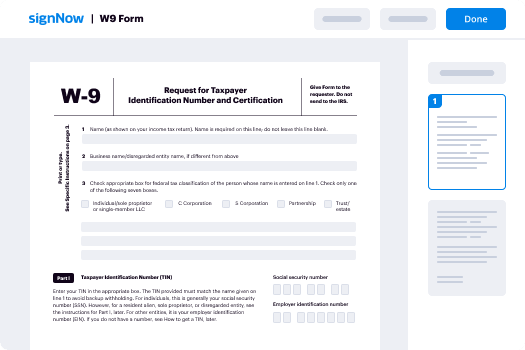
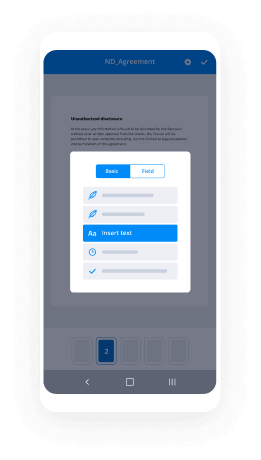
Draw eSignature Form iPad
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Discover the easiest way to Draw eSignature Form iPad with our powerful tools that go beyond eSignature. Sign documents and collect data, signatures, and payments from other parties from a single solution.
Robust integration and API capabilities
Enable the airSlate SignNow API and supercharge your workspace systems with eSignature tools. Streamline data routing and record updates with out-of-the-box integrations.
Advanced security and compliance
Set up your eSignature workflows while staying compliant with major eSignature, data protection, and eCommerce laws. Use airSlate SignNow to make every interaction with a document secure and compliant.
Various collaboration tools
Make communication and interaction within your team more transparent and effective. Accomplish more with minimal efforts on your side and add value to the business.
Enjoyable and stress-free signing experience
Delight your partners and employees with a straightforward way of signing documents. Make document approval flexible and precise.
Extensive support
Explore a range of video tutorials and guides on how to Draw eSignature Form iPad. Get all the help you need from our dedicated support team.
Keep your eSignature workflows on track
Make the signing process more streamlined and uniform
Take control of every aspect of the document execution process. eSign, send out for signature, manage, route, and save your documents in a single secure solution.
Add and collect signatures from anywhere
Let your customers and your team stay connected even when offline. Access airSlate SignNow to Draw eSignature Form iPad from any platform or device: your laptop, mobile phone, or tablet.
Ensure error-free results with reusable templates
Templatize frequently used documents to save time and reduce the risk of common errors when sending out copies for signing.
Stay compliant and secure when eSigning
Use airSlate SignNow to Draw eSignature Form iPad and ensure the integrity and security of your data at every step of the document execution cycle.
Enjoy the ease of setup and onboarding process
Have your eSignature workflow up and running in minutes. Take advantage of numerous detailed guides and tutorials, or contact our dedicated support team to make the most out of the airSlate SignNow functionality.
Benefit from integrations and API for maximum efficiency
Integrate with a rich selection of productivity and data storage tools. Create a more encrypted and seamless signing experience with the airSlate SignNow API.
Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
Our user reviews speak for themselves






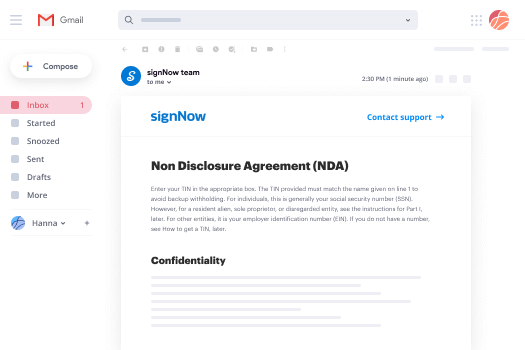
How to Create a Signature on iPad
If you wish to create a signature on your iPad, airSlate SignNow provides a smooth solution that is both intuitive and budget-friendly. This platform enables you to easily generate, distribute, and sign documents while benefiting from a comprehensive set of features that deliver impressive ROI for your organization.
Instructions to Create a Signature on iPad with airSlate SignNow
- Launch your web browser and go to the airSlate SignNow website.
- Sign up for a free trial account or log into your current account.
- Upload the document that requires your signature or needs to be prepared for signing.
- If you intend to reuse this document, save it as a template for future reference.
- Open the document and perform any necessary modifications, like adding fillable sections or inserting particular details.
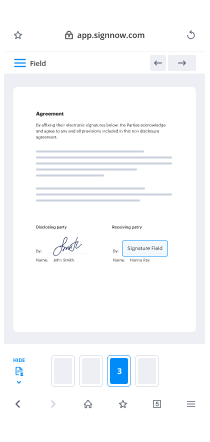
- Insert your signature and add signature fields for additional signers if required.
- Hit 'Continue' to complete and dispatch the eSignature request.
By adhering to these instructions, you can effectively create your signature on your iPad using airSlate SignNow. This platform not only streamlines the signing process but also boosts your document management efficiency.
Experience the advantages of airSlate SignNow now! Register for your free trial and learn how simple it is to handle your eSignatures and documents.
How it works
Upload & open your document in the editor
Fill it out and eSign it in minutes
Save the signed document or share it with others
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
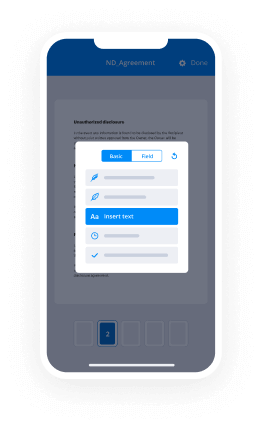
How can I draw my signature on iPad using airSlate SignNow?
