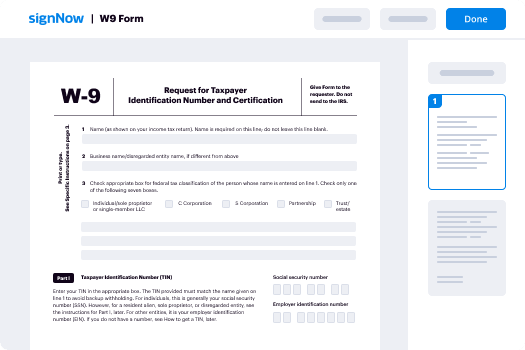
eSignature Document for Administrative Computer
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






Grasping document management with airSlate SignNow
Document management is essential for effective workflow oversight, and airSlate SignNow presents a variety of advantages that simplify this task. This platform allows organizations to transmit and digitally sign documents effortlessly, offering a user-friendly and economical answer for all document requirements.
Advantages of document management with airSlate SignNow
- Open your internet browser and go to the airSlate SignNow homepage.
- Establish a complimentary trial account or log in to your pre-existing account.
- Choose the document you intend to sign or send for signature and upload it.
- If you intend to utilize this document several times, transform it into a reusable template.
- Access your uploaded document to personalize it: insert fillable fields or add necessary details.
- Affix your signature to the document and allocate fields for the recipients’ signatures.
- Proceed by clicking Continue to arrange and send your eSignature invitation.
In summary, airSlate SignNow greatly improves document management by providing a comprehensive suite of features that deliver substantial returns on investment. Its user-friendly interface is tailored particularly for small and medium-sized enterprises, guaranteeing scalability and simplicity of use.
Prepared to enhance your document management process? Register for a complimentary trial with airSlate SignNow today and discover the benefits firsthand!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is document administration and how does airSlate SignNow facilitate it?
Document administration refers to the systematic management of documents throughout their lifecycle. airSlate SignNow simplifies document administration by providing tools for creating, sending, and eSigning documents efficiently. Our user-friendly platform ensures that all documents are organized, easily accessible, and secure, streamlining your workflow.
-
How can airSlate SignNow improve my team’s document administration process?
airSlate SignNow enhances document administration by automating repetitive tasks, such as sending reminders and tracking document status. This allows your team to focus on more strategic activities, ultimately improving productivity. Additionally, our platform offers customizable workflows that adapt to your specific document management needs.
-
What are the pricing options for airSlate SignNow's document administration services?
We offer flexible pricing plans tailored to fit various business sizes and needs. Our document administration solutions start with a free trial, allowing you to explore features before committing. Contact our sales team for detailed pricing based on the scale of your document management requirements.
-
Does airSlate SignNow integrate with other document administration tools?
Yes, airSlate SignNow seamlessly integrates with numerous third-party applications, enhancing your document administration capabilities. Popular integrations include Google Drive, Salesforce, and Microsoft Office, enabling you to manage documents from your preferred platforms efficiently. This connectivity ensures a smooth workflow across your existing tools.
-
What security measures does airSlate SignNow implement for document administration?
Security is a top priority for airSlate SignNow when it comes to document administration. We use advanced encryption protocols and secure cloud storage to protect your documents. Additionally, our platform complies with industry standards, ensuring that your sensitive information remains safe throughout the document lifecycle.
-
Can I customize templates for document administration in airSlate SignNow?
Absolutely! airSlate SignNow allows users to create and customize document templates to suit their specific needs. This feature streamlines the document administration process, as you can quickly generate documents by filling in necessary fields without starting from scratch each time.
-
How does airSlate SignNow support mobile document administration?
airSlate SignNow offers a mobile app that enables users to manage document administration on the go. With this app, you can create, send, and eSign documents from your smartphone or tablet, ensuring that you can stay productive and access important documents anytime, anywhere.
-
Why don't all the states use a paper ballot marked by a pen instead of voting machines that can be hacked?
To a certain extent anything can be hacked (also a paper!)According to Electronic voting by country - Wikipedia only 25 countries in the world used to have or are still using some kind of electronic voting system.Switzerland only uses it for expats, others (South Korea and Scotland) merely use it for counting of ballot papers. Some of the countries discontinued it: The Netherlands, Germany, Italy, and Finland to name a few.So less than 10 countries actually use the electronic voting system today.I really don’t know why the world is so scared of electronic voting, but I can only comment on the system I know best: the one that is used in BelgiumIn Belgium, they used to have pure electronic voting but a few years ago they decided to use a hybrid system.You vote electronically in a small cubicle. (To give a rough figure there are at least one of such cubicles per 200 citizens.)A paper printout will be printed by the system.This printout has a QR-code and a text field showing your vote. In theory, people can check if the QR-code corresponds to the text. (Although they do not actively promote it since it slows down the process.)Subsequently, you leave the cubical and the QR code is read out by a more central computer. (Max 6 ‘cubicles’ per computer so at least one per 1200 citizens.)and the paper printout is collected in a special compartment (by the citizen.)The votes are encrypted on two redundant USB-sticks.It is important to emphasize that up till this point everything works in isolation so fully stand-alone. Also the preparation of the USB sticks with the software to be used is done on a digital island in a secure zone. None of the hardware stores the votes. Even the software that is used is not stored on the hardware. This makes external influences on the reliable operation of the software virtually impossible.After the closure of the elections both USB sticks are secured and e-signed by the chairman. Subsequently, all paper votes are sealed into an envelope and signed by the chairmen + all members of the local polling office. The same process is performed on the USB sticks.The envelopes are physically transported to more central head Offices (one per voting district). Here all USB-sticks are read and the results are dispatched to the central administration via a secure web application with e-signatures of the chairmen of the local head offices. The full process is controlled and any abnormality in the process is documented and needs to be explained.After the elections, random spots checks are performed and the full process is evaluated by a panel of experts and improved if necessary.Since it does require a large investment (As explained above at least one voting pc per 200 citizens.) it is not implemented in the whole country.In Flanders, about 60% of the votes are electronically.In Brussels and the German-speaking part of the country, every vote is electronic.In the Walloon area, it is not used. As decided by the Walloon government, don’t ask me why.Even in a manual voting system, the votes need to be counted and subsequently, they need to be put in some kind of electronic system. So no system is 100% secure.The experts in Belgium analyzed the advantages and disadvantages and most of them state that the risks of voting electronically are actually smaller in comparison with a manual system.The fact that we have a paper trail of the actual ballots in case of issues or in case someone demands a recount reassures the non-believers.Drawings are taken from the official info of the Flemish government (© Agentschap Binnenlands Bestuur.)To be complete the system is developed by the Venezuelan company Smartmatic, some people in Belgium are against the fact that a foreign company is ‘in control’ of such an important process as an election.
