Remove Electronic signature Form Safe
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






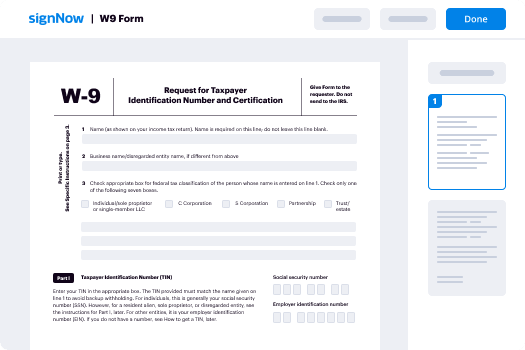
Grasping the rimworld entanglement manifold
The rimworld entanglement manifold is a notion that can be compared to the advantages of utilizing airSlate SignNow for document signing. This robust tool simplifies the signing procedure, presenting a user-friendly and economical solution for businesses aiming to improve their document workflows. With airSlate SignNow, you can handle your documents with convenience and effectiveness, guaranteeing a smooth experience for both you and your clients.
Detailed guide to utilizing the rimworld entanglement manifold with airSlate SignNow
- Launch your web browser and head to the airSlate SignNow homepage.
- Set up a complimentary trial account or log in if you possess an existing account.
- Choose the document you want to sign or send for signatures by uploading it.
- If you intend to use this document regularly, think about saving it as a template.
- Access the document and modify it by incorporating fillable fields and required information.
- Insert your signature and assign signature fields for the recipients.
- Advance by clicking Continue to complete and dispatch the eSignature invitation.
To conclude, airSlate SignNow offers an essential platform for managing document signing effectively and efficiently. By streamlining the procedure, it enables businesses to concentrate on growth rather than paperwork.
Prepared to revolutionize your document management process? Begin your complimentary trial with airSlate SignNow today and witness the benefits firsthand!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is the rimworld entanglement manifold?
The rimworld entanglement manifold refers to a unique feature in airSlate SignNow that enhances document management within the gaming world of RimWorld. It allows users to streamline the signing process, ensuring that all necessary documents are signed quickly and efficiently. This feature is particularly beneficial for maintaining organization in a complex, multi-faceted game environment.
-
How does the rimworld entanglement manifold improve collaboration?
The rimworld entanglement manifold enhances collaboration by providing a seamless platform for signing and managing documents among team members. With this feature, players can easily share documents and track their signing status, which fosters better communication and coordination. This ultimately leads to a more organized and efficient gameplay experience.
-
Is there a cost associated with using the rimworld entanglement manifold?
Using the rimworld entanglement manifold as part of airSlate SignNow comes with a variety of pricing plans to fit different business needs. We offer flexible subscription options that cater to both small teams and large organizations. You can choose a plan that maximizes the value of the rimworld entanglement manifold without breaking your budget.
-
What features are included with the rimworld entanglement manifold?
The rimworld entanglement manifold includes features such as customizable templates, real-time tracking, and automated reminders for document signing. These functionalities ensure that all players can effectively manage their documents without unnecessary delays. This makes the rimworld entanglement manifold a vital tool for anyone looking to enhance their gameplay through better document management.
-
Can the rimworld entanglement manifold be integrated with other tools?
Yes, the rimworld entanglement manifold is designed to integrate smoothly with various third-party applications, enhancing its functionality. This means you can use it alongside your favorite project management or communication tools, creating a comprehensive workflow. These integrations allow for easier document sharing and signing, making the rimworld entanglement manifold even more powerful.
-
What are the benefits of using the rimworld entanglement manifold in gaming?
The rimworld entanglement manifold provides gamers with a structured way to manage their documents, which can enhance overall gameplay. By facilitating quick and easy eSigning, it reduces the time spent on paperwork, allowing players to focus on their in-game strategies. This efficiency makes the rimworld entanglement manifold an essential asset for serious players.
-
How secure is the rimworld entanglement manifold for document signing?
The rimworld entanglement manifold prioritizes security by employing advanced encryption and authentication measures to protect your documents. This ensures that all signed documents are stored securely and are accessible only to authorized users. With the rimworld entanglement manifold, you can confidently manage your sensitive information without compromising on security.
-
What is the best free PDF reader for large documents?
[1] PDF format is popularly known as print document format. This creates a virtual printer within operating system to print the document. For offline scanning of document, the PDF format is popular. The importance attached with these program is that you need to have PDFsoftware installed to run these files. If someone sends you PDF file and your computer do not have such software installed then that file is not to be read from there.There are so many PDF softwires available and this article aims to find out the mostly free software or freeware to help readers to choose from variety of options. More and more operating systems are providing built-in facilities for such products. Now-a-days everything comes with PDF formats beginning from circulars, bank statement, insurance statement, tax statement and e-books.That is why there immense important to have the free PDF software installed on computer but the thousand question is which one is to choose from the variety of resources available.Sumatra PDF:Sumatra PDF is available for download to Windows since the times of Windows XP. This program has very low foot print, light on system resources and fast. It is going to perform simple task as well as it is going to perform complex task depending upon you choose from PDFfiles. It is available with installed version as well as standalone portable version in which it does not write to registry.It is available in 64 bit version on Windows. It is available for Windows XP, Vista, 7, 8, 8.1 and 10. It is available for Windows operating system only.signNow Reader DC:It is from signNow and signNow is available for free for users. While installing this software do check for installation of MCAfee security and safe connect.it is a big download of nearing to 120 MB. Yours antivirus software might stop this installation so allow to install it. This software for high=end computing processes.Many features are included with it and for some features you might need it and if you want to have these features then it is better to choose this software. It has mobile version of android and apple operating system. With it you are going to synchronize documents with clouds and yours signature too and everything is going to stay with cloud to access from each and every device.When you first download signNow on Windows, a download manager first downloads and it is small in size and then by opening that download manager signNow software is installed and this is nearer to 120 MB.PDF-Xchange Editor:PDF-Xchange Editor is a smart PDF tools and most functions are free except some complex ones. It is a PDF reader, pdf editor and pdf tools. It can print PDFs, fill the forms created with signNow and can extract images from PDF files. There are some advanced features included in this free version but most of these are not free one is that watermarking of PDFsoftware which is not free.Foxit Reader:Foxit Reader is fast, simple and is there for years. It is available for Windows, Apple and android versions. It can fill forms and save data. Can include and validate electronic signatures. During installation user need to be cautioned not to install so many verities of other software. In order to keep the size of download minimal, the user manual is available for separate download.It is faster than PDF-Xchange Editor. If you are not interested in OCR facilities then Foxit reader is best suited for yours work. Multiple PDF documents when opened all these are opened in tab format and shifting from one tab to the other is easier. From time to time it introduces some new features in order to provide dynamic software development.It allows adding up of multimedia files easier. Collaboration with social media accounts becomes easier with Fixit Reader because of the ease to synchronize with Twitter, Facebook, Evernote and SharePoint. One caution is that Foxit Reader comes bundled with so many other software and toolbar and it is important to not to allow installations of such software during its installation.MuPDF Reader:It is very lightweight PDF Reader. On its first launch it will ask you about to choose from files instead of showing its interface and when the PDF is opened then it shows the exact documents and no toolbar and other interfaces are present. In order to see the interface of MuPDF reader you are going to click on the top left of the visible windows to find it. It provides a cleaner interface and superior look for PDF files.Google Chrome PDF viewer:While browsing for internet whenever you see any PDF and click on it and it will slowly open in another tab of Chrome and you can read it from there or download by clicking the downloadsymbol available there. This setting can be turned and changed out there easily, go to settings of chrome and then advanced and then content settings and then pdf documents, Scroll down and click on PDF documents and from there switch on ‘Download PDF files instead of opening automatically opening them in Chrome’ and this will download PDF files from net to computer.If you want to read PDF files that are stored inside computer, then right click on that files and then open with chrome and your chrome reader will automatically, open pdf files and for this you will not have to install pdf viewers. Similarly, with android if you install Google Drive then you will not need any other third-party PDF apps as Google Drive act as PDF viewer and make it default while opening the first PDF and that is going to make it default.TinyPDF:TinyPDF as the name suggests has very small foot print of PDF reader and it has no string attached. It is only 586k as it is less than one MB. It does not contain no malware, adware, watermarks and no pop Global Home: UPS is completely free. JPEG compression is supported. No ghost script and third-party software included with the installer version. The downside is that it is partially supported on 64-bit computer. Automatic font management is there.There are so many alternatives to use for PDF viewer and if your computer is 64 bit then you can download the 64 bit version of Sumatra PDF and if you want to insert electronic signature then opt for Foxit PDF reader and if you want to have the old and classic PDF reader which is heavier in file composition and not for low end computing purposes then go for signNow and lastly if you do not want to install PDF readers at all then it is better to open it with Google Chrome built in PDF viewer.So, there are many large numbers of option to choose from and if you want to have some complex PDF functions besides the presence of PDF reader you need pdf tools and others then it is best to have PDF-Xchange viewer and so many other option listed here you can choose it from. There are some other alternatives are available which are there to search ad find in internet.This entry was posted in Android Apps on Google Play, Apple Inc., Computer Information Technology, Google, Google Chrome, Information Technology, Internet, Windows 10, Windows 8, Windows XP and tagged signNow, Apple, doPDF, FOXIT READER, free PDF converter, google chrome, image to pdf converter, PDF Password Remover, pdf printer, pdf-xchange, Sumatra PDF A PDF Viewer for Windows, WINDOWS, Windows 8, WINDOWS VISTA, WINDOWS XP, Windows XP SP3 onFootnotes[1] Best Free PDF Writer and Reader
-
What are the laws - Data Protection, Data Transmission and Export and Data Encryption in India to operate a technology platform
The Information Technology Act, 2000 came into force on 17.10.2000 vide G.S.R No. 788(E) dated 17.10.2000 and for the first time, a legal definition of “Computer”, “Data”, “electronic record”, “Information” et al were provided. The said Act gave a legal recognition to the electronic records and digital signatures and in Chapter IX thereof provided for penalty and adjudication. Section 43 of the Act interalia provided that in case of unauthorised access, download or copying or damage to data etc, the person responsible shall be liable to pay damages by way of compensation not exceeding one crore rupees to the person affected.Apart from civil liability provided under Section 43, Chapter XI (Sections 63 to 78) of the Act of 2000 provided for criminal liability in cases of Tampering, Hacking, publishing or transmitting obscene material, misrepresentation etc. Apart from the same, Section 72 of the Act provided for penalty in case of bsignNow of confidentiality and privacy and laid that in case any person who has secured access to any electronic record, Data or information, discloses the same to any other person without obtaining the consent of the person concerned, he shall be punished with imprisonment upto two years or with fine upto Rupees one lakh or with both.However, the provisions of the Information Technology Act, 2000 were not adequate and the need for more stringent data protection measures were felt, the Information Technology (Amendment) Act, 2008 was enacted which came into force on 27.10.2009. The said Amendment Act brought in the concepts like cyber security in the statute book and widened the scope of digital signatures by replacing the words “electronic signature”. The amendment act also provided for secure electronic signatures and enjoined the central government to prescribe security procedures and practices for securing electronic records and signatures (Sections 15-16) The amendment Act also removed the cap of Rupees One Crore as earlier provided under Section 43 for damage to computer and computer systems and for unauthorised downloading/ copying of data. The said Amendment Act also introduced Section 43A which provides for compensation to be paid in case a body corporate fails to protect the data. Section 46 of the Act prescribes that the person affected has to approach the adjudicating officer appointed under Section 46 of the Act in case the claim for injury or damage does not exceed Rupees Five crores and the civil court in case, the claim exceeds Rupees Five crores. The amendment act also brought/ introduced several new provisions which provide for offenses such as identity theft, receiving stolen computer resource/ device, cheating, violation of privacy, cyber terrorism, pornography (Section 66A-F & 67A-C). The amendment act also brought in provisions directing intermediaries to protect the data/information and penalty has been prescribed for disclosure of information of information in bsignNow of lawful contract (Section 72A)With the enactment of the Amendment Act of 2008, India for the first time got statutory provisions dealing with data protection. However, as the ingredients of “sensitive personal data and information” as well as the “reasonable security practices and procedures” were yet to be prescribed by the Central Government, the Ministry of Communications and Information Technology vide Notification No. GSR 313 (E) dated 11th April 2011 made the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information ) Rules, 2011 (the said rules). Rule 3 of the said rules defines personal sensitive data or information and provides that the same may include information relating to password, financial information such as bank account or credit card details, health condition, medical records etc. Rule 4 enjoins every body corporate which receives or deals with information to provide a privacy policy. Rule 5 prescribes that every body corporate shall obtain consent in writing from the provider of the sensitive information regarding purpose of usage before collection of such information and such body corporate will not collect such information unless it is collected for a lawful purpose connected with the function or activity of such body corporate and collection of such information or data is necessary and once such data is collected, it shall not be retained for a period longer than what is required. Rule 6 provides that disclosure of the information to any third party shall require prior permission from the provider unless such disclosure has been agreed to in the contract between the body corporate and the provider or where the disclosure is necessary for compliance of a legal obligation. The Body corporate has been barred to publish sensitive information and the third parties receiving such information have been barred to disclose it further. Rule 7 lays down that the body corporate may transfer such information to any other body corporate or person in India or outside, that ensure the same level of data protection and such transfer will be allowed only if it is necessary for performance of lawful contract between the body corporate and provider of information or where the provider has consented for data transfer. Rule 8 of the said rules further provide reasonable security practises and procedures and lays down that international standard IS/ISO/IEC 27001 on “Information Technology- Security Techniques- Information Security Management System- requirements “ would be one such standard.The Ministry of Communication and Information Technology further issued a press note dated 24th August 2011 and clarified that the said rules are applicable to the body corporate or any person located within India. The press note further provides that any body corporate providing services relating to collection or handling of sensitive personal data or information under contractual obligation with any other legal entity located within India or outside is not subject to requirements of Rules 5 &6 as mentioned hereinabove. A body corporate providing services to the provider of information under a contractual obligation directly with them however has to comply with Rules 5 &6. The said press note also clarifies that privacy policy mentioned in Rule 4 relates to the body corporate and is not with respect to any particular obligation under the contract. The press note at the end provides that the consent mentioned in Rule 5 includes consent given by any mode of electronic communication.Data Protection relates to issues relating to the collection, storage, accuracy and use of data provided by net users in the use of the World Wide Web. Visitors to any website want their privacy rights to be respected when they engage in e-Commerce. It is part of the confidence-creating role that successful e-Commerce businesses have to convey to the consumer. If industry doesn't make sure it's guarding the privacy of the data it collects, it will be the responsibility of the government and it's their obligation to enact legislation.Any transaction between two or more parties involves an exchange of essential information between the parties. Technological developments have enabled transactions by electronic means. Any such information/data collected by the parties should be used only for the specific purposes for which they were collected. The need arose, to create rights for those who have their data stored and create responsibilities for those who collect, store and process such data. The law relating to the creation of such rights and responsibilities may be referred to as ‘data protection’ law.The world’s first computer specific statute was enacted in the form of a Data Protection Act, in the German state of Hesse, in 1970.The misuse of records under the Nazi regime had raised concerns among the public about the use of computers to store and process large amounts of personal data.The Data Protection Act sought to heal such memories of misuse of information. A different rationale for the introduction of data protection legislation can be seen in the case of Sweden which introduced the first national statute in 1973.Here, data protection was seen as fitting naturally into a two hundred year old system of freedom of information with the concept of subject access (such a right allows an individual to find out what information is held about him) being identified as one of the most important aspects of the legislation.In 1995, the European Union adopted its Directive (95/46/EC) of the European Parliament and of the Council of 24 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data (hereinafter, the Directive), establishing a detailed privacy regulatory structure. The Directive is specific on the requirements for the transfer of data. It sets down the principles regarding the transfer of data to third countries and states that personal data of EU nationals cannot be sent to countries that do not meet the EU “adequacy” standards with respect to privacy.In order to meet the EU “adequacy” standards, US developed a ‘Safe Harbour’ framework, according to which the US Department of Commerce would maintain a list of US companies that have self-certified to the safe harbor framework. An EU organization can ensure that it is sending information to a U.S. organization participating in the safe harbor by viewing the public list of safe harbor organizations posted on the official website.Data protection has emerged as an important reaction to the development of information technology. In India data protection is covered under the Information Technology Act, 2000 (hereinafter, the Act). The Act defines ‘data’ as, “‘data’ means a representation of information, knowledge, facts, concepts or instructions which are being prepared or have been prepared in a formalized manner, and is intended to be processed, is being processed or has been processed in a computer system or computer network, and may be in any form (including computer printouts magnetic or optical storage media, punched cards, punched tapes) or stored internally in the memory of the computer”. Protection of such data and privacy are covered under specific provisions in the Act. In the recent past, the need for data protection laws has been felt to cater to various needs. The following analyses the position of data protection law with respect to some of the needs.Data Protection Law In Respect of Information Technology Enabled Services (ITES)India started liberalizing its economy in the 1990’s and since then a huge upsurge in the IT business process outsourcing may be witnessed. Financial, educational, legal, marketing, healthcare, telecommunication, banking etc are only some of the services being outsourced into India. This upsurge of outsourcing of ITES into India in the recent past may be attributed to the large English-speaking unemployed populace, cheap labour, enterprising and hardworking nature of the people etc. Statistics have shown that the outsourcing industry is one of the biggest sources of employment. In a span of four years, the number of people working in call centers in the country supporting international industries has risen from 42,000 to 3,50,000. Exports were worth $5.2 billion in 2004-2005 and are expected to grow over 40% this fiscal year. US is currently the biggest investor in Indian ITES, taking advantage of cheap labour costs. Statistics indicate that software engineers with two-years experience in India are being paid about 1/5th of an equivalent US employee.Concerns about adequacy of lawBPO FraudsWith globalization and increasing BPO industry in India, protection of data warrants legislation. There are reasons for this. Every individual consumer of the BPO Industry would expect different levels of privacy from the employees who handle personal data. But there have been situations in the recent past where employees or systems have given away the personal information of customers to third parties without prior consent. So other countries providing BPO business to India expect the Indian government and BPO organizations to take measures for data protection. Countries with data protection law have guidelines that call for data protection law in the country with whom they are transacting.For instance, in, the European Union countries according to the latest guidelines, they will cease to part with data, which are considered the subject matter of protection to any third country unless such other country has a similar law on data protection. One of the essential features of any data protection law would be to prevent the flow of data to non-complying countries and such a provision when implemented may result in a loss of "Data Processing" business to some of the Indian companies.In the recent past, concerns have been raised both within the country as well as by customers abroad regarding the adequacy of data protection and privacy laws in the country. A few incidents have questioned the Indian data protection and privacy standards and have left the outsourcing industry embarrassed. In June 2005, ‘The Sun’ newspaper claimed that one of its journalists bought personal details including passwords, addresses and passport data from a Delhi IT worker for £4.25 each. Earlier BPO frauds in India include New York-based Citibank accounts being looted from a BPO in Pune and a call-center employee in Bangalore peddling credit card information to fraudsters who stole US$398,000 from British bank accounts.UK's Channel 4 TV station ran broadcast footage of a sting operation exposing middlemen hawking the financial data of 200,000 UK citizens. The documentary has prompted Britain's Information Commissioner's Office to examine the security of personal financial data at Indian call centers.In the absence of data protection laws, the kind of work that would be outsourced to India in the future would be limited. The effect of this can be very well seen in the health-care BPO business, which is estimated to be worth close to $45 billion. Lack of data protection laws have left Indian BPO outfits still stagnating in the lower end of the value chain, doing work like billing, insurance claims processing and of course transcription. Besides healthcare, players in the retail financial sector are also affected. Financial offshoring from banks is limited because of statutory compliance requirements and data privacy laws protecting sensitive financial information in accounts. In the Human Resource (HR) domain, there are many restrictions on sharing of personal information. In the medical domain, patient history needs to be protected. In credit card transactions, identity theft could be an issue and needs to be protected. Companies in the banking, financial services and insurance (BFSI) sector and healthcare have excluded applications/processes which use sensitive information from their portfolio for offshoring till they are comfortable about the data protection laws prevalent in the supplier country.Since there is lack of data protection laws in India, Indian BPO outfits are trying to deal with the issue by attempting to adhere to major US and European regulations. MNCs have to comply with foreign Regulations so that they don’t lose on their international partners. There are problems involved in this. Efforts by individual companies may not count for much if companies rule out India as a BPO destination in the first place in the absence of data protection law.Today, the largest portion of BPO work coming to India is low-end call centre and data processing work. If India has to exploit the full potential of the outsourcing opportunity, then we have to move up the value chain. Outsourced work in Intellectual Property Rights (IPR)-intensive areas such as clinical research, engineering design and legal research is the way ahead for Indian BPO companies. The move up the value chain cannot happen without stringent laws. Further, weak laws would act as deterrents for FDI, global business and the establishment of research and development parks in the pharmaceutical industry.Looking to the above scenario, we can say that for India to achieve heights in BPO industry stringent laws for data protection and intellectual property rights have to be made. . Thus, a law on data protection on India must address the following Constitutional issues on a "priority basis" before any statutory enactment procedure is set into motion:(1) Privacy rights of interested persons in real space and cyber space.(2) Mandates of freedom of information U/A 19 (1) (a).(3) Mandates of right to know of people at large U/A 21.Once the data protection rules are enforced in India, companies outsourcing to India are unlikely to dismantle the systems they have in place straightaway, and move data more freely to India. Hence ,the need for data protection laws would win over the confidence of international business partners; protect abuse of information; protection of privacy and personal rights of individuals would be ensured; there would be more FDI inflows, global business and the establishment of research and development parks in the pharmaceutical industry & impetus to the sector of e-Commerce at national and international levels would be provided.Data protection law in India (Present status):-Data Protection law in India is included in the Act under specific provisions. Both civil and criminal liabilities are imposed for violation of data protection.(1) Section 43 deals with penalties for damage to computer, computer system etc.(2) Section 65 deals with tampering with computer source documents.(3) Section 66 deals with hacking with computer system.(4) Section 72 deals with penalty for bsignNow of confidentiality and privacy. Call centers can be included in the definition of ‘intermediary’and a ‘network service provider’ and can be penalized under this section.These developments have put the Indian government under pressure to enact more stringent data protection laws in the country in order to protect the lucrative Indian outsourcing industry. In order to use IT as a tool for socio-economic development, employment generation and to consolidate India’s position as a major player in the IT sector,amendments to the IT Act, 2000 have been approved by the cabinet and are due to be tabled in the winter session of the Parliament.Proposed amendments:-The amendments relate to the following[22]:(i) Proposal at Sec. 43 (2) related to handling of sensitive personal data or information with reasonable security practices and procedures.(ii) Gradation of severity of computer related offences under Section 66, committed dishonestly or fraudulently and punishment thereof.