With airSlate SignNow, you can easily draw your signature on iPad using your finger or a stylus. Simply open the document you want to sign, select the signature field, and choose the 'Draw' option. This allows you to create a personalized signature that perfectly fits your style.
-
Is there a cost associated with drawing a signature on iPad with airSlate SignNow?
airSlate SignNow offers various pricing plans that include the ability to draw a signature on iPad. You can choose a plan that fits your business needs and budget, ensuring that you get a cost-effective solution for eSigning and document management.
-
What features does airSlate SignNow offer for drawing signatures on iPad?
airSlate SignNow provides several features for drawing signatures on iPad, including the ability to customize your signature and save it for future use. Additionally, you can add text fields, checkboxes, and other elements to your documents, making it a comprehensive eSigning tool.
-
Can I use airSlate SignNow to draw a signature on iPad without an internet connection?
While airSlate SignNow requires an internet connection to access its full range of features, you can still draw your signature on iPad and save it locally. Once you're back online, you can upload your signed documents to the platform for secure storage and sharing.
-
What are the benefits of using airSlate SignNow to draw a signature on iPad?
Using airSlate SignNow to draw your signature on iPad offers numerous benefits, including increased efficiency and convenience. You can sign documents on the go, eliminate the need for printing and scanning, and streamline your workflow, saving both time and resources.
-
Does airSlate SignNow integrate with other apps to enhance the signature drawing process on iPad?
Yes, airSlate SignNow integrates with various applications such as Google Drive, Dropbox, and Microsoft Office, allowing you to easily access and sign documents. These integrations enhance the signature drawing process on iPad, making it seamless and more efficient.
-
Is it secure to draw my signature on iPad using airSlate SignNow?
Absolutely! airSlate SignNow prioritizes security by employing advanced encryption methods to protect your documents and signature. When you draw your signature on iPad, you can trust that your sensitive information is secure and compliant with industry standards.
-
Does change.org really brings a change in India?
Has Change.org India influenced any change in India? Ben Rattray knew he was on to something big when the website he founded, Change.org, managed to get the South African government to acknowledge for the first time the scourge of “corrective rape,” a heinous crime meant to “cure” lesbians of their sexual orientation. In 2010 a rape victim from a township started a petition on The world’s platform for change that eventually got 170,000 signatures. In March 2011 the South African parliament formed a national task force to stop the abuses. “There’s almost no person in the country who has seemingly less power than this [South African] woman, but...
-
How can I create a visitor management system?
Visitor Management Techniques and StepsEvery business and organization has visitors. Some just get a few package and food deliveries. Others have customers, vendors and interview candidates streaming in and out all day. How offices manage visitors can be as varied as the organizations themselves. For some, the process of visitor check-in is regimented and formal. For others, handling guests is a fly-by-the-seat-of-the-pants affair.Regardless of the visitor management system, there are certain aspects to the process of handling guests that are common across the board. Most are done so quickly that sometimes very little thought goes into the process at all. Each step, however, is important to the functioning of your organization, the safety of your employees and data, the comfort of the guest and -- most importantly -- the overall efficiency of time spent.In this six-part article about the visitor management process, we’ll break down each step of the process, explain why it is important, and give examples of different methods for effectively accomplishing the end goal - great first impressions, productivity and safety.Visitor Management Step 1: Recognizing Visitors and Making Them ComfortableHave you ever walked into a restaurant or other place of business, looked around and had no idea what you were supposed to do next? No one said hello. No sign directed you to “Order at the Window” or “Please seat yourself.” No directory on the wall pointed you to a visitor desk. Most guests in that situation will do one of three things: 1) they’ll wander around awkwardly and watch what other people do; 2) they’ll ask someone for help; or 3) they’ll turn around and leave.This is an obvious failure of the organization to accomplish the first technique of a strong visitor management process: recognizing that visitors will come to your organization and they will need tools to make the initial moments of that visit comfortable and pleasant. We all know it is easier to remember negative experiences. Visitors who feel confused, lost or unwelcome may never want to return, and even worse, may tell others about their treatment.People have an inherent need to be recognized. The first step of recognizing visitors can be easy as saying, “hello”, having a sign that reads “Welcome Visitors” or a welcome screen that informs visitors of their next step. Not every location needs to roll out the red carpet for visitors, but every location needs to acknowledge the visitors who do walk through the door.Every organization has different ways of recognizing guests, and they range from very hands-on and labor intensive, to reception automation. Some methods can be combined for maximum impact.Using People to Recognize GuestsHistorically, the most common method used by organizations to make guests feel recognized was to use people. There are really three types of personnel employed to greet visitors.Dedicated receptionist: The dedicated receptionist’s primary job is to welcome visitors and perhaps answer incoming phone calls. They often have minimal responsibilities outside of assisting guests. The greeter at Wal-Mart has minimal duties beyond saying hello and checking the occasional receipt. In some locations where security is a concern, the dedicated person might be a security guard or a door-person.Semi-dedicated receptionist: The difference between a dedicated and a semi-dedicated receptionist is one of responsibilities. A semi-dedicated receptionist is stationed near the door and expected to greet guests as part of the job description (or, maybe they forgot to mention that part), but also has other responsibilities. Most administrative assistants fall into this category. They are expected to greet walk-in guests, answer phones, and perform other tasks, like write letters, manage calendars, set up meetings, and sometimes accomplish large projects. It is surprisingly hard to resume these other responsibilities after interruptions.Informal/unrecognized receptionist: This is perhaps the least considered visitor welcome method, but is, unfortunately, a very common one. The unrecognized receptionist is often a junior employee with a functional role - human resources, accounting, office management - a person who has their own list of priorities. But in today’s modern office happens to sit in a desk by the door. Depending on the number of walk-ins every day, unrecognized receptionists find themselves interrupting important tasks to help guests find their way. Whether they tell you or not, the unrecognized receptionist HATES IT. They resent the guests and the