-
How do I get an e-signature?
The exact details depend on the country’s e-signature law and the organizations that have been approved as certificate authorities.Basically, you buy a token that will hold your keys and certificates in confidence. This token normally looks like a flash disk pen drive and connects to your PC's USB port. You will also need to install some software on your computer.Next, the software will generate a key pair on the token. The public key together with some personally identifying data will be put together in a certificate request file.Now the certificate authority will check your identity thoroughly, according to the laws of the country and their operating procedures. Very likely this will include in-person identification using some identifying documents: passport, or ID card, or driving license or whatever happens to be an acceptable identification document in your country.Having identified you, the certificate authority will sign on the certificate request and transform it into a certificate. Your certificate now contains the following data: your public key, personal info, administrative information such as expiry date, acceptable uses of the key, etc., and the CA's signature. The certificate will then be loaded into the token.From now on your token and the software on your PC can be used to sign documents and electronic transactions in your name. The purpose of the electronic signature law is to declare that such a signature is as binding legally as a handwritten signature on a document. Typically the use of the token is protected by a PIN code.
-
How does censorship work in China?
Internet content companies can only operate with business operating licenses. If they lose their license, they cannot operate. (If you go to a Chinese website and you see the little red shield at the bottom of the page, that is their registration information which is filed with local police and the security services. Following it is a police phone number where anyone can immediately report an infraction to the authorities which will be dealt with in real-time.);Every internet content company has an editor-in-chief who is personally responsible for making sure that the site’s content conforms with government regulations. In other words, if he does not follow regulations, he can be tried and put in jail and the company may lose its business operating license;Every morning, the editor-in-chief at about 7AM, receives a phone call (Note: there are no written directives issued) from the relevant Chinese Communist Party department about what can only be reported through official channels and quotes, what can be reported with specific reporting guidelines, and what cannot be reported. The editor-in-chief is then responsible for passing on this information to his editing team, who then insure that all content meets these regulations before they are posted.Every Chinese company, before they get an operating license, must agree to and sign Chinese security regulations. Here is a copy of those security regulations in English:Declaration: This Department will solemnly adhere to all items in this agreement, and be fully responsible for any civic, legal, or criminal repercussions resulting from a failure to do so.This Department agrees to adhere to the Regulation on Telecommunications of the People's Republic of China, the Regulations of the People's Republic of China for Safety Protection of Computer Information Systems, the Measures for Security Protection Administration of the International Networking of Computer Information Networks, and all related laws, policies, and documented regulations.This Department agrees all legal requirements and qualifications needed to provide this service have been obtained.This Department agrees that the telecommunications network will not be used to compromise national security, reveal sensitive state information, or otherwise break any laws or infringe on the legal rights of the People’s Republic of China, the public, any groups, or third parties.This Department agrees to adhere strictly to the national standards and regulations of information security.This Department agrees to comprehensively adhere to the standards and technologies used to protect information security.This Department agrees to any audit or review by the state, to willfully provide accurate information and data regarding information security, and aid the state in any investigation of criminal activity over the computer information network.This Department agrees not to use the telecommunications network to produce, copy, search, or transmit the following:a) Content fundamentally prohibited by the Constitution of the People’s Republic of China.b) Content that would be detrimental to national security, destabilize national capacities, reveal sensitive state information, or harm national unity.c) Content that is detrimental to national reputation and interests.d) Content that incites public hostility, prejudice, or division.e) Content that harms national policies regarding religion, aims to start a cult, or spread misinformation.f) Content that spreads false information and incites public unrest or chaos.g) Conduct that promotes obscenity, pornography, gambling, violence, murder, intimidation, or criminal behavior.h) Content that slanders others or violates their legal rights.i) Other content in violation of applicable laws and regulations.8. This Department agrees to not engage in any activity that may harm the security of computer information systems, including but not limited to:a) Unlawfully accessing or using computer information system resources.b) Unlawfully adding to, deleting, or editing resources on the computer information network.c) Unlawfully preserving or transmitting data or software that would add to, delete, or edit resources on the computer information system network.d) Willfully create or transmit computer viruses or similarly harmful software.e) Other activities detrimental to the security of the computer information network.9. In the event of an extensive security failure or bsignNow of the computer information network, this Department agrees to promptly take emergency measures, preserve all relevant original data, inform the state regulatory authorities within 24 hours, and send a written report.10. This Department shall solely be responsible for any legal repercussions arising from the failure to adhere to the rules described in this agreement or any related state regulations. This Department will also be solely responsible for any monetary damage caused by such a failure. In the event of a bsignNow of this agreement, related services may be paused or concluded, and mutual agreements may also be terminated.11. This agreement takes effect from the date of signature.
-
As a computer science student, what can I learn right now in just 10 minutes that could be useful for the rest of my life?
