eSignature Presentation for Legal Computer
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






Advantages of Utilizing a Presentation Computer for airSlate SignNow
In the current digital landscape, employing a presentation computer to oversee documents has become vital for enterprises. One notable tool is airSlate SignNow, which provides effortless eSignature solutions and document oversight. This guide will outline the advantages of using airSlate SignNow and how to efficiently get started.
Initializing airSlate SignNow on Your Presentation Computer
- Launch your web browser and go to the airSlate SignNow website.
- Set up a complimentary trial account or log into your existing one.
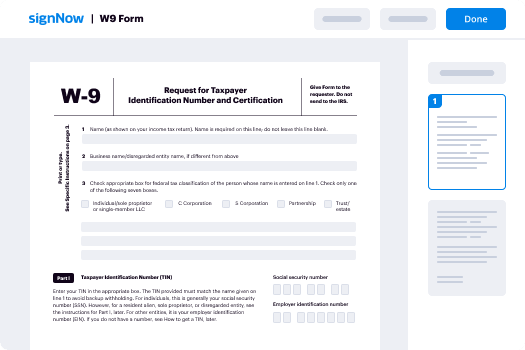
- Choose the document that you want to sign or send for signatures.
- If you intend to reuse this document, think about saving it as a template.
- Open your document to make required adjustments, such as adding fillable fields or including essential information.
- Insert your signature and assign signature fields for the recipients.
- Click 'Continue' to set up and send the eSignature invitation.
Using airSlate SignNow on your presentation computer not only streamlines the signing procedure but also improves document management efficiency. Its intuitive interface enables businesses to optimize their workflows without the complications of intricate systems.
Eager to enhance your document signing experience? Register for airSlate SignNow today and discover an affordable solution with clear pricing, outstanding support, and a comprehensive feature set designed for businesses like yours!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is a presentation computer and how can it enhance my presentations?
A presentation computer is a device specifically designed to create, manage, and display presentations effectively. By using a presentation computer, you can seamlessly integrate multimedia content, animations, and transitions to engage your audience. This enhances the overall effectiveness of your presentations, ensuring that your message is communicated clearly and memorably.
-
Can I integrate airSlate SignNow with my presentation computer?
Yes, airSlate SignNow can easily be integrated with your presentation computer to streamline document signing during your presentations. This integration allows you to send and eSign documents on the spot, making your presentations more interactive and efficient. With a few clicks, you can ensure your audience can sign important documents directly from your presentation.
-
What features should I look for in a presentation computer?
When selecting a presentation computer, look for features such as high processing power, a dedicated graphics card, and ample RAM to handle complex presentations smoothly. Additionally, ensure it has multiple connectivity options for peripherals and displays, as well as software compatibility for popular presentation tools. These features will enhance your overall presentation experience.
-
What are the benefits of using airSlate SignNow with my presentation computer?
Using airSlate SignNow with your presentation computer offers numerous benefits, including real-time document signing and reduced turnaround times. This allows you to keep your audience engaged while handling essential paperwork, thereby improving operational efficiency. Moreover, airSlate SignNow's user-friendly interface makes it easy to manage documents during your presentations.
-
How much does airSlate SignNow cost for businesses using a presentation computer?
airSlate SignNow offers flexible pricing plans that cater to businesses of all sizes, making it an affordable solution for users of presentation computers. The pricing typically varies based on the features and number of users, but you can expect a cost-effective solution that enhances your document management processes. Visit our pricing page for detailed information on available plans.
-
Is airSlate SignNow compatible with various presentation software?
Yes, airSlate SignNow is compatible with a variety of presentation software, making it an excellent choice for users of presentation computers. Whether you are using Microsoft PowerPoint, Google Slides, or other popular tools, you can easily integrate eSigning capabilities into your workflow. This compatibility ensures that you can manage your documents efficiently while delivering compelling presentations.
-
How does airSlate SignNow ensure the security of documents signed during presentations?
airSlate SignNow prioritizes document security by implementing advanced encryption protocols and secure storage solutions. When using a presentation computer, you can trust that all signed documents are protected against unauthorized access and data bsignNowes. This commitment to security allows you to focus on delivering impactful presentations without worrying about document safety.
-
What is the best real estate technology?