interruptions and prefer to just get their own work done.Using people to greet guests has the advantage of bringing a personal touch to the welcome process. A warm smile, and a “how may I help you?” can provide the start to a truly positive experience.On the other hand, using people is expensive. You have the direct cost of a dedicated receptionist who is paid primarily to greet guests. Or, if you prefer, you have the high cost of productivity lost for semi-dedicated and informal receptionists. And in the case where you have a less-than-effective receptionist – one who greets people gruffly because they are tired of being interrupted – the cost could be greater in terms of negative attitudes toward your organization.Un-staffed Ways to Recognize VisitorsVisitors don’t always want or need to talk to a person to feel welcome. Organizations can spare employee time and save money by making effective use of the following methods for greeting guests.Automated receptionists: More and more locations are taking advantage of automation in order to greet and assist guests. It is common to see airport check-in kiosks, visitor registration kiosks, informational kiosks in visitor centers and libraries, self-ordering stations at fast-food restaurants. Even just an automated announcement connected to your door - “Welcome, please turn right and proceed to the counter” - tells visitors they are expected and what they are supposed to do. Modern offices are rapidly adopting visitor check-in apps to create strong impressions and improve efficiency.Signage: Prominent signs bridge important gaps for visitors. Posted directories, plaques that identify visitor check-in locations or information desks, and directional signs all help visitors to feel comfortable.Automated receptionists and signage have the advantage of being relatively permanent, tireless, and available 24 hours a day. The cost is far less than paying a dedicated person. Also, as crazy as it sounds, people don’t always like talking to people. Being able to use a kiosk or signage is often preferable to having to ask someone for directions. Signs and kiosks may not be able to deliver the warmth of a smile, but they can direct visitors to the person most likely to give them that smile.Conclusion: The Best WayYou guessed it, there is no single "best way". Rather, the best option to greet guests varies by organization, but all of the most effective methods ensure that the guest is acknowledged, either by a sign or a smile. Visitors should feel welcome, and confident that they can accomplish what they came to do. Using forethought and planning, you can ensure your organization recognizes visitors as part of your visitor management process.Visitor Management Step 2: Identifying VisitorsWhen visitors arrive in your place of work, how do you find out who they are and what their business is? Identifying visitors is an important step in the visitor management process. Once you have this valuable piece of information you can create a great visitor experience. Not having it though could cause you to steer a guest the wrong direction, or allow someone onto the premise who should not be there.In Part One of this series, we described how important it is to simply greet guests and make them feel comfortable. Once this is accomplished, the next step in the process is to determine who they are, what type of guest they are, and how best to meet their needs.Visitors VaryOrganizations have varying levels for how they need or want to greet guests, and it often depends on the type of business that person has come to accomplish. You might be thinking, “My organization doesn’t have any visitors,” but you’d be wrong. Even the most insular of organizations will have people from outside show up from time to time. Consider the following types of visitors:Task-oriented visitors: These include postal workers and delivery personnel, maintenance workers, building and code inspectors. These are people who arrive with a set task that must be done at your location (e.g. dropping off a pizza, painting an office, checking the smoke detectors). They are often paid (or tipped) per task so they will leave quickly once it is complete.Important guests: Prospective and current clients or donors, prospective and current vendors, management visiting from the head office, contacts from a related firm, etc., are all important guests. Anyone who your organization wants to have an ongoing, positive relationship with needs to have special care taken to ensure they feel welcome and are treated accordingly.Casual visitors: These are visitors who don’t plan to stay long do business, but need to know how to get where they are going. Consider hospitals, who have people stop in to visit patients all the time. Colleges have family visiting students on campus. Friends and family of employees also fall into this category; the manager’s spouse might show up to take her out to lunch.Visitor-visitors: This might seem like a no-brainer, but places like museums, hotels, tourist attractions, restaurants, and retail are designed to draw people in and welcome those who may only ever be there once.Starting the ConversationOnce a visitor walks in the door, how do you find out what they need?If you are employing a full-time receptionist to greet people, the logical next step is to ask the person who they are, and what they are there to accomplish. With a person at the door, a simple, “How may I help you?” will start the conversation, though other questions may be needed. Depending upon the security needs of your organization, you might require a guest to show an I.D., fill out forms, create a and explain their business.What happens if the receptionist is busy on the phone when a guest arrives? Or if you don’t have a dedicated receptionist, and the person nearest the door is engaged in other tasks?People aren’t the only way to ask guests what they need. More and more offices are using iPad receptionists to allow visitors to check in themselves, whether they employ a receptionist or not. If the receptionist is tied up on the phone but can pause long enough to point a guest to an automated reception kiosk, the guest can continue the visitor registration process instead of waiting around. Guests of all kinds don’t like to wait and appreciate the ability to be proactive instead of inactive.A reception application might ask the following questions:Your NameThe name of the person you are meeting, if applicableThe purpose for your visitOnce the information is obtained, the receptionist or the kiosk can either direct the guest to the appropriate location, or contact the appropriate person to come meet the guest.Conclusion: This is Mission-Critical InformationUnless they are lost and only walked in to get directions to somewhere else, every visitor who enters your organization is there for a specific purpose. However the person is greeted, finding out the reason for their visit is mission-critical to successfully moving them along on their journey. Your method for identifying them, whether a person or a digital visitor management system, needs to have the necessary skills to politely and effectively gather this key information. Then, they must be intelligent enough to guide the visitor to their next step.Only after you have successfully identified the visitor and their purpose can both your visitor and your organization continue the tasks that keep you in business.Visitor Management Step 3: Signing InDoes your organization require visitors to sign in upon arrival? Every organization and even individual offices within has different guidelines surrounding guests and whether or not signing guests in is part of their visitor management