Have you ever felt that something(like taking backup of files, deleting old files etc.) should automatically happen when you connect your pen-drive to your system?Let us take an example, Suppose your teacher wants you to copy your assignments into his pendrive in front of him. The pen drive contains your final examination paper. You want your ubuntu system to automatically copy all the data from that pen drive to your hard disk automatically in the background (without even opening a copy dialogue). Here is how to do it on ubuntu:1] First let us write a simple shell script which we want to execute whenever a pen drive is connected to our system. Let us write a simple script which copies all data from the connected device to your home directory.First open a new fileemacs $HOME/script.shand add following lines to that file.#!/bin/bash sudo mkdir -p /tmp/test sudo mkdir -p $HOME/device_data sudo mount /dev/sdb1 /tmp/test sudo cp -r /tmp/test/* $HOME/device_data/ sudo umount /tmp/test Save and close the file.This script essentially creates a new directory named "device_data" inside your home folder and copies all the data from the pen drive into device_data directory.(Note: You can write ANYHTING into this script, so use it wisely :P)Now let us make this script executable.sudo chmod +x $HOME/script.sh As this script needs sudo permissions, we need to make it sudo runnable. To do this add the name of the script into sudoers file.Open sudoers file.sudo visudo -f /etc/sudoers Now after the 25th line (%sudo…) add this line
ALL=(ALL) NOPASSWD: /home/ /script.sh So now this script will run with sudo rights but will not ask for password! :)2]Now we need to tell our system to follow OUR rules (i.e execute our script) whenever a pendrive is connected. For this we need to create our own "udev rules" file. This file should be created in '/etc/udev/rules.d' directory.cd /etc/udev/rules.d Open a new file (with sudo rights):sudo emacs 91-myrules.rules Make sure the file name starts with "91". This gives your rules priority over other rules.Now add these lines into that fileACTION=="add", ATTRS{idVendor}=="****", ATTRS{idProduct}=="****", RUN+="/paht/to/your/script.sh" Make sure you enter proper path into RUN variable.Done!!Now plug any pendrive into your system and test this!Note: 1] When you connect your external drive this script will be run and your system won’t be able to use it unless this script execution is complete! So have some patience! :p 2] This answer is written for educational purposes only! Do not misuse it.Thanks Mehak Sharma for promoting the answer! -
Do you really need to cover the camera on your laptop?
A few years ago, I was working on my laptop, when the screen suddenly froze, and went black. A message popped up, covering the whole screen. I couldn’t remove it, shut down or navigate to another screen. Even removing the battery and then restarting did not remove it. It was completely locked out. The message was from the ‘Australian Federal Police’ and stated that I had been caught breaking pirating laws by illegally downloading content. It said they had seized control of my laptop, would be investigating me further, and that I would be forced to pay a large fine. The message also included a picture of me. I began hyperventilating when I realised someone had hacked into my webcam, and taken a picture of me. All without my knowledge or consent. They had been able to take control of my laptop, and watch me in my own home. Then they had attempted to blackmail me. I used my housemate’s computer to Google what was happening to mine, discovered that this was a fairly widespread scam, and was able to get my laptop fixed. After that, I completely and permanently disabled the webcam, and put tape over the camera. I still cover the cameras on the laptops I’ve owned since. People think I’m quite paranoid. But they’ve never had a stranger watching them through their laptop. There are people out there who have the ability to access your webcam remotely. These people may also attempt to hurt you with the information they retrieve. So yes, everyone should be covering the cameras on their laptops. Better to be safe than sorry.
-
What are some good computer tricks that are not commonly known?
I’m not a computer specialist. But someone has asked my answer even on this topic. Alright, I try to contribute something. Almost every one of us is sure that he knows the computer well, whether it's “Windows” or "Macintosh". And 99% of us are mistaken. Meanwhile, studies show (and any programmer will confirm) that short-cuts can speed up your computer tasks by several times. Here are the main hot keys. Maybe some of you know these tricks, but if you don’t know them, I assure: they will really save you thousands of hours of life! 1- How to instantly open a randomly closed tab? Unfortunately, this happens often: wanted to close a window in the browser but accidentally closed other important windows as well. Instead of looking for it in history, use these "short-cuts" to compensate your inattention: For Windows: Ctrl + Shift + T For Mac: cmd + Z (Safari) and cmd + Shift + T (for Google Chrome). 2- What if the boss/Papa/Mama crept in from behind? Sometimes you feel lazy at work and start reading random stuff on Quora. And you have a dozen other windows opened. How to quickly pretend that you are working? These shorts quickly remove the browser windows by minimising all and showing the desktop(in windows) and you can return to the Word or Excel screen (manually): For Windows: Windows + D (minimises all applications and shows desktop) For Mac: Fn + F11 3- How to lock the computer, if you need to leave for a while? No one likes his boss to read his chat conversations or you do not want anyone to look into your monitor, until you leave to make coffee. Others will not able to open only if you have set a password to login. One can simply enter by clicking your user icon if you dont have a password. This quick combination of keys will instantly lock your computer and you will be able to fully enjoy the break: For Windows: "Windows" key + L. For Mac: cmd + Alt + Eject. 4- What if the computer halts? It happens that you are sitting in Photoshop, and all of a sudden - the entire computer is “hung”. And it does not react to anything. Typically, users immediately press Ctrl + Alt + Del to reboot. But this is far from the best solution. It is much better to use short-cuts: they will stop only this one nasty program: For Windows: Ctrl + Shift + Esc (Opens the task manager) For Mac: cmd + Option (alt) + Shift + Esc. Hold these buttons for three seconds in a row, and the hung program closes, and you will be able to work on and not lose any changes in all your documents. 5- Need to quickly save the url of any web-page? As practice shows, this combination will save you millions of minutes: For Windows: Ctrl + D Mac version: cmd + L 6- How to make a screenshot not of the whole screen, but only of the required part of it? All Windows users are accustomed to press "Print Screen" when they need to show something to their comrades. But it happens that there are too many things on the screen, and it is long and tedious to crop the picture. Here's how to always allocate only what you need: For Windows: -Alt + Print Screen(the screenshot is saved to a folder called “Screenshots” in Pictures folder) For Mac: - cmd + Shift + 3 (the screenshot is saved on the desktop) - cmd + Shift + Ctrl + 3 (the screenshot gets to the clipboard) - cmd + Shift + 4 (Only the desired piece of the screen gets saved on the desktop) - cmd + Shift + Ctrl + 4 (the desired piece gets copied to the clipboard) I think for now, it’s enough. Maybe next time, under any other question, I’ll add a few more tips. Good Luck!