A survey conducted by Coldwell Banker and CNET found that eighty-one percent of prospective home buyers were drawn to homes equipped with the latest in-home technology. Among those, thirty-five percent of people who preferred what is known as smart homes over traditional residences believed that such features solidified the property as “move-in ready.”Technology is also changing the field of home selling. Here are five ways that apps and other online features are making the life of a real estate agent easier.1. Broadcasting with Periscope and TwitterWhat better way to send out a massive blast than on Twitter? The social media site lets you keep it short but sweet as you tell followers that the home of their dreams has an upcoming open house session. You can also post pictures on Twitter that give potential buyers a better perspective of what they will see during their in-person tour of the property. Take the virtual showing a step further by using Periscope to share live footage of yourself walking through the house online. In past times, a substantial amount of money was necessary to promote property by way of commercials. Twitter and Periscope bring the perk to you for free so long as you have a smartphone or tablet when going live and taking pictures.2. Tracking with Glympse and WazeRunning twenty minutes behind used to be a deal breaker pre-Digital era. Not only did you inconvenience the client but you also provided a guess that was often inaccurate and led to more time wasted at the property. Traffic apps in the twenty-first century have made such estimating unnecessary.Waze is one app that provides navigation tips based on real-time traffic information. You can better coordinate appointments so that clients are not left waiting for several minutes and provide clearer updates when you are running late. Glympse also tracks traffic in real-time but takes things a step further by offering a link by which clients can track your whereabouts. Text or email the URL to prospective buyers and let them follow along as you make your way to the location.3. Meet Online with Reflector 2 and Join.meReal estate agents should consider investing in Reflector 2 instead of bringing their USB stick along to nail that next listing presentation. The app serves as a sort of projector by allowing you to cast all activity on your smartphone and tablet on a larger screen. The Reflector 2 works with nearly any device and does not require additional purchase outside of the app itself.Free Screen Sharing, Online Meetings & Web Conferencing is another app that has made buying a selling a home more convenient. Agents can hold brief meetings with clients without requiring them to come into the office. Sharing your computer screen is the best way to convey pertinent information to new homeowners. The recording and playback feature is particularly useful when you need to recall a client’s home preferences. They will be impressed with your attention to detail in finding a house with a built-in barbecue pit. You will know that such meticulousness is because of Free Screen Sharing, Online Meetings & Web Conferencing.4. Add Transparency and Rapidity with an Automated Mortgage Loan ProcessThe traditional method of the home loan process involved hours spent trying to secure financing. Leaving one paycheck stub or bank statement at home often meant holding off on the process until the client was able to furnish proof of such documentation. There was no transparency in the process, which meant that customers were entirely reliant on the expertise of the real estate agent.Technological advances have revolutionized the mortgage loan process. Automated processing now establishes criteria by which applicants are judged that makes applying simpler. Some financial institutions can pre-approve hopefuls in ten minutes. Individuals who go through the entire process may see their loans finalized in ten days instead of the average four-week period. Digital tools provide real-time updates so that even those who are not approved can move on to the next bank quickly instead of waiting for a rejection letter to arrive by way of snail mail.5. Agree from Home with E-signaturesIn past times, the thrill of closing quickly became inconvenient for buyers upon hearing that all approved owners would need to stop by the real estate agent’s office to sign final documents. Some individuals were forced to take a sick day from work just to make their mark on the paper. Such heartache is why the masses are thrilled to learn that e-signatures have the same weight as traditional marks on legal documents. A real estate agent can email paperwork that his clients can sign at their leisure and return electronically. It is even possible to solidify documents on a smartphone in some instances, which makes the home loan process that much more convenient.
-
What digital tool, as a real estate agent, do you most use?
As an agent, we have access to the MLS, which the public only has limited access to. In my area the public can see exactly what Zillow can which is active listings. Our board does not disclose the sales price of closed prices, which makes services like Zillow pretty much worthless in my area. (Zillow may be useful in some areas, perhaps many, just not where I work).That said, my favorite and most useful tool, which is also available to the public, is the GIS (Government Information Service). Type in to Google: (Your county)(Your state) GIS [ie: Marion County Indiana GIS ] . While it isn’t available in every county of the country, you will find it in most major areas. It will give you access to the tax assessor records and often times the sales history of the property. The tax records will give you the details of site size, improvements, assessed values and depending on the county may or may not give you the annual taxes.Since real estate agents in some areas count the basement area when they list the size of the property, the GIS will allow me to figure out what is really there if I’m new to the area. For what I am looking for, there is a signNow difference between a stated 3,600 square foot house by the agent and 1,800 square foot above ground over a 1,800 square foot basement. - Lenders only count the above ground square footage as living area when making a loan.Hope this helps.
