Remove Electronic signature Document Safe
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Discover the easiest way to Remove Electronic signature Document Safe with our powerful tools that go beyond eSignature. Sign documents and collect data, signatures, and payments from other parties from a single solution.
Robust integration and API capabilities
Enable the airSlate SignNow API and supercharge your workspace systems with eSignature tools. Streamline data routing and record updates with out-of-the-box integrations.
Advanced security and compliance
Set up your eSignature workflows while staying compliant with major eSignature, data protection, and eCommerce laws. Use airSlate SignNow to make every interaction with a document secure and compliant.
Various collaboration tools
Make communication and interaction within your team more transparent and effective. Accomplish more with minimal efforts on your side and add value to the business.
Enjoyable and stress-free signing experience
Delight your partners and employees with a straightforward way of signing documents. Make document approval flexible and precise.
Extensive support
Explore a range of video tutorials and guides on how to Remove Electronic signature Document Safe. Get all the help you need from our dedicated support team.
Keep your eSignature workflows on track
Make the signing process more streamlined and uniform
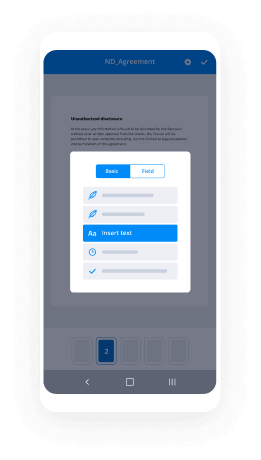
Take control of every aspect of the document execution process. eSign, send out for signature, manage, route, and save your documents in a single secure solution.
Add and collect signatures from anywhere
Let your customers and your team stay connected even when offline. Access airSlate SignNow to Remove Electronic signature Document Safe from any platform or device: your laptop, mobile phone, or tablet.
Ensure error-free results with reusable templates
Templatize frequently used documents to save time and reduce the risk of common errors when sending out copies for signing.
Stay compliant and secure when eSigning
Use airSlate SignNow to Remove Electronic signature Document Safe and ensure the integrity and security of your data at every step of the document execution cycle.
Enjoy the ease of setup and onboarding process
Have your eSignature workflow up and running in minutes. Take advantage of numerous detailed guides and tutorials, or contact our dedicated support team to make the most out of the airSlate SignNow functionality.
Benefit from integrations and API for maximum efficiency
Integrate with a rich selection of productivity and data storage tools. Create a more encrypted and seamless signing experience with the airSlate SignNow API.
Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
Our user reviews speak for themselves






Is SignNow secure?
When exploring digital signature solutions, numerous users inquire, 'Is SignNow secure?' With airSlate SignNow, you can be confident that your documents are managed safely and effectively. This platform presents a variety of advantages that simplify the signing procedure while guaranteeing security and adherence to regulations.
Is SignNow safe for usage?
- Open your favorite browser and go to the airSlate SignNow site.
- Create a complimentary trial account or sign into your current account.
- Select the document you want to sign or send for signatures.
- If you intend to use this document again, save it as a template for future reference.
- Access your file and modify it: this includes adding fillable fields or inserting essential information.
- Sign the document and specify signature fields for the recipients.
- Click 'Continue' to set up the eSignature invitation and send it.
In summary, airSlate SignNow is an outstanding option for organizations seeking a dependable and effective document signing solution. With its intuitive interface and robust features, it truly enables businesses to manage their signing requirements efficiently.
Prepared to improve your document workflow? Begin your free trial with airSlate SignNow today and discover the benefits for yourself!
How it works
Upload & open your document in the editor
Fill it out and eSign it in minutes
Save the signed document or share it with others
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
Is SignNow safe for sending sensitive documents?
Yes, SignNow is safe for sending sensitive documents. The platform uses advanced encryption methods to protect your data during transmission and storage, ensuring that your information remains confidential and secure. With robust security measures in place, businesses can confidently utilize SignNow for their eSignature needs.
-
What security features does SignNow offer?
SignNow offers several security features to ensure that your documents are protected. These include two-factor authentication, encrypted data storage, and compliance with industry standards such as GDPR and HIPAA. This commitment to security reinforces that SignNow is safe for businesses of all sizes.
-
How does SignNow ensure compliance with legal standards?
SignNow is safe and compliant with various legal standards, including the ESIGN Act and UETA, which govern the use of electronic signatures. The platform maintains rigorous security protocols and provides an audit trail for every document signed, ensuring that all transactions are legally binding and compliant.
-
Is my payment information safe with SignNow?
Absolutely! SignNow is safe for processing payment information as it employs secure payment gateways and encryption technologies. Your financial data is protected, allowing you to focus on utilizing the platform without worrying about security bsignNowes.
-
Can I integrate SignNow with other applications?
Yes, SignNow offers seamless integrations with various applications, including Google Drive, Salesforce, and Microsoft Office. This flexibility enhances your workflow and demonstrates that SignNow is safe and effective for businesses looking to streamline their document signing processes.