-
Does anyone still use Gwoyeu Romatzyh to romanise Chinese?
[無調漢語拼音的缺憾 Toneless Hanyu Pinyin can cause serious problems][GR Tonal Spelling makes names maximally distinctive; Hanyu Pinyin leads to a confusing blend of totally unrelated names that sound quite different to Chinese ears, but look exactly the same to foreign eyes]Three names that look totally different in GR Tonal Spelling: confusingly blended in Hanyu Pinyin:Imaginary, but plausible names: 陸六贏醫師, 魯劉穎大師 and 盧柳鶯大師1. 陸六贏醫師 Dr. Luh Liowyng (Lù Liùyíng Yīshī), the dentist, bears the auspicious name 六贏 “six successes”2. 魯劉穎大師 Master Luu Liouyiing (Lǔ Liúyǐng Dàshī), the photographer, bears the name 劉穎, which is a pun on the word 留影 “take a photo [as a souvenir]” (this phrase is often used for photo captions)3. 盧柳鶯大師 Master Lu Leouing (Lú Liǔyīng), the musician, bears the name 柳鶯 “[literally] willow warbler”, one of many species of songbirds, some of which can be found in Taiwan.TL;DR 性命攸關 Not using GR Tonal Spelling can have serious, or even life-changing consequencesAnswer: Yes, people in Taiwan still use GR Tonal Spelling (a.k.a. Gwoyeu Romatzyh), but it is hiding in plain sight where most foreigners don’t bother looking (not just tour buses ;-). GR Tonal Spelling is used for naming people, clothing, household goods (rubber bands, insecticide), Chinese medicine, noodles, beverages, snacks, doctors’ offices, beauty parlors, restaurants, companies, schools etc.I took all of the photos below within the last month. I live in Taipei, but I managed to locate several samples of GR Tonal Spelling even in Kaohsiung, a DPP stronghold where Southern Min is more popular than Mandarin][Jyma Liuhdow 芝麻綠豆, GR Tonal Spelling (Gwoyeu Romatzyh)—a children’s clothing brand I found in a traditional market] [zhīma lǜdòu][Song Jer CPA 松哲會計師事務所, GR Tonal Spelling (Gwoyeu Romatzyh)—an accounting firm on Nanjing West Road in Taipei. The sign is bigger than the side of a bus, but is only visible when people look up from their cell phones ;-)] [Sōng Zhé][Piin U Bakery 品屋麵包蛋糕, GR Tonal Spelling (Gwoyeu Romatzyh), a bakery/coffee shop in Kaohsiung] [Pǐn Wū][Shiow Chwan Hospital 秀傳醫院, GR Tonal Spelling (Gwoyeu), a private hospital with branches all over Taiwan; name is slightly misspelled (omitted -i-)] [Xiù Chuán][Yuh Tay Farm 裕泰農場, GR Tonal Spelling (Gwoyeu)][jingpiin pyishye 精品皮鞋, GR Tonal Spelling (Gwoyeu), shoe shop in Kaohsiung]GR Tonal Spelling still appears side by side with Bopomofo in many monolingual Chinese dictionaries (字典、詞典) published in Taiwan. Foreign students tend to only consult bilingual dictionaries published outside of Taiwan, so they mostly don’t notice GR’s continued existence.[In Taiwan, dictionaries for native speakers include Bopomofo only, or a mixture of Bopomofo and GR Tonal Spelling/Hanyu Pinyin. Unfortunately, Pinyin is gaining ground; I saw these books in the 國語日報社 Mandarin Daily News bookstore]When it comes to romanization, what most foreigners do notice is the major exception to the use of GR Tonal Spelling: place names, which are a chaotic battlefield for three competing systems: the decrepit 150-year-old Wade-Giles system (and its cousin: Postal Romanization), 1958 Hanyu Pinyin and a modified Pinyin system (slightly different spellings) used mostly in southern Taiwan.Edit: GR Tonal Spelling still survives in certain localities:[Shinnyih Street 信義街 GR Tonal Spelling, 29 June 2019 (Gwoyeu Romatzyh, street sign)] [Xìnyì Jiē, Hanyu Pinyin]Rarely Asked Questions (RAQs)Many people take it for granted that one single commonly-used romanization system is all we need: whatever is used by the majority of Chinese people. The Hanyu Pinyin for everybody approach neglects to consider two important facts:(1) For many western learners, the use of optional diacritics implies that tones are also optional (“Tones are too subtle. I don’t need to be a perfectionist: muddling through is good enough. If I can find the time, I’ll master tones later!”)(2) For Chinese people who spend time abroad, an ill-considered choice of spellings can facilitate identity theft or lead to confusion. The consequences can include canceled credit, job loss, mistaken arrests, medical errors and expensive lawyer’s fees.Rarely-Asked Questions:RAQ 1: Who needs to use romanization?RAQ 2: What is the purpose of romanization?RAQ 3: Why should everyone use the same romanization?RAQ 4: Which problems does Pinyin (un)intentionally ignore?RAQ 5: How is 1928 GR Tonal Spelling better than 1958 Hanyu Pinyin?RAQ 1: Who Needs To Use Romanization?A: Children learning to read and write their native language for the first timeB: Chinese adults who want to# look up the correct pronunciation of less common or problematic words or characters# produce or consult lists or indexes# input characters on a computer or smartphoneC: Foreign students of Chinese, who need a tool for learning and annotating characters, and inputting them on a computer or smartphoneD: Foreign visitors who need an easy way to get around in China (identify people’s names, place names, names of products, items on a menu etc.)E: People outside of China who need easily-identifiable spellings for Chinese people and thingsRAQ 2: What is the purpose of romanization?Groups A & B: Romanization is supposed to correctly and unambiguously annotate the sounds of Chinese. Everything that sounds different to Chinese ears (initials 聲母, medials 介音, finals 韻母, and tones 聲調) should be explicitly marked when romanized. However, because of redundancies that are an integral part of Chinese phonology (音系規則, the Chinese sound system), people (especially computer users) can take shortcuts: tones are often left out, and IMEs (input method editors) can even ignore medials and finals (i.e. a computer user can type HYPY instead of hànyǔ pīnyīn: both yield the same result 漢語拼音).Group C: Foreign students are not aware of how Chinese sounds form patterns. Unlike native speakers, who learn phonology with their mother’s milk (so to speak), foreign beginners have definite trouble dealing with Hanyu Pinyin’s shorthand spellings.Hanyu Pinyin was designed for the convenience of native speakers of Chinese, so it