system.In parts of this series detailing the visitor management process, we described different ways to greet and identify your guests. Once you’ve identified which type of person or group is standing in your lobby, it is time to determine how much of the check-in process they are required to complete.Whether or not you have visitors sign a paper or digital visitor logbook will depend largely on the rules or customs of your organization, but there are definite benefits to requiring visitors to check in.Security FirstIn today’s modern world, office security is a higher priority than ever before. Schools, government buildings, large firms and factories all have reasons for knowing who is inside their facilities. And while businesses might like to maintain an open-campus type policy when it comes to visitors, that also makes them less secure.Visitors are wild cards. Security best practices require visitors to sign in, which acts as the first layer of protection from would-be criminals – people who would harm people or steal data – by causing them to have to think twice about leaving a trail of evidence.Many organizations require employees to wear or carry identification that doubles as electronic access keys for buildings. Visitors might also need visitor badges in order to access areas, or simply for identification.A good, secure sign-in process will require, at a minimum, the following information from guests:First and last nameBusiness or organization they represent (if applicable)Purpose for visitingName of the employee, host or contact person they are visitingTo go above and beyond, some organizations might also require:A visitor photograph is taken on site.Signed, or electronically signed non-disclosure agreements or waiversMaking Visitors WelcomeIt might seem slightly counter-intuitive, but having visitors sign in can actually help them feel more welcome. While some visitors may be frustrated by having to jump through hoops, this technique is also a signal that your organization has taken visitors into consideration, and it gives guests the knowledge that they’ve come to the right place. When a guest signs in, they know you are aware of their presence and therefore they are less likely to be left wandering around.Also, if visitor badges are part of the sign-in process, you can train your employees to keep an eye out for those visitors who might need a little extra help. Guests often find themselves lost in an unfamiliar location, especially if your building has a lot of twists, turns and levels. Visitor badges give employees the immediate knowledge that the people wearing them are supposed to be in the building, but may not be familiar with the layout.Who signs in?Not every organization is super-sensitive to security, and maybe not every visitor who comes in will be required to sign in. When thinking about your organization and its security needs, you’ll want to think about what your goals are, and what happens in your visitor management process. In step six of this article, we will discuss the benefits of keeping a visitor registration log that includes all guests, but here are some possible questions to consider.Do delivery personnel need to sign in? Will they go beyond the lobby? If not, then signing in may not be necessary. Or, you may require less information for delivery people.How much access will the person have? Could they see or hear sensitive information or encounter semi-dangerous manufacturing equipment? If so, they might need to sign a non-disclosure agreement or a waiver. Such documents can be handled during the sign-in process with an e-signature app.Does your organization want or need to know who is in the building at all times? If yes, then having every person sign in is important. Some organization may not; perhaps you don’t need to know about the visit from an employee’s spouse or the pizza delivery person.Do you have a skilled dedicated receptionist to help visitors find their way? If the answer is no, then an electronic check-in kiosk has the benefit of both signing in visitors and helping to move them along in the process. Otherwise, they may very well be lost from the start.Conclusion – Efficient Sign-In for Happy GuestsWhatever process you choose for signing in guests, visitors will appreciate any steps you take to make the experience easy. Take the time to plan ahead to determine your security needs and how best to make guests feel welcome. An efficient visitor sign-in process shows your guests that they are not just an afterthought, but rather an integrated part of a well-functioning workplace.Visitor Management Step 4: Contacting the HostWhen any visitor arrives at your workplace, they are there to connect with a person. It might be their host for a meeting, one of the people who receives food or package deliveries or someone they need to consult with. Helping the guest and their host connect is a crucial step in any visitor management process. There is nothing worse than walking into a building and talking to ten different people before you find someone who can actually help you. So how can you make this step seamless?First, of course, you have to ensure you are first greeting guests, if necessary. Upon knowing their purpose, you can determine who they came to see; it may be a specific person, a group of people, a department or even security if they are not wanted at your site.What is a host employee’s job? And what are the mechanics of making sure the host knows their guest has arrived in a timely manner?The Responsibilities of a HostWhen we think of a host, we often think of those who hold a dinner party, house guests or even travelers in their home, like Airbnb. The fact is, whenever an employee has someone come to see them at work, that employee is serving as a host. For however long the visitor is at your organization, that employee is the face of your organization. It is their responsibility to leave a good impression.Here are some basic reception etiquette tasks a host can do prior to a guest’s arrival to make sure their visitor has a good experience:Provide crucial information to a visitor, like their name or their department.Communicate vital contact information, like telephone number, email and office number.Inform the guest of which entrance to use and any sign-in requirements your organization has.If possible, determine a meeting spot with the guest in advance and be there prior to the appointed meeting time.If appropriate, preregister the guest with either your human receptionist or visitor registrationThe Mechanics of Connecting Visitors to HostsHow you connect your visitors to your hosts will largely depend on how your reception area is staffed and what the practices of your organization are, but the mechanics are basic. One of the following things has to happen:Reception notifications via a phone call, text, email or instant message - or several of those - is sent to the host, who comes and meets the guest.The visitor is given directions for how to find the host, either by another person or a posted directory and finds the host themselves. This method can have several unfortunate consequences ranging from lost and frustrated guests to unwanted visitors unfettered access to your place of work.The visitor is escorted by another person to their host.Who Makes the Call and Why it’s ImportantWhile the mechanics are simple, there are multiple consequences that could interfere with how work gets done and the impression guests get from your organization. The pros and cons hinge on whose responsibility it is to contact the host:The Receptionist: If you have an obvious reception desk, then the receptionist handles making phone calls, answering