-
Is ticking a check box for an online contract like a signature in the USA?
In the U.S., ticking a checkbox routinely is considered evidence showing that a user has accepted online terms and conditions. (Please see Online Terms can be Binding, even if You don’t have to Click!)This is, indeed, similar to a signature on a hard-copy contract being evidence showing that a party has agreed to that contract.
-
What industries must use electronic signature software?
Any industry involving a large amount of paperwork make use electronic signatures. In other words, all industries make use of electronic signatures because all of them have piles of paperwork to handle. Some examples of such industries include financial, life science, healthcare and pharmaceutical industries.Industries such as the pharmaceutical industry, have a number of licenses and other paperwork that they have to handle and keep track of. It can be a tedious task to perform such cumbersome paper processes. Therefore, e-signatures can facilitate an organisation in keeping a track of all this paperwork, by signing electronically.Healthcare industries usually involve time-sensitive documents, which need to be urgently completed. But, it can take days in case of the traditional wet ink paper signatures for the documents to signNow the signer and back, if the parties are geographically scattered. But with electronic signatures, that is not the case. Geographical barriers do not play a role. Documents which earlier needed days to be completed, can now be signed and sent back within minutes, in the click of a button. Furthermore, it takes a long time to bring assets under management. The time taken by the signing process, if wet ink paper signatures are used, may even further delay the process. But by using electronic signatures, the whole process can speed up.Apart from these, there are many paper prone industries which require huge amount of paperwork and with the use of electronic signatures they can make their everyday processes smoother and more efficient.
-
What are elite upcoming tech startups ideas and technologies?
In terms of the most exciting tech startup ideas, let’s clarify that “exciting” could mean immediate cash or it could mean sentient recommender systems and robotic bartenders. The opportunity for business impact is usually due to the fact that society has still failed to adapt to the paradigms of what’s possible for computers. There are existing, amazing technologies that are going to waste!Solved Problems Waiting For AdoptionWhen computers were invented, people weren’t sure how to work with them, so everything was essentially just a digital adaption of existing processes. This also influenced the naming − “email”, “e-signature” etc. Emails should more accurately be called “e-postcards” btw, since everyone along the way can read it and it certainly doesn’t have to be this way.On the Internet, we still often don’t really know who people are; and we still make mistakes that are meant to be within the realm of “robotic” thought − we lose things; we forget things; we make mistakes in calculations; we leave our information vulnerable. In particular I’d like to mention spreadsheets − they were based on the idea that humans can understand what’s happening between the columns, but for VLOOKUP, they can’t infer what’s going on and they need to easily see the formulas or there are going to be mistakes. There are trillions of dollars being caused by avoidable problems, as discussed in Spreadsheets Are Sabotaging Your BusinessWord-processing suffers many of the same problems as spreadsheets btw − data; algorithms; and presentation should be kept separate. To achieve this, documents should be written in LaTeX (or even Jupyter Notebooks & MathJax), not Microsoft Word or its clones.I don’t consider blockchains as an obvious solution that should’ve already been adopted, but now that they exist, we have a similar scenario to the already-mentioned problems, where there’s plenty of opportunity to solve real problems right now. Ethereum in particular can be used to solve problems around provenance; escrow; and even the legal immunity of computing.A Practical Guide To Eternal LifeFuturistic Technology For Our Other ProblemsComputers struggle to see; it’s just not something that you can expect a calculator to do; and yet, at the LDV Vision Summit, it became clear that through sheer perseverance, humans are pushing computers to use images as the input for seemingly any problem imaginable. IBM Watson can now accurately classify food and its portion sizes from photos. It would’ve been easier with a scale, but whatever, humans take pictures; they share pictures; and they hence provide plenty of training data for machine learning. Nobody shares the data from their scales except on Grindr.Tell me what you eat, and I’ll tell you what you areIn judging these future technologies, I think we can clearly make the conclusion that society is just going to do its own thing for decades, even if it’s the wrong approach. Computers can still become smarter thanks to all the training data, but unfortunately we can’t count on consumer adoption of a product simply because it’s good or even optimal.There are a few startups that can be put in both buckets − they’re using futuristic technology to solve problems that could’ve already been solved, had people just adopted the right solution. Tanuki.ai is one of these. Adoption of Tanuki’s software is a critical part in the roadmap to liberating humanity from its existing enslavement, where we’re performing the tasks of robots.
