Download eSignature Presentation Free
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






Advantages of utilizing digital signatures with airSlate SignNow
In the modern digital landscape, the ease of a digital signature is crucial for optimizing document processes. airSlate SignNow provides a comprehensive platform that allows users to generate, distribute, and endorse documents with ease. Featuring an intuitive interface and powerful functionalities, airSlate SignNow aims to boost efficiency and secure transactions for enterprises of all scales.
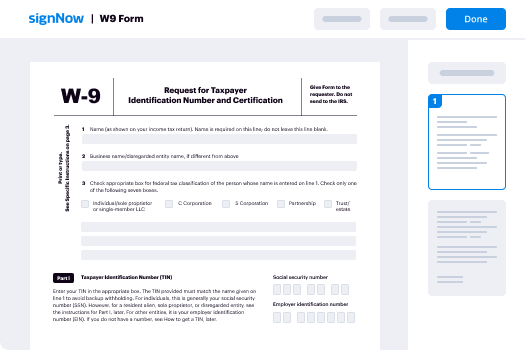
Procedure for creating a digital signature with airSlate SignNow
- Launch your web browser and visit the airSlate SignNow homepage.
- Sign up for a complimentary trial account or log in if you already possess one.
- Select a document that you wish to sign or send for signatures.
- If you intend to utilize this document again, transform it into a reusable template.
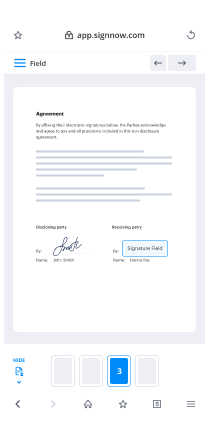
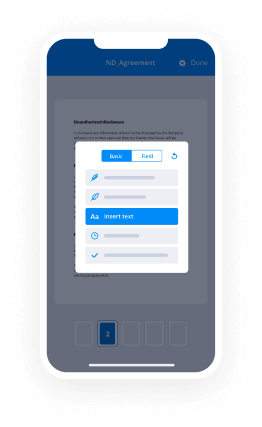
- Open your document and perform necessary modifications, such as adding fillable fields or inserting information.
- Sign your document and create signature fields for your recipients.
- Click 'Continue' to set up and distribute the eSignature invitation.
Using airSlate SignNow not only eases the signing procedure but also enhances your return on investment with its extensive range of features designed to accommodate your financial plan. Its simplicity and scalability render it a perfect option for small to medium-sized enterprises, ensuring you can expand without the complications of conventional signing techniques.
Eager to improve your document signing experience? Initiate your free trial with airSlate SignNow today and find out how simple it is to effectively handle your digital signatures.
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is a digital signature and how does it work?
A digital signature is an electronic equivalent of a handwritten signature that ensures the authenticity and integrity of a document. It uses cryptographic techniques to secure the signing process, making it virtually tamper-proof. By employing a digital signature, businesses can easily validate the identity of the signer and ensure that the document has not been altered.
-
How can airSlate SignNow help my business with digital signatures?
airSlate SignNow offers a user-friendly platform for businesses to create, send, and manage digital signatures seamlessly. With features like customizable templates and automated workflows, it streamlines the signing process, saving time and reducing errors. This makes it an ideal solution for businesses looking to enhance efficiency while ensuring compliance with legal standards.
-
Is there a cost associated with using airSlate SignNow for digital signatures?
Yes, airSlate SignNow provides various pricing plans to accommodate different business needs regarding digital signatures. Our plans are designed to be cost-effective and scalable, offering essential features at competitive rates. You can choose a plan that best fits your budget and requirements, ensuring you get the most value out of your digital signature solution.
-
Are digital signatures legally binding?
Yes, digital signatures are legally binding in many countries, including the U.S., under laws such as the ESIGN Act and UETA. airSlate SignNow complies with these regulations, ensuring that your digital signatures hold the same legal weight as traditional signatures. This compliance helps to provide peace of mind when conducting business transactions electronically.
-
Can I integrate airSlate SignNow with other applications?
Absolutely! airSlate SignNow offers integrations with numerous applications, allowing you to incorporate digital signatures into your existing workflows seamlessly. Whether it's CRM systems, document management tools, or productivity software, our platform ensures that you can streamline processes without disrupting your current operations.
-
What security measures does airSlate SignNow implement for digital signatures?
Security is a top priority at airSlate SignNow. We implement advanced encryption protocols to protect your digital signatures and ensure data integrity throughout the signing process. Additionally, our platform offers features like two-factor authentication and audit trails to enhance security and provide a comprehensive overview of document interactions.
