoTSalesforce has a multitenant architecture. This means that every Salesforce customer, regardless of company size and type of purchase, has the same platform and system. Multitenancy also means that they don't need to worry about downtime and upgrades. Salesforce rolls out three (3) free updates a year to every customer simultaneously and seamlessly.A lot of companies choose Salesforce because it is customizable and scalable. Salesforce has its own app store, which is the AppExchage. If your business wants to extend Salesforce's functionality, you can find third-party apps in the AppExchange. Every app that businesses need like CTI tools that connect phone systems with Salesforce or email automation solutions for their marketing campaigns can be found in the AppExchange.It is somewhat impossible to explain in words how Salesforce really works and what it can do for your business. What I recommend is for you to sign-up for their free trial. See for yourself what benefits can your business get by implementing this reliable piece of technology.
-
I am strong in the demo/closing phase of my sales process but weak in the appointment setting phase. What has helped others impr
Get to a point where you no longer have to set our own demos by hiring SDR or an assistant. If you can't do that in the foreseeable future try to increase the amount of referrals you get and genuine inbound interest. Those 2 sources of leads tend to have shorter sales cycles and go through first phases of the sales cycle relatively quickly so that you can get to the point you are strong in fast.Other thing you can do is improving your game in first stages. Simple process you can perform on yourself: map every action (especially the little things) you need to do during the sales cycle based on your previous sales cycles. Get rid of as many of them as you can and try to automate as much of those you can't get rid of you can so that you can get quicker through phases you seem not be the best at. Last thing: look at touch points with your clients during your sales cycle and think how can you make them as friction less as you can. Couple of hacks which helped me to optimise my sales cycle are:CRM - pipedrive (although we'll propably migrate to salesforce sometime soon)Inserting my skype ID into the footer of my e-mailCalendly which eased up setting meetingsImplementing an easier, faster and cheaper payment system Implementing a faster deal signing process
-
Is it easy to implement Salesforce?
SFDC is so broad, I can safely say one could spend their entire career learning, modeling and signNowing themselves for various aspects of the platform. There's just basic SFDC (Salesforce.com) and then there are other areas; Service Cloud, Sales Cloud, Heroku, Data.com, etc.The best advice I would give before even attempting to do anything "real" is to do the following;1. Sign up for a developer account (it's free - forever)2. Go through the http://wiki.developerforce.com/p... - examples by examples. It's basically all there - The problem I find is that people with software developer experience try to "beat into submission" their current experience to the SFDC platform.That, IMHO why SFDC is seen as "hard to learn" - it's not that it's hard. it's just hard to mentally ditch your previous experience (or at least tweak the heck out of it).Some For-instances - *. The APEX language, even though it's "java-like" is simply not Java.*. The Visualforce language, although "HTML-like" is simply not HTML or javascript. Further, the architecture of how it works is completely different from how thing work in typical web server environments.*. SOQL/SOSL Data queries are not SQL. The typical scenario is, many companies that have big expensive development staffs that try to just "pick up" SFDC, run into huge problems. Usually involving large licensing fees (upwards of $65/month/user to $250/month) and some completely befuddled developers....And then in come the consultants - billing out at about $250/hour (and up)Soon companies can be hemorrhaging money. SFDC has a lot of advantages - multi-tenant architecture, guaranteed availability, mobile apps, APIs, great, friendly user interface, internationalization, JSON/RESTful interfaces, lots of extensibility, a great user community.... and lots more. BUT- Learning the SFDC platform is infrastructure programming, pure and simple, with a lot of "clicks-not-code" activity.I've found it hard to convince java programmers, for instance, that (s)he can implement a workflow and/or Validation rule to do what they need to do, rather than sling a bunch of lines of code into a trigger or anonymous APEX to have things done.To learn Salesforce, throw your java/SQL/HTML (well most of your HTML) experience away, and just make it through the workbooks in the link I provided above.... THEN - determine if it's for you.There are so many specific tricks to learning how to build a really robust SFDC implementation, that it can seem daunting at first.... however, it's absolutely amazing to me how many people simply have not gone through the workbooks.... It's usually my first question: "have your developers gone through the Force.com workbook?"