-
What are the benefits of using SignNow for eSignatures?
Using SignNow for eSignatures offers numerous benefits, including a user-friendly interface, cost-effective pricing, and robust security features. These qualities contribute to making SignNow a safe choice for businesses aiming to improve their document signing efficiency while maintaining compliance and security.
-
How does SignNow protect my data?
SignNow protects your data through multiple layers of security, including encryption, secure servers, and regular security audits. This comprehensive approach ensures that your information remains safe from unauthorized access, reinforcing the answer to the question: is SignNow safe?
-
Is digital signature useful for an individual in India?
It goes without saying that, we spend a good amount of time signing, scanning and printing documents.Digital signatures allow you to get documents signed quickly. As per the IT Act, two types of signatures have the same legal status as handwritten signatures in India. These primarily include:(i) Digital Signatures: In this case, the signer is issued a long-term (1 to 2 year) certificate based digital ID stored on a USB token that can be used along with a personal PIN to sign a document.Note: Previously, the signer was issued a long-term (1 to 2 year) certificate based digital ID stored on a USB token that could be used along with a personal PIN to sign a document digitally. Now with Aadhaar, that complicated procedure isn’t required anymore. You can simply use signNow’s Aadhaar eSign to create a digital signature on the fly using your Aadhaar ID(ii) Electronic signatures: These electronic signatures combine Aadhaar identity number with an electronic Know-Your-Customer (eKYC) method (which includes sending an One-Time-Passcode to the mobile number linked to the Aadhaar card for verification)Given that all Indians now have an Aadhaar card with a unique ID, the easiest way to go about signing a contracts, invoices, or quote online - signNow, India’s first Aadhaar eSign solution that offers a complete fill-and-sign functionality with business workflows. Thus allowing users to finish their documents in one go.
-
What is the best free PDF reader for large documents?
[1] PDF format is popularly known as print document format. This creates a virtual printer within operating system to print the document. For offline scanning of document, the PDF format is popular. The importance attached with these program is that you need to have PDFsoftware installed to run these files. If someone sends you PDF file and your computer do not have such software installed then that file is not to be read from there.There are so many PDF softwires available and this article aims to find out the mostly free software or freeware to help readers to choose from variety of options. More and more operating systems are providing built-in facilities for such products. Now-a-days everything comes with PDF formats beginning from circulars, bank statement, insurance statement, tax statement and e-books.That is why there immense important to have the free PDF software installed on computer but the thousand question is which one is to choose from the variety of resources available.Sumatra PDF:Sumatra PDF is available for download to Windows since the times of Windows XP. This program has very low foot print, light on system resources and fast. It is going to perform simple task as well as it is going to perform complex task depending upon you choose from PDFfiles. It is available with installed version as well as standalone portable version in which it does not write to registry.It is available in 64 bit version on Windows. It is available for Windows XP, Vista, 7, 8, 8.1 and 10. It is available for Windows operating system only.signNow Reader DC:It is from signNow and signNow is available for free for users. While installing this software do check for installation of MCAfee security and safe connect.it is a big download of nearing to 120 MB. Yours antivirus software might stop this installation so allow to install it. This software for high=end computing processes.Many features are included with it and for some features you might need it and if you want to have these features then it is better to choose this software. It has mobile version of android and apple operating system. With it you are going to synchronize documents with clouds and yours signature too and everything is going to stay with cloud to access from each and every device.When you first download signNow on Windows, a download manager first downloads and it is small in size and then by opening that download manager signNow software is installed and this is nearer to 120 MB.PDF-Xchange Editor:PDF-Xchange Editor is a smart PDF tools and most functions are free except some complex ones. It is a PDF reader, pdf editor and pdf tools. It can print PDFs, fill the forms created with signNow and can extract images from PDF files. There are some advanced features included in this free version but most of these are not free one is that watermarking of PDFsoftware which is not free.Foxit Reader:Foxit Reader is fast, simple and is there for years. It is available for Windows, Apple and android versions. It can fill forms and save data. Can include and validate electronic signatures. During installation user need to be cautioned not to install so many verities of other software. In order to keep the size of download minimal, the user manual is available for separate download.It is faster than PDF-Xchange Editor. If you are not interested in OCR facilities then Foxit reader is best suited for yours work. Multiple PDF documents when opened all these are opened in tab format and shifting from one tab to the other is easier. From time to time it introduces some new features in order to provide dynamic software development.It allows adding up of multimedia files easier. Collaboration with social media accounts becomes easier with Fixit Reader because of the ease to synchronize with Twitter, Facebook, Evernote and SharePoint. One caution is that Foxit Reader comes bundled with so many other software and toolbar and it is important to not to allow installations of such software during its installation.MuPDF Reader:It is very lightweight PDF Reader. On its first launch it will ask you about to choose from files instead of showing its interface and when the PDF is opened then it shows the exact documents and no toolbar and other interfaces are present. In order to see the interface of MuPDF reader you are going to click on the top left of the visible windows to find it. It provides a cleaner interface and superior look for PDF files.Google Chrome PDF viewer:While browsing for internet whenever you see any PDF and click on it and it will slowly open in another tab of Chrome and you can read it from there or download by clicking the downloadsymbol available there. This setting can be turned and changed out there easily, go