(iii) Proposed additional Section 72 (2) for bsignNow of confidentiality with intent to cause injury to a subscriber.It is hoped that these amendments will strengthen the law to suffice the need.Data Protection Laws In Order To Invite ‘Data Controllers’.There has been a strong opinion that if India strengthens its data protection law, it can attract multi-national corporations to India. India can be home to such corporations than a mere supplier of services.In fact, there is an argument that the EU’s data protection law is sufficient to protect the privacy of its people and thus lack of strong protection under Indian law is not a hindrance to the outsourcing industry. To enumerate, consider a company established in EU (called the ‘data controller’) and the supplier of call center services (‘data processor’) in India. If the data processor makes any mistake in the processing of personal data or there are instances of data theft, then the data controller in the EU can be made liable for the consequences. The Indian data processor is not in control of personal data and can only process data under the instructions of the data controller. Thus if a person in EU wants to exercise rights of access and retrieve personal data, the data controller has to retrieve it from the data processor, irrespective of where the data processor is located. Thus a strong data protection law is needed not only to reinforce the image of the Indian outsourcing industry but also to invite multi-national corporations to establish their corporate offices here.Data Protection And TelemarketingIndia is faced with a new phenomenon-telemarketing. This is facilitated, to a large extent, by the widespread use of mobile telephones. Telemarketing executives, now said to be available for as low as US $70 per month, process information about individuals for direct marketing. This interrupts the peace of an individual and conduct of work. There is a violation of privacy caused by such calls who, on behalf of banks, mobile phone companies, financial institutions etc. offer various schemes. The right to privacy has been read into Article 21, Constitution of India, but this has not afforded enough protection. A PIL against several banks and mobile phone service providers is pending before the Supreme Court alleging inter alia that the right to privacy has been infringed.The EC Directive confers certain rights on the people and this includes the right to prevent processing for direct marketing. Thus, a data controller is required not to process information about individuals for direct marketing if an individual asks them not to. So individuals have the right to stop unwanted marketing offers. It would be highly beneficial that data protection law in India also includes such a right to prevent unsolicited marketing offers and protect the privacy of the people.Data Protection With Regard To Governance And PeopleThe Preamble to the Act specifies that, the IT Act 2000, inter alia, will facilitate electronic filing of documents with the Government agencies. It seeks to promote efficient delivery of Government services by means of reliable electronic records. Stringent data protection laws will thus help the Government to protect the interests of its people.Data protection law is necessary to provide protection to the privacy rights of people and to hold cyber criminals responsible for their wrongful acts. Data protection law is not about keeping personal information secret. It is about creating a trusted framework for collection, exchange and use of personal data in commercial and governmental contexts. It is to permit and facilitate the commercial and governmental use of personal data.The Data Security Council of India (DSCI) and Department of Information Technology(DIT) must also rejuvenate its efforts in this regard on the similar lines. However, the best solution can come from good legislative provisions along with suitable public and employee awareness. It is high time that we must pay attention to Data Security in India. Cyber Security in India is missing and the same requires rejuvenation. When even PMO's cyber security is compromised for many months we must at least now wake up. Data bsignNowes and cyber crimes in India cannot be reduced until we make strong cyber laws. We cannot do so by mere declaring a cat as a tiger. Cyber law of India must also be supported by sound cyber security and effective cyber forensics.Indian companies in the IT and BPO sectors handle and have access to all kinds of sensitive and personal data of individuals across the world, including their credit card details, financial information and even their medical history. These Companies store confidential data and information in electronic form and this could be vulnerable in the hands of their employees. It is often misused by unsurplous elements among them. There have been instances of security bsignNowes and data leakages in high profile Indian companies. The recent incidents of data thefts in the BPO industry have raised concerns about data privacy.There is no express legislation in India dealing with data protection. Although the Personal Data Protection Bill was introduced in Parliament in 2006, it is yet to see the light of day. The bill seems to proceed on the general framework of the European Union Data Privacy Directive, 1996. It follows a comprehensive model with the bill aiming to govern the collection, processing and distribution of personal data. It is important to note that the applicability of the bill is limited to ‘personal data’ as defined in Clause 2 of the bill.The bill applies both to government as well as private enterprises engaged in data functions. There is a provision for the appointment of, “Data Controllers”, who have general superintendence and adjudicatory jurisdiction over subjects covered by the bill. It also provides that penal sanctions may be imposed on offenders in addition to compensation for damages to victims.The stringency of data protection law, whether the prevailing law will suffice such needs, whether the proposed amendments are a welcome measure, whether India needs a separate legislation for data protection etc are questions which require an in-depth analysis of the prevailing circumstances and a comparative study with laws of other countries. There is no consensus among the experts regarding these issues. These issues are not in the purview of this write-up. But there can be no doubt about the importance of data protection law in the contemporary IT scenario and are not disputable.
-
What are some of the pragmatic solutions for preventing mass shootings in the US that both liberals and conservatives find mutua
For the benefit of people who don’t have a lot of time to read, I’m going to list a short version of my proposals in bullet points after this paragraph. However, if you have the time, I strongly suggest reading this answer in its entirety because it explains the proposals in fairly granular detail. The proposals are nuanced because gun control is a complicated issue when looked at objectively.Standardize on a process which flags individuals in the FBI’s Terrorist Screening Database for a delay in the background check process when said individuals try to buy a gun. During the three day delay period, the FBI has the opportunity to investigate and take legal action against the individuals if necessary.Create a secure electronic background check system which is available to the public so individuals selling firearms to residents of the same state can know whether it is safe to proceed with a transaction.Require membership in the Civilian Marksmanship Program for the purchase of semiautomatic centerfire weapons and centerfire magazines with more than ten rounds of capacity.Create a national permitting process for carrying concealed handguns which overrides state laws.The Gun Control Act of 1968 mandated that manufacturers and commercial sellers of firearms had to obtain a Federal Firearms License (FFL). This was done under the guise of regulating interstate commerce, trade which crosses state lines. The federal government is generally not allowed to regulate intrastate commerce, trade which remains entirely within a state. In 1994, the Brady Handgun Violence Prevention Act mandated that FFL holders had to perform a background check on any firearm transferred through the FFL to a individual who does not hold an FFL. In 1998, this process was streamlined into the National Instant Criminal Background Check System (NICS).With that in mind, we’re going to look at how firearms are legally purchased currently so we can have a perspective on potential improvements to the process.When buying a gun through an FFL, buyers must fill out BAFTE form 4473. I strongly recommend readers view the form. Buyers must submit valid photo identification (usually a driver’s license) to the FFL holder to verify their identity and some of the information on their form 4473. There are three categories of firearm which can be bought through a standard FFL dealer: handguns, long guns (rifles and shotguns), and “other firearms”. Buyers must be 18 years of age to buy long guns and 21 years of age to buy handguns from an FFL. “Other firearms” are a weird category which includes receivers for firearms (which is generally the serialized portion of a firearm) or firearms which do not fit the legal definition of a handgun or long gun but are also not regulated by the National Firearms Act. If the “other firearm” can be made into a pistol, the buyer must be 21 years of age. After a buyer has completed their form 4473, the FFL holder calls NICS and relays the completed information to the FBI.Source: (NICS Process in Motion for the Gun Buyer Video Transcript)The FBI runs the information through the NICS database. If the buyer’s provided information has matches within the NICS database, this will generate a “hit”. At the moment, hits include indictments and convictions for felonies, indictments and convictions for domestic violence, indictments and convictions for other crimes which are punishable by one or more years of imprisonment, known fugitives, dishonorable discharges, adjudications which determined an individual to be mentally defective, restraining orders for children or intimate partners, renouncements of citizenship, unlawful users of controlled substances, illegal aliens, and resident aliens who do not meet very specific criteria.If no hits in the NICS database are generated, the FFL is told to “proceed” and the FFL may complete transferring the firearm at the business’s discretion. If the buyer’s provided information generates a hit, the call will be transferred to an FBI employee who will review the information and determine whether the hit matches the rest of the buyer’s provided information. If the hit is valid and the buyer is a prohibited purchaser, the FFL will be told to “deny” the transfer. If the FBI employee determines the hit is invalid, the FFL will be told to “proceed”. If the FBI employee can not immediately determine the validity of a hit, the FFL will be told to “delay” the transfer and the FBI will do more research to determine the validity of a hit. At this point, the FBI is allotted three business days to tell the FFL to “proceed” or “deny”. If those three business days pass without a final judgement, the FFL may proceed with the transfer at their discretion. The system is set up this way so the FBI can not delay a buyer they can not prove is a prohibited possessor of firearms indefinitely, essentially amounting to a denial without due process of law. Nevertheless, some FFL holders maintain a policy of not proceeding with transfers which have do not receive a definite “proceed”; that is the business’s prerogative.If at any point in this process the FFL holder or its employees believes a buyer is purchasing a firearm on behalf of another person, then the FFL will deny the transfer independent of any judgement made by the FBI. Purchasing a firearm on behalf of another person is illegal.Now what about “internet gun sales”?Websites in the business of selling firearms are legally required to acquire an FFL. Since the website which holds an FFL can not visually verify a buyer’s identity, this means the firearms they sell are legally required to be transferred to an FFL near the buyer. At the FFL which facilitates the transfer, the buyer will be required to complete a form 4473 and go through a background check as described above.On auction sites which deal with firearms, buyers and sellers who do not hold FFLs will submit the information of an FFL near each party and arrange for the firearm to be transferred. The seller’s FFL will ship the firearm to the buyer’s FFL and once again the buyer will complete a form 4473 and go through a background check.The final category would be classified websites which allow firearms to be posted for sale. These are essentially the 21st century equivalent of posting a classified advertisement in a newspaper. In these cases, a buyer contacts the seller who posted the advertisement and the two parties enter negotiations. If the buyer and seller legally reside within the same state and are able to meet face to face to conduct a transfer, the firearm in question may be legally bought under federal law without a background check being conducted provided the seller does not have reason to believe the buyer is a prohibited possessor. If any of those conditions are not met, or if state law prohibits intrastate commerce in this fashion, then FFL holders must once again be involved. These conditions apply to all private person to person sales. One noteworthy quirk, under federal law, persons between the ages of 18 and 21 are not prohibited from purchasing a handgun through a private sale. This is in fact one of the very few ways citizens in this age group can exercise their constitutional right to possess handguns.What about gun shows?If a person buys a firearm from an FFL participating in a gun show (this constitutes the majority of firearm sales at gun shows) then a 4473 is filled out as normal. If a person is buying a firearm from a private party, laws regarding private sales apply. Think of gun shows simply as a way for people who might be interested in buying or selling firearms to all be in the same place at the same time. There’s nothing sneaky or tricky about them, they literally happen in convention centers and on fairgrounds. Local police and BATFE agents are always present at gun shows.Now that we have all that basic information out of the way, we can talk about actual changes to federal law.First let’s take a look at prohibiting suspected terrorists from purchasing firearms. We can all agree we hate terrorists, but they still have due process rights. Fortunately, the FBI is in charge of both the Terrorist Screening Database (TSDB) and the NICS database. Prospective gun buyers with records that produce a match in the TSDB could generate a hit in the NICS database. The FBI could then investigate the hit and, assuming the hit actually matched the buyer in question, determine whether or not to tell the FFL to delay the transfer. Within the current three day delay window, the FBI could bring the case before a judge. Should the judge find probable cause, the transfer could be legally halted. At this point the buyer should be notified and be interviewed as part of the investigation. If charges are appropriate, the FBI can file charges in a timely manner. Otherwise, the suspect should be allowed to go about their business without further interference. That puts a lot of burden on the FBI, but it isn’t supposed to be easy to legally strip citizens’ rights in the United States. Remember, the burden of proof always lies upon the accuser, not the defendant.One rather common gun control proposal in the United States is that of universal background checks on all firearm sales, including private intrastate sales. On a practical level, compliance and enforcement of a universal background check would be very difficult without some kind of national firearm registry linking specific firearms to their owners. No national firearm registry exists for regular rifles, shotguns, or pistols at the moment and it’s actually illegal to create one because of the Firearm Owners Protection Act passed in 1986. There remains a visceral fear of a firearms registry among many conservatives; the concerned parties believe that all firearm registries are