Send Electronic signature Word iOS
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






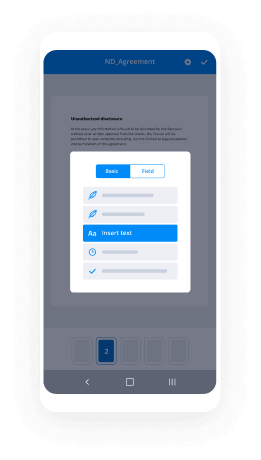
How to utilize electronic iOS signature with airSlate SignNow
In the contemporary digital landscape, employing an electronic iOS signature is crucial for optimizing document workflows. airSlate SignNow provides a robust platform that allows users to transmit and sign documents with ease. With its intuitive interface and comprehensive features, companies can improve their productivity while conserving time and resources.
Steps to generate an electronic iOS signature with airSlate SignNow
- Launch your chosen web browser and head to the airSlate SignNow webpage.
- Register for a complimentary trial account or sign in to your existing account.
- Select the document you intend to sign or distribute for signatures by uploading it to the platform.
- If you plan to reuse this document, transform it into a reusable template for future reference.
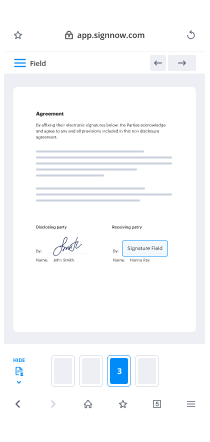
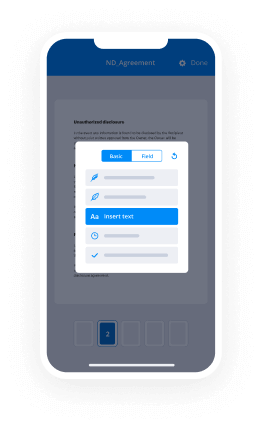
- Access your document and perform necessary modifications, such as adding fillable sections or specific information required from recipients.
- Insert your electronic signature on the document and allocate signature fields for each recipient.
- Click on 'Continue' to complete and send out an invitation for eSigning.
By adhering to these instructions, you can effectively leverage airSlate SignNow to handle your electronic iOS signatures. This platform not only simplifies the signing procedure but also fosters collaboration among team members and clients.
Eager to enhance your document signing process? Register for airSlate SignNow today and explore how our clear pricing and outstanding 24/7 support can aid your business!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is an electronic iOS signature and how does it work?
An electronic iOS signature is a digital representation of your handwritten signature that can be created and used on iOS devices. With airSlate SignNow, you can easily sign documents on your iPhone or iPad using a finger or stylus. This process ensures that your signature is legally binding and securely attached to your documents.
-
Is airSlate SignNow compatible with all iOS devices?
Yes, airSlate SignNow is compatible with all iOS devices, including iPhones and iPads. This allows users to create and manage electronic iOS signatures seamlessly, no matter what device they are using. Whether you're in the office or on the go, you can easily eSign documents from your iOS device.
-
What are the benefits of using electronic iOS signatures?
Using electronic iOS signatures offers numerous benefits, including increased efficiency and reduced turnaround times for document signing. With airSlate SignNow, you can sign documents anytime and anywhere, eliminating the need for printing and scanning. Moreover, electronic signatures enhance security and ensure compliance with legal standards.
-
How much does airSlate SignNow cost for electronic iOS signatures?
airSlate SignNow offers flexible pricing plans to cater to different business needs. You can choose a plan that suits your requirements and budget, with options for monthly or annual billing. Each plan includes features for creating electronic iOS signatures, allowing you to manage your signing process effectively.
-
Can I integrate airSlate SignNow with other applications?
Yes, airSlate SignNow offers various integrations with popular applications such as Google Drive, Salesforce, and Dropbox. This allows you to streamline your workflow and make the most out of your electronic iOS signature capabilities. Integrating with other tools enhances productivity and keeps all your documents organized.
-
Are electronic iOS signatures legally binding?
Absolutely! Electronic iOS signatures created with airSlate SignNow are legally binding and compliant with e-signature regulations, such as the ESIGN Act and UETA. This means you can confidently use electronic signatures for contracts and agreements, knowing they hold the same legal weight as traditional handwritten signatures.