questions, giving directions and escorting guests. While this has the benefit of being great customer service, it also requires a very knowledgeable and personable staff member – and it’s expensive. In a busy office, the receptionist might be overwhelmed by people who don’t follow rules or too many people at once. This could leave your desk without staff, and keep guests waiting. It also prevents the receptionist from accomplishing other work, if necessary.The unlucky person by the door: If you are in a modern office or coworking situation, you likely don’t have a designated receptionist. The unfortunate soul who sits near the door may find themselves constantly interrupted by deliveries, salespeople, prospective candidates and more. They then have to stop what they are doing to use a phone, shout across the room (we hope not!) or guide the guest to the person in question, wasting work productivity in the process.A Digital Receptionist: Having a digital visitor check-in kiosk with a visitor management system can be a simple solution for visitors. It can automatically inform the host of a guest’s arrival via the host’s preferred method. A digital system can be set to contact hosts using email, text, phone, Slack or all of the above. This is especially helpful in the case of unexpected guests, like the flower delivery person sent to bring a surprise bouquet. They simply enter the name of the recipient into the system, and the person is contacted – wherever they are – that they have a delivery. One drawback of a digital receptionist is that it can be quite easy for a visitor to walk right past a kioskPerhaps the most fail-safe method of ensuring that guests and hosts get connected is to have a combination of a visitor check-in app supported by live staff for extenuating circumstances.Conclusion – Get Them TogetherReal-time reception notifications connecting visitors with the appropriate host is vital to getting business done. You want your visitors to feel welcomed, and to leave with the impression that your office has its act together. Contacting their host quickly and efficiently allows everyone to get on with the important job of accomplishing the purpose of their visit.Visitor Management Step 5: Checking OutYour visitor has arrived, been greeted, signed in and has been connected with the appropriate host. When their business at your workplace is complete, what happens? Does your guest just walk out the door? Or is your visitor required to check out?Throughout this series, we’ve been exploring the various steps to a good visitor management system and explaining why some easily overlooked steps and processes can important. Perhaps the most overlooked step of visitor management is visitor checkout. Unless you run a medical office or are in the hotel business, most organizations don’t focus on guests checking out; guests just leave. However, there is one very compelling reason to have guests check out: security.Your Secure WorkplaceSecurity means protecting your people, physical assets and your data. When it comes to securing your workplace from the dangers of onsite visitors, you can’t know if a guest has left your premises unless the guest is required to check out. There are multiple security reasons for a visitor to actively check out of the location.Access: If a guest is given any sort of physical access capability (a key, key card or identification) it must be returned at the time of checkout. If the visitor gives it to the host and just leaves the site, then the host is responsible for returning it, and it is more likely to get lost. If the guest has been given electronic key card access, even if they don’t return the card or item, your system should register that they have left and deactivate access connected to the unreturned key card (like that pile of hotel keys you have).Accurate records: Knowing who was in your facility on which days at which times and for how long can be incredibly important if it is ever necessary to investigate a crime. (We’ll discuss in detail why it is important to keep these records in our final installment in this series.)Visual record: If all visitors are required to check out at the same location (a security best practice), it is easy to station a staff person or a security camera to watch for anything unusual. Strange behavior, unusual bulges in pockets and other visual cues can alert staff to theft or other crimes. If the use of a camera is engaged, it can also provide the physical appearance of a person for identification in connection with a crime – whether that person is a suspect or a victim – and can provide a record of their movements and what they were wearing.Visitor Safety: Imagine if a visitor completed their meeting, accidentally wandered into an unused area and either got locked in or had an accident of some sort. If the visitor isn’t required to check out, how would anyone know to look for them? At the end of the day or at shift changes, it is good practice to review a visitor log and see if anyone is still in the building or has stayed far longer than is normal. (A good host will also make sure to walk a visitor who is unfamiliar with the facility to the exit!)Methods for Checking OutHow your visitors check out will largely depend upon how they check in. If a guest is writing their name on a paper visitor logbook upon checking in, then they might be required to write the time at which they check out next to their initial signature. If you have a large volume of guests checking in and out, this may require flipping through a number of pages and isn’t very efficient. Not to mention that every guest can see everyone else that has visited.If you have a staffed reception desk, the receptionist or security guard may check the visitor out, taking any physical objects, like keys or key cards, at that time. The staff person might be required to update the paper or electronic log, or to ask the visitor to do so.Pointing visitors to an iPad receptionist for checkout is probably one of the most efficient ways to have them check out. This maintains easy-to-search electronic records of the visit. It also gives visitors some active role in the check-out process. It is a signal that their business is complete and they can transition to their next task accordingly.Summary – Checking Out Completes the CircleLast time you went to an amazing restaurant, did you save room for dessert? Never underestimate the value of a great last impression.Checking out of your facility is quite simply the final step a visitor ought to take before leaving your facility. With the stress of business complete, and all parties mentally recapping the visit or moving onto their next activities, it is easy to skip. Yet this important step in the visitor management process gives your organization a measure of security nearly impossible to achieve without it.Visitor Management Part 6: Keeping a Visitor LogWe all love visitors! It’s a chance to move your business or projects forward, to showcase your work or even to take a respite from those!When putting a process to your visitor management system, when a visitor to your organization has signed in, accomplished something amazing - or maybe just had lunch - with one of your staff, and then signed out... Do you keep the visitor log?Over the course of this series, we’ve discussed all the important steps of having a visitor management process. The final piece of an efficient process occurs almost completely outside the visitor’s experience. While the visitor is aware of signing in and signing out, whether or not you keep a record of visitors is completely at the discretion of your organization. There are definite benefits to keeping a visitor