-
Should a startup use InfusionSoft or AutopilotHQ?
I've used both and I would recommend Autopilot between these two options. It's a tool progressing in the right direction and put together much better than Infusionsoft. If you're B2B, and can afford it, I would also look into HubSpot as it's the best tool in this arena in my opinion. Autopilot is great for B2C though, even a better option than HubSpot in some cases. Unfortunately it's a case by case basis depending upon your company's needs and should be assessed this way before choosing one.
-
What are some ways to make implementation of company-wide single sign-on successful?
In the single sign-on implementation, there are various identity as a service vendors and you can check out the Gartner quadrant for Identity and Access Management as a Service (IDaaS) here. Some vendors are: Okta, OneLogin, Azure, PingIdentity (Now Vista Equity Partners), Centrify, Google, etc. Without going in-depth, there are two providers here in this single sign-on workflow: 1) Identity provider (who can act as the master for the identity) and 2) Service provider (application that needs to be accessed - Salesforce, Pagerduty, Amazon,Dropbox, etc). Here are ten concrete steps for a successful single sign-on implementation:Create Application MatrixAs part of assessing the need for SSO, you might have done this already. For a successful implementation, it's very important to identify all the applications that you want to roll-out in different phases. Think about quick but real wins. What apps do you want to integrate with your identity provider first? Sometimes, if employees do not have two-factor enabled for an app and there's enough non-compliance, you should consider those apps first and enforce 2FA behind the identity provider (ex: Okta or OneLogin). This must be the first and foremost step for a successful SSO implementation.ArchitectureAs an example, do you want AD or Google apps to be the delegated master? For instance, if you decide Active Directory as the master, identity provider will be delegating all authentication requests to your Active directory allowing users to sign in to with your identity provider with their AD credentials. The IAM solution should automatically import the existing group hierarchy from Active Directory, simplifying the deployment.There are DaaS solutions available if you do not have LDAP or Active Directory. DaaS solutions connect users to a wide variety of IT resources, including: Mac, Windows, and Linux devices as well as applications located both on-premise and in the cloud. If you do not have any of these solutions, design your architecture so that your identity provider will be the master who can authenticate and authorize based on local groups and roles.Scope of the roll-out:Which apps in the organization are SWA (Secure web authentication) and which apps in the organization are SAML (applications that understand security assertion mark up language)?Licenses: For some applications, if you want to enable SAML or provisioning, you would need additional licenses. For example, unless you have Slack's Enterprise plan, you cannot integrate SAML with Slack. Again, this should be carefully scoped out to fully account for the costs.Do you want provisioning to be enabled for the applications that support it? You need to be extremely careful with this. Some applications such as Dropbox and Google Apps provide these capabilities. If you remove/disassociate an application from a user, they will be automatically deprovisioned in the respective application as well. Same goes for provisioning as well. Deprovisioning accounts for inactive users bolsters security and aids in preparing for audits and compliance reporting.Do you want to enable both organization managed apps and user managed apps? Some orgs just want to expose only the company approved enterprise applications.Multi-factor authenticationYou want to audit your existing applications on what value this single sign on tool provides. Do you already have most of your critical apps behind two-factor? Is it enabled for all critical apps currently? Will this implementation/roll-out provide signNow security advantage or more of a user-convenience? This helps you prioritize this project accordingly.As MFA provides more security, it's also important on the risk appetite for your organization. Do you want to enforce MFA for people logging in within the office/corporate network? If so, plan accordingly so you want to whitelist your corporate network IP's.SLA, Response times, & AvailabilityAs part of the evaluation of the SSO tool, you might have already researched about the cost of downtime, service level outages, and any system failures seen with identity provider. If the identity provider network goes down, all the apps that have SAML enabled (Big Bang) cannot be accessible (unless you change the configuration).Ensure that the IAM solution can integrate with multiple Active Directory domains/forests and/or LDAP directories so that even if one domain controller is down, your users can still authenticate to the other controller via delegated authenticationThe identity providers offer local agents to sync passwords, import user repositories, and keep a constant sync of your identity store. As part of the plan, make sure to deploy multiple agents and install them on your servers.Shared accountsIf there are shared accounts employees use, you need to identify the owners