-
What features does airSlate SignNow offer for electronic iOS signatures?
airSlate SignNow includes a range of features designed for easy document signing on iOS devices. These features include customizable templates, real-time tracking, and secure storage for your signed documents. Additionally, the platform allows you to collect signatures from multiple parties, making it ideal for collaborative workflows.
-
What does PDF stand for a computer?
Portable Document FormatThe .pdf files can only be open with pdf reader softwares like the most popular signNow and Foxit Reader. These applications are also available for Android and iOS.Well, we mostly create pdf files for electronic signatures and to make it more safer.As we know, most of the companies uses their unique font style in their documents and if the company send a letter to any of their associates by an email in a Ms Word format. Their associates might find the document in different font style because they are not using the same font style. So pdf documents are not editable which makes them more portable to share. Pdf files maintain the same font style and style in which it was created.You can check by yourself by making documents in a ms word format and pdf format.If u wanna know how to create pdf documents u must google it.
-
How secure is WhatsApp's new end-to-end encryption?
Warning long answer!Since 1990, I’ve been studying the confidentiality of the messaging systems on computers and mobile devices.It was obvious that the electronic forums, emails and SMS messages could easily be intercepted by 3rd parties. Expecting the service providing companies to develop and implement confidentiality protocols were unrealistic. There were never a general consensus about the need for confidentiality or inter-service protocol development.With the discouragement of the governments many computer scientists shied away from creating software to keep communication confidential between parties.Many spy movies showed advanced technologies to keep the communication between spies and their organizations. The most famous being the Enigma machine used by the Germans during the World War 2. British scientist Alan Turing was the one to develop an early version of today’s computers to solve the mystery of the Enigma machine. Like every visionary he had serious problems with the establishment. After the government discovering that he was gay, he was given 2 options. First option was jail time until he turned heterosexual, or chemical castration. Poor Turing chose the second option and after a while he committed suicide. Every cryptologist today remembers to what happened to the first representative of this science.Without getting into the technological terms (they are all available on Wikipedia) the best way to keep conversation confidential is to use a code book between 2 (or more, but more on that later) parties. A code book is a simple definition and a list of codes that is shared between the parties and each code is used only once. Unless the code book is compromised this method of communication privacy is bullet proof. There is no computer in the world, and there won’t be any in the future that can figure out what the communication is. The only method would be the old school spying on the parties who are communicating between each other.If I need to give an example for the method above, it would be like, let’s choose a newspaper that is accessible to both parties. That will be our message base.Let’s define a codebook now:First code in the book is3–4,6–7,1–2 and repeats itselfsecond code is5–7,3–1,8–5,4–2 and repeats itselfSo let’s say I send you a message today like20,42,15,5,8,67,23,56,12,43,13,11,10Since it is our first message exchange you will use the first code in the book. Also our message base is only known to us which also makes it even more difficult for others to understand the secret message I just sent you.To understand the message, here is what you do: you pick up today’s New York Times which is the newspaper we agreed to use.Take the first number in the secret message which is 20, then look in the codebook for the first code which is 3–4. You go to the 3rd page find the 4th paragraph and get the 20th character and repeat this process for each number in the secret message I sent.Let’s say MI6 is trying to intercept the message, which they do because I sent the message by email or SMS or event with both to you.All they have is 20,42,15,5,8,67,23,56,12,43,13,11,10 and they have no idea what it means. They don’t know which text source we used, which was New York Times and they don’t know the code we used for that message which was 3–4,6–7,1–2. We can even make this more difficult, for each day of the week we use a different newspaper that we agree upon.And let’s say MI6 figures out which newspaper we use for each day, let’s say they even figure out our code mechanism which is the page, paragraph and character to decode the secret message.As long as we use each line of code only once and never repeat used codes, there is virtually no way that MI6 to figure out our conversation. Except of course sending their double o agent to one of us and beating us in the head with an iron bar which would make us sing like a bird and spill all the secrets.As you can see in the example an iron bar, strategically placed on your head with a moderate blow would break all the code we established.That reality aside, if I whisper to your ear the newspaper names and hand you a piece of paper with a