nothing more than a precursor to the total confiscation of all firearms. This belief is objectively refuted because numerous firearm registries in multiple US states and democratic countries as well as a national registry on firearms regulated by the National Firearms Act exist and have not been precursors to a total confiscation of all firearms. However, many conservatives latch onto the words of a select handful of extremist politicians who espouse a desire for confiscation as proof that confiscation is the inevitable result of all registries.With all that being said, what might be feasible as an alternative to a universal background check is creating an online version of form 4473 so the public could voluntarily conduct background checks without going to an FFL. This is actually something most gun owners want because, at the moment, there’s no way of conducting a background check for a private intrastate sale in most states without involving an FFL. Involving an FFL introduces a financial disincentive because FFLs are businesses and usually charge for their services. I’ll propose the best system I’ve thought of so far which allows for minimal fraud and abuse.First, create a secure electronic variant of the 4473. It should include the buyer and seller information along with contact information for both parties. Once the form is completed, a unique confirmation number is sent out to both parties using the provided contact information. Both parties enter their confirmation numbers, then the form is submitted to the FBI and run through the NICS database. A single transaction number is generated for the NICS check and provided to the buyer and seller. The parties then call a phone number for a NICS automated line and enter the transaction number along with their unique confirmation numbers. This transfers the call to a live operator who examines the results of the NICS check performed for the transaction. The operator then tells the seller to “proceed”, “delay”, or “deny” just as they would with an FFL.The idea behind the whole system is that it allows for an effective background check to be done while offering a reasonable measure of privacy for the buyer. Sure, somebody could abuse the system if they wanted to put in enough effort, but they wouldn’t get very much information. It also removes a financial disincentive; it only costs individuals time to do a check like this and the check and be performed virtually anywhere, not just at FFL locations.Now, let’s discuss assault weapons and magazines which hold more than ten rounds. The problem with the Federal Assault Weapons Ban of 1994 was that it didn’t do anything except drive up prices on the magazines and weapons described by the ban. There was no measurable impact on crime during the ten years the Assault Weapons Ban was in effect.Here is how assault weapons were defined in 1994:Semi-automatic rifles able to accept detachable magazines and two or more of the following:Folding or telescoping stockPistol gripBayonet mountFlash suppressor, or threaded barrel designed to accommodate oneGrenade launcher mountSemi-automatic pistols with detachable magazines and two or more of the following:Magazine that attaches outside the pistol gripThreaded barrel to attach barrel extender, flash suppressor, handgrip, or suppressorBarrel shroud safety feature that prevents burns to the operatorUnloaded weight of 50 oz (1.4 kg) or moreA semi-automatic version of a fully automatic firearm.Semi-automatic shotguns with two or more of the following:Folding or telescoping stockPistol gripDetachable magazine.All of those things are cosmetic features that can be designed around. In fact, they frequently were and are designed around. Even today in states with more stringent feature based assault weapon bans, like California, there exist so called “featureless” firearms which are perfectly legal and not objectively worse for killing people than assault weapons. Now we could try an assault weapon ban again and again have no impact on crime… or we could recognize that semiautomatic centerfire weapons are undeniably the arms of choice in a militia. Police and military forces all over the world use semiautomatic (or fully automatic) centerfire weapons almost exclusively. As such, it makes more sense to more stringently regulate all semiautomatic centerfire weapons, not just a certain subset with specific cosmetic features. At the same time, we can breathe new life into the militia concept described by the Second Amendment to the United States Constitution, even make the militia well regulated.In the United States, we currently have an organization called the Civilian Marksmanship Program, a federally chartered corporation whose purpose is:To instruct citizens of the United States in marksmanship;To promote practice and safety in the use of firearms;To conduct competitions in the use of firearms and to award trophies, prizes, badges, and other insignia to competitors.Among numerous other things, the CMP sells M1 Garand rifles. The Garand is a .30–06 semiautomatic battle rifle roughly twice as powerful as common AR-15 or Kalashnikov rifles. The Garand was the primary infantry rifle of the US military during the Second World War and the Korean War. The CMP literally sells them so people can practice target shooting with a weapon of war.Image by Curiosandrelics - Own work, CC BY-SA 3.0, File:M1-Garand-Rifle.jpg - Wikimedia CommonsLet’s take a look at eligibility requirements for the CMP:REQUIREMENTS FOR PURCHASEBy law, the CMP can sell surplus military firearms, ammunition, parts and other items only to members of CMP affiliated clubs who are also U.S. citizens, over 18 years of age and who are legally eligible to purchase a firearm.PROOF OF U.S. CITIZENSHIP:You must provide a copy of a U.S. birth certificate, passport, proof of naturalization, or any official government document (When using a military ID to prove citizenship, must be an E5 or above) that shows birth in the U.S. or states citizenship as U.S.PROOF OF AGE:You must provide proof of age. Usually proof of citizenship also provides proof of age. In those cases where it may not, a driver’s license is sufficient.MEMBERSHIP IN CMP AFFILIATED ORGANIZATION:You must provide a copy of your current membership card or other proof of membership. This requirement cannot be waived. The CMP currently has over 2,000 affiliated organizations located in many parts of the country. CMP Club Member Certification Form- If your CMP affiliated club does not issue individual membership cards, please have the club fill out the CMP Club Member Certification Form and return it with your order.Membership in many of these organizations costs $25.00 or less and can be accomplished online. A listing of affiliated organizations can be found by clicking on our Club Search web page at http://ct.thecmp.org/app/v1/inde.... If you have any difficulty in locating a club, please contact the CMP at 256-835-8455 or by emailing CMP Customer Service. We will find one for you. In addition to shooting clubs, the CMP also has several special affiliates. Membership in these organizations satisfies our requirement for purchase. These special affiliates include: Congressionally chartered veterans' organizations such as the VFW, AL, DAV, MCL, etc. U.S. Military services (active or reserves), National Guard, to include retirees. Professional 501(c)3 law enforcement organizations and associations such as the FOP, NAPO, NSA, etc. The Garand Collector's Association is a CMP Affiliated Club. You can download a Garand Collector's Association Application Form.Note: Club membership IS required for purchase of rifles, parts, and ammunition.Club membership is NOT required for instructional publications or videos or CMP memorabilia.MARKSMANSHIP OR OTHER FIREARMS RELATED ACTIVITY:You must provide proof of participation in a marksmanship related activity or otherwise show familiarity with the safe handling of firearms and range procedures. Your marksmanship related activity does not have to be with highpower rifles; it can be with smallbore rifles, pistols, air guns or shotguns. Proof of marksmanship participation can be provided by documenting any of the following:Current or past military service.Current or past law enforcement serviceParticipation in a rifle, pistol, air gun or shotgun competition (provide copy of results bulletin).Completion of a marksmanship clinic that included live fire training (provide a copy of the certificate of completion or a statement from the instructor).Distinguished, Instructor, or Coach status.Concealed Carry License.Firearms Owner Identification Cards that included live fire training. - FFL or C&R license.Completion of a Hunter Safety Course that included live fire training.Certification from range or club official or law enforcement officer witnessing shooting activity. Complete the CMP Marksmanship Form to signNow your range firing and the required marksmanship related activity for an individual to purchase from the CMP.No proof of marksmanship required if over age 60. Proof of club membership and citizenship required for all ages. NOTE: Proof of marksmanship activity is not required for purchase of ammunition, parts, publications or memorabilia.BE LEGALLY ELIGIBLE TO PURCHASE A FIREARM:The information you supply on your application will be submitted by the CMP to the FBI National Instant Criminal Check System (NICS) to verify you are not prohibited by Federal, State or Local law from acquiring or possessing a rifle. Your signature on the Purchaser Certification portion of the purchase application authorizes the CMP to initiate the NICS check and authorizes the FBI to inform CMP of the result. IMPORTANT: If your State or locality requires you to first obtain a license, permit, or Firearms Owner ID card in order to possess or receive a rifle, you must enclose a photocopy of your license, permit, or card with the application for purchase.As you can see, the CMP eligibility process is quite a bit more involved than the background check system we have now. It seems to have worked for keeping the powerful semiautomatic Garand rifles out of the hands of mass murderers. The last mass shooting on US soil that I know of which involved an M1 Garand was the Kent State massacre and that involved the Ohio National Guard shooting anti-war protesters, not civilians who were sold rifles through the CMP. I haven’t been able to find any records of crimes committed with guns sold through the CMP. I’m sure it has happened at one point in time or another, but the occurrence is so rare that there hasn’t been any documentation. My point is that the CMP has a really great track record in the United States for making sure guns don’t go to bad guys.Since the Assault Weapons Ban of 1994 didn’t have any measurable impacts on crime and the CMP has great results, I propose we extend the CMP eligibility requirements to all semiautomatic centerfire firearms and centerfire magazines with more than ten rounds of capacity. This means only people who meet the listed criteria will be able to buy the types of weapons most useful in a militia which are also the weapons we primarily see used in mass shootings from an FFL. The proposal also effectively introduces a mandatory training and basic competency requirement before individuals can purchase semiautomatic centerfire weapons from a gun store. The inclusion of CMP eligibility for the purchase of centerfire magazine over ten rounds creates a strong incentive for existing gun owners and individuals who purchase firearms through private intrastate sales to get training and join the CMP if they want easy access to centerfire magazines over ten rounds.The word centerfire is really important because there is another class of firearms which use rimfire cartridges.A collection of rimfire and centerfire cartridges, left to right: .22lr (rimfire), .22WMR (rimfire), .357 magnum (centerfire), .30–06 Springfield (centerfire), 12 gauge shotshell (centerfire)Rimfire cartridges aren’t very powerful; they’re mostly used for small game hunting and target shooting. Most countries allow ownership of semiautomatic rimfire rifles with only basic licensing; countries like Canada and the UK don’t even have restrictions on magazine capacity for rimfire rifles. Could they be used by a mass shooter? Sure, anything could, but semiautomatic rimfire firearms just aren’t a threat compared to semiautomatic centerfire firearms or even non-semiautomatic centerfire firearms. Wounds caused by bullets fired from rimfire cartridges are almost always less severe than wounds caused by bullets fired from centerfire cartridges. Very precise shot placement is required for rimfire weapons to instantly kill a person and mass shooters are unlikely to take the time to precisely place their shots.Seen above are four rimfire rifles made by Marlin.Regulating firearms in this way allows new gun owners to hunt, shoot targets, and defend themselves using semiautomatic rimfire or manually operated firearms. If new gun owners want easy access to semiautomatic centerfire firearms which are useful in a militia context, they can join the CMP, effectively becoming a member of a well regulated militia, after demonstrating themselves to be competent and well trained.I have some final thoughts on the CMP related proposal before moving on to the next topic. CMP eligibility introduces additional layers of human interaction between people and semiautomatic centerfire weapons and centerfire magazines over ten rounds. Barring major advances in mental healthcare and adjudication in the United States, layers of human interaction are the best way for red flags to be raised about somebody who might want to kill large numbers of people with a firearm. Additional layers of human interaction also introduce a larger hurdle for straw purchasers, people who buy firearms for people who can’t pass background checks because they’re ineligible to own firearms. Additional layers of human interaction make law enforcement investigations slightly easier as well.At the moment, laws, standards, and permits for carrying concealed handguns vary wildly. Some states have no requirements while other states functionally don’t allow anybody except police officers to carry handguns in any way. While the percentage of the US population which actually carries handguns regularly, concealed or openly, is relatively small, those who do carry handguns regularly can often face great legal peril for no particularly good reason when crossing state lines. At the same time, it would be good for the public to know that people carrying concealed handguns are actually competent and not a hazard to the public. In essence, a balance would be preferable to the extremes which currently exist.I propose creating an national permit for carrying concealed handguns in any state. Police officers already enjoy something similar to this. The permitting process should include a standardized class which can be taught by police officers or other qualified instructors. Before attending the class, applicants should undergo a background check. Among other things, the class should cover the legal use of deadly force, safe firearms handling practices, and conflict deescalation practices. Then applicants should be given a written test on the subjects. If the applicants pass, they should then undergo a practical handgun handling and shooting competency test. If applicants are able to both handle handguns safely and shoot accurately, they will then be issued a carry permit which is valid for a certain number of years; three to five years seems reasonable. If applicants fail either test then they go home without a permit and can retake the whole class the next time it is offered if they still wish to carry a concealed handgun.