log.Why keep a visitor log?There are some distinct advantages to keeping a visitor log. You never know when you might need to reference the information. Here are some possible reasons and scenarios.Visitor Recall: Some employees meet with LOTS of people: salespeople, job candidates in a low unemployment market, vendors crucial to delivering a great product, potential and current clients, maintenance workers and even key staff from other sites. If they had an unfamiliar walk-in visitor and did not get the name or contact information of that person – or misplaced it – a visitor log can fill in the gap. Categorizing every visitors correctly in your CRM database and following up can be crucial for sales and relationship building.Following Up with Visitors: Perhaps you wish to send a message to certain visitors. For example, if you run a service organization, you might wish to send a survey after visitor departs your facility. The insights and data they provide will allow for continuous improvement. Or, perhaps you hosted a grand opening party or Meetup event. You might wish to recap the event to reinforce the good feelings or cause. With a properly built and maintained visitor log you can automate these tasks.Crime Investigation: If you know exactly when a visitor checked in and out of your facility, it can greatly assist with the investigation of a crime. If even the pizza delivery person must sign in and out, but for some reason spent an hour in your facility on the same day property was stolen, that is suspicious. The crime need not even be committed at your organization. If law enforcement is tracking the movements of a suspect or a victim, as in this case, the information of whether they entered your premises could be vital.Digital vs. PaperMost visitor logs are going to be in one of two forms: a paper log that people sign in and out of, or a digital record.In our increasingly digital world, it is hard to believe that paper logbooks still exist. There are a number of drawbacks to paper visitor records.Bad handwriting can make it impossible to read.Unless closely monitored, it is easier for a person to fake entries, in particular, the check-in and check-out times. It is also easy to bypass altogether.They take up a lot of space.They can’t be sorted by name or otherwise easily searched.Digital visitor logs, especially cloud-based, have several distinct advantages over paper logs.They can be sorted by any field, including name, date, time of check-in or check-out, their host’s name or more. All of the visitor’s info is easy to read.They can be searched quickly and efficiently by computer.They take up only a small amount of digital storage space.They can store other records with the log, like non-disclosure agreements and waivers.The time is logged automatically by the electronic device, and therefore the time cannot be falsified.How Long Should You Store Visitor Log Records?When it comes to keeping organizational records, we often fall into two camps.Throw Everything Out: It frees up a lot of physical and mental space. (There is a reason Marie Kondo is so popular.) However, if you throw out records prematurely, you could find yourself needing them for reference; financial audits are the perfect example.Keeping Everything Forever: This can be beneficial when you need to reference information, assuming the records are kept in an organized system. If, however, you keep everything indefinitely AND your system is disorganized, you might as well just take a bulldozer to your files.As is usually the case, the best scenario is somewhere in the middle: you may have reason to go back in the records two, five or ten years, depending on your organization’s needs.If you are keeping paper records, it is likely they will either be thrown out long before this or filed away in a manner that it is unlikely to be retrieved. Digital records can be automatically archived or deleted after a certain length of time. Even if you choose never to delete the records, they take up so little space that keeping them will be no hassle at all.Wrapping it all upKeeping a visitor log, preferably in digital form, is the final step in a comprehensive visitor management process. A guest is greeted, identified, signs in, meets up with the host and signs out. Then, the log of these visits is filed away to the benefit of all the different parties who might have need of them. It is the final link in the chain of a successful visit and an efficient process.You made it! You are now officially one of the world's foremost experts on visitor management techniques!Originally posted by Greetly visitor management system at www.greetly.com/blog/visitor-management-techniques-steps. Reposted with permission.
-
What are the best ways to manage your visitors?
Visitor Management Techniques and StepsEvery business and organization has visitors. Some just get a few package and food deliveries. Others have customers, vendors and interview candidates streaming in and out all day. How offices manage visitors can be as varied as the organizations themselves. For some, the process of visitor check-in is regimented and formal. For others, handling guests is a fly-by-the-seat-of-the-pants affair.Regardless of the visitor management system, there are certain aspects to the process of handling guests that are common across the board. Most are done so quickly that sometimes very little thought goes into the process at all. Each step, however, is important to the functioning of your organization, the safety of your employees and data, the comfort of the guest and -- most importantly -- the overall efficiency of time spent.In this six-part article about the visitor management process, we’ll break down each step of the process, explain why it is important, and give examples of different methods for effectively accomplishing the end goal - great first impressions, productivity and safety.Visitor Management Step 1: Recognizing Visitors and Making Them ComfortableHave you ever walked into a restaurant or other place of business, looked around and had no idea what you were supposed to do next? No one said hello. No sign directed you to “Order at the Window” or “Please seat yourself.” No directory on the wall pointed you to a visitor desk. Most guests in that situation will do one of three things: 1) they’ll wander around awkwardly and watch what other people do; 2) they’ll ask someone for help; or 3) they’ll turn around and leave.This is an obvious failure of the organization to accomplish the first technique of a strong visitor management process: recognizing that visitors will come to your organization and they will need tools to make the initial moments of that visit comfortable and pleasant. We all know it is easier to remember negative experiences. Visitors who feel confused, lost or unwelcome may never want to return, and even worse, may tell others about their treatment.People have an inherent need to be recognized. The first step of recognizing visitors can be easy as saying, “hello”, having a sign that reads “Welcome Visitors” or a welcome screen that informs visitors of their next step. Not every location needs to roll out the red carpet for visitors, but every location needs to acknowledge the visitors who do walk through the door.Every organization has different ways of recognizing guests, and they range from very hands-on and labor intensive, to reception automation. Some methods can be combined for maximum impact.Using People to Recognize GuestsHistorically, the most common method used by organizations to make guests feel recognized was to use people. There are really three types of personnel employed to greet visitors.Dedicated receptionist: The