list of codes which I also have the same copy, until ve run out of codes there is no way our communication can be interpreted when intercepted.The difficulty in this type of message confidentiality is sharing and keeping a piece of paper with a list of codes and do the code exchange again when the list of codes are depleted and never use a code again.When this is not possible for practical reasons like distance between parties or the number of messages exchanged being too high and frequent the methodology used is computer based encryption (ensuring the confidentiality of communication between parties) of messages.This is also not so unlike what we did in the first example. To create our never ending codes is that for each message we exchange we use 3 constants. You have a master key, a public key and we agree on a mathematical formula which is very very difficult for the computer to solve. The difficulty here ensures that the time to try every combination of variables (without the master key) for the formula is so long, it practically makes it impossible for others to guess our code list.In this method I also have a master key and a public key. To solve the issue of keeping a list of established codes and communicating that between parties we freely exchange our public keys with everyone and when I’m sending you a message, I use your public key (any of my keys except generating a special signature with my private key so that you can validate with my public key that ensures the message has originated really from me) to create a confidential message. When you receive it by email, SMS or regular post mail, you use your private key which can only find out the contents of the confidential message. And since we are talking about computer systems, we protect our private keys with passwords.I don’t like using names given by computer engineers or any other technical person but for the sake of clarification this master/public key and an established algorithm to use is called public private key cryptology.Another term I don’t like is ‘end to end encryption’. This is to confirm that the cryptology method used can not be intercepted by other parties and only the recipient can understand the contents of the message.One company who has developed an implementation of end to end encryption is Open Whisper Systems. They named their product ‘Signal’ which is a platform and also the name of their app on iOS and Android. Their product uses this public private key cryptology to ensure the text and voice communications between parties to stay confidential. Supposedly the infamous NSA whistle blower Edward Snowden uses their app and he considers it quite good.Now let’s circle back to the WhatsApp security issue. WhatsApp is using the protocol established by the Open Whisper Systems for their public private key protected communications (audio, video and text messages).The problem is the user friendliness of the Signal app is not good. There are certain times that these public and private keys have to be changed. 2 example of those times is if you change your phone or uninstall / reinstall your app (whichever app you are using, Signal or WhatsApp)To test the user friendliness of Signal App’s handling the change of the key pairs (public private key combinations) I used my regular human guinea pig Riz. It was very difficult for me to explain what he has to do and also to find the location of the menu items were horribly difficult. After cursing at me and the app designers many times Riz completed the approval of the new key exchange between us so we could communicate again.Let’s have a look into how WhatsApp has implemented this renewal of key pairs between users. Since authenticity of a user can only identified by trusting their private key signed signature and for the likely case of the user have a new phone or has reinstalled the WhatsApp App, WhatsApp servers keep a copy of the secret message until the recipient downloads it. Now let’s say that you sent me a message while I was offline and I changed phones meanwhile. When I get that message from you what the Signal app does is, it warns me and it won’t let you communicate with you until I approve your new public key (in the style of a combined public keys of both parties because there is only one code that needs to be verified on both ends). Instead of asking user to do the verification what WhatsApp does it re-encrypts your message with my new key again (in their explanation by asking your WhatsApp to keep that message in memory in encrypted form and first decrypt then re-encrypt the same message with my new public key) without asking neither of us to re-confirm the identity of both parties.This technically opens up a backdoor for intelligence agencies to decrypt the messages between parties.How does that happen? WhatsApp confirms App installation by SMS confirmation. Let’s say I want to intercept your WhatsApp messages. I send a team in a delivery van which looks like a repair van but which has a mobile communication signal jammer to your home address. The jamming is smart enough to make your phone think it is still in network coverage so you don’t suspect a thing unless you try to make a call which will look like mobile network is crowded and unavailable. While I knock your phone off the network I can do 2 things, I can either intercept any SMS messages which comes your way in my service van, or give a court order to the mobile phone company to give me a copy of your SMS messages in real time.Then