to settings of chrome and then advanced and then content settings and then pdf documents, Scroll down and click on PDF documents and from there switch on ‘Download PDF files instead of opening automatically opening them in Chrome’ and this will download PDF files from net to computer.If you want to read PDF files that are stored inside computer, then right click on that files and then open with chrome and your chrome reader will automatically, open pdf files and for this you will not have to install pdf viewers. Similarly, with android if you install Google Drive then you will not need any other third-party PDF apps as Google Drive act as PDF viewer and make it default while opening the first PDF and that is going to make it default.TinyPDF:TinyPDF as the name suggests has very small foot print of PDF reader and it has no string attached. It is only 586k as it is less than one MB. It does not contain no malware, adware, watermarks and no pop Global Home: UPS is completely free. JPEG compression is supported. No ghost script and third-party software included with the installer version. The downside is that it is partially supported on 64-bit computer. Automatic font management is there.There are so many alternatives to use for PDF viewer and if your computer is 64 bit then you can download the 64 bit version of Sumatra PDF and if you want to insert electronic signature then opt for Foxit PDF reader and if you want to have the old and classic PDF reader which is heavier in file composition and not for low end computing purposes then go for signNow and lastly if you do not want to install PDF readers at all then it is better to open it with Google Chrome built in PDF viewer.So, there are many large numbers of option to choose from and if you want to have some complex PDF functions besides the presence of PDF reader you need pdf tools and others then it is best to have PDF-Xchange viewer and so many other option listed here you can choose it from. There are some other alternatives are available which are there to search ad find in internet.This entry was posted in Android Apps on Google Play, Apple Inc., Computer Information Technology, Google, Google Chrome, Information Technology, Internet, Windows 10, Windows 8, Windows XP and tagged signNow, Apple, doPDF, FOXIT READER, free PDF converter, google chrome, image to pdf converter, PDF Password Remover, pdf printer, pdf-xchange, Sumatra PDF A PDF Viewer for Windows, WINDOWS, Windows 8, WINDOWS VISTA, WINDOWS XP, Windows XP SP3 onFootnotes[1] Best Free PDF Writer and Reader
-
What are the laws - Data Protection, Data Transmission and Export and Data Encryption in India to operate a technology platform
The Information Technology Act, 2000 came into force on 17.10.2000 vide G.S.R No. 788(E) dated 17.10.2000 and for the first time, a legal definition of “Computer”, “Data”, “electronic record”, “Information” et al were provided. The said Act gave a legal recognition to the electronic records and digital signatures and in Chapter IX thereof provided for penalty and adjudication. Section 43 of the Act interalia provided that in case of unauthorised access, download or copying or damage to data etc, the person responsible shall be liable to pay damages by way of compensation not exceeding one crore rupees to the person affected.Apart from civil liability provided under Section 43, Chapter XI (Sections 63 to 78) of the Act of 2000 provided for criminal liability in cases of Tampering, Hacking, publishing or transmitting obscene material, misrepresentation etc. Apart from the same, Section 72 of the Act provided for penalty in case of bsignNow of confidentiality and privacy and laid that in case any person who has secured access to any electronic record, Data or information, discloses the same to any other person without obtaining the consent of the person concerned, he shall be punished with imprisonment upto two years or with fine upto Rupees one lakh or with both.However, the provisions of the Information Technology Act, 2000 were not adequate and the need for more stringent data protection measures were felt, the Information Technology (Amendment) Act, 2008 was enacted which came into force on 27.10.2009. The said Amendment Act brought in the concepts like cyber security in the statute book and widened the scope of digital signatures by replacing the words “electronic signature”. The amendment act also provided for secure electronic signatures and enjoined the central government to prescribe security procedures and practices for securing electronic records and signatures (Sections 15-16) The amendment Act also removed the cap of Rupees One Crore as earlier provided under Section 43 for damage to computer and computer systems and for unauthorised downloading/ copying of data. The said Amendment Act also introduced Section 43A which provides for compensation to be paid in case a body corporate fails to protect the data. Section 46 of the Act prescribes that the person affected has to approach the adjudicating officer appointed under Section 46 of the Act in case the claim for injury or damage does not exceed Rupees Five crores and the civil court in case, the claim exceeds Rupees Five crores. The amendment act also brought/ introduced several new provisions which provide for offenses such as identity theft, receiving stolen computer resource/ device, cheating, violation of privacy, cyber terrorism, pornography (Section 66A-F & 67A-C). The amendment act also brought in provisions directing intermediaries to protect the data/information and penalty has been prescribed for disclosure of information of information in bsignNow of lawful contract (Section 72A)With the enactment of the Amendment Act of 2008, India for the first time got statutory provisions dealing with data protection. However, as the ingredients of “sensitive personal data and information” as well as the “reasonable security practices and procedures” were yet to be prescribed by the Central Government, the Ministry of Communications and Information Technology vide Notification No. GSR 313 (E) dated 11th April 2011 made the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information ) Rules, 2011 (the said rules). Rule 3 of the said rules defines personal sensitive data or information and provides that the same may include information relating to password, financial information such as bank account or credit card details, health condition, medical records etc. Rule 4 enjoins every body corporate which receives or deals with information to provide a privacy policy. Rule 5 prescribes that every body corporate shall obtain consent in writing from the provider of the sensitive information regarding purpose of usage before collection of such information and such body corporate will not collect such information unless it is collected for a lawful purpose connected with the function or activity of such body corporate and collection of such information or data is necessary