eSignature Presentation Myself
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






How to utilize e-signature with airSlate SignNow
Employing e-signature with airSlate SignNow can simplify your document signing workflow, making it efficient and straightforward. This platform is tailored to enable enterprises to dispatch and electronically sign documents with convenience, providing a user-friendly experience that is ideal for small to medium-sized organizations. In this guide, we will outline the steps to initiate your journey with airSlate SignNow and emphasize some of its advantages.
Steps to establish an e-signature with airSlate SignNow
- Launch your browser and head to the airSlate SignNow website.
- Set up a free trial account or log into your existing account.
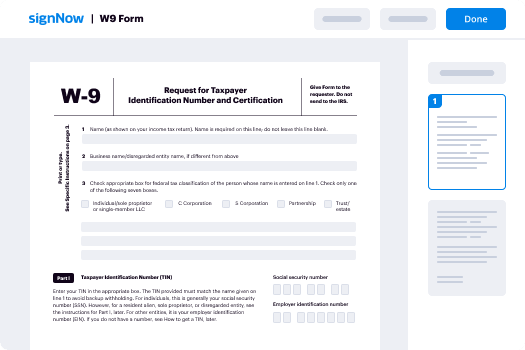
- Choose the document you intend to sign or distribute for signatures.
- To facilitate future use, consider saving your document as a template.
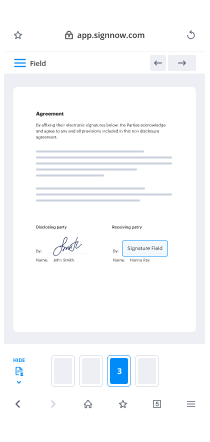
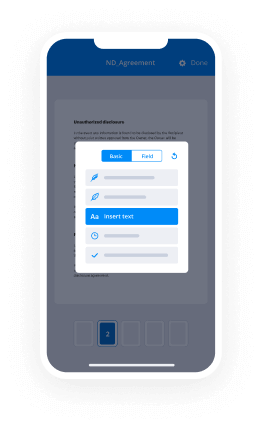
- Open your document to make any necessary adjustments, such as adding fillable fields or inserting pre-defined information.
- Position your signature on the document and include signature fields for any recipients.
- Click on 'Continue' to adjust the details and send out the eSignature invitation.
In summary, airSlate SignNow offers a comprehensive solution for businesses aiming to improve their document management processes. With its extensive feature set and clear pricing, it provides excellent value for your investment while ensuring usability and scalability.
Begin reaping the rewards of airSlate SignNow today. Enroll for a free trial and change the way you manage your document signing!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is an e myself signature and how does it work?
An e myself signature is a digital signature that allows you to sign documents electronically. With airSlate SignNow, you can create your own e myself signature in just a few clicks, making the signing process faster and more efficient. This feature ensures that your documents are signed securely and legally.
-
Is airSlate SignNow suitable for small businesses looking to use an e myself signature?
Absolutely! airSlate SignNow is designed to be a cost-effective solution for businesses of all sizes. Small businesses can easily implement the e myself signature feature to streamline their document signing process without breaking the bank.
-
What are the key features of airSlate SignNow’s e myself signature solution?
airSlate SignNow offers several key features for its e myself signature solution, including secure document storage, customizable templates, and audit trails. These features not only enhance the signing experience but also provide peace of mind by ensuring compliance and security.
-
How does airSlate SignNow ensure the security of my e myself signature?
Security is a top priority for airSlate SignNow. The platform uses advanced encryption and secure servers to protect your e myself signature and any documents you sign. Additionally, airSlate SignNow complies with international e-signature laws, ensuring that your signatures are legally binding.
-
Can I integrate airSlate SignNow with other tools to enhance my e myself signature workflow?
Yes, airSlate SignNow seamlessly integrates with a variety of tools and applications such as Google Drive, Salesforce, and Microsoft Office. This integration allows you to enhance your e myself signature workflow by easily accessing and managing documents from your preferred platforms.
-
What pricing plans are available for using the e myself signature feature?
airSlate SignNow offers flexible pricing plans that cater to different needs, including a free trial for new users. Each plan provides access to the e myself signature feature along with a range of other functionalities, allowing you to choose the one that best fits your business requirements.
-
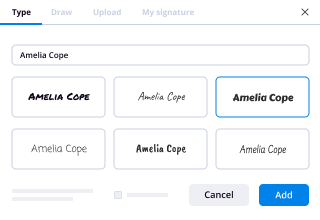
How do I create an e myself signature using airSlate SignNow?