I install WhatsApp on a new phone, enter your phone number as my number and receive a copy of the SMS confirmation with the verification number and enter it in WhatsApp. From that moment on I will receive any waiting (since I knocked you off mobile network) and any news messages WhatsApp users send to you.Intentional or unintentional this is a secret door that can be easily used by government agencies.If I used the above technique to intercept messages between Signal users, what would happen were to be, first I couldn’t receive any messages waiting in the cloud because Signal does not keep messages in the cloud, when you are offline, the message waits in the sender’s Signal App. When the sender tries to send a new or resend the unsent message to you, my new installation of Signal app on my government agency phone will inform your friend, the sender that I’ve changed our shared agreed secret code and asks your friend if s/he wants to approve this new installation on the other end by confirming the new shared secret code with you. When s/he calls you on your landline, you say you haven’t installed a new WhatsApp on your phone or changed phones, you both understand that there is another party in between trying to intercept your messages.Now, WhatsApp says that there is an option in their App, under Settings / Account / Security / Show Security Notifications which is by default off. If you turn this ON then their claim is you will receive notifications when a contact’s security code has changed. They don’t say if the messages will still be delivered in spite of a security notification or not. They add that ‘The messages you send your calls are encrypted regardless of this setting, WHEN POSSIBLE’. I capitalized the last 2 words, what the heck ‘WHEN POSSIBLE’ mean? They also do not say anything about the messages you are going to receive. Even though you enable this warning setting on, if your friend’s setting is not on, they will not be notified if the messages they are sending to you are intercepted.This unintentional secret door is called a ‘user friendly design choice’ by WhatsApp. It is such a user friendly design choice it is government agents friendly as well. I can’t imagine how many diplomats already delivered confidential messages to enemy agencies using WhatsApp. Diplomats in Brussels wake up and smell the coffee…
-
How secure is WhatsApp? What does the company have to say about the recent security flaws pointed out in their app?
Since 1990, I’ve been studying the confidentiality of the messaging systems on computers and mobile devices.It was obvious that the electronic forums, emails and SMS messages could easily be intercepted by 3rd parties. Expecting the service providing companies to develop and implement confidentiality protocols were unrealistic. There were never a general consensus about the need for confidentiality or inter-service protocol development.With the discouragement of the governments many computer scientists shied away from creating software to keep communication confidential between parties.Many spy movies showed advanced technologies to keep the communication between spies and their organizations. The most famous being the Enigma machine used by the Germans during the World War 2. British scientist Alan Turing was the one to develop an early version of today’s computers to solve the mystery of the Enigma machine. Like every visionary he had serious problems with the establishment. After the government discovering that he was gay, he was given 2 options. First option was jail time until he turned heterosexual, or chemical castration. Poor Turing chose the second option and after a while he committed suicide. Every cryptologist today remembers to what happened to the first representative of this science.Without getting into the technological terms (they are all available on Wikipedia) the best way to keep conversation confidential is to use a code book between 2 (or more, but more on that later) parties. A code book is a simple definition and a list of codes that is shared between the parties and each code is used only once. Unless the code book is compromised this method of communication privacy is bullet proof. There is no computer in the world, and there won’t be any in the future that can figure out what the communication is. The only method would be the old school spying on the parties who are communicating between each other.If I need to give an example for the method above, it would be like, let’s choose a newspaper that is accessible to both parties. That will be our message base.Let’s define a codebook now:First code in the book is3–4,6–7,1–2 and repeats itselfsecond code is5–7,3–1,8–5,4–2 and repeats itselfSo let’s say I send you a message today like20,42,15,5,8,67,23,56,12,43,13,11,10Since it is our first message exchange you will use the first code in the book. Also our message base is only known to us which also makes it even more difficult for others to understand the secret message I just sent you.To understand the message, here is what you do: you pick up today’s New York Times which is the newspaper we agreed to use.Take the first number in the secret message which is 20, then look in the codebook for the first code which is 3–4. You go to the 3rd page find the 4th paragraph and get the 20th character and repeat this process for each number in the secret message I sent.Let’s say MI6 is trying to intercept the message, which they do because I sent the message by email or SMS or