and once such data is collected, it shall not be retained for a period longer than what is required. Rule 6 provides that disclosure of the information to any third party shall require prior permission from the provider unless such disclosure has been agreed to in the contract between the body corporate and the provider or where the disclosure is necessary for compliance of a legal obligation. The Body corporate has been barred to publish sensitive information and the third parties receiving such information have been barred to disclose it further. Rule 7 lays down that the body corporate may transfer such information to any other body corporate or person in India or outside, that ensure the same level of data protection and such transfer will be allowed only if it is necessary for performance of lawful contract between the body corporate and provider of information or where the provider has consented for data transfer. Rule 8 of the said rules further provide reasonable security practises and procedures and lays down that international standard IS/ISO/IEC 27001 on “Information Technology- Security Techniques- Information Security Management System- requirements “ would be one such standard.The Ministry of Communication and Information Technology further issued a press note dated 24th August 2011 and clarified that the said rules are applicable to the body corporate or any person located within India. The press note further provides that any body corporate providing services relating to collection or handling of sensitive personal data or information under contractual obligation with any other legal entity located within India or outside is not subject to requirements of Rules 5 &6 as mentioned hereinabove. A body corporate providing services to the provider of information under a contractual obligation directly with them however has to comply with Rules 5 &6. The said press note also clarifies that privacy policy mentioned in Rule 4 relates to the body corporate and is not with respect to any particular obligation under the contract. The press note at the end provides that the consent mentioned in Rule 5 includes consent given by any mode of electronic communication.Data Protection relates to issues relating to the collection, storage, accuracy and use of data provided by net users in the use of the World Wide Web. Visitors to any website want their privacy rights to be respected when they engage in e-Commerce. It is part of the confidence-creating role that successful e-Commerce businesses have to convey to the consumer. If industry doesn't make sure it's guarding the privacy of the data it collects, it will be the responsibility of the government and it's their obligation to enact legislation.Any transaction between two or more parties involves an exchange of essential information between the parties. Technological developments have enabled transactions by electronic means. Any such information/data collected by the parties should be used only for the specific purposes for which they were collected. The need arose, to create rights for those who have their data stored and create responsibilities for those who collect, store and process such data. The law relating to the creation of such rights and responsibilities may be referred to as ‘data protection’ law.The world’s first computer specific statute was enacted in the form of a Data Protection Act, in the German state of Hesse, in 1970.The misuse of records under the Nazi regime had raised concerns among the public about the use of computers to store and process large amounts of personal data.The Data Protection Act sought to heal such memories of misuse of information. A different rationale for the introduction of data protection legislation can be seen in the case of Sweden which introduced the first national statute in 1973.Here, data protection was seen as fitting naturally into a two hundred year old system of freedom of information with the concept of subject access (such a right allows an individual to find out what information is held about him) being identified as one of the most important aspects of the legislation.In 1995, the European Union adopted its Directive (95/46/EC) of the European Parliament and of the Council of 24 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data (hereinafter, the Directive), establishing a detailed privacy regulatory structure. The Directive is specific on the requirements for the transfer of data. It sets down the principles regarding the transfer of data to third countries and states that personal data of EU nationals cannot be sent to countries that do not meet the EU “adequacy” standards with respect to privacy.In order to meet the EU “adequacy” standards, US developed a ‘Safe Harbour’ framework, according to which the US Department of Commerce would maintain a list of US companies that have self-certified to the safe harbor framework. An EU organization can ensure that it is sending information to a U.S. organization participating in the safe harbor by viewing the public list of safe harbor organizations posted on the official website.Data protection has emerged as an important reaction to the development of information technology. In India data protection is covered under the Information Technology Act, 2000 (hereinafter, the Act). The Act defines ‘data’ as, “‘data’ means a representation of information, knowledge, facts, concepts or instructions which are being prepared or have been prepared in a formalized manner, and is intended to be processed, is being processed or has been processed in a computer system or computer network, and may be in any form (including computer printouts magnetic or optical storage media, punched cards, punched tapes) or stored internally in the memory of the computer”. Protection of such data and privacy are covered under specific provisions in the Act. In the recent past, the need for data protection laws has been felt to cater to various needs. The following analyses the position of data protection law with respect to some of the needs.Data Protection Law In Respect of Information Technology Enabled Services (ITES)India started liberalizing its economy in the 1990’s and since then a huge upsurge in the IT business process outsourcing may be witnessed. Financial, educational, legal, marketing, healthcare, telecommunication, banking etc are only some of the services being outsourced into India. This upsurge of outsourcing of ITES into India in the recent past may be attributed to the large English-speaking unemployed populace, cheap labour, enterprising and hardworking nature of the people etc. Statistics have shown that the outsourcing industry is one of the biggest sources of employment. In a span of four years, the number of people working in call centers in the country supporting international industries has risen from 42,000 to 3,50,000. Exports were worth $5.2 billion in 2004-2005 and are expected to grow over 40% this