-
Have you ever had your blog content stolen?
Sadly, the internet is rampant with clicky-fingered bloggers and writers ready to cut and paste content from your website on to their own without permission. Luckily, if you find your content has been posted online without your permission, there are ways to deal with the theft (and it is not my bruiser cousin Michael Corleone). Here’s an abbreviated version of an article posted on my blog Sidebar Saturdays outlining what can be done. The Case Of The Stolen ContentFirst, determine if the unauthorized use is considered “Fair Use” under the copyright laws. The copyright laws permit use of your copyrighted work without permission for things like criticism, commentary, news reporting, educational, and research purposes. If you want to learn more about fair use, see this article on PhotoAttorney.If you believe the use of your work is not considered “fair use,” then begin the process of having the infringing content removed.1. Send a cease-and-desist emailBefore you go all formal-copyright-ballistic on the person who has copied your content, send them a please-remove-my-content email first. Simply state in the email you are the copyright holder of the content in question and have not given them permission to use it. Provide a link to your content that has been stolen, the date it was published, and why you are the copyright owner (author, work-for-hire, etc). Then give a time frame by which the stolen content should be removed from their site or you will file a formal complaint (24-48 hours is usually enough time). The tone should be polite, direct, and business-like (without blustery). This process usually works (often without a reply).2. Send a takedown complaintIf a polite email gets you zippo traction, the next option is to take advantage of The Digital Millennium Copyright Act. The DMCA is a law that, among other things, extends the copyright laws and penalties to digital media and the internet. These provisions provide a process for the removal of infringing content, what most call “takedown notice” procedures.First, file a complaint (the “takedown notice”) with the service hosting the website with the infringing content. The complaint is a nicely worded request to the hosting service to remove the unlawfully copied content from the website in question. In addition, you can also send the notice to search engines like Google and Yahoo. Website hosting services and internet search engines have policies that outline the removal of copied content. It is a requirement per the DMCA if they want to avail themselves of the “Safe Harbor” protection (see below). Here are two examples of policies for legal removal requests: one for Google, and the other WordPress.If the website host has no takedown notice form to fill out, use one of these sample takedown notices: IPWatchdog, The Electronic Publishing Industry Coalition, or Innovation-To-Profits.These forms or letters are simple to fill out or write, and contain the following information:1. Description of your copyrighted work being infringed and where it is located (website URL);2. Identification of the infringing content and where it is located (website URL);3. Your contact information — name, address, telephone, email address;4. A statement that the copyright owner (you, or the agent authorized on your behalf) did not authorize the infringing use;5. A statement the information in the takedown notice is accurate; and6. A signature of the copyright owner or person authorized to act on the owner’s behalf.Once the hosting service has been properly notified via a complaint, they have two choices.1. Technically, the service provider is infringing the copyright laws by hosting a website with pilfered content. But the DMCA provisions provide them with immunity from copyright infringement lawsuits, something called “Safe Harbor” under the copyright laws, provided they take certain steps. They must take reasonable action to remedy the infringement by removing the infringing content. Failure to do this means loss of immunity. Invariably, when presented with the potential of a complex copyright lawsuit or avoiding liability, the web hosting service will almost always comply with a takedown notice demand.2. If the web-hosting service or search engine does not remove the infringing material, and instead believes the complaint was filed in error, they can respond to the complaint, refuse to remove the content, leaving you to pursue a copyright infringement action.If the material is taken down, the website host will notify the person who posted the infringing material that they have received a takedown notice. The person accused of the infringing act, can then file a counter-notice to dispute the allegations. The website host will then consider the circumstances and if the copyright owner has not initiated formal legal proceedings in ten days (which hopefully will not be needed), the website host will restore the content as required by the DMCA.One thing worth noting, if you feel you’ve received a takedown notice by someone seeking to silence critiques or other unwanted content (which does happen by overzealous free speech squelchers), dispute the notice and request the website host to repost your content.What not to do?The Shame ApproachIf you want to look petty, resort to shaming the infringer by blogging on your website or posting comments to your Facebook groups about how horrible the person is for copying your material. Shaking your internet blogging finger at the person will only inflame the situation, and may, depending on how deep you go into angry-Wolverine mode, set you up for a defamation lawsuit. (If you want to know more about defamation, see my earlier post on Sidebar Saturdays).Other things to consider?Duplication Detection SoftwareIf theft of your content happened once, it will happen again. Be proactive. Set up a search for stolen content using duplication detection software. Here are a few tools worth checking out.1. Google Alerts scans the internet for your stolen content, then notifies you. The great thing about this tool, it is free.2. There are also other sites with duplicate content detection software that are free, like SEO Review Tools, Article Checker, Duplichecker, and Plagiarisma.3. Copyscape also searches for duplicate content, but unlike Google Alerts and the others above, it requires a fee.4. Another premium services is Content Rescue.Trackback and Pingback NotificationsThese alerts do not really inform you if your content has been stolen, but they do notify you if someone is commenting on your content (trackback), or they are linking to your content (pingback) from their blog or website. Here is a brief article about the difference between the two notifications. Be aware that trackback and pingback notifications tend to be mostly spam, so moderating these notifications to look for someone who might be copying your content without your permission can be laborious and not worth your trouble.We writers work hard at creating content. No one should be allowed to take credit for our efforts and words. Unfortunately, our cut-and-paste internet world encourages content theft. Thankfully, the copyright laws provide relatively easy (but somewhat time-consuming) measures for protecting your creative content.
-
What are some must have Android apps?
Edit: I wrote this answer for “must have Android apps” but these are same apps which have changed the way I used to live my life. Each and every App has helped me in one or the other way. I hope you will also find them helpful and a bit life changing. So here is the list: 10. Psiphon For those who use WiFi with proxy settings. So Psiphon bypasses and tunnel the websites or app through a different IP Address. 9. Mirror It's a simple app to record your mobile screen. Based on the concept of CamStudio in PC where you can record your screen, Mirror offers recording of your Mobile screen. 8. NTES- National Train Enquiry System If you are from India and you want to know the running status, cancelled train (partial or fully), Live Station and other features, this App is a must have. 7. VOLT Simple but effective for those who want to learn new vocabulary. That's too obvious, then why not others? Coz here you get the “memory key” which helps you relate the words and easier to remember them. 6. Parchi It a note making app. But here’s a catch. You can view, review, edit and add right from your lockscreen without need to open the app. Isn't that amazing! I personally find this app very useful. 5. edX If you are student or a learner who wants learn something new everyday, and cannot afford to go in the prestigious institutions like MIT, Harvard University, Cambridge, IITM, etc ten it is a must have app. Enroll yourself in any course and Bazinga!! You are ready to learn from the most amazing professors. Similar to edX, we have Coursera. 4. Walnut Manage your expenses on your finger tips. Its easier then that. It shows you your monthly expenditure, ATM locations, bill remainders and many more features. Its a must have app. 3. CamScanner Everyone doesn’t own a scanner but most of us have camera. So click the pic, upload to CamScanner and voila you are done. You have the scanned copy of your documents, notes, Marksheet and upload them on your DigiLocker. 2. inshorts Till now you all must be knowing this app. The tagline is also simple “News in 60 words” and trust me it is worth having. In this “I don't have time” world, you need news to be fast and accurate so here it is. 1. DigiLocker If you have this app then you don’t need to carry your personal documents like driving license, Adhar card, voter ID card, or even your Marksheets. Keep them safe in actual locker and leave the rest to your DigiLocker. And the best part is that it is acceptable as the original ones at every governmental or non governmental institution because it is developed under Digital India initiative. That's it for the day. Thank you and Enjoy !!! Update 1: Today I came across two new apps which I found useful. Hope it would help you all. 1.Forest : Stay focused Features • A self-motivated and interesting way to help you beat phone addiction • Stay focused and get more things done • Share your forest and compete with friends • Track your history in a simple and pleasant way • Earn reward and unlock more tree species • Customize your whitelist : Leaving Forest and using apps in whitelist won’t kill your tree. 2. Swachh Bharat Toilet Locator Swachh Bharat Toilet Locator is specifically useful for Indians who're committed for Swachh Bharat. Update 2: So I am back with yet another interesting app for you all. And trust me it is worth hanving. You are bored just go through it and kaboooom !!! You are into a black hole. Enjoy the ride. 3. Curiosity It is the latest app I installed but got addicted to it. It’s exactly works like its name, generates a curiosity which inturn increases your knowledge. It covers a large field of scope from Humanity to science to faith and many more. This app deserves more snapshots but why to increase the length of my answer. Comment below if you think the list should be updated? Thank you.
-
What is the strongest fictional metal or material? Why?