event with both to you.All they have is 20,42,15,5,8,67,23,56,12,43,13,11,10 and they have no idea what it means. They don’t know which text source we used, which was New York Times and they don’t know the code we used for that message which was 3–4,6–7,1–2. We can even make this more difficult, for each day of the week we use a different newspaper that we agree upon.And let’s say MI6 figures out which newspaper we use for each day, let’s say they even figure out our code mechanism which is the page, paragraph and character to decode the secret message.As long as we use each line of code only once and never repeat used codes, there is virtually no way that MI6 to figure out our conversation. Except of course sending their double o agent to one of us and beating us in the head with an iron bar which would make us sing like a bird and spill all the secrets.As you can see in the example an iron bar, strategically placed on your head with a moderate blow would break all the code we established.That reality aside, if I whisper to your ear the newspaper names and hand you a piece of paper with a list of codes which I also have the same copy, until ve run out of codes there is no way our communication can be interpreted when intercepted.The difficulty in this type of message confidentiality is sharing and keeping a piece of paper with a list of codes and do the code exchange again when the list of codes are depleted and never use a code again.When this is not possible for practical reasons like distance between parties or the number of messages exchanged being too high and frequent the methodology used is computer based encryption (ensuring the confidentiality of communication between parties) of messages.This is also not so unlike what we did in the first example. To create our never ending codes is that for each message we exchange we use 3 constants. You have a master key, a public key and we agree on a mathematical formula which is very very difficult for the computer to solve. The difficulty here ensures that the time to try every combination of variables (without the master key) for the formula is so long, it practically makes it impossible for others to guess our code list.In this method I also have a master key and a public key. To solve the issue of keeping a list of established codes and communicating that between parties we freely exchange our public keys with everyone and when I’m sending you a message, I use your public key (any of my keys except generating a special signature with my private key so that you can validate with my public key that ensures the message has originated really from me) to create a confidential message. When you receive it by email, SMS or regular post mail, you use your private key which can only find out the contents of the confidential message. And since we are talking about computer systems, we protect our private keys with passwords.I don’t like using names given by computer engineers or any other technical person but for the sake of clarification this master/public key and an established algorithm to use is called public private key cryptology.Another term I don’t like is ‘end to end encryption’. This is to confirm that the cryptology method used can not be intercepted by other parties and only the recipient can understand the contents of the message.One company who has developed an implementation of end to end encryption is Open Whisper Systems. They named their product ‘Signal’ which is a platform and also the name of their app on iOS and Android. Their product uses this public private key cryptology to ensure the text and voice communications between parties to stay confidential. Supposedly the infamous NSA whistle blower Edward Snowden uses their app and he considers it quite good.Now let’s circle back to the WhatsApp security issue. WhatsApp is using the protocol established by the Open Whisper Systems for their public private key protected communications (audio, video and text messages).The problem is the user friendliness of the Signal app is not good. There are certain times that these public and private keys have to be changed. 2 example of those times is if you change your phone or uninstall / reinstall your app (whichever app you are using, Signal or WhatsApp)To test the user friendliness of Signal App’s handling the change of the key pairs (public private key combinations) I used my regular human guinea pig Riz. It was very difficult for me to explain what he has to do and also to find the location of the menu items were horribly difficult. After cursing at me and the app designers many times Riz completed the approval of the new key exchange between us so we could communicate again.Let’s have a look into how WhatsApp has implemented this renewal of key pairs between users. Since authenticity of a user can only identified by trusting their private key signed signature and for the likely case of the user have a new phone or has reinstalled the WhatsApp App, WhatsApp servers keep a copy of the secret message until the recipient downloads it. Now let’s say that you sent me a message while I was offline and I changed phones meanwhile. When I get that message from you what the Signal app does is, it warns me and it won’t let you communicate with you until I approve your new public key (in the style of a combined public keys of both parties because there is only one code that needs to be verified on both ends). Instead of asking user to do the verification what WhatsApp does it