-
How can I track the status of my digital signature requests?
With airSlate SignNow, tracking the status of your digital signature requests is straightforward. Our dashboard provides real-time updates on the progress of sent documents, allowing you to see when a document is viewed, signed, and completed. This transparency helps you manage your signing processes efficiently and stay informed.
-
What is the best invoicing app for small businesses?
SeisoRidh-Billing Acoounting Softwarefor demo click hereKey Features:Multiple Business/Shops:Set up multiple businesses in the application.No restriction on numbers of businesses.Inventory & accounting information is kept separately for each business.Add Location / Storefronts / Ware House:Create multiple locations for your business/shopManage all of them at the same time.Stocks, Purchases, Sell can be tracked differently for locations.Customize invoice layout, invoice scheme for each locationUser & Role Management:Powerful user and role management systemPredefined roles – Admin & CashierCreate different Roles with permission as per your need.Create unlimited users with different roles.Contacts (Customer & Suppliers):Mark contact as customer or supplier or both(customer & Supplier)View details of transactions with a contact.View total of Credit/Debit balance amountDefine pay term and get payment alerts week before the due date.Products:Manage Single & Variable products.Classify products according to Brands, Category, Sub-Category.Add products having different unitsAdd SKU number or auto-generate SKU number with prefixes.Get stock alerts on low stocks.Save time by auto calculating selling price, the system is smart to auto calculate selling price based on purchase price and profit margin.No need to type variations every time, create variation template and use it everytime you need to create variable products.Purchases:Easily add purchases.Add purchase for different locations.Manage Paid/Due purchases.Get Notified of Due purchases week before the pay date.Add discounts & TaxesSell:Simplified interface for selling productsDefault Walk-In-Customer automatically added to a businessAdd new customer from POS screen.Ajax based selling screen – save reloading time.Mark an invoice for draft or final.Different options for payments.Customize invoice layout and invoice scheme.Manage Expenses:Easily add business expensesCategorise expensesAnalyse expenses based on category and business locations with expenses report.Reports:Purchase & Sale reportTax ReportContact ReportsStock ReportsExpense ReportView Trending Products, drill down by Brands, Category, Sub-category, Units and date rangesOther useful feature:Set currency, timezone, financial year, the profit margin for a business.Translation ready.Predefined barcode sticker settings.Create your barcode sticker settingManage Brands, Tax Rate & Tax groups, Units, Category & Sub-CategoryEasy 3 steps installation.Detailed documentation
-
What is a good iPhone invoicing app for a startup marketing company?
Disclaimer: I am the founder of Invoice by Alto.Alto brings desktop-class invoicing and time tracking functionality to mobile devices. The app enables small businesses and freelancers to track billable hours, send estimates and invoices and get paid. Users can choose from five invoice template options to suit their brand images. The Alto Timer companion app makes it possible for users to track billable time on the fly and then bill for it instantly by email. Alto can work for individuals or teams. The app features integration with Stripe, Square and Paypal to make Alto a payment processing app that can collect funds from clients. Integration with Dropbox, Github, and Photos enables the user to reference files, documents, images, code commits and other items needed to support an invoice. AddressBook integration simplifies setup and streamlines the invoicing process. A built-in set of animated visual charts give the user visibility into business statistics.http://www.alto.co
-
What is a good free software for keeping track of invoices and expense for a small business?
Hi,Invoicing and expense tracking is one of the biggest aspects of managing a business and its finances. And yet, small business owners make some grave mistakes when it comes to invoicing and they suffer the actions of their consequences.One such mistake is not investing in a robust cloud-based invoicing software which costs less with a pay-as-you-go model.This cloud-based accounting and invoicing software have invoicing features like:Ability to send invoices anywhere you are using any device,Ability to customize invoices and make them look beautiful to wow the customers.Ability to add multiple payment avenues(net banking, debit card, credit card, payment gateways, etc) within the invoices that saves time.Ability to track unpaid invoices and send automated reminders once the due-date is met and the invoices remain unpaid.Ability to send invoices on a recurring basis.Some of the best invoicing, expense management and overall accounting software today are not free but they offer high bang for buck with their features and support. They are listed below:GiddhQuickbooksZoho invoicesProfitbookBearbookSage
-
What is the best invoicing software that has a mobile app?