dedicated receptionist’s primary job is to welcome visitors and perhaps answer incoming phone calls. They often have minimal responsibilities outside of assisting guests. The greeter at Wal-Mart has minimal duties beyond saying hello and checking the occasional receipt. In some locations where security is a concern, the dedicated person might be a security guard or a door-person.Semi-dedicated receptionist: The difference between a dedicated and a semi-dedicated receptionist is one of responsibilities. A semi-dedicated receptionist is stationed near the door and expected to greet guests as part of the job description (or, maybe they forgot to mention that part), but also has other responsibilities. Most administrative assistants fall into this category. They are expected to greet walk-in guests, answer phones, and perform other tasks, like write letters, manage calendars, set up meetings, and sometimes accomplish large projects. It is surprisingly hard to resume these other responsibilities after interruptions.Informal/unrecognized receptionist: This is perhaps the least considered visitor welcome method, but is, unfortunately, a very common one. The unrecognized receptionist is often a junior employee with a functional role - human resources, accounting, office management - a person who has their own list of priorities. But in today’s modern office happens to sit in a desk by the door. Depending on the number of walk-ins every day, unrecognized receptionists find themselves interrupting important tasks to help guests find their way. Whether they tell you or not, the unrecognized receptionist HATES IT. They resent the guests and the interruptions and prefer to just get their own work done.Using people to greet guests has the advantage of bringing a personal touch to the welcome process. A warm smile, and a “how may I help you?” can provide the start to a truly positive experience.On the other hand, using people is expensive. You have the direct cost of a dedicated receptionist who is paid primarily to greet guests. Or, if you prefer, you have the high cost of productivity lost for semi-dedicated and informal receptionists. And in the case where you have a less-than-effective receptionist – one who greets people gruffly because they are tired of being interrupted – the cost could be greater in terms of negative attitudes toward your organization.Un-staffed Ways to Recognize VisitorsVisitors don’t always want or need to talk to a person to feel welcome. Organizations can spare employee time and save money by making effective use of the following methods for greeting guests.Automated receptionists: More and more locations are taking advantage of automation in order to greet and assist guests. It is common to see airport check-in kiosks, visitor registration kiosks, informational kiosks in visitor centers and libraries, self-ordering stations at fast-food restaurants. Even just an automated announcement connected to your door - “Welcome, please turn right and proceed to the counter” - tells visitors they are expected and what they are supposed to do. Modern offices are rapidly adopting visitor check-in apps to create strong impressions and improve efficiency.Signage: Prominent signs bridge important gaps for visitors. Posted directories, plaques that identify visitor check-in locations or information desks, and directional signs all help visitors to feel comfortable.Automated receptionists and signage have the advantage of being relatively permanent, tireless, and available 24 hours a day. The cost is far less than paying a dedicated person. Also, as crazy as it sounds, people don’t always like talking to people. Being able to use a kiosk or signage is often preferable to having to ask someone for directions. Signs and kiosks may not be able to deliver the warmth of a smile, but they can direct visitors to the person most likely to give them that smile.Conclusion: The Best WayYou guessed it, there is no single "best way". Rather, the best option to greet guests varies by organization, but all of the most effective methods ensure that the guest is acknowledged, either by a sign or a smile. Visitors should feel welcome, and confident that they can accomplish what they came to do. Using forethought and planning, you can ensure your organization recognizes visitors as part of your visitor management process.Visitor Management Step 2: Identifying VisitorsWhen visitors arrive in your place of work, how do you find out who they are and what their business is? Identifying visitors is an important step in the visitor management process. Once you have this valuable piece of information you can create a great visitor experience. Not having it though could cause you to steer a guest the wrong direction, or allow someone onto the premise who should not be there.In Part One of this series, we described how important it is to simply greet guests and make them feel comfortable. Once this is accomplished, the next step in the process is to determine who they are, what type of guest they are, and how best to meet their needs.Visitors VaryOrganizations have varying levels for how they need or want to greet guests, and it often depends on the type of business that person has come to accomplish. You might be thinking, “My organization doesn’t have any visitors,” but you’d be wrong. Even the most insular of organizations will have people from outside show up from time to time. Consider the following types of visitors:Task-oriented visitors: These include postal workers and delivery personnel, maintenance workers, building and code inspectors. These are people who arrive with a set task that must be done at your location (e.g. dropping off a pizza, painting an office, checking the smoke detectors). They are often paid (or tipped) per task so they will leave quickly once it is complete.Important guests: Prospective and current clients or donors, prospective and current vendors, management visiting from the head office, contacts from a related firm, etc., are all important guests. Anyone who your organization wants to have an ongoing, positive relationship with needs to have special care taken to ensure they feel welcome and are treated accordingly.Casual visitors: These are visitors who don’t plan to stay long do business, but need to know how to get where they are going. Consider hospitals, who have people stop in to visit patients all the time. Colleges have family visiting students on campus. Friends and family of employees also fall into this category; the manager’s spouse might show up to take her out to lunch.Visitor-visitors: This might seem like a no-brainer, but places like museums, hotels, tourist attractions, restaurants, and retail are designed to draw people in and welcome those who may only ever be there once.Starting the ConversationOnce a visitor walks in the door, how do you find out what they need?If you are employing a full-time receptionist to greet people, the logical next step is to ask the person who they are, and what they are there to accomplish. With a person at the door, a simple, “How may I help you?” will start the conversation, though other questions may be needed. Depending upon the security needs of your organization, you might require a guest to show an I.D., fill out forms, create a and explain their business.What happens if the receptionist is busy on the phone when a guest arrives? Or if you don’t have a dedicated receptionist, and the person nearest the door is engaged in other tasks?People aren’t the only way to ask guests what they need. More and more offices are using iPad receptionists to allow visitors to check in themselves, whether they employ a receptionist or not. If the