is a less than ideal system for foreign learners, especially in the early stages.Group D: Tourists and short term visitors assume that Chinese is very difficult, so if they can go about their business without too much trouble, they are generally satisfied with Pinyin.Group E: This group has some limited, but very specific requirements that are not at all obvious to Chinese people who spend all their lives in a Chinese-only environment. Chinese people living in other countries need to be easily and unambiguously identified without referring to the Chinese characters of their names. This is where Hanyu Pinyin can cause EXTREMELY SERIOUS PROBLEMS.RAQ 3: Why should everyone use the same romanization?The five groups of users mentioned above have different needs that cannot all be properly served by Hanyu Pinyin. In the 1950s, when Hanyu Pinyin was designed, the world was a different place. The committee that set up and promulgated this romanization only needed to consider the needs of Chinese people within China. 60+ years later, the millions of Chinese who now live, travel or study abroad are affected by the shortcomings of Hanyu Pinyin’s shorthand spellings. Foreigners can also benefit from more than one approach.RAQ 4: Which problems does Pinyin (un)intentionally ignore?In 1956, Pinyin’s designers, who were influenced by Soviet linguists such as А. А. Драгунов 龍果夫, strove to create a simple China-only spelling system with single-letter spellings for each consonant. Thus, hard-to-type letters were used for common sounds: {ç = ch}, {ʐ = zh}, {ч = j}, {ŋ = ng}. Cyrillic, IPA and Latin letters were mixed together with no thought given to ease of use on standard ASCII typewriter keyboards (Why did the Chinese language begin using Latin letters for Pinyin?)The 1958 final revision of Hanyu Pinyin finally settled on an all-Latin alphabet solution “with Chinese characteristics”, including some unique letter values that are not commonly used by European languages, such as q, x, z, c, u and i.Thus, people whose family name is either 徐 Xú or 許 Xǔ (both very common Chinese surnames: Shyu & Sheu in GR Tonal Spelling) are both spelled Xu, which many speakers of English will assume is pronounced the same as “Zoo”. Gross mispronunciations aside, Hanyu Pinyin can lead to much more serious problems.Because Pinyin tone marks are optional, the foreigner-readable versions of birth certificates, diplomas, degrees, household registration papers, hospital records, leases, licenses, passports and other documents do not show tones.Readers may ask: So what? Foreigners can’t pronounce tones anyway! What difference does it make?Here’s why. Including tones, Mandarin Chinese has about 1200 different syllables. For the sake of argument, let us assume that each and every syllable in Mandarin could be used as part of a name (obviously not true). Because most Chinese names consist of three syllables, GR Tonal Spelling could be used to write a maximum of 1200*1200*1200 = 1,728,000,000 phonetically distinctive names (although this would never be attempted, such a scheme would theoretically be enough for every person in China to have a unique name).How many possible syllables are there in Chinese Mandarin?/answer/Robert-Matthews-%E9%A6%AC%E5%AD%B8%E9%80%B2However, because Hanyu Pinyin omits tones, there is only a maximum of 400*400*400 = 64,000,000 distinctive names. Chinese names spelled in GR Tonal Spelling are much more distinctive than toneless Hanyu Pinyin names. 1,728,000,000 [GR] / 64,000,000 [PY] = 27 times more distinctive!Another way to put this: omitting the tones in romanized three-character Chinese names leads to potential information loss of as much as 96%.RAQ 5: How is 1928 GR Tonal Spelling better than 1958 Hanyu Pinyin?[Animated GIF: How abandoning GR Tonal Spelling led to scrambled Chinese surnames][Animated GIF: Different-Sounding Chinese Surnames That Are Unfortunately Blended In Pinyin]GR Tonal Spelling (a.k.a. Gwoyeu Romatzyh, National Phonetic Alphabet Version 2) was created by a small subgroup (數人會) of the committee responsible for creating National Phonetic Alphabet Version 1 (also known by the name Bopomofo or the anachronistic spelling Zhuyin Fuhao).The most important scholar behind the creation and popularization of GR Tonal Spelling is China’s greatest modern linguist, 趙元任 Chao Yuenren, a genius educated in the US who used his knowledge of mathematics, physics, music theory, phonetics and Chinese phonology to create a system based on “native speaker intuition” that also takes English orthographic habits into account (blending the two was not at all an easy task).GR Tonal Spelling is a “green” romanization that follows the Principle of Economy 經濟原則 and its three basic rules: keep, change, add 留改加. The 1st tone is usually the basic, unmodified form (“Keep”). The other three tones are spelled by making minimal changes to the basic form (“Change”), usually a different spelling for a glide vowel. If this is not possible, a letter is added (“Add”).Thus, tiau is a first tone form (spelled tiao in Hanyu Pinyin). The other three tones are spelled tyau, teau and tiaw. Notice how in each case the shape of the glide letter imitates the tone contour: The red bolded strokes of “y”, “e” and “w” are GIANT, indelible tone marks typable on any ASCII keyboard. They also provide valuable mnemonics for foreign learners struggling to remember the correct tones of words such as mae 買 and may 賣: “buy” and “sell”.Robert Matthews (馬學進)'s answer to As an English speaker, what's the best way to learn Chinese?