Since last 10 years Spectrum POS is one of the best invoicing software that has a mobile app MOBEX for any retail business. A most innovative invoicing software and complete solution to run your business in a better way at your location. According to latest trends & technology, now latest version of Spectrum POS has changed the features in a better performing way and have added new features for more performance. It offers Invoicing, Inventory, CRM, Payments and E-commerce for your business. This invoicing software mobile app works on any hardware including your mobile phone, tablet or lapto...
-
How are cracked versions of software created and why are developers not able to prevent it?
Cracked versions of software are created with the use of debuggers. (A debugger is a special type of software that lets programmers deconstruct their software into its constituent parts for the purpose of finding bugs, and thus de-bugging. Additionally debuggers can be used for reverse-engineering, or to see what is inside the software, to learn its logic. The latter method is used mostly by malware researchers to study what malware (or computer viruses) do on-the-inside. But it can be also used by an attacker to "crack" (or bypass) legal software registration, or at times, to alter normal behavior of software, for instance by injecting a malicious code into it.)For the sake of this example, I will assume that the software that is being "cracked" was compiled into a native code, and is not a .NET or a JavaScript based application. (Otherwise it will be somewhat trivial to view its source code.) The compiled native code is a bit more tricky "beast" to study. (Native means that the code executes directly by the CPU, GPU, or other hardware.)So let's assume that the goal of an attacker is to bypass the registration logic in the software so that he or she doesn't have to pay for it. (Later for lolz, he or she may also post such "crack" on some shady online forum or on a torrent site so that others can "use" it too and give him or her their appreciation.)For simplicity let's assume that the original logic that was checking for the software registration was written in C++ and was something similar to the following code snippet:In this code sample "RegistrationName" and "RegistrationCode" are special strings of text that a legitimate software user will receive after paying for the license. (The name is usually that person's actual name or their email address, and the code is some string of unique/special characters that is tied to the name.)In the logic above, the function named "isRegistrationCodeGood()" will check if "RegistrationName" and "RegistrationCode" are accepted using some proprietary method. If they are, it will return true. Otherwise false. That outcode will dictate which branch (or scope) the execution will follow.So the logic above will either show that registration failed and quit:Or, if the registration code and name matched, it will save the registration details in persistent storage (such as the File System or System Registry) using the function named "rememberRegistrationParameters()" and then display the message thanking the user for registering:A "cracker" will obviously want to achieve the second result for any registration code that he or she enters. But they have a problem. They do not have the C++ source code, part of which I showed above. (I hope not!)So the only recourse for an attacker is to disassemble the binary code (that always ships with software in the form of .exe and .dll files on Windows, and mostly as Unix executables inside the .app packages on a Mac.) An attacker will then use a debugger to study the binary code and try to locate the registration logic that I singled out above.Next you can see the flowchart for a snippet of code that I showed in C++, presented via a low-level debugger. Or, as the code will be read in the binary form after compilation:(For readability I added comments on the right with the names of functions and variables. They will not be present in the code that an attacker could see.)(To understand what is shown above an attacker will have to have good knowledge of the Assembly language instructions for the native code.)I also need to point out that having a disassembly snippet like the one above is the final result for an attacker. The main difficulty for him or her is to locate it among millions and millions of other similar lines of code. And that is their main challenge. Not many people can do it and that is why software "cracking" is a special skill.So having found the code snippet above in the software binary file a "cracker" has two choices:1) Modify (or patch) the binary.2) Reverse-engineer the "isRegistrationCodeGood()" function and copy its logic to create what is known as a "KeyGen" or "Key Generator."Let's review both:The first choice is quite straightforward. Since an attacker got this far, he or she knows the Intel x64 Instruction Set quite well. So they simply change the conditional jump from "jnz short loc_7FF645671430" at the address 00007FF645671418 (circled in red in the screenshots) to unconditional jump, or "jmp short loc_7FF645671430". This will effectively remove any failed registration code entries and anything that the user types in will be accepted as a valid registration.Also note that this modification can be achieved by changing just one byte in the binary code from 0x75 to 0xEB:But this approach comes with a "price" of modifying the original binary file. For that an attacker needs to write his own "patcher" (or a small executable that will apply the modification that I described above.) The downside of this approach for an attacker is that patching an original executable file will break its digital signature, which may alert the end-user or the vendor. Additionally the "patcher" executable made by an attacker can be easily flagged and blocked by the end-user's antivirus software, or lead criminal investigators to the identity of the attacker.The second choice is a little bit more