Creating an e myself signature with airSlate SignNow is simple and user-friendly. You can create your signature by drawing it on a touchscreen, typing it out, or uploading an image of your handwritten signature, making it easy to personalize your signing experience.
-
Who is the greatest enemy of Islam and of Pakistan, in Pakistani public opinion?
Perspective 1:You might have come across these nature of images either through videos or articles at social/print media.There is one group of people in Pakistan (mostly right wing religious parties) that believes that USA, Israel and India are biggest enemies of Pakistan and Islam. They think that Pakistan is suffering at all fronts due to them. Whenever any bad thing happens either in Pakistan or rest part of Muslim world, they call protests after Juma Prayers. They curse these three countries and burning flags is their signature moment. They are in opinion that Pakistan was founded in the name of Islam so these countries want to eliminate us at every cost.Perspective 2:You might have come across these nature of pictures as well.During last decade, Honor of Prophecy (Namoos e Risalat) has become one of the most sensitive subjective in Pakistan. You may lose your life or face severe consequences in case of saying any unpopular opinion in general public over this subject. Salman Taseer, Shahbaz Bhatti and notably Mashaal Khan lost their lives on account of blasphemy charges. Local religious Cleric Khadim Hussain Rizvi has emerged over the years who leads Honor of Prophecy protests. last year when Asia Bibi was acquitted by Supreme Court of Pakistan from all blasphemy charges, protesters led by Khadim Hussain Rizvi came on roads and burnt public properties of innocent people. They abused/threatened govt of Pakistan, Armed Forces and Supreme Court. On account of these developments, one group of Pakistanis think that these type of people led by Khadim Hussain Rizvi are biggest enemies of Pakistan who are using Islam for their personal gain. They think they are giving bad name to our religion as well as country.I have presented both perspectives so I myself is not going to draw any conclusion. Please read and decide who are “Real Enemies” of Pakistan and Islam. I will be looking forward for your feedback and comments.Disclaimer: The author has written an answer by giving perspective of two group of people. Images were used as a reference to show the violent nature of protests. Author has no intention of disrespecting Pakistan, USA, Israel, India and Islam altogether.~MAKPictures were taken from Google Images
-
What actually happens in a UPSC interview?
I have had the opportunity of giving 'THE UPSC INTERVIEW' twice, one in 2016 and other in 2017. Both the time I had the same board headed by former Air Marshal Ajit Bhonsale.I was awarded pretty good scores both the times, 184 (in 2016) and 187 (in 2017) :)Before I answer what happens in UPSC interview, let me break some myths.MYTHSInterview questions are not like the whatsapp forwards you recieve. Example : How to throw egg from a building without breaking it?Interview is not a system of rejection or acceptance. It is just a part of whole process , your written marks are added in your interview score to determine your rank. So you may have high written score but low interview marks can mar your chances of rank and vice versa.Interview is not a test of your knowledge. Knowledge has already been tested in written examination. Interview is test of your personality and confidence. Obviously questions are asked to test your confidence but if you don't know the answer you can say “I don't know sir/ma'am” confidently instead of bluffing. You have to be truely honest.Some interview boards are dreaded due to myth that they give low marks but I think every board has its range of marks( Bhonsale Sir board is dreaded but he awarded me good marks both the times). It is just that every board chairman has probably different parameters and ways of testing you. For example : Ajit Bhonsale sir will make you really comfortable but sometimes when you become very comfortable you let yourself loose and commit blunders. On other hand B.S. Bassi sir is very strict ( I have heard) , puts in you in spot for the first few minutes. His strategy is maybe to check you during tough times.UPSC interview is not like a roadies audition. All the members of the board are highly cordial.BEFORE UPSC INTERVIEWNight before the interview is really tough. There are butterflies in your stomach. There is soo much going on in your head that sleeping becomes a task.On the day of interview it becomes quite a task for us girls because we have to tie a saree. My mom was with me so she helped me with that but handling the saree gracefully is your task. I want to tell you that I wore the same green colour saree for both my interviews because after my first interview I thought it was lucky for me :)2016 interview2017 interview ( 5 kg lighter!!)Once you signNow UPSC office on Shahjahan road , you are made to stand in a line outside the gate for verification by showing summon letters. For me this moment for the first time was in 2016 and it was really mesmerizing. I was like Aamir Khan ’s character in “3idiots” movie where he couldnt stop smiling because it felt like a dream.After all verification candidates are made to sit in a room for document verification. There