fiscal year. US is currently the biggest investor in Indian ITES, taking advantage of cheap labour costs. Statistics indicate that software engineers with two-years experience in India are being paid about 1/5th of an equivalent US employee.Concerns about adequacy of lawBPO FraudsWith globalization and increasing BPO industry in India, protection of data warrants legislation. There are reasons for this. Every individual consumer of the BPO Industry would expect different levels of privacy from the employees who handle personal data. But there have been situations in the recent past where employees or systems have given away the personal information of customers to third parties without prior consent. So other countries providing BPO business to India expect the Indian government and BPO organizations to take measures for data protection. Countries with data protection law have guidelines that call for data protection law in the country with whom they are transacting.For instance, in, the European Union countries according to the latest guidelines, they will cease to part with data, which are considered the subject matter of protection to any third country unless such other country has a similar law on data protection. One of the essential features of any data protection law would be to prevent the flow of data to non-complying countries and such a provision when implemented may result in a loss of "Data Processing" business to some of the Indian companies.In the recent past, concerns have been raised both within the country as well as by customers abroad regarding the adequacy of data protection and privacy laws in the country. A few incidents have questioned the Indian data protection and privacy standards and have left the outsourcing industry embarrassed. In June 2005, ‘The Sun’ newspaper claimed that one of its journalists bought personal details including passwords, addresses and passport data from a Delhi IT worker for £4.25 each. Earlier BPO frauds in India include New York-based Citibank accounts being looted from a BPO in Pune and a call-center employee in Bangalore peddling credit card information to fraudsters who stole US$398,000 from British bank accounts.UK's Channel 4 TV station ran broadcast footage of a sting operation exposing middlemen hawking the financial data of 200,000 UK citizens. The documentary has prompted Britain's Information Commissioner's Office to examine the security of personal financial data at Indian call centers.In the absence of data protection laws, the kind of work that would be outsourced to India in the future would be limited. The effect of this can be very well seen in the health-care BPO business, which is estimated to be worth close to $45 billion. Lack of data protection laws have left Indian BPO outfits still stagnating in the lower end of the value chain, doing work like billing, insurance claims processing and of course transcription. Besides healthcare, players in the retail financial sector are also affected. Financial offshoring from banks is limited because of statutory compliance requirements and data privacy laws protecting sensitive financial information in accounts. In the Human Resource (HR) domain, there are many restrictions on sharing of personal information. In the medical domain, patient history needs to be protected. In credit card transactions, identity theft could be an issue and needs to be protected. Companies in the banking, financial services and insurance (BFSI) sector and healthcare have excluded applications/processes which use sensitive information from their portfolio for offshoring till they are comfortable about the data protection laws prevalent in the supplier country.Since there is lack of data protection laws in India, Indian BPO outfits are trying to deal with the issue by attempting to adhere to major US and European regulations. MNCs have to comply with foreign Regulations so that they don’t lose on their international partners. There are problems involved in this. Efforts by individual companies may not count for much if companies rule out India as a BPO destination in the first place in the absence of data protection law.Today, the largest portion of BPO work coming to India is low-end call centre and data processing work. If India has to exploit the full potential of the outsourcing opportunity, then we have to move up the value chain. Outsourced work in Intellectual Property Rights (IPR)-intensive areas such as clinical research, engineering design and legal research is the way ahead for Indian BPO companies. The move up the value chain cannot happen without stringent laws. Further, weak laws would act as deterrents for FDI, global business and the establishment of research and development parks in the pharmaceutical industry.Looking to the above scenario, we can say that for India to achieve heights in BPO industry stringent laws for data protection and intellectual property rights have to be made. . Thus, a law on data protection on India must address the following Constitutional issues on a "priority basis" before any statutory enactment procedure is set into motion:(1) Privacy rights of interested persons in real space and cyber space.(2) Mandates of freedom of information U/A 19 (1) (a).(3) Mandates of right to know of people at large U/A 21.Once the data protection rules are enforced in India, companies outsourcing to India are unlikely to dismantle the systems they have in place straightaway, and move data more freely to India. Hence ,the need for data protection laws would win over the confidence of international business partners; protect abuse of information; protection of privacy and personal rights of individuals would be ensured; there would be more FDI inflows, global business and the establishment of research and development parks in the pharmaceutical industry & impetus to the sector of e-Commerce at national and international levels would be provided.Data protection law in India (Present status):-Data Protection law in India is included in the Act under specific provisions. Both civil and criminal liabilities are imposed for violation of data protection.(1) Section 43 deals with penalties for damage to computer, computer system etc.(2) Section 65 deals with tampering with computer source documents.(3) Section 66 deals with hacking with computer system.(4) Section 72 deals with penalty for bsignNow of confidentiality and privacy. Call centers can be included in the definition of ‘intermediary’and a ‘network service provider’ and can be penalized under this section.These developments have put the Indian government under pressure to enact more stringent data protection laws in the country in order to protect the lucrative Indian outsourcing industry. In order to use IT as a tool for socio-economic development, employment generation and to consolidate India’s position as a major player in the IT sector,amendments to the IT Act, 2000 have been approved by the cabinet and are due to be tabled in the winter session of the Parliament.Proposed amendments:-The amendments relate to the following[22]:(i) Proposal at Sec. 43 (2) related to handling of sensitive personal data or information with reasonable security practices and procedures.