tricky. An attacker will have to study "isRegistrationCodeGood()" function and copy it into his own small program that will effectively duplicate the logic implemented in the original software and let him generate the registration code from any name, thus giving any unscrupulous user of that software an ability to register it without making a payment.Vendors of many major software products understand the potential impact of the second method and try to prevent it by requiring what is known as "authentication." This is basically a second step after registration, where the software submits registration name to the company's web server that returns a response back to the software of whether the code was legitimate or not. This is done by Microsoft when you purchase Windows (they call it "Activate Windows") and also by signNow, and many other companies. This second step may be done behind-the-scenes on the background while the software is running, and will usually lead to cancellation of prior registration if it was obtained illegally.So now you know how software is "cracked".Let me answer why it is not possible to prevent it. It all boils down to the fact that any software code needs to be read either by CPU (in case of a binary native code) or by an interpreter or a JIT compiler (in case of JavaScript or .NET code.) This means that if there's a way to read/interpret something, no matter how complex or convoluted it is, an attacker with enough knowledge and persistence will be able to read it as well, and thus break it.There is an argument though that cloud-based software is more secure, which is true, since its (binary) code remains on the server and end-users do not have direct access to it. And even though cloud-based software is definitely the future, it has some major drawbacks that will never allow it to fully replace your conventional software. To name just a few:Not everyone has an internet connection, or is willing to upload their data online. Additionally someone’s internet connection can be very expensive or too slow to make the software run very laggy.Then there’s a question of distributed computing. For instance, Blizzard Entertainment would never make “World of Warcraft” to fully run on their servers due to immense computational resources needed to render every single scene for every player they have. Thus it is in their best interest to let each individual user’s computer to do the rendering instead.As a software developer myself, I obviously don't like when people steal software licenses. But I have to accept it and live with it. The good news is that there are not that many people who are willing to go extra mile and search for a cracked version of software. The main problem for those who do, is that by downloading a patched executable, or an attacker's KeyGen or a Patcher, they are effectively "trusting" him or her not to put anything "nasty" into it that was not "advertised on the package" (stuff like trojans, malware, or keyloggers.) So the question for those people becomes -- is it worth the cost of the software license to potentially infect your system with a nasty virus?On the other side of the equation, some developers react very negatively to any attempts to steal their software licenses. (I was there too.) They try to implement all kinds of countermeasures -- anything from tricking reverse-engineers, to adding booby traps in the code that may do something nasty if the code detects that it is being debugged, to obfuscating or scrambling the code, to enforcing all kinds of convoluted DRM schemes, to blocking users from certain countries. I personally try to stay away from all of those measures. And here's why:A) Any kind of anti-reverse-engineering tactics could be bypassed by an attacker with enough persistence. So why bother and waste my time when I can invest that time into adding something useful to my software that will make it more productive for legitimate users?B) Some code packers could create false positives with antivirus software, which is obviously not good for marketing of that software. It also creates unnecessary complexity for the developer to debug the software.C) Adding booby traps in the code can also “misfire” on your legitimate users, which will really infuriate them and can even lead to lawsuits.D) Any DRM scheme will probably catch some 100 illegal users and greatly inconvenience 10,000 legitimate ones. So why do it to your good customers?E) Our statistics show that about 75% of all illegal licenses come from China, Russia, Brazil, to name the worst offenders. (I also understand that the reason may be much lower incomes that people have in those countries.) The main issue for us though was the fact that if we enforce our DRM or add some strong registration authentication, many people that wanted to bypass our registration would simply use a stolen credit card number. And we had no control over it. Our system will use it to send them a legitimate license only to have the payment bounce in weeks time. As a result we would lose the money that were paid for the license, plus the credit card company will impose an additional chargeback fee to our account, which may range from $0.25 to $20 per bad purchase on top of the license cost.F) As was pointed out in the comments, some companies may actually benefit from allowing pirated copies of their software. Microsoft for instance gets a lot of free publicity from people using their Windows OS, the same goes for signNow with their Photoshop. That is a good point that I agree with.So my philosophy is now this -- if someone wants to go extra mile and steal our software, go for it! They went this far to do it anyway, so they probably have a good reason. On the positive side there are so many other customers that appreciate the work that goes into creating software that greatly outnumber those that don’t.PS. Thank you for all your feedback! It makes me feel good that the knowledge I shared is useful to others.
-
What are some great tools to use for sales prospecting?