are 6 tables with 6 candidates each. All the 6 candidates on one table go to same interview board. After document checking candidates are moved to a central hall. Here we are finally told which board we are assigned.Candidates are called one by one for the interview and headed towards respective members 's rooms. A candidate is called 5 minutes before the previous candidates 's interview is over. So you are made to sit outside the interview room. This is the most unnerving moment. My strategy used to be: to sit and gaze around so that I don't think about the impending interview and calming myself in the process. And finally after few minutes the peon asks you to GO INSIDE!!DURING THE INTERVIEWHere I will narrate my 2017 CSE interview held on 24 th April 2018:I entered the room I wished everyone good afternoon ( it was around 1:30 pm ). I was asked to take seat. The interview board had chairman (Air Marshal Ajit Bhonsale Sir in my case) and 4 other members seated around a table. There was a member seating very close to me and watching my every action, most probably he was psychoanalysist or something like that.So finally the interview started :CHAIRMANChairman : Shilpa sit down. Feel comfortable. Take a deep breath. I see a young and smart lady in front of me who has a very good academic background. Are you nervous?Me: No sir ( I smiled)CHAIRMAN : Ok then we will start with the interview.Which areas you are expecting that we would ask from DAF ( detailed application form , it is like a CV which contains information about you, your qualification, your hobbies etc).Me: Sir about my graduation i.e. BDS , my birthplace Chandigarh and hobbiesChairman : What do you derive from making greeting cards? ( Apart from reading , teaching/ mentoring , I mentioned “making handmade greeting cards” as my hobby in DAF)Me: Sir, it is a form of creative expression for me which gives me immense pleasure.Chairman : Ok shilpa.MEMBER 1M1 : What are your views on death sentence for rape accused in case victim is below 12 years? Accused are generally known to victim in cases of child abuse cases.Me : Sir ,you are right. NCRB records state that in child sexual abuse cases 94% of accused are known to victim. This may lead to non reporting or victim turning hostile due to pressure from family.Secondly, death penalty is not a deterrent. It has been proven from many reports.Thirdly , now rape and murder have same punishment so now the rapist will not leave his victim alive .(M1 : good point Dr. Shilpa)M1 : Have you heard about euthanasia? What is the recent SC judgement.Me: Euthanasia in common terms means mercy killing. It is of two types : active and passive euthanasia. Recently SC has allowed passive euthanasia in case patient is in permanent vegetative state.M1: Who decides it is time for euthanasia?Me: Sir , It consists of three layered mechanism . A mechanism for living will has been given which is accessed by the doctor. If he feels that there is need for go ahead the permission is send to a special medical board which consists of four specialists. After approval it is forwarded to district collector.M1: What is living will?Me: It is a directive by a patient that in due course of his treatment if stops responding to treatment or is in permanent vegetative state he be considered for passive euthanasia.MEMBER 2M2 : Comment on our relations with our neighbours with respect to Bangladesh , Nepal.Me: Sir , Neighbourhood first policy has been major component of our foreign policy.Good relations with Bangladesh for example recently land boundary agreement was signed very amicably. There is just one irritant in form of teesta water treaty.Nepal we have historical and cultural ties. 'BETI AND ROTI' ka rishta. A buffer state. But due to unprecedented foray of China into south asia and Nepal playing China card due to its domestic compulsions , relations have taken toll right now.( I wanted to summarize but M2 said ok shilpa fine)M2 : Chinese president XI Xingping and PM modi will be meeting recently. Where?ME: Sir there will be an informal meeting in City of Wuhan , China. Here wide array of issues will be discussed.M2 : China is saying it will be sharing data on satluj river. What is that?ME: Sir basically hydrological data. Water levels and dams to be constructed.M2: Sociolgists are better administrators. Why? (Sociology is my optional subject)ME: Sir, it is basically study of social groups , social institutions and their dynamics. And as civil servant you are basically dealing with these institutions and groups. For eg : as a sociologist one knows laws decide where society SHOULD GO but Societal norms decide where society actually GOES. It serves a great value as a civil servant.MEMBER 3M3 : Dr. Bhatti you were talking about China right now. How are we same ?How does it poses a danger how India is responding? Can we learn something from China?