-
How are cracked versions of software created and why are developers not able to prevent it?
Cracked versions of software are created with the use of debuggers. (A debugger is a special type of software that lets programmers deconstruct their software into its constituent parts for the purpose of finding bugs, and thus de-bugging. Additionally debuggers can be used for reverse-engineering, or to see what is inside the software, to learn its logic. The latter method is used mostly by malware researchers to study what malware (or computer viruses) do on-the-inside. But it can be also used by an attacker to "crack" (or bypass) legal software registration, or at times, to alter normal behavior of software, for instance by injecting a malicious code into it.)For the sake of this example, I will assume that the software that is being "cracked" was compiled into a native code, and is not a .NET or a JavaScript based application. (Otherwise it will be somewhat trivial to view its source code.) The compiled native code is a bit more tricky "beast" to study. (Native means that the code executes directly by the CPU, GPU, or other hardware.)So let's assume that the goal of an attacker is to bypass the registration logic in the software so that he or she doesn't have to pay for it. (Later for lolz, he or she may also post such "crack" on some shady online forum or on a torrent site so that others can "use" it too and give him or her their appreciation.)For simplicity let's assume that the original logic that was checking for the software registration was written in C++ and was something similar to the following code snippet:In this code sample "RegistrationName" and "RegistrationCode" are special strings of text that a legitimate software user will receive after paying for the license. (The name is usually that person's actual name or their email address, and the code is some string of unique/special characters that is tied to the name.)In the logic above, the function named "isRegistrationCodeGood()" will check if "RegistrationName" and "RegistrationCode" are accepted using some proprietary method. If they are, it will return true. Otherwise false. That outcode will dictate which branch (or scope) the execution will follow.So the logic above will either show that registration failed and quit:Or, if the registration code and name matched, it will save the registration details in persistent storage (such as the File System or System Registry) using the function named "rememberRegistrationParameters()" and then display the message thanking the user for registering:A "cracker" will obviously want to achieve the second result for any registration code that he or she enters. But they have a problem. They do not have the C++ source code, part of which I showed above. (I hope not!)So the only recourse for an attacker is to disassemble the binary code (that always ships with software in the form of .exe and .dll files on Windows, and mostly as Unix executables inside the .app packages on a Mac.) An attacker will then use a debugger to study the binary code and try to locate the registration logic that I singled out above.Next you can see the flowchart for a snippet of code that I showed in C++, presented via a low-level debugger. Or, as the code will be read in the binary form after compilation:(For readability I added comments on the right with the names of functions and variables. They will not be present in the code that an attacker could see.)(To understand what is shown above an attacker will have to have good knowledge of the Assembly language instructions for the native code.)I also need to point out that having a disassembly snippet like the one above is the final result for an attacker. The main difficulty for him or her is to locate it among millions and millions of other similar lines of code. And that is their main challenge. Not many people can do it and that is why software "cracking" is a special skill.So having found the code snippet above in the software binary file a "cracker" has two choices:1) Modify (or patch) the binary.2) Reverse-engineer the "isRegistrationCodeGood()" function and copy its logic to create what is known as a "KeyGen" or "Key Generator."Let's review both:The first choice is quite straightforward. Since an attacker got this far, he or she knows the Intel x64 Instruction Set quite well. So they simply change the conditional jump from "jnz short loc_7FF645671430" at the address 00007FF645671418 (circled in red in the screenshots) to unconditional jump, or "jmp short loc_7FF645671430". This will effectively remove any failed registration code entries and anything that the user types in will be accepted as a valid registration.Also note that this modification can be achieved by changing just one byte in the binary code from 0x75 to 0xEB:But this approach comes with a "price" of modifying the original binary file. For that an attacker needs to write his own "patcher" (or a small executable that will apply the modification that I described above.) The downside of this approach for an attacker is that patching an original executable file will break its digital signature, which may alert the end-user or the vendor. Additionally the "patcher" executable made by an attacker can be easily flagged and blocked by the end-user's antivirus software, or lead criminal investigators to the identity of the attacker.The second choice is a little bit more tricky. An attacker will have to study "isRegistrationCodeGood()" function and copy it into his own small program that will effectively duplicate the logic implemented in the original software and let him generate the registration code from any name, thus giving any unscrupulous