[Animated GIF: 2nd tone tiau → tyau in GR Tonal Spelling; the tone mark is blended with the spelling of the medial vowel][Animated GIF: 3rd tone tiau → teau in GR Tonal Spelling; the tone mark is blended with the spelling][Animated GIF: 4th tone tiau → tiaw in GR Tonal Spelling; 4th tones are always marked at the end of a syllable: the tone mark is blended with the spelling]For almost 1900 years (since the end of the Eastern Han Dynasty), the 反切 fǎnqiè / faanchieh system has been used to indicate the pronunciation of Chinese characters.Each Chinese syllable is split into two parts: 聲母 shēngmǔ/shengmuu “the initial” (the single consonant, if any, at the beginning of a syllable) and 韻母yùnmǔ/yunnmuu “the final” (the rest of the syllable, including the tone). Bopomofo modifies this tradition by using 2-4 symbols to represent each syllable.First tone 張 (a common surname) is marked in Bopomofo with only 2 symbols, ㄓ+ㄤ (first tone is not explicitly marked).GR Tonal Spelling, Bopomofo’s younger brother, is similarly economical. Only four letters are needed for 張: j+ang (just like in the faanchieh system, ang includes the first tone).Fourth tone 賬 (account) is marked in Bopomofo with three symbols, ㄓ+ㄤ+ˋ, and GR Tonal Spelling still only requires four letters: j+anq (again, just like in the faanchieh system, anq includes the fourth tone).Hanyu Pinyin follows the all or nothing European approach of either ignoring all tones or marking all of them with tiny optional diacritics not found on ASCII keyboards. Pinyin thus uses 6 symbols for 1st tone 張 z+h+a+ˉ+n+g (a+ˉ are combined) and six symbols for 4th tone 賬 z+h+a+ˋ+n+g (a+ˋ are combined)Hanyu Pinyin is a system better suited to native speakers who are intimately familiar with the Mandarin phonological system.Thus, in Hanyu Pinyin the letters “i” and “u” have multiple pronunciations:(1) When “i” is preceded by z, c, or s, it is automatically pronounced as an unusual (for European ears) apical vowel /ɿ/, a mosquito-like buzzing sound.(2) When “i” is preceded by zh, ch or sh, it is pronounced as a similar-sounding /ʅ/.(3) When “i” is preceded by any other consonant and not followed by any other vowel letter, it is pronounced as a very different-sounding “normal” vowel /i/.(4) When “i” is preceded by any other consonant and followed by any other vowel letter, it is pronounced as a semi-vowel /j/.(5) When “i” is preceded by “u”, it is pronounced as /ej/ (not /ui/), as in 對 dui “correct”Hanyu Pinyin’s “u” follows similar rules.(1) When “u” is preceded by z, c, or s, it is pronounced as /u/.(2) When “u” is preceded by zh, ch or sh and not followed by any other vowel letter, it is pronounced as /u/.(3) When “u” is preceded by zh, ch or sh and followed by any other vowel letter, it is pronounced as a semi-vowel /w/.(4) When “u” is preceded by j, q, x, but not followed by any other vowel letter, “u” is pronounced as a front rounded vowel /y/.(5) When “u” is preceded by j, q, x, but followed by any other vowel letter, it is pronounced as a semi-vowel /w/.(6) When “u” is preceded by “i”, it is pronounced as /jow/, as in 休 xiu “to rest”, pronounced /ɕjow/, not /ziu/.Despite this hidden complexity, many foreigners who cut their teeth on Hanyu Pinyin swear by it and insist that it is much easier and more “reasonable” than GR Tonal Spelling (Gwoyeu Romatzyh)’s traditional 反切 based approach, with its three basic rules.Hanyu Pinyin economizes on symbols by assuming that its users are native speakers who can figure out what sounds right (“i” and “u” rules) automatically. Foreign beginners and casual readers (people who only occasionally need to pronounce Chinese words) have a very difficult time.GR combines Bopomofo’s traditional Chinese 反切 analysis with an ingenious spelling system that is mnemonically-based (letters with shapes that resemble tone contours are used to spell tones) and much more foreigner-friendly than Hanyu Pinyin (even foreigners who have never learned any Chinese at all can usually make a passable guess).Basically, whatever looks different in Gwoyeu Romatzyh sounds different to Chinese ears, and whatever sounds different looks different, including the four tones of Mandarin Chinese.GR Tonal Spelling (Gwoyeu Romatzyh) is widely used for spelling the names of well-educated people in Taiwan (doctors, lawyers, professors etc.).In Hanyu Pinyin, the following four names (Shy, Shyr, Shyy and Shyh) are blended together. Millions of people are forced to share one artificial giant surname (Shī + Shí + Shǐ + Shì —> Shi) created for administrative convenience when producing foreigner-readable documents. Typing tone diacritics is a hassle: let Mr. Chabuduo handle everything.[1st tone surname 施 SHy in GR Tonal Spelling] [Shī][2nd tone surname 石 SHyr in GR Tonal Spelling] [Shí][3rd tone surname 史 SHyy in GR Tonal Spelling] [Shǐ][4th tone surname 釋 SHyh in GR Tonal Spelling] [釋 is a surname adopted by Buddhists who give up their worldly property, including their original surnames] [Shì]A real-life example of potential confusion:(1) The PRC Ambassador to the German Federal Republic is 史明德 (spelled Shǐ Míngdé in “official” Pinyin).(2) Taiwan’s most famous political activist is 施明德 (spelled Shī Míngdé in “official” Pinyin).Imagine the confusion and embarrassment that would result if the PRC ambassador (Shi Mingde in “Street” Pinyin) was erroneously refused entry to a country that had banned the Taiwan activist (they seem to have exactly the same name)!Such problems could be easily eliminated if Chinese names were written using GR Tonal Spelling. 史明德, the ambassador, would be spelled Shyy Mingder and 施明德, the political activist, would be spelled Shy Mingder. The 1928 official spelling prevented such unfortunate misunderstandings.In Taiwan, even people with less common names use GR Tonal Spelling:[Surnames Jin 金 and Jinn 靳 (GR Tonal Spelling, Gwoyeu Romatzyh)]Surnames Bau 包 and Baw 鮑1. Professor Bau Da-Tian 包大靝http://webap.cmu.edu.tw/TchEport...Graduate Institute of Biomedical Sciences, China Medical University2. Dr. Bau Tzong-ho 包宗和Professor of Department of Political Science, National Taiwan University監察院 - 人權主題網 ─ Members1. Aser Baw 鮑美瑟Animal Behavior Resource AssociationABRA國際認證訓練師資歷:2014 第二屆亞洲訓練師行為治療師培訓取得ABRA國際認證 LE 資格2. Wayne Baw 鮑維芳Wayne Baw 鮑維芳 (@waynebaw)https://www.linkedin.com/in/wayn...3. Spencer Baw鮑穎https://www.youtube.com/channel/...Identity Theft And Other Serious Problems Caused By Spelling ConfusionOutside of China, Hanyu Pinyin’s toneless version can lead to or facilitate:1) Mistaken Identity Arrests2) Identity Theft3) Credit Card Fraud4) Medical ErrorAll of these problems can cause financial pain or have life-changing consequences, such as job loss, imprisonment or even worse.1) Mistaken Identity ArrestsA policeman conducting a routine traffic stop may wind up arresting the driver. Why?For one thing, suspect descriptions on warrants can apply to many people: “A black-haired, thin Chinese man in his 20s”. Having a non-distinctive (no tones indicated), Pinyin-only name that is identical to the one on a warrant certainly wouldn’t help.