(ii) Gradation of severity of computer related offences under Section 66, committed dishonestly or fraudulently and punishment thereof.(iii) Proposed additional Section 72 (2) for bsignNow of confidentiality with intent to cause injury to a subscriber.It is hoped that these amendments will strengthen the law to suffice the need.Data Protection Laws In Order To Invite ‘Data Controllers’.There has been a strong opinion that if India strengthens its data protection law, it can attract multi-national corporations to India. India can be home to such corporations than a mere supplier of services.In fact, there is an argument that the EU’s data protection law is sufficient to protect the privacy of its people and thus lack of strong protection under Indian law is not a hindrance to the outsourcing industry. To enumerate, consider a company established in EU (called the ‘data controller’) and the supplier of call center services (‘data processor’) in India. If the data processor makes any mistake in the processing of personal data or there are instances of data theft, then the data controller in the EU can be made liable for the consequences. The Indian data processor is not in control of personal data and can only process data under the instructions of the data controller. Thus if a person in EU wants to exercise rights of access and retrieve personal data, the data controller has to retrieve it from the data processor, irrespective of where the data processor is located. Thus a strong data protection law is needed not only to reinforce the image of the Indian outsourcing industry but also to invite multi-national corporations to establish their corporate offices here.Data Protection And TelemarketingIndia is faced with a new phenomenon-telemarketing. This is facilitated, to a large extent, by the widespread use of mobile telephones. Telemarketing executives, now said to be available for as low as US $70 per month, process information about individuals for direct marketing. This interrupts the peace of an individual and conduct of work. There is a violation of privacy caused by such calls who, on behalf of banks, mobile phone companies, financial institutions etc. offer various schemes. The right to privacy has been read into Article 21, Constitution of India, but this has not afforded enough protection. A PIL against several banks and mobile phone service providers is pending before the Supreme Court alleging inter alia that the right to privacy has been infringed.The EC Directive confers certain rights on the people and this includes the right to prevent processing for direct marketing. Thus, a data controller is required not to process information about individuals for direct marketing if an individual asks them not to. So individuals have the right to stop unwanted marketing offers. It would be highly beneficial that data protection law in India also includes such a right to prevent unsolicited marketing offers and protect the privacy of the people.Data Protection With Regard To Governance And PeopleThe Preamble to the Act specifies that, the IT Act 2000, inter alia, will facilitate electronic filing of documents with the Government agencies. It seeks to promote efficient delivery of Government services by means of reliable electronic records. Stringent data protection laws will thus help the Government to protect the interests of its people.Data protection law is necessary to provide protection to the privacy rights of people and to hold cyber criminals responsible for their wrongful acts. Data protection law is not about keeping personal information secret. It is about creating a trusted framework for collection, exchange and use of personal data in commercial and governmental contexts. It is to permit and facilitate the commercial and governmental use of personal data.The Data Security Council of India (DSCI) and Department of Information Technology(DIT) must also rejuvenate its efforts in this regard on the similar lines. However, the best solution can come from good legislative provisions along with suitable public and employee awareness. It is high time that we must pay attention to Data Security in India. Cyber Security in India is missing and the same requires rejuvenation. When even PMO's cyber security is compromised for many months we must at least now wake up. Data bsignNowes and cyber crimes in India cannot be reduced until we make strong cyber laws. We cannot do so by mere declaring a cat as a tiger. Cyber law of India must also be supported by sound cyber security and effective cyber forensics.Indian companies in the IT and BPO sectors handle and have access to all kinds of sensitive and personal data of individuals across the world, including their credit card details, financial information and even their medical history. These Companies store confidential data and information in electronic form and this could be vulnerable in the hands of their employees. It is often misused by unsurplous elements among them. There have been instances of security bsignNowes and data leakages in high profile Indian companies. The recent incidents of data thefts in the BPO industry have raised concerns about data privacy.There is no express legislation in India dealing with data protection. Although the Personal Data Protection Bill was introduced in Parliament in 2006, it is yet to see the light of day. The bill seems to proceed on the general framework of the European Union Data Privacy Directive, 1996. It follows a comprehensive model with the bill aiming to govern the collection, processing and distribution of personal data. It is important to note that the applicability of the bill is limited to ‘personal data’ as defined in Clause 2 of the bill.The bill applies both to government as well as private enterprises engaged in data functions. There is a provision for the appointment of, “Data Controllers”, who have general superintendence and adjudicatory jurisdiction over subjects covered by the bill. It also provides that penal sanctions may be imposed on offenders in addition to compensation for damages to victims.The stringency of data protection law, whether the prevailing law will suffice such needs, whether the proposed amendments are a welcome measure, whether India needs a separate legislation for data protection etc are questions which require an in-depth analysis of the prevailing circumstances and a comparative study with laws of other countries. There is no consensus among the experts regarding these issues. These issues are not in the purview of this write-up. But there can be no doubt about the importance of data protection law in the contemporary IT scenario and are not disputable.