re-encrypts your message with my new key again (in their explanation by asking your WhatsApp to keep that message in memory in encrypted form and first decrypt then re-encrypt the same message with my new public key) without asking neither of us to re-confirm the identity of both parties.This technically opens up a backdoor for intelligence agencies to decrypt the messages between parties.How does that happen? WhatsApp confirms App installation by SMS confirmation. Let’s say I want to intercept your WhatsApp messages. I send a team in a delivery van which looks like a repair van but which has a mobile communication signal jammer to your home address. The jamming is smart enough to make your phone think it is still in network coverage so you don’t suspect a thing unless you try to make a call which will look like mobile network is crowded and unavailable. While I knock your phone off the network I can do 2 things, I can either intercept any SMS messages which comes your way in my service van, or give a court order to the mobile phone company to give me a copy of your SMS messages in real time.Then I install WhatsApp on a new phone, enter your phone number as my number and receive a copy of the SMS confirmation with the verification number and enter it in WhatsApp. From that moment on I will receive any waiting (since I knocked you off mobile network) and any news messages WhatsApp users send to you.Intentional or unintentional this is a secret door that can be easily used by government agencies.If I used the above technique to intercept messages between Signal users, what would happen were to be, first I couldn’t receive any messages waiting in the cloud because Signal does not keep messages in the cloud, when you are offline, the message waits in the sender’s Signal App. When the sender tries to send a new or resend the unsent message to you, my new installation of Signal app on my government agency phone will inform your friend, the sender that I’ve changed our shared agreed secret code and asks your friend if s/he wants to approve this new installation on the other end by confirming the new shared secret code with you. When s/he calls you on your landline, you say you haven’t installed a new WhatsApp on your phone or changed phones, you both understand that there is another party in between trying to intercept your messages.Now, WhatsApp says that there is an option in their App, under Settings / Account / Security / Show Security Notifications which is by default off. If you turn this ON then their claim is you will receive notifications when a contact’s security code has changed. They don’t say if the messages will still be delivered in spite of a security notification or not. They add that ‘The messages you send your calls are encrypted regardless of this setting, WHEN POSSIBLE’. I capitalized the last 2 words, what the heck ‘WHEN POSSIBLE’ mean? They also do not say anything about the messages you are going to receive. Even though you enable this warning setting on, if your friend’s setting is not on, they will not be notified if the messages they are sending to you are intercepted.This unintentional secret door is called a ‘user friendly design choice’ by WhatsApp. It is such a user friendly design choice it is government agents friendly as well. I can’t imagine how many diplomats already delivered confidential messages to enemy agencies using WhatsApp. Diplomats in Brussels wake up and smell the coffee…
-
What is a good, free document management solution?
When it comes down to choosing a good solution to manage your documents, whether you’re an individual, or part of a company, there are a few things to consider, and it basically boils down to what you need the software to accomplish, how much automation you want, how easy do you want it to be.A good all around option I’d suggest checking out it Kdan Document 365. It has some nice features to help you manage your PDFs (editing, signing, etc.,) and other kinds of documents you might be working with. If you’re part of a company, it’s easy to share and collaborate on projects/documents/presen...
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
What is an eSign message?
How to sign a pdf on pic?
Get more for Send Electronic signature Word iOS
- eSign Michigan Car Insurance Quotation Form Online
- eSign Michigan Car Insurance Quotation Form Mobile
- eSignature Massachusetts Mechanic's Lien Online
- eSignature Massachusetts Mechanic's Lien Free
- eSign Ohio Car Insurance Quotation Form Mobile
- eSign North Dakota Car Insurance Quotation Form Online
- eSign Pennsylvania Car Insurance Quotation Form Mobile
- eSignature Nevada Mechanic's Lien Myself
Find out other Send Electronic signature Word iOS
- Application for early notification of resignation program enrp form
- Multiplying and dividing integers guided notes form
- Application for approval of assembly plan metropolitan police mpdc dc form
- Form 2060
- Proportions and percents module quiz b answers form
- Oppt peru form
- Ndlm certificate generation tcpdf tutorial form
- Loan application form national australia bank
- Acrobat javascript scripting guide form
- Ercms form
- Hca medical records release form hca midwest health
- Prenatal care fact sheet womenshealth form
- L32100gj1996plc030976 form
- Requesters ong ohio form
- Blank invoice form
- W4 oklahoma form
- Jim beckert beaufort sc form
- Popsicle stick bridge blueprints pdf form
- Employers return of remuneration pensions form
- Certified letter template form