[this subsection was upgraded from my reply to a comment by Ni Ming]:Taiwanese police have an excellent reputation for tracking down criminals and cracking difficult cases. I'm sure the mainland police are equally intelligent and professionally dedicated. Unfortunately, such praise is hard to apply to their American militarized counterparts, who have a reputation for shooting first and asking questions later.Even small town police departments use SWAT teams and armored personnel carriers to handle routine, non-violent cases (such as seizing a child with a fever late at night to take it to see a doctor). They use battering rams to smash down doors, shoot family dogs (even a chihuahua has been viewed as a “threat”) and leave extensive trauma in their wake, especially when they barge in on completely innocent people.If you Google “cops” + “wrong house”, or “cops” + “shoot dog”, you will get a flavor. I very much doubt American cops will stand patiently while listening to an explanation of the subtle tonal difference between three different Chinese surnames who are forced to share one single toneless spelling.Real people with false homonym namesForeigners outside of China have no way of knowing that 古真福, 顧振福, 辜振甫, 辜振富 are four different people. If they have PRC-issued ID documents, all four seem to have exactly the same name: Gu Zhenfu.Hanyu Pinyin: Gu Zhenfu ← Gǔ Zhēnfú, Gù Zhènfú, Gū Zhènfǔ, Gū ZhènfùThese are all real people:"古真福" - Google Search"顧振福" - Google Search"辜振甫" - Google Search辜振富 (Facebook)GR Tonal Spelling (different people, different names): Guu Jenfwu, Guh Jennfwu, Gu Jennfuu, GU JennfuhIf any one of these people commits a crime (such as ignoring a pile of unpaid parking tickets), the other three could mistakenly be arrested by a policeman whose warrant only says “Gu Zhenfu: wanted for being a scofflaw”.American police don’t fool around. Strictly following the law and making arrests improves their chances of promotion. What’s not to like?法律就是法律,美國警察不講人情.These supposed scofflaws will be thrown in jail, and they will wait for a judge to (hopefully) sort out the mess. How many innocent Chinese people have suffered because of an incomplete romanization that doesn’t work properly outside of China?1. Why Mistaken Identity Arrests Happen2. Can You Be Arrested with a Warrant for Someone Else? | WK LawBeing arrested, even if later proven to be a mistake, can have financial (expensive lawyers) and social consequences (job loss, shunning, shaming of one’s children), and there is sometimes nothing one can do.3. Man jailed based on mistaken identity can't sue, court rules***Examples of Mistaken Arrests Due to Having the Same Name1. Man With Accused Criminal's Name Battles Mistaken Identity2. Man Sues Police Over Mistaken Identity Arrest | Hartford Criminal Defense Attorney3. Woman held in case of mistaken identity to seek compensation [New Zealand]4. Innocent man arrested, jailed twice because of name5. This Woman Lost Kids and Job After Being Mistaken for Drug Trafficking Suspect with Same Name6. Mistaken identity leads to physical arrest of Victorville man at his front door7. Mistaken identity of same-name men causes wrong arrest by Edmond policehttps://www.edmondsun.com/news/m...8. When the Only Crime is a Common Name...9. Grandmother Arrested, Spends 5 Days in Jail.....Whoops, Wrong Person.2) Identity Theft3) Credit Card FraudIdentity theft is a serious problem that is often connected with credit card fraud. Because the US does not have a national ID card, other types of ID are used, some of which are easily forged.A case in point is signatures. Because they are not intimately familiar with Latin alphabet handwriting, many Chinese rely on a very simple foreign signature that is easily copied (to combat this problem in my university language classes, I often included instruction in cursive handwriting).Handwriting University Forgery Proof[Unhappy Consequences of Using Toneless Pinyin On Foreign Documents]A. Report: Medical Identity Theft – The Information Crime that Can Kill YouDefinition: “when someone uses an individual's identifying information, such as their health insurance information or social security number, without the individual's knowledge or permission, to obtain medical services or goods, or to obtain money by falsifying claims for medical services and falsifying medical records to support those claims.”Medical Identity theft can have all sorts of cserious consequences, including:1. Financial losses (you may be required to pay for someone elese’s expensive medical care),2. Harm from false entries in your medical record (such as being given the wrong type of blood)3. Insurance caps signNowed (Someone may have used up all of your coverage; any further treatment may be prohibitively expensive)Victims of medical identity theft find out the truth in many unexpected ways:1. collection notices (a collection agency insists that you have to pay a penalty for unpaid bills that have nothing to do with you)2. Notification by law enforcement, an insurance company, or a health care provider that you have a problem3. Your insurance company tells you that benefits have run out, or a “lifetime cap” has been signNowed (you have supposedly used up all of the benefits provided by your medical insurance)Report: Medical Identity Theft - The Information Crime that Can Kill YouB. Exploring Medical Identity TheftDesla Mancilla, MPA, RHIA, principal investigator and Jackie Moczygemba, MBA, RHIA, CCS, secondary investigator, associate professorPerspect Health Inf Manag. 2009; 6(Fall): 1e. || PMCID: PMC2804460 || PMID: 20169017Exploring Medical Identity TheftC. Medical Identity Theft in the Emergency Department: Awareness is CrucialMichelino Mancini, DOWest J Emerg Med. 2014 Nov; 15(7): 899–901. || doi: 10.5811/westjem.2014.8.22438 || PMCID: PMC4251251 || PMID: 25493150“According to the Federal Trade Commission (FTC), medical identity theft accounted for 3% of identity theft crimes, or 249,000 of the estimated 8.3 million people who had their identities stolen in 2005. More recently, the Ponemon Institute calculated that there were 1.84 million victims of medical identity theft in 2013.”Medical Identity Theft in the Emergency Department: Awareness is CrucialImage Credits (Public Domain images)Digital Camera, Happy Tooth images by Clker-Free-Vector-Images (Clker-Free-Vector-Images | Pixabay)Bubbleman images by Peggy und Marco Lachmann-Anke from Pixabay (3dman_eu | Pixabay)Blender image: OpenClipart-Vectors from PixabayShi Mingde (the bigshot): CC BY-SA Raimond SpekkingShi Mingde (the Taiwanese activist): Public Domain image