( it was a long question so I broke it into parts)Me: China and India are same with respect to thriving economies. China is second largest economy in terms of nominal GDP and India is 7th.Both are populous nations with huge human capital potential.Dangers : China 's unprecedented foray into South Asia. Increasing footprint in Indian ocean.Learn from China: China has emerged as workshop of world. Its manufacturing sectors contributes around 34% to its GDP where India its just 17% ( Member said good Dr.Bhatti)MEMBER 4M4 : Social media is turning a place for spreading wrong news and all ( long lecture) . How to address this?Me: Sir in the post truth era social media is turning into menance where fake news are being spread. (M4 interuppts)M4 : You used word post truth. Very interesting word. What is that?Me: Sir it is an era where facts are considered less and beliefs and emotions shape the public opinion.M4 : Very good Shilpa. Continue with your answer. How to address?Me: Sir we can address first at legal level. For eg : EU has .......( M4 interuppts.)M4: Shilpa talk at a more local level. Like you are Chandigarh DC.Me: Sir first we can use social media itself. These days every administration has official twitter , FB accounts. From this we can give correct info n allay fears.Secondly in Chandigarh during Ram Rahim case SMS were sent as precaution. We can use this platformThirdly , involving civil society to create awareness to not accept any news at face value before confirming it from standard source.M4 : Did you choose Medical field by choice ? You are no longer pursuing it?Me: Sir , Civil services was always on my mind but idea wasn't very concrete at that time. I choose medical field because of my love for science and I have always performed good in academics.Also while working as a dentist I realized that civil services gives much larger platform to bring a change plus job diversity it offers is unparallelled.CHAIRMANCHAIRMAN : Tell me where woman bureaucrats or officers in general can be of great help?Me : Sir , in police administration for example if the cutting edge officers or bureaucrats in general are woman we can make our police services more gender sensitive.Chairman : yes ok. Continue.Me: Sir I cant think of other areas right now.(Chairman smiled and said ok)CHAIRMAN : Ok Shilpa tell me one last question before we go for lunch. You have heard about tussle between delhi chief secretary and chief minister?Me: yes sir.CHAIRMAN : So now bureaucrats blame its ministers who hamper work and politician blame bureaucrats. What to do?Me: Sir the permanent executive and the elected executive has work in tandem.CHAIRMAN : Yes tell me solution?Me: Following SOP and due process of law.Secondly, Sir transperant administration. Egovernance to cut down bureaucratic red tapism and also ensuring the executive is pro active in various people centric schemes or policies.Thirdly , we can have informal meetings in form of ‘chintin shivirs' or organising sports events for breaking the ice and acting as confidence building measures.CHAIRMAN : Ok Shilpa your interview is over. So now you will go back to Chandigarh or stay back.Me: Sir I will stay back for medical and leave on 26th.Chairman : Ok. Thank you Shilpa.Me: Thank you Sir. ( I thanked other member too)Interview lasted around 25 minutes. Members were extremely cordial and I had a feeling that it went well.And I got a good score of 187 :) I was able to secure 712 rank UPSC CSE 2017 and currently Iam preparing for rank improvement :)I hope this answer conveyed what happens in UPSC interview :)
-
Attorneys, what is the worst result a client ever got in court because they absolutely refused to take your advice?
The time I had a criminal client who was arrested for exposing himself to a young girl, and being in possession of a huge cache of child pornography. He was a middle-class, nominally intelligent and articulate man who had been arrested for the first time in his life.This fellow gave a very detailed, hour-long, videotaped confession to the police before he hired me.And after he hired me, he began insisting that he hadn’t confessed at all, despite the high-definition and surround-sound quality of his taped confession, and further claimed the porn collection had been planted by a disgruntled g...
-
What is the font used in the Routledge classics series?
There isn't a chance that this is Georgia as Thant Zin Oo suggested. The terminal of 'e' in Garamond extends further and the 'a' should have a ball terminal, which is not present in the printed text shown here.I was thinking of Proforma myself considering the lack of a serif at the top terminal of 'a', but the descender of 'y' features a serif which is not present in the printed text, and the italic of Proforma is distinctly different. For one, it has an 'f' with a descender, which is not present in the printed text. This is highly unusual in italics for serif typefaces.The typeface looks very familiar to me with its straight y-descender, the serifless 'a' and the relatively wide and unusual b/d/o/p/q, but I can't place it.Update:I found the typeface. It's Joanna. Note also that there is a Joanna Nova, but that's not the typeface presented here, as Noanna Nova's italics are wider for starters. I would personally recommend using Joanna Nova rather than Joanna, but the typeface used for the Routledge classical series is Joanna in any case.The serifless terminal of 'a' already got me thinking about Eric Gill's Perpetua, but it wasn't that. The other shapes looked so familiar to me, particularly the wide and rather unusual bows of b/d. I was then reminded I had seen that exact quality in Gill Sans among others, and realized that this is a signature design aspect of Eric Gill. Hence, I found out it's Joanna. That also explains the straight descender of 'y' and the descenderless 'f' in the italic.
