Digital Signature FAQ: Everything You Need to Know About eSignatures
- Quick to start
- Easy-to-use
- 24/7 support
Simplified document journeys for small teams and individuals



We spread the word about digital transformation
Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.







Get the most from your eSignatures with airSlate SignNow
Speed up paperwork
Modify samples securely
Share files
Use Digital signature faq
Incorporate eSignatures via API
Make straightforward workflows
Quick-start guide on how to use digital signature faq feature
Is your organization ready to cut inefficiencies by three-quarters or more? With airSlate SignNow eSignature, weeks of contract negotiation become days, and hours of signature collection turn into a few minutes. You won't need to learn everything from scratch thanks to the intuitive interface and step-by-step guides.
Take the following steps listed below to use the digital signature faq functionality within a few minutes:
- Open your web browser and visit signnow.com.
- Subscribe for a free trial or log in with your email or Google/Facebook credentials.
- Click User Avatar -> My Account at the top-right corner of the page.
- Personalize your User Profile by adding personal information and altering settings.
- Design and manage your Default Signature(s).
- Get back to the dashboard page.
- Hover over the Upload and Create button and select the needed option.
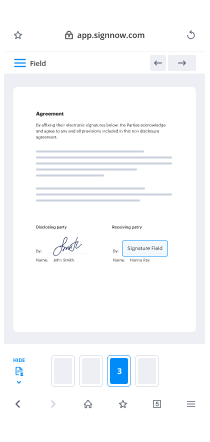
- Click the Prepare and Send key next to the document's name.
- Input the email address and name of all signers in the pop-up box that opens.
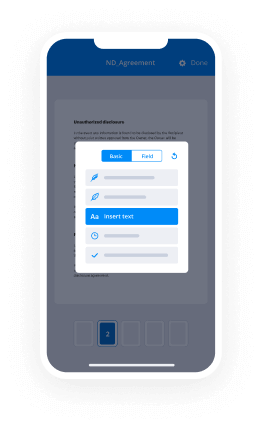
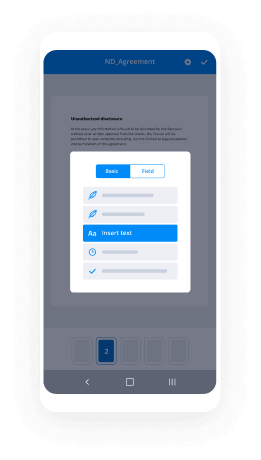
- Use the Start adding fields option to begin to edit document and self sign them.
- Click SAVE AND INVITE when completed.
- Continue to configure your eSignature workflow employing more features.
It can't get any easier to use the digital signature faq feature. It's available on your mobile devices as well. Install the airSlate SignNow application for iOS or Android and manage your custom eSignature workflows even while on the go. Forget printing and scanning, labor-intensive filing, and expensive document delivery.
How it works
Rate your experience
What is airSlate SignNow?
airSlate SignNow is a powerful electronic signature solution designed to help businesses streamline their document workflows. It enables users to send, sign, and manage documents digitally, enhancing efficiency and reducing the need for paper-based processes. With airSlate SignNow, users can easily create legally binding eSignatures, ensuring compliance with U.S. regulations. The platform is user-friendly and supports various document types, making it an ideal choice for organizations looking to modernize their signing processes.
How to use airSlate SignNow
Using airSlate SignNow is straightforward. First, users can create an account on the airSlate SignNow platform. Once logged in, they can upload documents needing signatures. The platform allows users to add signature fields and other necessary information directly onto the document. After setting up the document, users can send it for signature via email to the intended recipients. Recipients can then review, sign, and return the document electronically, all within a secure environment.
Steps to complete the airSlate SignNow
Completing a document with airSlate SignNow involves several simple steps:
- Log in to your airSlate SignNow account.
- Upload the document you wish to have signed.
- Add signature fields and any other required information.
- Send the document to the recipients for their signatures.
- Once signed, the document is automatically saved in your account.
- You can download or share the completed document as needed.
Legal use of airSlate SignNow
airSlate SignNow complies with U.S. eSignature laws, including the ESIGN Act and UETA, ensuring that electronically signed documents are legally binding. Users can confidently use airSlate SignNow for various legal documents, such as contracts, agreements, and forms, knowing they meet the necessary legal standards. The platform also maintains a detailed audit trail for each document, providing proof of consent and the signing process.
Security & Compliance Guidelines
Security is a top priority for airSlate SignNow. The platform employs advanced encryption methods to protect user data and signed documents. Additionally, airSlate SignNow adheres to industry standards for data protection and privacy, ensuring compliance with regulations such as GDPR and HIPAA where applicable. Users can trust that their information is secure throughout the eSignature process.
Documents You Can Sign
airSlate SignNow supports a wide range of document types, allowing users to sign anything from contracts and agreements to tax forms and HR documents. The platform is versatile, accommodating PDF files, Word documents, and other common formats. This flexibility makes airSlate SignNow suitable for various industries, helping organizations manage their documentation needs efficiently.
Sending & Signing Methods
airSlate SignNow offers multiple methods for sending and signing documents. Users can send documents via email directly from the platform or share links for recipients to access. The airSlate SignNow mobile app allows users to sign documents on the go, providing flexibility and convenience. Whether using a web browser or mobile device, airSlate SignNow ensures a seamless signing experience.
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
FAQs
-
What is SignNow and how does it work?
SignNow is an electronic signature solution that allows users to send, sign, and manage documents online. With its intuitive interface, SignNow simplifies the signing process, enabling businesses to streamline their workflows and enhance productivity. Users can easily upload documents, add signature fields, and send them for signing in just a few clicks.
-
What are the pricing options for SignNow?
SignNow offers flexible pricing plans to accommodate various business needs. Users can choose from monthly or annual subscriptions, with options for individual users, small teams, and larger enterprises. Each plan includes essential features, ensuring that businesses can find a cost-effective solution that fits their budget.
-
What features does SignNow offer?
SignNow provides a range of features designed to enhance document management and signing efficiency. Key features include customizable templates, in-person signing, document tracking, and advanced security measures. These tools empower businesses to manage their documents effectively while ensuring compliance and security.
-
How can SignNow benefit my business?
By using SignNow, businesses can signNowly reduce the time and costs associated with traditional paper-based processes. The platform enhances collaboration, speeds up contract turnaround times, and improves overall customer satisfaction. With SignNow, companies can focus on their core operations while ensuring a seamless signing experience.
-
Is SignNow secure for sensitive documents?
Yes, SignNow prioritizes the security of your documents with industry-standard encryption and compliance with regulations such as GDPR and HIPAA. The platform offers features like two-factor authentication and audit trails to ensure that your sensitive information remains protected. Trust SignNow to keep your documents safe throughout the signing process.
-
Can SignNow integrate with other applications?
SignNow seamlessly integrates with a variety of popular applications, including Google Drive, Salesforce, and Microsoft Office. These integrations allow users to streamline their workflows and enhance productivity by connecting their existing tools with SignNow's eSignature capabilities. This flexibility makes it easy to incorporate SignNow into your business processes.
-
How does SignNow support mobile signing?
SignNow offers a mobile-friendly platform that allows users to sign documents on-the-go. With the SignNow mobile app, users can easily access their documents, sign them, and send them for signatures from their smartphones or tablets. This convenience ensures that business transactions can be completed anytime, anywhere.
Digital signature faq
Trusted eSignature solution - digital signature faq
Join over 28 million airSlate SignNow users
Get more for digital signature faq
The ins and outs of eSignature