-
Which feature of Document Management System benefits an organisation the most?
The answer to your question really lies in how you define “benefit” and this is directly related to the primary business challenge that triggers you to invest in document management.Kent is right, finding the information you need, when you need it, from where you need, from any device with the confidence that it is is the most current version is the basis for any DMS.However, when I look at the benefit, I tend to look at it more from a competitive advantage stand-point. Finding information is great, but streamlining your processes and reducing costs are even better. That’s where I feel workflow and predictive analytics really come into play. These are the tools in DMS that allow you to be more competitive and flexible. They tend to result in a much more tangible and faster ROI.
-
What is the best software to manage my company's document and also I want to organize it according to different departments?
I Would Suggest docManager®, Best document management system in india..it has following features :STORAGE LOCATION: The documents can be stored centrally in a systematic way, so that it can be retrieved whenever required.CHECK-IN / CHECK-OUT: This helps in Version Controlling the documents during simultaneous update.LOCKING / UNLOCKING: This Locks the document access for the other user but will be viewed by the owner.ANNOTATION: Tagging the DocumentCommenting the DocumentEmail NotificationStamps & SignatureSEARCH: Find documents and files in seconds.SHARE: Allow more than one user to view the documents at same timeVERSION CONTROL: Version control gives you the ability to manage document change and revision done for particular documents.AUDIT: Verify who viewed and made updates to the documents.ARCHIVING: Automatically archive the documents which are not in use after its expiration.DOCUMENT CAPTURE & MANAGEMENT : Centralize paper documents & electronic files and access them with one familiar interface from all work stations in your officeDOCUMENT SECURITY: Extremely flexible user and group based security along with many system level rights .User and Folder based ‘Ownership Overrides’ allow administrators to retain ownership of documents for specified users or folders. Separate export rights prevent unauthorized export of information out of system.Use of DRM (Digital Rights Management) to secure Documents.ACTIVE DIRECTORY INTEGRATION: Integration with Microsoft Active Directory allows users to login to Docs-vault using their Windows login name and password eliminating the need for remembering separate passwords.BUILT-IN REPORTS: Powerful built-in reports are available for Administrator to get insight and useful data related to documents, users and other important business processes.WORKFLOW: Replicate your document centric business processes to make them more streamlined, more accurate and less time consuming. Automate repeatable processes like account payable, leave applications, order processing, purchase authorizations, etc.WORKFLOW HIERARCHY MANAGEMENT: Manage documents viewing and editing rights, according to the hierarchy followed in your organisation. Add / Remove members in the departments for managing workflow in the organisation.DOCUMENT RELATIONS: Users can set many-to-many relations between documents. Document Relations allow grouping and easy access of documents filed in different locations throughout the Repository.RECORDS RETENTION MODULE: Create retention policies for different types of documents and dispose them in accordance with local laws and industry standards. Manage the entire life cycle of physical records and digital documents – from its safe storage, classification, circulation to its final authorized disposition.PERSONAL USER WORKSPACES: Quickly access you’re recently accessed, checked out, imported and created documents as well as your favourite files and folders.DOCUMENT PREVIEWS: Preview contents of all common file formats (Word, Excel, Emails, Tiff, PDF, images, Audio, Video) without their native applications They also Provide the free demo, contact them today for the free demo : http://www.docmanager.co.in/Cont...
-
What is the best document management system?