Unobtainium: They just don't make it like that any more.Since the first tales of gods and myths, there have been legends of devices crafted, machines made, engines imagined that have been considered the strongest, most powerful, most durable devices in creation. It is the cornerstone of many such tales.And since everyone of them has some legend where their smiths created the ultimate weapon, comparing them is basically a fool's errand. So rather than engage in random and useless comparison, let's travel through myth, legend, storied lore, four colored wonders, as well as far-flung futures and see some of these mythically-indestructible materials or devices.Legendary Mythic MetalsOrichalcum (variously spelled orichalcon, orihalcon or orichalc): a metal first appeared in Plato's version of the Atlantis myth. The name means "mountain copper" in Greek, and it, indeed, often appears the color of copper or bronze. Orihalcum's properties vary heavily from source to source: sometimes its schtick is strength, sometimes it's high value, sometimes it's magic resistance, sometimes it's room-temperature superconductivity. Sometimes it floats.Atlantis : a legendary city which was reputed to have sank beneath the waves in ancient times.Cold Iron (variously called cold steel, wrought iron, magnetic iron and so on) is the traditional bane of The Fair Folk. Precisely what constitutes cold iron varies from source to source, such as being forged without heat, forged by hand, being ferromagnetic, possessing trace amounts of iridium, literally being cold, and so on. In some legends being struck with iron had a poisonous effect on the Fey, in some, even being in the same area as cold iron could be dangerous.Adamant, any impenetrably or unyieldingly hard substance; a legendary stone of impenetrable hardness, formerly sometimes identified with the diamond.Origin of adamant: Middle English, Old French, Latin, 900 AD. before 900; Middle English < Old French adamaunt < Latin adamant-(stem of adamas) hard metal (perhaps steel), diamond < Greek,equivalent to adamant- verbal adjective of damân to tame, conquer; replacing Old Eng. athamans (< Medieval Latin) and Middle English aymont < Middle French aimant < Vulgar Latin *adimant- < LatinAdamant in the Bible(Heb. shamir), Ezek. 3:9. The Greek word adamas means diamond. This is not referred to, but corundum or some kind of hard steel. It is an emblem of firmness in resisting adversaries of the truth (Zech. 7:12), and of hard-heartedness against the truth (Jer. 17:1).Legendary Indestructible WeaponsLegends abound with indestructible weapons. Here are just a few of the more well-known magical swords.Excalibur:Having many names and sometimes confused with the Sword in the Stone, the legendary Excalibur was often referred to as a Blade of Light.Impossibly light and durable, having Excalibur and its attendant scabbard made a warrior a killing machine unable to die from his wounds.Inspiration of Medieval Language & Literature: The Song of Roland (Batlle of Roncesvalles Pass, 778)DurendalDurendal (most likely from the French "durer," "to endure") is the sword of Charlemagne's paladin Roland in the literary series known as the Matter of France.In The Song of Roland, Durendal is said to contain within its golden hilt one tooth of Saint Peter, blood of Saint Basil, hair of Saint Denis, and a piece of the raiment of the Blessed Virgin Mary, and to be the sharpest sword in all existence.Roland attempted to destroy the sword to prevent it from being captured by the attacking Saracens but Durandal proved indestructible, so he hid it beneath his body along with the oliphant, the horn used to alert Charlemagne.In the poem, Roland uses the sword to hold off a hundred-thousand-strong Muslim army long enough for Charlemagne's army to retreat into France.KusanagiKusanagi-no-Tsurugi (草薙の剣?) is a legendary Japanese sword and one of three Imperial Regalia of Japan. It was originally called Ame-no-Murakumo-no-Tsurugi (天叢雲剣?, "Sword of the Gathering Clouds of Heaven") but its name was later changed to the more popular Kusanagi-no-Tsurugi ("Grass Cutting Sword").Found in the tail of a great beast by the god Susanoo-no-Mikoto it was presented to the goddess Amaterasu to settle an old grievanceIn the reign of the Twelfth Emperor, Keikō, Ame-no-Murakumo-no-Tsurugi was given to the great warrior, Yamato Takeru as part of a pair of gifts given by his aunt, Yamato-hime the Shrine Maiden of Ise Shrine, to protect her nephew in times of peril.These gifts came in handy when Yamato Takeru was lured onto an open grassland during a hunting expedition by a tsignNowerous warlord. The lord had fiery arrows loosed to ignite the grass and trap Yamato Takeru in the field so that he would burn to death. He also killed the warrior's horse to prevent his escape.Desperately, Yamato Takeru used the Ame-no-Murakumo-no-Tsurugi to cut back the grass and remove fuel from the fire, but in doing so, he discovered that the sword enabled him to control the wind and cause it to move in the direction of his swing.Taking advantage of this magic, Yamato Takeru used his other gift, fire strikers, to enlarge the fire in the direction of the lord and his men, and he used the winds controlled by the sword to sweep the blaze toward them. In triumph, Yamato Takeru renamed the sword Kusanagi-no-Tsurugi (lit. "Grasscutter Sword") to commemorate his narrow escape and victory.Super-metals of the DC UniverseKryptonianIn the Silver Age of the DC Universe, Krypton was one of most sophisticated worlds in the DC Universe. A world so incredible that anything created there was virtually indestructible once it was under a yellow sun. (Don't think about it. The writers of the era didn't and it was fine.)Superman rocket he came to Earth in was was undamaged upon traveling across space and it delivers baby Kal-el to Earth without a scratch despite its crash landing.Martha Kent was said to have unwoven the fabrics he was wrapped in and rewoven them into his only costume. The costume was indestructible except to Kal-El's heat vision, which was how she was said to have cut the material, when necessary.These two pages are from Superboy v1 #169, October 1970.In this version of the character, baby Kal-El was so hard on his clothing due to his powers manifesting as a child, he was unable to wear anything except materials woven from those fabrics. (I am not making this up.)This explanation was made as part of a series called the Superboy Legend. This was a common thing done during the period because the comics were both numerous and often had unconnected (and sometimes conflicted) stories. This was one of the early attempts to help readers keep up.This was not an imaginary story. It was written in the canon to explain how Superman's costume came to be nigh-invulnerable. The above pencil art is by Superboy artist at the time, Bob Brown, with inks by the famed Wally Wood. Some of the illustrations here, particularly the sequence where Pa shoots and blows up the blankets, are adapted from stories published in much earlier issues of Superboy.Since his costume and cape were practically indestructible, Superman's used his invulnerable cape in a number of ways in early comics.He would use his cape to protect people near him. In this case, molten lava didn't land on Miss Lane, which I am certain she considered a good thing.Superman could use it to hold dangerous materials, toxic chemicals or to protect innocents from a rain of bullets when a broad chest wasn't quite broad enough. It was pretty handy to have around when a nuclear weapon had to be contained, too.He also used it to protect passengers from the effects of friction from his passage through the atmosphere at super-speed. He would also wrap passengers, both to protect them and to maintain the anonymity of his Fortress of Solitude, in the Arctic.Superman Airlines: It's fast. It's cheap. But the accommodations make "coach" seem absolutely spacious compared to flying "mummy-wrapped."Supermanium, named for its inventor, was introduced in World's Finest #41 (Jul-Aug 1949), a prison created to contain the menace of Brainiac.According to Superman (Volume 1) #167, Superman forged it out of the heart of a star, which implied its durability was related to its molecular density.It would also make it the heaviest prison anywhere since collapsed stellar matter would be incredibly dense and highly radioactive...Supermanium's more famous appearance was in the emergency vehicle Superman created when the threat of losing his powers from a nearby red sun supernova required he create his most inauspicious vehicle, the Supermobile. Yes, it has robotic arms with super-strength and it can replicate Superman's vision powers and has an onboard computer and television.This is the Supermobile. Don't think too much about it. You'll forget it eventually. Almost every comic reader has, at least up till now. Even Superman fans pretend it didn't happen.From the isle of ThemysciraAmazonium was the name of a metal used for the construction of Wonder Woman's Bracelets of Submission. These bracelets, created by Aphrodite were to remind them of the cruel submission the Amazons suffered under Heracles. In the classic tales of Wonder Woman, binding the bracelets together removed an Amazon's abilities.The bracelets have thus far proven indestructible and able to absorb the impact of incoming attacks, allowing Wonder Woman to not only deflect automatic weapon fire, energy blasts and other projectile weaponry (Wonder Woman Vol. 1 #52, 1952)Speaking of Wonder Woman, her golden lasso was reforged from the Girdle of Hera and reputed to be all but indestructible. While the material used for its creation is never named, its magical powers include immediate submission to the will of the wielder, the ability to force the person entangled to tell the truth and the ability to change its length to whatever Wonder Woman needs it to be.In the current era of the DC Universe, (New 52) Wonder Woman is a demigod and her bracers are still indestructible (as well as a whole lot heavier) and used to bind her godlike powers, allowing her to remove them and become more powerful and more uncontrolled as long as they are removed.New Wonder Woman is scary. Really, really scary.Modern depictions of Wonder Woman indicate her sword and shield are both god-forged weapons, made by the smith-god Hephaestus and are (by his admission, alone) indestructible. Granted, there is no way to tell for certain but all of his devices are incredible durable and in the case of Wonder Woman we have seen her use said armor and weapons against other powerful magical beings such as Ares and Hades to good effect. So we can safely assume a great degree of durability due to their magical enhancement and manufacture. Did I mention it was sharp enough to carve atoms apart?It can cut Kryptonians too. Ask Faora and Zod. I would say it’s plenty sharp if not completely indestructible.ThanagarNth Metal (also called ninth metal) is a special metal found in the DC Universe. Native to Thanagar, the home planet of Katar Hol and Shayera Thal. The material possesses a number of special abilities and can take on both mystical and technological properties depending on who's using it.Among the unusual properties of Nth metal is the ability to negate gravity, allowing a person wearing an object, such as a belt, made of Nth Metal to fly. In addition, Nth metal also protects the wearer from the elements and speeds the healing of wounds, increases their strength, and protects them from extremes in temperature.Hawkgirl's mace emitted an energy field which disrupted technology and magical energies.In its animated appearance in Justice League and Justice League Unlimited, Nth metal is transuranic iron with an atomic number of 676, possesses innate anti-magical properties, is hyper-conductive and is able to invert mesons and gravitons. Hawkgirl could us it to disrupt magical attacks and magical beings.Earth (You know what it looks like)Promethium is the name given to two metal alloys: "Depleted" and "Volatile" Promethium.Depleted promethium was invented and patented by Steve Dayton of Dayton Industries. Promethium alloyed with titanium and vanadium it forms a nearly-indestructible metal."But son, I made you out of promethium, the strongest man-made metal on Earth!" Okay, Cyborg didn't take to his condition very well in the beginning.The weapon-master, Arsenal (formerly Speedy, the archer sidekick of Green Arrow), wore protective armor which comprised depleted promethium armor. The metallic components of the Justice League member Cyborg (Victor Stone), are made from depleted promethium. Victor Stone's limbs were capable of exercising superhuman strength and durability.He got better. He's a member of the Justice League. Attitude adjustment!"Volatile" Promethium is capable of absorbing energy in proportion to its mass without loss of efficiency. Depending on the volume of the material, it can be used to generate and absorb a near-limitless amount of energy.Both metals are seemingly difficult to manufacture and thus supplies are limited. Deathstroke, the Terminator, uses volatile promethium in his weapons and has been known to charge them before his missions adding to their deadly profile.30th Century, Legion of SuperheroesWelcome to the 30th century. So clean. So sterile. No trees, no grass. No soul...Inertron is a fictional metallic substance found in the DC Comics Legion of Super-Heroes universe. It is the hardest, densest substance in the DC universe, and is often used by the Legion of Super-Heroes in the 30th century. The first mention of inertron was in Adventure Comics #336.Inertron is frequently described as indestructible and impenetrable, but this applies to beings and technologies based in human strength norms. Kryptonians and Daxamites have been show to be