-
How are cracked versions of software created and why are developers not able to prevent it?
Cracked versions of software are created with the use of debuggers. (A debugger is a special type of software that lets programmers deconstruct their software into its constituent parts for the purpose of finding bugs, and thus de-bugging. Additionally debuggers can be used for reverse-engineering, or to see what is inside the software, to learn its logic. The latter method is used mostly by malware researchers to study what malware (or computer viruses) do on-the-inside. But it can be also used by an attacker to "crack" (or bypass) legal software registration, or at times, to alter normal behavior of software, for instance by injecting a malicious code into it.)For the sake of this example, I will assume that the software that is being "cracked" was compiled into a native code, and is not a .NET or a JavaScript based application. (Otherwise it will be somewhat trivial to view its source code.) The compiled native code is a bit more tricky "beast" to study. (Native means that the code executes directly by the CPU, GPU, or other hardware.)So let's assume that the goal of an attacker is to bypass the registration logic in the software so that he or she doesn't have to pay for it. (Later for lolz, he or she may also post such "crack" on some shady online forum or on a torrent site so that others can "use" it too and give him or her their appreciation.)For simplicity let's assume that the original logic that was checking for the software registration was written in C++ and was something similar to the following code snippet:In this code sample "RegistrationName" and "RegistrationCode" are special strings of text that a legitimate software user will receive after paying for the license. (The name is usually that person's actual name or their email address, and the code is some string of unique/special characters that is tied to the name.)In the logic above, the function named "isRegistrationCodeGood()" will check if "RegistrationName" and "RegistrationCode" are accepted using some proprietary method. If they are, it will return true. Otherwise false. That outcode will dictate which branch (or scope) the execution will follow.So the logic above will either show that registration failed and quit:Or, if the registration code and name matched, it will save the registration details in persistent storage (such as the File System or System Registry) using the function named "rememberRegistrationParameters()" and then display the message thanking the user for registering:A "cracker" will obviously want to achieve the second result for any registration code that he or she enters. But they have a problem. They do not have the C++ source code, part of which I showed above. (I hope not!)So the only recourse for an attacker is to disassemble the binary code (that always ships with software in the form of .exe and .dll files on Windows, and mostly as Unix executables inside the .app packages on a Mac.) An attacker will then use a debugger to study the binary code and try to locate the registration logic that I singled out above.Next you can see the flowchart for a snippet of code that I showed in C++, presented via a low-level debugger. Or, as the code will be read in the binary form after compilation:(For readability I added comments on the right with the names of functions and variables. They will not be present in the code that an attacker could see.)(To understand what is shown above an attacker will have to have good knowledge of the Assembly language instructions for the native code.)I also need to point out that having a disassembly snippet like the one above is the final result for an attacker. The main difficulty for him or her is to locate it among millions and millions of other similar lines of code. And that is their main challenge. Not many people can do it and that is why software "cracking" is a special skill.So having found the code snippet above in the software binary file a "cracker" has two choices:1) Modify (or patch) the binary.2) Reverse-engineer the "isRegistrationCodeGood()" function and copy its logic to create what is known as a "KeyGen" or "Key Generator."Let's review both:The first choice is quite straightforward. Since an attacker got this far, he or she knows the Intel x64 Instruction Set quite well. So they simply change the conditional jump from "jnz short loc_7FF645671430" at the address 00007FF645671418 (circled in red in the screenshots) to unconditional jump, or "jmp short loc_7FF645671430". This will effectively remove any failed registration code entries and anything that the user types in will be accepted as a valid registration.Also note that this modification can be achieved by changing just one byte in the binary code from 0x75 to 0xEB:But this approach comes with a "price" of modifying the original binary file. For that an attacker needs to write his own "patcher" (or a small executable that will apply the modification that I described above.) The downside of this approach for an attacker is that patching an original executable file will break its digital signature, which may alert the end-user or the vendor. Additionally the "patcher" executable made by an attacker can be easily flagged and blocked by the end-user's antivirus software, or lead criminal investigators to the identity of the attacker.The second choice is a little bit more tricky. An attacker will have to study "isRegistrationCodeGood()" function and copy it into his own small program that will effectively duplicate the logic implemented in the original software and let him generate the registration code from any name, thus giving any unscrupulous user of that software