user of that software an ability to register it without making a payment.Vendors of many major software products understand the potential impact of the second method and try to prevent it by requiring what is known as "authentication." This is basically a second step after registration, where the software submits registration name to the company's web server that returns a response back to the software of whether the code was legitimate or not. This is done by Microsoft when you purchase Windows (they call it "Activate Windows") and also by signNow, and many other companies. This second step may be done behind-the-scenes on the background while the software is running, and will usually lead to cancellation of prior registration if it was obtained illegally.So now you know how software is "cracked".Let me answer why it is not possible to prevent it. It all boils down to the fact that any software code needs to be read either by CPU (in case of a binary native code) or by an interpreter or a JIT compiler (in case of JavaScript or .NET code.) This means that if there's a way to read/interpret something, no matter how complex or convoluted it is, an attacker with enough knowledge and persistence will be able to read it as well, and thus break it.There is an argument though that cloud-based software is more secure, which is true, since its (binary) code remains on the server and end-users do not have direct access to it. And even though cloud-based software is definitely the future, it has some major drawbacks that will never allow it to fully replace your conventional software. To name just a few:Not everyone has an internet connection, or is willing to upload their data online. Additionally someone’s internet connection can be very expensive or too slow to make the software run very laggy.Then there’s a question of distributed computing. For instance, Blizzard Entertainment would never make “World of Warcraft” to fully run on their servers due to immense computational resources needed to render every single scene for every player they have. Thus it is in their best interest to let each individual user’s computer to do the rendering instead.As a software developer myself, I obviously don't like when people steal software licenses. But I have to accept it and live with it. The good news is that there are not that many people who are willing to go extra mile and search for a cracked version of software. The main problem for those who do, is that by downloading a patched executable, or an attacker's KeyGen or a Patcher, they are effectively "trusting" him or her not to put anything "nasty" into it that was not "advertised on the package" (stuff like trojans, malware, or keyloggers.) So the question for those people becomes -- is it worth the cost of the software license to potentially infect your system with a nasty virus?On the other side of the equation, some developers react very negatively to any attempts to steal their software licenses. (I was there too.) They try to implement all kinds of countermeasures -- anything from tricking reverse-engineers, to adding booby traps in the code that may do something nasty if the code detects that it is being debugged, to obfuscating or scrambling the code, to enforcing all kinds of convoluted DRM schemes, to blocking users from certain countries. I personally try to stay away from all of those measures. And here's why:A) Any kind of anti-reverse-engineering tactics could be bypassed by an attacker with enough persistence. So why bother and waste my time when I can invest that time into adding something useful to my software that will make it more productive for legitimate users?B) Some code packers could create false positives with antivirus software, which is obviously not good for marketing of that software. It also creates unnecessary complexity for the developer to debug the software.C) Adding booby traps in the code can also “misfire” on your legitimate users, which will really infuriate them and can even lead to lawsuits.D) Any DRM scheme will probably catch some 100 illegal users and greatly inconvenience 10,000 legitimate ones. So why do it to your good customers?E) Our statistics show that about 75% of all illegal licenses come from China, Russia, Brazil, to name the worst offenders. (I also understand that the reason may be much lower incomes that people have in those countries.) The main issue for us though was the fact that if we enforce our DRM or add some strong registration authentication, many people that wanted to bypass our registration would simply use a stolen credit card number. And we had no control over it. Our system will use it to send them a legitimate license only to have the payment bounce in weeks time. As a result we would lose the money that were paid for the license, plus the credit card company will impose an additional chargeback fee to our account, which may range from $0.25 to $20 per bad purchase on top of the license cost.F) As was pointed out in the comments, some companies may actually benefit from allowing pirated copies of their software. Microsoft for instance gets a lot of free publicity from people using their Windows OS, the same goes for signNow with their Photoshop. That is a good point that I agree with.So my philosophy is now this -- if someone wants to go extra mile and steal our software, go for it! They went this far to do it anyway, so they probably have a good reason. On the positive side there are so many other customers that appreciate the work that goes into creating software that greatly outnumber those that don’t.PS. Thank you for all your feedback! It makes me feel good that the knowledge I shared is useful to others.