able to break inertron if they push themselves to the limits of their strength.However, reinforced inertron structures (like prisons) can resist even their formidable strength. Karate Kid once managed to, using his formidable super-martial arts techniques, to break a set of shackles formed from inertron.A strange fact: Inertron has been eaten by 30th century residents of Bismoll of whom Matter-Eater Lad is a known representative of the species. As you can probably tell from his name, he is able to somehow, inexplicably, and I mean never to my scientific curiosity or satisfaction consume any kind of matter, at superhuman speed, without waste products, or surplus energy output while retaining a human shape in all overall appearance.The Silver Age was an age of wonders. You wonder what they were using. You wonder how long they were high. You wonder how these books made it past an editor with a straight face. An age of wonders...A member of the Legion of Unfortunately Named Heroes, Matter-Eater Lad's signature power was eating anything between him and freedom.Matter-Eater Lad once ate inertron. The most indestructible metal in the known universe. He also ate the indestructible, miraculous Miracle Machine. This was the first time he ate something that didn't agree with him.See kids, even a lame power like matter-eating can come in handy to save the universe under the right conditions. I know this is what you're doing when you think of a superhero based on this idea. I look like this when I think about the Bismolleans.How do you imprison Bismolleans? Are they a society of perfectly well-adjusted non-criminal citizens?Do Bismolleans need toothbrushes? I mean do they even have teeth? What exactly happens from inside their gumline to their "digestive tract?"Do they use antacids, er...anti-radioactives when they have an upset "whatever passes for their super-nuclear furnace" region in their mouth?Screw that: What kind of atomic nightmare is taking place in side of Bismolleans? Are they most radioactive members of the United Federation of Planets?Why aren't we powering our star-cruisers on directed energy-Bismollean power supplies? (Besides the inhumanity and monstrous reality of such an incredibly powerful energy source running on garbage and Bismollean misery...) How do we know the UFP doesn't already run this way?Charlton Universe (now a subset of the DCU)Shazamium, Marvelium and Sivanium: highly adaptable and mutable metal capable of storing fantastic levels of magical energy. Used in numerous schemes by the nefarious Dr. Sivana.The largest supply of this strange magical metal, was held by the wizard, Shazam. First appears in Captain Marvel #100.Ancient Earth TechHumans went from primitive stone tools to space age metallurgy over a period of 200,000 years.Those periods are often broken up into the Stone Age, the Bronze Age, the Iron Age and the Industrial Age, which takes the best of all of the previous technologies.I focused on weapons because that seems to be where human innovations almost always seem to be highly focused and result oriented. (Such a sad statement...)Weapons without MetalBronze Age Swords (Introduction)Iron Age swordsMaking Damascus SteelJapanese SwordsmithingModern MetallurgyModern metallurgy has taken the knowledge of previous eras and created using new discoveries on the periodic table to create new and harder and stronger metals than ever before.Maraging steels are used in jet enginees and other technologies needing strength, durability and heat tolerance.Maraging steelsMaraging steels (a portmanteau of "martensitic" and "aging") are steels (iron alloys) that are known for possessing superior strength and toughness without losing malleability, although they cannot hold a good cutting edge. Aging refers to the extended heat-treatment process.These steels are a special class of low-carbon ultra-high-strength steels that derive their strength not from carbon, but from precipitation of intermetallic compounds. The principal alloying element is 15 to 25wt.% nickel.Secondary alloying elements are added to produce intermetallic precipitates, which include cobalt, molybdenum, and titanium.Inconel Exhaust ManifoldInconelInconel is a family of austenite nickel-chromium-based superalloys. The name is a trademark of Special Metals Corporation, a wholly owned subsidiary of Precision Castparts Corp.Inconel alloys are oxidation and corrosion resistant materials well suited for service in extreme environments subjected to pressure and heat. When heated, Inconel forms a thick, stable, passivating oxide layer protecting the surface from further attack.Inconel retains strength over a wide temperature range, attractive for high temperature applications where aluminum and steel would succumb to creep as a result of thermally induced crystal vacancies. Inconel’s high temperature strength is developed by solid solution strengthening or precipitation strengthening, depending on the alloy.An extremely hard metal, this tungsten rotary burr set is used to shape softer substances (meaning anything that isn't tungsten...) Tungsten carbide burr sets get excellent ratings from the craftsman crowd.Tungsten carbideTungsten carbide (chemical formula: WC) is a chemical compound (specifically, a carbide) containing equal parts of tungsten and carbon atoms.In its most basic form, tungsten carbide is a fine gray powder, but it can be pressed and formed into shapes for use in industrial machinery, cutting tools, abrasives, armor-piercing rounds, other tools and instruments, and jewelry.Tungsten carbide is approximately two times stiffer than steel, with a Young's modulus of approximately 530–700 GPa, and is much denser than steel or titanium.It is comparable with corundum (α-Al2O3) in hardness and can only be polished and finished with abrasives of superior hardness such as cubic boron nitride and diamond powder, wheels, and compounds.TitaniumTitanium can be alloyed with iron, aluminium, vanadium, and molybdenum, among other elements, to produce strong, lightweight alloys for aerospace (jet engines, missiles, and spacecraft), military, industrial process (chemicals and petro-chemicals, desalination plants, pulp, and paper), automotive, agri-food, medical prostheses, orthopedic implants, dental and endodontic instruments and files, dental implants, sporting goods, jewelry, mobile phones, and other applications.The two most useful properties of the metal are corrosion resistance and the highest strength-to-density ratio of any metallic element. In its unalloyed condition, titanium is as strong as some steels, but less dense.There are two allotropic forms and five naturally occurring isotopes of this element, 46Ti through 50Ti, with 48Ti being the most abundant (73.8%). Although they have the same number of valence electrons and are in the same group in the periodic table, titanium and zirconium differ in many chemical and physical properties.Super Metals of the Marvel Universe (Earth-616)Marvel's canon Earth-616 is rife with imaginary metals and metallic alloys. Most of these have nothing to do with real science and everything to do with comic hyperbole.The short list includes:Proto-Adamantium: The adamantium-vibranium found uniquely within Captain America's shield (now with added Uru!) A device so unusually durable, it has only been broken a handful of times in its entire existence.In any case where it shouldn't have been broken, it was later retconned and a facsimile was being broken instead. It has only failed against magical beings who were wielding the Odin-force, an all-powerful magic, and the source of the Asgard's mystical might. The shield also failed against the Thanos when he was using the Infinity Gems.The shield's greatest strength is its nearly immutable nature and resistance to being damaged or changed. The process used to create adamantium requires the material be brought together, shaped and within a fixed amount of time before setting.The process used to create Captain America's shield was similar to the normal process of adamantium development with the inclusion of vibranium. The process was lost and therefore unable to be repeated.I accept this is the origin of Captain America's shield BUT:Thanks to a sleepy scientist and a time traveler from the future...I mean what we are to expect, some vibranium found its way into the secured locked lab when it wasn't there before?And with the mysterious addition of vibranium, we create a device which has been at the center of dozens of temporal events which changed the future.Nobody, Tony Stark, Reed Richards, or Doctor Doom have tried to figure out why they can't recreate Captain America's shield because...what? It would give Stark or Doom the perfect impenetrable armor, resistant to everything in the universe?Why wouldn't Reed Richards want to sit around for a few weekends with Cap's shield and learn how it was made so he could make everything he wants to keep COMPLETELY INVULNERABLE? Isn't that worth a weekend or two, Reed?When you can't get Proto-Adamantium (and you can't, I tried), you end up with the next most amazing thing: Adamantium.Adamantium is incredibly hard to come by, can be used to coat normal metals to enhance their durability as well. Almost impossible to make on Earth-616, process is limited to a select few corporations. Most notably found in Ultron's nigh-indestructible carapace. It can also be found coating Doctor Octopus' tentacles increasing their durability and strength.Yes, this android which is beating both Thor and Wonder Man like ugly step-children. Ultron is coated in Adamantium making his super-strength even more formidable, because he can put his back into every swing. No stress fractures on him...no strings either.Secondary Adamantium: When you can't afford real adamantium, you make, buy or steal this. Nearly as good, far more durable than normal metallic alloys, very, very expensive.Adamantium Beta: Wolverine's Skeleton and claws are made from this. Unique to Wolverine or any mutant fitted with secondary adamantium which is somehow altered by their regenerative properties (There's at least a couple - Lady Deathstrike, Sabertooth - see, I named two.) Don't think any more about it. Impenetrable metal worn down by regeneration powers... Here you go ladies, a picture of Hugh Jackman as Wolverine.Vibranium A: A metallic substance which absorbs vibrational energy, once found exclusively in the African kingdom of Wakanda. It was of extraterrestrial origins. The Wakandan stockpile was recently destroyed before Marvel's soft reboot in Secret Wars 2015.While not as durable as Adamantium, it is a very resilient alloy and can be very durable particularly when it comes to absorbing incoming kinetic energy attacks. Vibranium A makes for great body armor and can allow a properly fitted wearer to fall great distances without injury. Black Panther once wore a uniform fitted with a variety of vibranium technologies for his protection.Vibranium B: Also known as anti-metal, which destroys metallic bonds even in adamantium. Black Panther used to have claws made from it. This material was found exclusively in the Savage Land.Uh. I forgot to mention the Savage Land has dinosaurs. And mutants. And Humans running around with saber-toothed beasts. Some guy name Ka-Zar...In the Marvel Cinematic UniverseCaptain America's shield in the Marvel Cinematic Universe (Earth-199999) is NOT indestructible; far from it.Created by Howard Stark from a vibranium alloy, the MCU shield is very tough but nowhere near as durable as Captain America's shield in the comics. With sufficient force or continued bombardment, a shield composed of only vibranium can be destroyed as the vibranium destabilizes.VibraniumVibranium is not as hard or dense as Adamantium, but it is still very durable. The apparent observable vibratory rate of the molecules of the Vibranium itself does not noticeably increase when the Vibranium absorbs mechanical energy.The outside vibratory energy is stored within the bonds between the molecules making up the Vibranium. As a result, a chunk of Vibranium which had absorbed a considerable amount of vibratory energy would be exceedingly hard to demolish.If enough force were were applied to this chunk to smash it, the Vibranium would explode, releasing much of the absorbed energy in a fashion similar to a large multi-megaton bomb.Captain America's MCU shield is composed singularly from a vibranium-metallic alloy. Durable, tough, damage resistant, capable of taking a hit from even Mjolnir, but far weaker than the comic version of Cap's shield.Runner-Ups after Adamantium for durabilityCarbonadium: Carbonadium is a resilient, unstable metal that is vastly stronger than steel; think of it as a synthetic and poor man's adamantium, very durable but also radioactively toxic as well. Must have a healing factor to use this metal. Most commonly associated with Omega Red. (above)You might want to duck. Mjolnir coming through!Enchanted uru is not made or normally found on Earth and is both more resistant to damage than normal uru metal but it is not indestructible.It's durable and can be enchanted to be even more damage-resistant but its primary benefit is the ability to bind amazing enchantments to it. Thor's hammer, Mjolnir, is made of from it; hard to come by, even in Asgard, dwarves horde it.The titanic tussle between two titans who terrorize timid tenants: Hercules, Prince of Power versus the Mighty Thor.Adamantine: To be fair to Marvel's Olympians, I will also include Adamantine, the material Hercules' Golden mace is was forged from. In the Marvel Universe, adamantine is a mystical metal capable of being enchanted and having its durability enhanced through mystical/scientific forging by Hephaestus, the smith of the Olympian gods.Iron Man Armors: - composed of metallic and ceramic-enhanced alloys allowing