an ability to register it without making a payment.Vendors of many major software products understand the potential impact of the second method and try to prevent it by requiring what is known as "authentication." This is basically a second step after registration, where the software submits registration name to the company's web server that returns a response back to the software of whether the code was legitimate or not. This is done by Microsoft when you purchase Windows (they call it "Activate Windows") and also by signNow, and many other companies. This second step may be done behind-the-scenes on the background while the software is running, and will usually lead to cancellation of prior registration if it was obtained illegally.So now you know how software is "cracked".Let me answer why it is not possible to prevent it. It all boils down to the fact that any software code needs to be read either by CPU (in case of a binary native code) or by an interpreter or a JIT compiler (in case of JavaScript or .NET code.) This means that if there's a way to read/interpret something, no matter how complex or convoluted it is, an attacker with enough knowledge and persistence will be able to read it as well, and thus break it.There is an argument though that cloud-based software is more secure, which is true, since its (binary) code remains on the server and end-users do not have direct access to it. And even though cloud-based software is definitely the future, it has some major drawbacks that will never allow it to fully replace your conventional software. To name just a few:Not everyone has an internet connection, or is willing to upload their data online. Additionally someone’s internet connection can be very expensive or too slow to make the software run very laggy.Then there’s a question of distributed computing. For instance, Blizzard Entertainment would never make “World of Warcraft” to fully run on their servers due to immense computational resources needed to render every single scene for every player they have. Thus it is in their best interest to let each individual user’s computer to do the rendering instead.As a software developer myself, I obviously don't like when people steal software licenses. But I have to accept it and live with it. The good news is that there are not that many people who are willing to go extra mile and search for a cracked version of software. The main problem for those who do, is that by downloading a patched executable, or an attacker's KeyGen or a Patcher, they are effectively "trusting" him or her not to put anything "nasty" into it that was not "advertised on the package" (stuff like trojans, malware, or keyloggers.) So the question for those people becomes -- is it worth the cost of the software license to potentially infect your system with a nasty virus?On the other side of the equation, some developers react very negatively to any attempts to steal their software licenses. (I was there too.) They try to implement all kinds of countermeasures -- anything from tricking reverse-engineers, to adding booby traps in the code that may do something nasty if the code detects that it is being debugged, to obfuscating or scrambling the code, to enforcing all kinds of convoluted DRM schemes, to blocking users from certain countries. I personally try to stay away from all of those measures. And here's why:A) Any kind of anti-reverse-engineering tactics could be bypassed by an attacker with enough persistence. So why bother and waste my time when I can invest that time into adding something useful to my software that will make it more productive for legitimate users?B) Some code packers could create false positives with antivirus software, which is obviously not good for marketing of that software. It also creates unnecessary complexity for the developer to debug the software.C) Adding booby traps in the code can also “misfire” on your legitimate users, which will really infuriate them and can even lead to lawsuits.D) Any DRM scheme will probably catch some 100 illegal users and greatly inconvenience 10,000 legitimate ones. So why do it to your good customers?E) Our statistics show that about 75% of all illegal licenses come from China, Russia, Brazil, to name the worst offenders. (I also understand that the reason may be much lower incomes that people have in those countries.) The main issue for us though was the fact that if we enforce our DRM or add some strong registration authentication, many people that wanted to bypass our registration would simply use a stolen credit card number. And we had no control over it. Our system will use it to send them a legitimate license only to have the payment bounce in weeks time. As a result we would lose the money that were paid for the license, plus the credit card company will impose an additional chargeback fee to our account, which may range from $0.25 to $20 per bad purchase on top of the license cost.F) As was pointed out in the comments, some companies may actually benefit from allowing pirated copies of their software. Microsoft for instance gets a lot of free publicity from people using their Windows OS, the same goes for signNow with their Photoshop. That is a good point that I agree with.So my philosophy is now this -- if someone wants to go extra mile and steal our software, go for it! They went this far to do it anyway, so they probably have a good reason. On the positive side there are so many other customers that appreciate the work that goes into creating software that greatly outnumber those that don’t.PS. Thank you for all your feedback! It makes me feel good that the knowledge I shared is useful to others.
-
What do pro-choicers think of third-trimester abortions?