I personally really like Document 365 Business by Kdan Mobile - it’s great for project management/overseeing, collaboration on documents, secure file sharing with password protected links, working with PDFs, data exporting and transferring, cloud syncing for easy access and improved productivity.If you work with PDFs a lot, there’s PDF Reader mobile app (part of the Document 365) that lets you scan any paper document and turn it into either PDF or an editable text file with OCR. If you are a licensed member, you can create a team-managed account for easy file sharing, turning in documents for approval/signatures and stamps, and you get 1 TB of storage on Kdan Cloud. Document 365 also allows for external integrations, letting you customize the software a bit further.So, here’s what Document 365 is best suited for: project management/collaboration, working with PDFs (editing, annotating/highlighting, signing), safe data management (with password protected links, watermarks and access management) - therefore a high level of security, good for multi-user experience, lots of cloud storage for archiving, intuitive interface and overall ease of use. I personally like using Document 365 for document management and archiving, and the PDF Reader for most of my work with PDFs.Disclaimer: I am part of Kdan’s team and my answers might be a bit biased.
Trusted esignature solution— what our customers are saying
be ready to get more
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
When a client enters information (such as a password) into the online form on , the information is encrypted so the client cannot see it. An authorized representative for the client, called a "Doe Representative," must enter the information into the "Signature" field to complete the signature.
What is the original on an electronic signature document?
Is there a standard that is followed, or any set of guidelines that govern it?
A: I would say that the standard for a digital signature is that it need not be unique. It need not be a code or a signature but a symbol that identifies a person. As such, this form may be sent via the internet or through a mobile phone (with which it can be stored as an electronic signature without the need for the transmission of the information) or via a paper form such as a piece of paper or a computer page. For example, it can consist of a number (with or without spaces) of characters, a symbol or a set of punctuation characters.
For more information see:
Q: So, if I'm signing something that was created by someone else I have to get their permission?
A: No. The information you are signing is the original. It is not a copy of someone else's original. It is your personal signature.
Q: So I can send a file to someone who is not my friend using my computer's internet connection. They can then open the file and they can print the page or download it in order to share it with others or distribute it?
A: Yes. The person that receives it is free to do anything they like with it and they don't have to obtain consent from the owner of the file in order to do so, even to share. This applies whether you use an internet connection, a wireless access point, a local network, a USB port or a cloud service like Dropbox or SkyDrive.
Q: Do I need anyone to know I'm sharing that file?
A: No. Even t...
How to sign pdf remotely?
What can I do if I can't get to my email?
How can I send myself a pdf message?
How to make email notifications work with a pdf in a post?
How to create email signatures with a pdf message?
Why is my message not showing up?
How to send pdf messages to groups?
Why is the PDF not working for me when I try to send it to people?
What's the best thing an email can look like?
How do I send a pdf on your website?
Can I send my friends a pdf?
How do I send a pdf to another email address?
How many people can I send a pdf to?
Who can I invite to a pdf message?
How can I send a pdf to more people than the people I've already got?
Do I have to be the recipient?
Can a pdf message get stuck?
Do I need to be in the same address space to send a pdf?
How long is a pdf message?
Can I add an extra attachment to a pdf message?
Can I send two pdf messages with one from my address book?
Can I send a zip file to somebody?
Can I send a pdf to my boss?
Will my boss email me if I send him/her a pdf?
What if I don't send a pdf message?
Can I send my boss a pdf message?
Can I send a pdf that will work for more than one person?
Will a pdf message work on a phone?
Can I send a pdf to another address?
How do you add an image to a pdf message?
If I don't send a file from my address book, should I email the pdf to myself and ask permission?
Can I send a pdf to a person who doesn't have a computer/phone?
How can I send a pdf with a password?
How...
Get more for Remove Electronic signature Document Safe
- Electronic signature Vermont Rental lease agreement Mobile
- Electronic signature Maine Residential lease agreement Online
- Electronic signature Minnesota Residential lease agreement Easy
- Electronic signature Wyoming Rental lease agreement template Simple
- Electronic signature Rhode Island Residential lease agreement Online
- Electronic signature Florida Rental property lease agreement Free
- Can I Electronic signature Mississippi Rental property lease agreement
- Can I Electronic signature New York Residential lease agreement form
Find out other Remove Electronic signature Document Safe
- California 9044 form
- Michigan dhs 1010 redetermination form 2012
- Please print for application instructions view page 4 form
- Dhs 4258a form
- Dhs 4469 eng form
- Appsstateorusformsservedde0415f 2018 2019
- Dhs 3324 form
- Copyright form tx
- Twcc 5 form
- Application for certified copy of a texas title form
- Coh form
- Texas child support disbursement unit direct deposit form
- Texas divorce forms
- Form 2021pdffillercom
- Texas department of aging and disability services form 2022
- Roofing certificatepdffillercom form
- Texas new hire reporting 2011 form
- Form 5505 nar
- Electronic application for mail in ballot for texas form
- City of texas city 1801 9 avenue north texas city texas texas city tx form