and plan this ahead of the single sign-on roll-out. Whether you use Office 365 or Google Apps, make sure you have a list of these shared accounts and provide the ability for these owners to login to these shared accounts. Mail delegation is one solution how those owners can login to those accounts after the SAML integration.Implementation windowSince the SAML implementation for some applications is “All-or-Nothing”, this can affect the way people access applications. There can be a signNow downtime depending on the application.Remember you need to involve all the other service providers (ex: Quip, Pagerduty, Amazon, Salesforce, Slack) and can make the necessary changes on their end during the same time. For example, they would need to know all employee email ID's, meta-data from your identity provider and enable the application configuration (SAML) at the same time to minimize the downtime.Integrate the tool/logs as part of your logging and continuous monitoringSingle sign-on logs should be integrated into your log aggregation and monitoring solution. Log critical events (login name, source address, geo-location, application access date & time, success or failure, User-Agent, etc) and forward it to your local log collector and integrate this process as part of your security operations. Make sure your security operations team is trained completely to analyze and respond to intrusions and suspicious events.As part of your data retention policies, ensure that the SSO logs are retained appropriately with your data retention practices.Contractors & Temp employeesContractors and temp employees usually are not part of all groups and channels employees belong to. On rare occasions, if your contractors access your corporate apps/tools, you want to make sure they are aware about the roll-out and clear instructions are provided. This is important especially if you do not have a strict delineation thereby forcing SSO layer to all the apps they access.Testing Group & FeedbackThis is a very critical component of a successful single sign-on roll-out. You are changing the way that people sign-in to different applications. Even though there is a huge user convenience aspect to this, everyone do not see the same way. Include all teams (including few senior management folks) as part of beta testing your single sign-on solution. Ensure that every piece of feedback is properly addressed.Start small, start engaging your employees, and sign-on securely.
-
What areas should a new salesforce admin focus on for getting a job?
Go through Salesforce to get your basic administrator certification.Salesforce CertificationThey provide the guidance, videos and technical information you need to learn. You can also get a free developer license to practice with or without the certification.Being proactive will help you stand out and you can get that first certification fairly quickly (1–2 weeks).To gain real life experience, you can study the Non-profit edition and find a local non-profit to help with a free implementation. They get it free for up to 10 users and a small organization won’t be as taxing on your time. Be up front about why you want to help and really understand the value in it for them in the long run. You’ll gain experience selling it and experience doing the administrative work.Aside from that, go find as many consulting firms as you can and sign up for their email blasts so that you can keep up with their work and potential openings. Start building that network on LinkedIn with personalized connect requests and be really straight about your goals. You’ll be amazed at how generous the Salesforce community can be.To your success!www.aaronhowerton.com
-
Should we implement Salesforce ourselves or hire a Salesforce partner?
Salesforce Partners are absolutely the best path to success because of their expertise and experience. They are capable of providing impeccable solutions to the company needing Salesforce to manage their business. Because of their experience, they bring to the table the best practices and accelerators which will enable the customers to implement Salesforce the right way and quickly. You don’t have to reinvent the wheel by doing the implementation yourself unless you have prior implementation experience.It is not just the Technical experience, many Salesforce partners have business consultants as part of the implementation team who has the domain expertise and will understand your business. The business consultant will work with you to define the “To-Be” business process which will enable you and your team to do things faster and better. You don’t want to just move what you are doing manually or in another system to Salesforce. You need to see identify gaps in the existing system and larger opportunities which will enable you to maximize your investment in Salesforce. Salesforce partners can help you decide the appropriate org architecture that is needed.In addition to it, Salesforce Partners have access to partner enablement resources, training, and certification programs which allows them to keep up to speed with the innovation happening in the Salesforce Platform and in turn enable the customers to take advantages of the new features and functionality. Salesforce has 3 releases in a year and have hundreds of enhancements/features going in each release. They offer strategic guidance and are flexible and can tailor an engagement to fit your specific requirements.