-
Why does a digital signature certificate have a limited validity period?
Digital signature certificates have an explicit start date and an explicit expiration date. Most applications check the validity period of a certificate when the digital certificate is used.The signature certificate expiration date is also used for managing the certificate revocation list (CRL). A certificate is removed from the revocation list when its natural expiration date arrives. As such, generally the shorter the certificate validity period, the shorter the CRL.
-
Have you ever gone into a limbo?
“Creativity is the answer.”They robbed me of $1 million. Judges and attorneys did this to me. There’s an entire organization of us that this has happened to. No justice for any of us, so far. (See our organization: Educate - Advocate - Legislate for more information about legal court theft that attorneys and judges and corporate guardians engage in.)I know. This is not a happy topic.Without my alter ego, Angelina, the Polka Queen, I would not have survived. I would be dead. It’s true. Others in my organization have literally died from the stress of it all. (Latifa Ring, our former leader, is dead.)My limbo lasted for ten years.For ten years, I was “imprisoned” because I believed in justice so strongly and I believed in the American Way. We grow up that way. We grow up believing that the American courts are fair and just. I kept writing more and more court papers, thinking that some honest judge would finally listen to me. An attorney forged my signature to commence the endless theft. I thought justice would eventually be rendered through our American court system. I spent 10 years trying to get back the money they were systematically stealing from me.So, when the despicable attorneys started to systematically rob me of my $1 million inheritance, which I helped to create and earn (I worked side by side with my abusive parents from the time I was six years old in our family businesses), I firmly felt that justice was right around the corner. But one day turned into one week. One week turn into one month. One month turned into one year. Soon, ten years had passed. I had no idea this would happen.Imagine what my deceased parents would say if they could come back and see what judges and attorneys did to me (and many others). We sat there on the living room floor every night, the three of us, in the days long before air conditioning, rolling up pennies and nickles and dimes and quarters in the heat of the night to take to the bank in the morning after a hard, full day of work at our family owned businesses. What if my parents could come back and see that attorneys took that change we sweat for, that ended up being our $1 million nest egg?What the attorneys did was so vile, so corrupt, and so surreal that I just could not actually believe that this was actually happening in the United States of America. I kept thinking, “There’s going to be some judge, some agency, some police department that will stop their taking a million dollars from me.”That day of court justice never arrived.For ten years, I sat in front of a computer screen. I wrote my own court papers. I spent the days researching court cases. I visited various courthouses and found evidence of fraud in similar cases. I contacted other victims. I formed a group. Together, we petitioned the state attorney’s office, the FBI, the Florida Judicial Qualifications Commission, the Department of Justice, and other agencies. I wrote and submitted a 300 page report — well-written, meticulous — enough evidence to put all of them behind bars.I started to realize what it means to be a Civil Rights Activist.I put aside all that I loved and had known my whole life for ten years. I put aside my music, my friends, pot luck music jams, my hobbies, and all that is creative. There is something deep inside of all of us that screams out for justice when something terribly, horribly wrong is going on.During each day, each court paper that I composed over a ten year time period, sitting there cramped in a chair, staring for hours on end at a computer screen, growing fat and unkempt, I kept thinking, “Tomorrow will be the last day of this. Tomorrow will be the day the judge realizes I am telling the truth. Tomorrow, justice will be rendered.”But then another batch of court papers would arrive in the mail.A sickening feeling would enter the pit of my stomach when I would open my mailbox.I got to the point where I would go weeks without opening my mailbox. I just could not bear it.Legal Fatigue Syndrome started to take over. I started watching TV a lot and eating entire pizzas. I slept a lot.But after several days in a row of doing this, I’d get up and put on one of my Polka Queen dresses. Over the years, I have stitched more than 200 Polka Queen dresses by hand.I’d don a tiara and strap on my accordion and “WEEEEEEOOOOOOO!!! IT’S POLKA TIME!!!!” I’d announce to my audience of SELF in the mirror.It’s finally over.Justice was never rendered. They stole all of my inheritance money from me — $1 million.But Angelina, the Polka Queen kept me alive.Angela V. Woodhull's answer to What is it like to lose $1 million of inheritance money due to court fraud?Angela V. Woodhull's answer to What are the five most common American court scams that the majority of people don’t even know about?Angela V. Woodhull's answer to What is the most callous thing anybody has ever said to you?Angela V. Woodhull's answer to Is USA a good place to live in?P.S.