-
How would I go about getting the Good Conduct Medal I did not receive upon discharge in 1965? I had three years service and no d
Finally a real question.While the Good Conduct Medal isnt a high award, it is a real award, and it is common to make a display of one's military awards to commemorate your service, and you want the complete set.Okay, first you need to look on your dd214… did they type in the letters GCM? At a minimum, you earned the NDSM, and GCM —two awards for serving honorably in 1965. The NDSM was because Vietnam had kicked off by 1965 and so you were in an army at war (yeah yeah, police action, so was Korea) anyone in service January 1, 1961, to August 14, 1974 got this automatically. You should have two medals or more, depending on if you deployed, or you served in an elite unit, etc. These days that stuff automatically populates by computer—back then a personnel clerk would have had to type it in.Sometimes that happens and while the unit doesn’t give you your medal, it is right there in the 201 file so they put it on your paperwork. When I retired they forgot to give me my retirement award, and I had to ask the clerk for it.If GCM is there, you can get your “lost” medal issued here at no cost to you:How to Replace Lost Military Medals, Awards, and DecorationsOkay, what if you lost your DD-214 and you can't tell if you were ever awarded the GCM? Get a copy of your DD-214Request your military service records (including DD214) | Veterans AffairsOkay, you have your military records, and the E-4 who cut your discharge orders was having a bad day and didn't type anything in the awards block of the DD-214.Now what? You have to get your DD-214 amended to correct the mistake.HRC Homepage“If you are in need of a correction to your Certificate of Release of Discharge from Active Duty (DD Form 214), you must submit a written request for a correction (DD Form 215) and include a copy of your DD Form 214. Your request needs to provide details about the items you believe to be in error including copies of documentation that support the changes.If you are a discharged veteran, changes to your official records are only warranted if the change occurred during your tour of active duty or reserve service.If you are a retiree, you can request change or correction of your official military records any time. Changes include information such as your name, social security number, date of birth or place of birth. You must attach copies of supporting documents to your request. Examples of supporting documents include:Divorce decreeCourt orderBirth certificateSocial Security CardYou can submit your requests in letter format (dated and with signature) or on a Standard Form 180, (download form in .PDF format).Mail your request to:CommanderU.S. Army Human Resources CommandATTN: AHRC-PDR-H/Dept 4201600 Spearhead Division AveFort Knox, KY 40122If you feel that an error or injustice exists in your military records and you have exhausted all other administrative remedies available, you may apply for corrections to the Army Board for Correction of Military Records or to the Army Discharge Review Board. You can obtain application forms and information from the Army Review Board Agency (ARBA), Commercial Tel #: 703-545 6900.”What you are asking for is easy and the first level clerk who gets your request can probably handle it. The tough cases they get are upgrading less than honorable discharges to honorable, or requests to upgrade awards because the person unfairly got a lower award due to racism or bias. What you want is quite doable. Good luck!
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How to scan and save an electronic signature?
How to sign in color on pdf?
Get more for eSignature Document for Administrative Computer
- How To Set Up eSignature in 1Password
- How Can I Implement eSignature in DropBox
- How Do I Integrate Electronic signature in ServiceNow
- Help Me With Set Up eSignature in 1Password
- How Can I Set Up eSignature in 1Password
- Can I Set Up eSignature in 1Password
- How To Integrate Electronic signature in NetSuite
- Help Me With Integrate Electronic signature in NetSuite
Find out other eSignature Document for Administrative Computer
- Form 3536 fill out ampamp sign online dochub
- Ca form 592 v fill out ampamp sign online dochub
- Nps form 10 930 application for special use permit for national mall and memorial parks special use permits
- 2023 form 592 resident and nonresident withholding statement 2023 form 592 resident and nonresident withholding statement
- Ftb 1123 forms of ownership california franchise tax
- 2023 form 592 a payment voucher for foreign partner or member
- And instructions for tax year 2023 form
- How to complete declaration form
- Arizona department of revenue azdorstate of arizona department of revenuearizona department of revenue azdor form
- Measure o senior citizen excemption claim form
- Handicap parking permit 529585664 form
- Arizona form a1 r 2022
- Da 5646 form
- Windjammers 2 will have switch owners in a spin next year form
- Formal hearing request illinois secretary of state 633524149
- Pdf doesnt display anything complains about my pdf form
- Jv 535 findings and orders limiting right to make ocde form
- Name you want to be known as form
- Jv 460 633533649 form
- Jv 287 confidential information