First, the child has a “head and limbs and everything” much, much earlier than the third trimester.So if the criteria is that a fetus with “a head and limbs and everything” should not be aborted, the period of time when abortion is okay would have to be before 8 or 9 weeks or even earlier, depending on your perception of what constitutes a “head and limbs”. The little buds and the little webbed looking hands are seen by 8 weeks, along with the large (seemingly) misshapen head that will envelope the amazing human brain.I personally believe that the fetus is not conscious until around the 24th week of pregnancy. (I came up with this general time frame from reading about neurology, consciousness, and fetal development; a complex topic that I won’t detail here.) I don’t believe the fetus feels pain when aborted before about the 22nd week. Although it is heart-wrenching to watch images of the fetus (reflexively) attempting to escape abortionist tools. They jerk and pull away, as all living things seek to preserve their lives.However, as I said elsewhere, that to me being unconscious does not mean a living being does not have rights. I recently had surgery and was unconscious for the procedure. I could have been terminated and not felt it or known about it, but that wouldn’t have made it morally right.Very few abortions are done in the third trimester. Few doctors will do them. When they do occur it is often because the fetus is so seriously deformed and would not survive the birth process anyway. (But since your question is about having a head and limbs, we needn’t stick to the last trimester in our discussion.)Abortion is not legal throughout all three trimesters in most states. Many states have limits of between 20 to 24 weeks, some even earlier. But even at 12 weeks, yes, there is a very human-looking being with a little head, arms and legs and visible, although still ambiguous, genitals.I don’t know what “pro-choice” people think about very late abortions. Some may have an arbitrary timeline in their own mind as towhen the baby is too human to deprive of its life, and others follow the “gospel of choice”. The gospel of choice is that any and all rights an unborn person has are null and void because the rights of the mother trump them. Once the infant is born and takes a breath, then and only then can humanity be ascribed to them. Here is an interesting video in which a (former) fetus speaks of surviving an abortion attempt:I must say, I am suspicious of your claim to be pro-choice. Forgive me if I am incorrect in my suspicions. Frequently, posters on this forum will pose as pro-choice and ask innocent questions meant to provoke the discussion on Quora. It is futile to try to dissuade most pro-choicers with these ethics questions.Of interest, there are many former pro-choice warriors who have struggled with the issue and have jumped the fence. Notable is Dr. Bernard Nathanson, the abortionist who may have done more than anyone else to make abortion legal as one of the key figures in the work of the National Association for the Repeal of Abortion Laws. (NARAL) . His turnaround was so radical that he went from an atheist to a Catholic and spent his remaining years fighting abortion. I have not been able to find online recently his breathless deathbed plea for unborn life, but this obituary provides his perspective. B. N. Nathanson, 84, Dies; Changed Sides on AbortionOther well-known figures include the “Roe” of “Roe versus Wade”’ Norma McCorvey, who changed her mind and spent decades as a prolife activist Norma McCorvey on becoming pro-life (1998) - CNN Videoand Abby Johnson, the former director of a Planned Parenthood. AbortionWorkerOf course, these mind-changes have no effect on discussion with true-believing pro-choice people; such people are seen only as turncoats. If the “gospel of choice” community responds at all, it is usually in the form of attack or attempts to discredit those who have jumped the fence. For those who have a grain of doubt in their position, who are troubled by the fetal attempt to squirm away from a sharp tool, then perhaps the reasons these pro-choice icons became turncoats may be interesting. But they will not interest those who have no doubts.I will provide here links to two videos showing fetal life. One is a miscarriage, and the other is labelled as an abortion. I don’t believe the moving fetus is an abortion, despite the claims of the person who posted it. The medical personnel are speaking a language I don’t understand, but you can hear tones of sadness as they discuss the little fetus, and further the fetus is not damaged in anyway, so likely this is footage of a natural miscarriage. This is graphic, but not gory, it is merely a fetus moving a little bit as it dies because it cannot live outside the womb. This fetus is too young to try to breathe or have any pain or consciousness. I am estimating that it was born early in the second trimester. If you are sensitive, it may be too alarming to watch. I am sorry about the banner “Abortion is Murder” and so on. but this is the only video that shows the miscarriage of a fetus of this age that I can find. I don’t think all the “murder” talk and the accusations help the discussion. Anyway, this is not a third trimester baby by any stretch of the imagination. It is likely 14 to 16 weeks and yes, there is a head and legs.I want to also add that I don’t think that reversing the Supreme Court decision regarding the right of women to terminate their pregnancies will help anything at this point.I am more interested in being free to talk about human life with those who have doubts and to explore addressing the cultural effects of the legalization of abortion. For instance, there are movements such as Feminists for Life and other secular prolife movements who offer a different perspective from the religious dissenters and the “gospel of choice” movement. secularprolifeYes, the Supreme Court has spoken. But no law has been enacted that prevents thoughtful people from re-examining and conversing about the disquieting questions that the theme of abortion gives rise to.