Trusted esignature solution— what our customers are saying
be ready to get more
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
When a client enters information (such as a password) into the online form on , the information is encrypted so the client cannot see it. An authorized representative for the client, called a "Doe Representative," must enter the information into the "Signature" field to complete the signature.
How do you know an electronic signature is real?
That you have the signature of an actual person that signed it.
And, of course, I do. Because that's the thing about an electronic signature. If you can't prove with something else that you were the actual person who actually signed it or that your physical signature is there, it becomes a fraud. That is, unless you could get a court to sign off on it, where the court would basically rule this electronic signature is a real signature, even if the electronic signature looks real to you. You can't be sure.
It's like the difference between a hologram and a hologram. It doesn't matter who put it there. They don't have to show a real hand to make it work. So, if you sign an electronic signature, if that person can't provide proof that the signature is theirs, it becomes fake. It becomes fraud.
So, in the case of electronic signatures, and there's an entire case that's been pending in the court for about ten years about, what to do about them, the judge actually said there was enough evidence in that case, which is sort of an interesting precedent for a lot of these kinds of cases. If you can show a court that an electronic signature can be faked, you could get a court ruling to allow you to make a copy of that signature and prove that the signature is fake. So that would solve that particular problem. It's not a complete fix by any stretch of the imagination, but it would solve that particular issue. So that would really solve one of the two problems, because then you could us...
What is authenticity page for electronic signature?
What is authenticity page? Authenticity page, or a validating signature, is used when there is a need to authenticate the identity of an electronic document or when it is necessary to check whether a person has an actual (not just a copy) signature on a document. If you want to check whether the signature of a person is real, your best option is to use one of the following methods: 1. Use cryptographic signature. The cryptographic signature has the effect of verifying that the document was signed by the person who is claimed to be the author of that document. 2. Use public key cryptography, such a public key encryption method. A public key method makes use of public information, like a cryptographic key, to encrypt a secret message that you then transmit to someone else. This method makes use of public information to prevent someone who knows the public key to encrypt the message from decrypting it. 3. Use an asymmetric cryptography method. A private key is a number that is used in the process of generating a public key encryption protocol, and it is not public. Thus, it is possible to hide the identity of whoever you are sending a message to and thereby protect that person. 4. Use an asymmetric cryptography method and use another public key. It is also possible to use other ways to hide your identity if you want to. The most common ways of hiding identity are through encryption, encryption and authentication (public key or private key). You can see a list of all these metho...
Get more for Help Me With Implement Sign in SalesForce
Find out other Help Me With Implement Sign in SalesForce
- 21 xlsx level of care loc digital scoring form childyouth info
- Dc5 166 donation form issued 10418
- Lost passport form two consulate general of jamaica miami
- 375 011212 missouri uniform application for bail bond or surety recovery license form b1
- Horse racing occupational license fees form
- Bulk milk hauler ampamp sampler license mda state mn us form
- Milk haulers license ca form
- Bond form missouri
- Replacement huntingfishing license application form
- Nj abc liquor license application form
- New york state vicuna license form
- Cfstes professional certification state fire marshal ca gov form
- City of philadelphia fire alarm systems inspector license renewal form
- Fire alarm systems inspector form
- Department of game and inland fisheriesvirginia gov form
- Application for virginia fertilizerlime contractor applicator form
- F 45016 wisconsin form
- Application for operatorsbartenders license form
- Cost of ginseng dealer license in arkansas form
- Office of land surveys manual caltrans state of california form