for durability, these armors can have their strength and durability further enhanced by charging it with electrical energies and integrated force fields.Osmium: A real metal, it makes this list because Colossus, the Living Juggernaut's mutant power is to transform into a being composed of an organic or living form of this dense and resilient metal.Cosmically-Enhanced Materials in the Marvel UniverseIn the current iterations of the Marvel Universe, the nature of the most powerful materials would be similar to the nature of the technological capabilities of the species; more advanced species would likely have better metallurgical technologies.In addition to better metallurgy these species may be able to infuse materials with energy, reinforcing the material's strength, resilience and durability.Adding to this mixture, concepts such as nanotechnology, memory materials, programmable matter and other meta-material science means such species have an unknowable advantage over species without such advancements.Their armors may be self-repairing, adaptable to varying environmental conditions on their own and maybe even self-aware, able to compensate against threats without direction from its wearer.Beings who have mastered all of the universes fundamental forces, matter and energy manipulation making them with the proper scientific knowledge to create the penultimate meta-materials. These entities include the Elders of the Universe, the Stranger and the the armor of the Space gods, the Celestials.Galactus, Scourge of Worlds, was ancient when the Universe was new. He forged his current armor from materials in this universe and except for in the presence of matter manipulation entities whose powers rival his own, his armor is impenetrable.Since Galactus imbues his heralds with a segment of the Power Cosmic, they too have some ability to create nearly indestructible materials either as armor or weapons unable to be affected by beings with lesser technologies. This includes the Silver Surfer's surfboard and the ax and armor of Terrax the Tamer.Galactus created the Silver Surfer, so it's safe to say the Silver Surfer is highly resistant to damage, considering his job duties and the potential threats he faces, he needs to be. Skirting black holes, wormholes, and stars, the Surfer's metallic skin is one of the toughest surfaces imaginable.Since Galactus and the Surfer both possess matter transmutation and advanced scientific capacity they can create or alter matter to make the strongest materials in the Universe. Other cosmic beings can likely create similar near-ultimate materials.This may also include unique weapons of the local god-like beings associated with Earth, such as Odin's spear, Gungnir.In the Marvel Universe, just because a particular metal ranks well, does not mean it cannot be damaged. With sufficient force, magic, technology or knowledge, almost anything can trump anything else, hence the reason Thor and the Hulk manage to damage anyone and everyone on this list at least some of the time.RingworldRingworld is a 1970 science fiction novel by Larry Niven, set in his Known Space universe and considered a classic of science fiction literature. Niven later added four sequels and four prequels. These books tie into numerous other books set in Known Space. Ringworld won the Nebula Award in 1970, as well as both the Hugo Award and Locus Award in 1971.General Products Hull:In Larry Niven's fictional Known Space universe, General Products is a Pierson's Puppeteers company which produces various spacecraft components.The most famous (and most profitable) items produced by General Products are General Products hulls, which are advertised as being impervious to anything apart from visible light (as defined by wavelengths visible to any of the species which are customers of General Products), antimatter, and gravity.The hulls are advertised as being capable of passing through the upper atmosphere of a star without damage, although the contents may become overcooked (but see below for a solution to this problem).The company even offers a guarantee that, should anything harm you within a General Products hull as a result of a failure of these specifications, you (or your estate) will receive a very large sum of money ("tens of millions" of "stars" in the event of a death, with a "star" having value roughly equivalent to one United States dollar in the middle of the 20th century).In the history of General Products this indemnity has been claimed only once, by Gregory Pelton, whose hull failed under extremely unusual circumstances (see Flatlander).Scrith:Scrith is the milky-gray translucent, nearly frictionless material that forms the walls and floor of the Ringworld in Larry Niven’s Ringworld.It is said that Scrith was artificially produced by transmutation of matter, and is nearly impervious to most weapons. Scrith absorbs heat and radiation nearly perfectly and can block neutrinos as well as a light year worth of lead.Some amateur scientists postulated Scrith couldn't technically exist since the mathematics to create Ringworld would require Scrith to be stronger than the strong nuclear force! Impossible.This means the Ringworld cannot exist outside of an appropriately-belief suspended environment.Lord of the RingsMithril: was a precious Silvery metal, very lightweight but capable of providing extreme strength in alloys, which was mined by the Dwarves in the deep mines of Khazad-dûm. This was considered a rare gift and extremely strong metal. Highly prized it was rarely seen in hands outside of dwarves.Galvorn: was the shining black metal devised by master craftsman Eöl. It was harder than mithril and nearly impossible to smith by anyone but a master-craftsman. The technique was believed lost when Eöl died.Tilkal: was a unique metal created by the Vala Aulë in the earlier forms of the legendarium.The metal was composed of six different metals that made it extremely strong, hard, bright, and smooth. The light that shown on it and what it was exposed to caused it to vary in color. Only Aulë knew the secret of its manufacture. It was used to bind Melkor for his tsignNowery in the Silmarillion.The Culture (Iain Banks - Consider Phlebas)An artist's representation of the very durable, nearly-living starships of Iain Bank's Culture GSV.General Systems VehicleEach Systems Vehicle was a great space-faring city that represented everything the Culture was socially, technologically, etc.. They built smaller ships, such as General Contact Units, and manned them from their own populations.A General Systems Vehicle (GSV) was the largest and most capable type of Systems Vehicle, and served as the Culture's premier ambassadors. The Culture's capabilities were almost totally mirrored on a smaller scale in a GSV.These titanic vessels house vast populations, factories or defense forces -- each controlled by a trio of extremely powerful artificial intelligences called Minds.These number crunchers do all the heavy lifting while the humanoids in their charge are free to peruse whatever sort of hedonistic or altruistic lifestyle they desire.Star Wars MaterialsWith the lightsaber as the gold standard for damage-dealing in the Star Wars universe, you might be surprised to discover there were numerous metals, compounds and even genetically engineered creatures who could resist a lightsaber's gentle touch.All of these metals, compounds or alloys are resistant to the plasma temperatures of a light-saber, which makes them pretty durable. Most were very rare or expensive and thus found themselves in the hands of soldiers, bounty hunters, warriors and occasionally Jedi and Sith.Lightsaber-resistant materials (Wookiepedia - Star Wars Wiki)Amphistaff: Genetically engineered serpentine creatures that served as the primary anti-personnel weapons of the Yuuzhan Vong.Amphistaffs were one of the most durable objects known, as not even lightsabers could cut through them. When used as a heavy staff, the serpent would endure blow after blow from the Jedi weaponry and remain unfazed.The amphistaff's edge—measured in atoms—slashed through flesh with no resistance. In the blink of an eye, the amphistaff could soften and wind around the lightsaber's blade, its venomous jaws snapping and tearing at the unfortunate victim's face.Because of its organic nature, these creatures were capable of recovering from virtually any wounds. Nigh indestructible, an amphistaff could only be killed by repeated blunt trauma to or removal of the head.Cortosis ore: A very rare, brittle, fibrous material whose conductive properties caused lightsabers to temporarily short out upon contact. This effect made cortosis a useful material for anti-lightsaber melee weapons, though with repeated strikes, a lightsaber could still cut through it. Cortosis, due to its energy resistant properties, was also resistant to blaster fire.Felucian Skullblade: Felucian Skullblades were constructed from the skull and teeth of specific native creatures. These creatures grew trace amounts of Force-reactive crystals, similar to those used in the construction of lightsabers, in their bones allowing weapons constructed from them, when imbued with the Force, to block lightsabers and blaster fire.Mandalorian iron: also known by its Mando'a name of beskar, was a near-indestructible iron ore whose only known source was the Outer Rim world of Mandalore and its moon, Concordia. The Mandalorian warrior culture that inhabited Mandalore mined their planet for beskar, using it in the creation of weapons, armor, and starships, occasionally even selling the rare and valuable metal on the galactic market. A versatile metal, Mandalorian iron could be melded into multiple alloys and forged into various configurations.Mandalorian warriors in trademark armors prepare for their next battle.Neuranium: was a metallic substance used to shield from radiation, and one of the heaviest and densest metals in the galaxy. A millimeter of it could stop most scanners, and it could even temporarily block lightsaber energy. However in order to cover a space as large as a cargo hold, it would be prohibitively heavy and thus inefficient to use.Phrik: was a rare metallic compound that was one of only a few lightsaber-resistant substances known. It was used in the construction of extremely light and durable battle armor as well as melee weapons. On a more extreme scale, at one point in the Galactic Civil War, a container of phrik was able to stay intact when it was on the surface of Alderaan during its destruction. Very rare, very expensive.Songsteel: was an extraordinarily light and luminescent silver metal, used in masterwork swords and staves. The metal was reserved only for the most exquisite of weapons, and was extremely tedious to forge and shape. Songsteel was highly resistant to lightsaber strikes in a manner similar to phrik and cortosis.Ultrachrome: was a metal used as starship armor around the time of the Great Sith War. Silver and superconductive, it reflected blaster and slugthrower weaponry, was heavily resistant to lightsaber attacks, and was immune to metal-eating fungi.Vonduun crab: The vonduun crab was an organism used to shape the vonduun crab armor suits of the Yuuzhan Vong.This list is nowhere near complete..."Pardon the crudity of the model, I didn't have time to paint it or cut it to scale."If you can think of a metal, well-known or interesting artifact or nigh-indestructible technology that should be on this list, write it in the comments with some information on how to find it, what books it came from and if I know anything about it, I will add it to the list. Thanks for reading.
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How to sign a pdf in paint?
How do i setup electronic signature ups?
Get more for Remove Electronic signature Form Safe
- Electronic signature Utah Contract Myself
- How Can I Electronic signature Texas Electronic Contract
- How Do I Electronic signature Michigan General contract template
- Electronic signature Maine Email Contracts Later
- Electronic signature New Mexico General contract template Free
- Can I Electronic signature Rhode Island Email Contracts
- How Do I Electronic signature California Personal loan contract template
- Electronic signature Hawaii Personal loan contract template Free
Find out other Remove Electronic signature Form Safe
- Mn tenant landlord 497312050 form
- Mn conveyancing form
- Temporary lease agreement to prospective buyer of residence prior to closing minnesota form
- Limited warranty 497312053 form
- Letter from tenant to landlord containing notice to landlord to cease retaliatory threats to evict or retaliatory eviction 497312054 form
- Letter from landlord to tenant returning security deposit less deductions minnesota form
- Minnesota quitclaim deed 497312056 form
- Letter from tenant to landlord containing notice of failure to return security deposit and demand for return minnesota form
- Letter from tenant to landlord containing notice of wrongful deductions from security deposit and demand for return minnesota form
- Mn business form
- Letter from tenant to landlord containing request for permission to sublease minnesota form
- Letter from landlord to tenant that sublease granted rent paid by subtenant but tenant still liable for rent and damages 497312061 form
- Minnesota uniform conveyancing blanks 497312062
- Landlord rent paid form
- Release of land from lien in marriage dissolution divorce judgment and decree ucbc form 811 minnesota
- Letter tenant landlord mn form
- Mn deed form 497312066
- Letter from landlord to tenant with 30 day notice of expiration of lease and nonrenewal by landlord vacate by expiration 497312067 form
- Entity joint form
- Letter from tenant to landlord for 30 day notice to landlord that tenant will vacate premises on or prior to expiration of 497312069 form