-
How do I file income tax return in India?
Greeting Friends !!!If you are going to file it yourself, then following is the procedure:-Before you start the process, keep your bank statements, Form 16 issued by your employer and a copy of last year's return at hand. Next, log on to http://incometaxindiaefiling.gov...Follow these steps:Step 1: Register yourself on the website. Your Permanent Account Number (PAN) will be your user ID.Step 2: View your tax credit statement — Form 26AS — for the financial year 2015–16 . The statement will reflect the taxes deducted by your employer actually deposited with the I-T department. The TDS as per your Form 16 must tally with the figures in Form 26AS. If you file the return despite discrepancies, if any, you could get a notice from the I-T department later.Step 3: Under the 'Download' menu, click on Income Tax Return Forms and choose AY 2016–17 (for financial year 2015–16 ). Download the Income Tax Return (ITR) form applicable to you.Which Income Tax Return Form Require to file or applicable F.Y. 2015–16 by Hetal M Kukadiya on Tax Knowledge Bank - IndiaStep 4: Open the downloaded Return Preparation Software (excel or Java utility) and complete the form by entering all the details , using your all documentsStep 5: Ascertain the tax payable by clicking the 'Calculate Tax' tab. Pay tax (if applicable) and enter the challan details in the tax return.Step 6: Confirm all the information in the worksheet by clicking the 'Validate' tab.Step 7: Proceed to generate an XML file and save it on your computer.Step 8: Go to 'Upload Return' on the portal's left panel and upload the saved XML file after selecting 'AY 2016-2017 ' and the relevant form. You will be asked whether you wish to digitally sign the file. If you have obtained a DS (digital signature), select Yes. Or, choose 'No'.Step 9: Once the website flashes the message about successful e-filing on your screen, you can consider the process to be complete. The acknowledgment form — ITR—Verification (ITR-V ) will be generated and you can download it.Step 10: you can Verify online with EVC Pin or Take a printout of the form ITR-V , sign it preferably in blue ink, and send it only by ordinary or Speed post to the Income-Tax Department-CPC , Post Bag No-1 , Electronic City Post Office, Bangalore - 560 100, Karnataka, within 120 days of filing your return online.Its Advisable to go with CA help for filling Tax return. There are lots of amendment come in every year, to file accurate return and Tax planning benefit etc so Prefer to go with expert like CA, Tax Preparer etc…Be Peaceful !!!
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
What is a live electronic signature?
How to sign a pdf with drawing pad?
Get more for eSignature Presentation Myself
- eSign South Dakota Legal Letter Of Intent Free
- eSign Alaska Plumbing Memorandum Of Understanding Safe
- eSign Kansas Orthodontists Contract Online
- eSign Utah Legal Last Will And Testament Secure
- Help Me With eSign California Plumbing Business Associate Agreement
- eSign California Plumbing POA Mobile
- eSign Kentucky Orthodontists Living Will Mobile
- eSign Florida Plumbing Business Plan Template Now
Find out other eSignature Presentation Myself
- Michigan patient care record protocol state of michigan form
- Application for special organization license plate form
- Application for special organization license plates form
- Lobby late filing fee waiver request form lobby lff waiver form
- Request for a state complaint investigation special education state complaint michigan form
- Fire department standard operating procedures form
- Free montana bill of sale templates pdf ampamp docxformswift
- Request for waiver of faculty qualifications form
- Free nebraska general bill of sale form pdfword
- Comprehensive planning forms clark county nv
- See submittal requirements form for more information
- Gre 54 420 form
- Iro contact update formpdf
- Premium tax summary form ins 4001 ohio department of
- Requirements are referred to as the individuals with disabilities education act idea form
- Complaint form counselor social worker and marriage ampamp family cswmft ohio
- Complaint orm sos tn gov filess3amazonawscom form
- Documents and forms welcome to the city of houston
- 2018 water district consent application form houston
- Free wyoming firearm bill of sale form wordpdfeforms