— I just received this e-mail (copy/pasted below) from an organization called “Equal Access Advocates.” Here’s what the e-mail says:“What's wrong with me?”Prolonged litigation is wearing me down financially and my health is failing. My life and priorities seem irrelevant to the court and it’s overwhelming. I’m angry that they can’t see what’s really going on, and I’m sad that I can’t just ‘make it right’.You need to know:"There is nothing wrong with you."If this sounds like you or a loved one (or a client) then it’s a story of being ensnared in the judicial system.Fearful, incredulous, isolated, beyond rage . . . feeling "alienated? Dr. Karin Huffer and her research shows a subtype of Post-Traumatic Stress Disorder called Legal Abuse Syndrome. When systems of care, i.e. the judicial system, cause or exacerbate medical conditions due to extreme stress, the dilemma presents a public health problem as well as a multidisciplinary legal/medical professional challenge. There is help for Legal Abuse Syndrome. Victims overcome psychological devastation caused by prolonged injustice by using methods developed by Dr. Huffer.”P.S.—Thank you, Aadesh Deshmukh, for asking this question of me. Maybe you, too, are going through a Trial by Fire right now. I think most people are faced with a serious, overwhelming Trial by Fire at some point in their lives. Mine was becoming aware of and experiencing extreme court fraud and court robbery. If you are currently going through a Trial by Fire, I sincerely hope that you will be able to live through it, learn from it, and remain a positive, loving person. So many people end up bitter in life. For me, it still overwhelms me — even to write about it. I suspect my next piece on Quora will be something simple and frivolous, like “How to Make a Vegetarian Corn Dog.” I can only write about what I experienced in small spurts. I’m still truly overwhelmed when I process it all. It was ten years of my life that I will never get back.PPSS — Other victims of this same, corrupt judge are holding a march next month and have started an online petition. Sign Petition: Corrupt and Destructive Judge Galluzzo Off The Bench, Now!! They also are making a documentary film about him. I will no longer participate. I’m just too worn out.PPPSSS — Quorans, I know it’s not so happy and funny and entertaining when I write about this 10 years of court fraud . . . but I really want you to know about this. This can happen to you. It’s a quite common practice, but little known. I really want you to know about this so that it won’t happen to you. Read up more on this topic, okay? It’s important that you know about this. Court reform in the USA is so desperately needed.
-
What is a digital signature, and why do we need this?
What is Digital Signature?A digital signature is basically a way to ensure that an electronic document (e-mail, spreadsheet, text file, etc.) is authentic. Authentic means that you know who created the document and you know that it has not been altered in any way since that person created it.Digital signatures rely on certain types of encryption to ensure authentication. Encryption is the process of taking all the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Authentication is the process of verifying that information is coming from a trusted source. These two processes work hand in hand for digital signatures.How do I get a Digital Signature?Digital Signature Certificate (DSC) is a secure digital key that certifies the identity of the holder, issued by a signNowing Authority (CA). There are many companies provide Digital Signature , i.e.SIFYeMudhra(n)codeThese companies gives LRA to several companies that are basically known as LRA. You may directly apply online and purchase from your local authority.Digital Signature for E-tenderingThere are three types of digital signature certificates depending on the validation of identity and type of use. They are:Class I DSC – Individuals get it for validating the email identification of the users and in situations where risk is minimal and here the signature is stored in software.Class II DSC – Business organizations or individuals use this digital signature certificate to validate the information given by the subscriber in the application against the information available in a trusted consumer database and in other such situations where security risk is moderate. In this case a hardware cryptographic device is used for storing the signature.Class III DSC – This digital certificate is directly issued by the signNowing authority and it is required that the person applying for DSC must be present at the signNowing authority’s premises and prove