I think that we all agree that the days of manual prospecting are long gone. If you automate your prospecting efforts you can save a lot of time and money, and streamline your whole sales process. But, since there are lots of prospecting tools in the market, it can be hard to figure out which ones are good and which ones you should avoid.I’ll give you a couple of suggestions based on the tools I used.Email Hunter is a decent little program that can extract a list of every single one company email. All you need to enter is a company domain, and you will soon be able to email any person from a company. You can use either its dedicated Chrome plugin, or you can do your search by means of their browser version. This program can come in really handy if you want to find the email of a particular decision maker and get in touch with them directly.HeadsignNow is another interesting tool that offers more options than Email Hunter as it has some advanced search features. This means that you can search prospects based on various criteria such as name, company, title, or website. You can also expect to find your prospects’ social media handles and memorize your search logs.Autoklose isn’t your average prospecting tool, mainly because it offers much more. It’s actually a sales automation platform that can dramatically speed up your sales cycle, and prospecting is just one of the weapons in its arsenal. Apart from automating your prospecting efforts and saving you a tremendous amount of time, Autoklose will make your job and life easier by automating your email marketing efforts, amplifying your follow-ups, providing you with detailed campaign stats and metrics, and streamlining numerous dull, repetitive tasks that have to be done during the sales process.When it comes to prospecting, Autoklose allows you several powerful methods of filling your funnel with quality leads.Upload your own reliable contacts from .CSV files and Autoklose will import the information in the database so that you can make lists according to various parameters, and additionally segment them in order to create customized outsignNow campaigns and improve your open and click-through rates;Connect your Salesforce account and sync the data with Autoklose thus growing your internal database. What’s great about this platform is that it prevents you from sending the same email to the same person twice;Gain access to a huge B2B leads database and find prospects from virtually any industry. I was impressed with the abundance of prospects that I could actually contact. This database is managed by Autoklose’s reliable third-party providers, and it’s absolutely clean and packed with verified, complete, and updated contact information.It’s clear that Autoklose gives you a plenty of prospecting options, and the fact that you can search for your potential customers by using different parameters makes it in a way similar to HeadsignNow, but one of the main and most important differences is that Autoklose provides you with validated data which undergoes a meticulous 50-point data-scrub, meaning that every missing field is filled in, and every email, phone number, address, and job title is checked both manually and through the proprietary technology. To cut the long story short, Autoklose keeps you covered and gives your prospecting a big boost.
-
Is it legal to keep copyright policy like todaypk.com?
I believe that this question mischaracterizes the DMCA-related provisions at TodayPk - Watch Online Movies Full Free Download HD Songs as requiring proof of content ownership.In Terms of Use and the Digital Millennium Copyright Act (DMCA), I summarized the elements of a DMCA takedown notice as follows:Furthermore, Section 512(c) requires that the service provider designate an agent to receive takedown notices and specifies, at length, six elements to be included in every notice. These elements pertain to:Signing the notice.Identifying the work that was infringed.Identifying the infringing m...
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How do you esign financial documents in pdf?
How to enable echo sign pdf for editing?
Get more for Download eSignature Presentation Free
- eSign Colorado Cease and Desist Letter Free
- How Do I eSign Alabama Hold Harmless (Indemnity) Agreement
- eSign Connecticut Hold Harmless (Indemnity) Agreement Mobile
- eSign Hawaii Hold Harmless (Indemnity) Agreement Mobile
- Help Me With eSign Hawaii Hold Harmless (Indemnity) Agreement
- How To eSign Louisiana Hold Harmless (Indemnity) Agreement
- eSign Nevada Hold Harmless (Indemnity) Agreement Easy
- eSign Utah Hold Harmless (Indemnity) Agreement Myself
Find out other Download eSignature Presentation Free
- Wuwludjoz kogil tuk vour p o box 942715 sacramento ca 942292715 888 calpers or 8882257377fax 800 9596545 www calpers ca gov form
- Low back and lower extremity exam form the supply center
- Sanitation inspection request cdss public site form
- Release of information former
- Initial combined assessmentreassessment form care1st health
- 855 202 0879 form
- Emacs sbcounty form
- Transfer on death deed ohio pdf form
- Life insurance beneficiary designation form anthem
- Behavioral health outpatient treatment when complete please fax to 1 form
- Dss form 3087 sep 12layout 1 dss sc
- St davids healthcare partnership financial assistance application financial assistance application form
- Patient history update form dr covell
- In service documentation form
- Form 1317 pharmacy eligibility verification portal access form
- Chow form docx
- Certificate of immunity form covid 4 6
- Medical nutrition therapy referral form
- By signing this form you acknowledge receipt of the notice of privacy practices the notice of forefront dermatology s
- Adult hiv confidential case report form illinois perinatal hiv hivpregnancyhotline