his/her identity in front of the authority and the security risk involved in this case is very high. In this case also a hardware cryptographic device is used for storing the signature.The Necessity of Digital Signature CertificatesFor e-filing of the income tax returns by any individual, the Government of India has made it mandatory to affix digital signatures to the income tax returns documents. For affixing the digital signature one must have digital signature certificates issued by licensed certification authority.In addition, Ministry of Corporate Affairs has set the mandatory guidelines for the companies directing them to file all reports, applications and forms using a digital signature only and this again requires a digital signature certificate.For GST also a company must verify its GST application by affixing a digital signature using digital signature certificate in order to get registered for GST.These days many Government procedures, filling different applications, amendments and forms require digital signatures made by using digital signature certificates.Benefits of Digital Signature CertificatesSaves Money & Time: As there is no need of physical presence you can digitally sign your PDF files and other documents using DSC anywhere & anytime. You need not sign your paper documents and then scan them to send them across through internet if you follow the above given option. You can save the money which would otherwise be spent on printing and scanning the document. You can also go green by saving paper.Secured Data: The digitally signed documents are tamper proof as the digital signatures are secured with a private key and public key and they cannot be edited after digitally signing the document.Authentic: Digitally signed documents are authentic and the receiver can be completely sure about the sender’s identity and integrity. The receiver can easily execute the information in the document without worrying about the document being forged.Certificate (DSC) is essential for companies and organizations that take part or intend to take part in eTendering processes on various Government sites. If a organisation going to apply for any Government eTender needs to have a Class 3 Digital Signature Certificate registered in the name of a representative who is authorized to submit online offers for e-Tendering applications.How to apply digital signature ?We enable compliance with legal and regulatory requirements for end-to-end electronic transactions for any kind of E-Business.What Documents required for Class 3 Digital Signature ?Documents required for Class 3 Digital SignatureApplication Form (Duly Signed)Recent Passport Size Photograph (Pasted on the Application form and Signed across the Photo)Identity ProofPAN CARD * (Income Tax F Filing Portal requires PAN Encrypted DSC)PassportDriving LicensePhoto ID Issued by Central Or State GovernmentVoter IDAadhar CardApply for Digital SignatureAddress ProofPassportDriving LicenseLatest Utility Bills - Not Older than 3 Months (Telephone, Electricity, Water, Tax, LIC)Ration CardVoter IDBank Account Statement ( Not Older than 2 Months)Service Tax/ VAT registration CertificateProperty tax/ Municipal tax ReceiptProof of Right to do Business (Any one of the Following)Certificate of IncorporationMemorandum of Association & Articles of associationRegistered Partnership deedValid Business licenses like VAT , Service Tax RegistrationLicense under shop and Establishment Act (For Proprietorship Concerns)PAN Card of the Company/FirmProof of Right to do Business (Any one of the Following)Latest annual Report / BalancesheetLatest Income Tax ReturnsOrganization Bank Details on Banks Letter Head/ Latest Bank statement attested by BankAuthorization Letter in Favor of the applicationAll Documents to be Self Attested by the applicant & Attested by the Authorised Signatory of the Business with Stamp & Seal. For More information about Best Digital Signature company in kanpur
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How to make an electronic signature from a scan?
How to integrate esign with laserapp?
Get more for eSignature Presentation for Legal Computer
Find out other eSignature Presentation for Legal Computer
- 2014 schedule f form 1040 profit or loss from farming irs ustreas
- Form 14135 rev 6 2010 application for certificate of discharge of property from federal tax lien irs ustreas
- Va form accommodation
- Atlanta vamc pgy1 form
- 10 0433 print form south texas veterans health care system southtexas va
- Appointment letter of dc industry form
- Vcs deduction form
- 10 0430 form
- Va form 21 0960c 9 multiple sclerosis ms disability benefits questionnaire vba va
- Oaan 7003 form
- Bp a0192 release of information consent jun federal bureau of bop
- Long care application form
- Az ica appeals opening brief example form
- Arizona state mine inspector asmi az form
- Dog license in flagstaff az form
- Change of venue forms
- Ol 16s 2012 form
- Ol 902 instructions form
- Application for recertification general ls calbar ca form
- Ceqa appendix g environmental checklist form