receptionist is tied up on the phone but can pause long enough to point a guest to an automated reception kiosk, the guest can continue the visitor registration process instead of waiting around. Guests of all kinds don’t like to wait and appreciate the ability to be proactive instead of inactive.A reception application might ask the following questions:Your NameThe name of the person you are meeting, if applicableThe purpose for your visitOnce the information is obtained, the receptionist or the kiosk can either direct the guest to the appropriate location, or contact the appropriate person to come meet the guest.Conclusion: This is Mission-Critical InformationUnless they are lost and only walked in to get directions to somewhere else, every visitor who enters your organization is there for a specific purpose. However the person is greeted, finding out the reason for their visit is mission-critical to successfully moving them along on their journey. Your method for identifying them, whether a person or a digital visitor management system, needs to have the necessary skills to politely and effectively gather this key information. Then, they must be intelligent enough to guide the visitor to their next step.Only after you have successfully identified the visitor and their purpose can both your visitor and your organization continue the tasks that keep you in business.Visitor Management Step 3: Signing InDoes your organization require visitors to sign in upon arrival? Every organization, and even individual offices within, has different guidelinessurrounding guests and whether or not signing guests in is part of their visitor management system.In Parts of this series detailing the visitor management process, we described different ways to greet and identify your guests. Once you’ve identified which type of person or group is standing in your lobby, it is time to determine how much of the check-in process they are required to complete.Whether or not you have visitors sign a paper or digital visitor logbook will depend largely on the rules or customs of your organization, but there are definite benefits to requiring visitors to check in.Security FirstIn today’s modern world, office security is a higher priority than ever before. Schools, government buildings, large firms and factories all have reasons for knowing who is inside their facilities. And while businesses might like to maintain an open-campus type policy when it comes to visitors, that also makes them less secure.Visitors are wild cards. Security best practices require visitors to sign in, which adds a first layer of protection from would-be criminals – people who would harm people or steal data – by causing them to have to think twice about leaving a trail of evidence.Many organizations require employees to wear or carry identification that doubles as electronic access keys for buildings. Visitors might also need visitor badges in order to access areas, or simply for identification.A good, secure sign-in process will require, at a minimum, the following information from guests:First and last nameBusiness or organization they represent (if applicable)Purpose for visitingName of the employee, host or contact person they are visitingTo go above and beyond, some organizations might also require:A visitor photograph taken on site.Signed, or electronically signed non-disclosure agreements or waiversMaking Visitors WelcomeIt might seem slightly counter-intuitive, but having visitors sign in can actually help them feel more welcome. While some visitors may be frustrated by having to jump through hoops, this technique is also a signal that your organization has taken visitors into consideration, and it gives guests the knowledge that they’ve come to the right place. When a guest signs in, they know you are aware of their presence and therefore they are less likely to be left wandering around.Also, if visitor badges are part of the sign-in process, you can train your employees to keep an eye out for those visitors who might need a little extra help. Guests often find themselves lost in an unfamiliar location, especially if your building has a lot of twists, turns and levels. Visitor badges give employees the immediate knowledge that the people wearing them are supposed to be in the building, but may not be familiar with the layout.Who signs in?Not every organization is super-sensitive to security, and maybe not every visitor who comes in will be required to sign in. When thinking about your organization and its security needs, you’ll want to think about what your goals are, and what happens in your visitor management process. In Step Six of this article , we will discuss the benefits of keeping a visitor registration log that includes all guests, but here are some possible questions to consider.Do delivery personnel need to sign in? Will they go beyond the lobby? If not, then signing in may not be necessary. Or, you may require less information for delivery people.How much access will the person have? Could they see or hear sensitive information or encounter semi-dangerous manufacturing equipment? If so, they might need to sign a non-disclosure agreement or a waiver. Such documents can be handled during the sign-in process with an e-signature app.Does your organization want or need to know who is in the building at all times? If yes, then having every person sign in is important. Some organization may not; perhaps you don’t need to know about the visit from an employee’s spouse or the pizza delivery person.Do you have a skilled dedicated receptionist to help visitors find their way? If the answer is no, then an electronic check-in kiosk has the benefit of both signing in visitors and helping to move them along in the process. Otherwise, they may very well be lost from the start.Conclusion – Efficient Sign-In for Happy GuestsWhatever process you choose for signing in guests, visitors will appreciate any steps you take to make the experience easy. Take the time to plan ahead to determine your security needs and how best to make guests feel welcome. An efficient visitor sign-in process shows your guests that they are not just an afterthought, but rather an integrated part of a well-functioning workplace.Visitor Management Step 4: Contacting the HostWhen any visitor arrives at your workplace, they are there to connect with a person. It might be their host for a meeting, one of the people who receives food or package deliveries or someone they need to consult with. Helping the guest and their host connect is a crucial step in any visitor management process. There is nothing worse than walking into a building and talking to ten different people before you find someone who can actually help you. So how can you make this step seamless?First, of course, you have to ensure you are first greeting guests, if necessary. Upon knowing their purpose, you can determine who they came to see; it may be a specific person, a group of people, a department or even security if they are not wanted at your site.What is a host employee’s job? And what are the mechanics of making sure the host knows their guest has arrived in a timely manner?The Responsibilities of a HostWhen we think of a host, we often think of those who hold a dinner party, house guests or even travelers in their home, like Airbnb. The fact is, whenever an employee has someone come to see them at work, that employee is serving as a host. For however long the visitor is at your organization, that employee is the face of your organization. It is their responsibility to leave a good impression.Here are some basic reception etiquette tasks a host can do prior to a guest’s arrival to make sure their visitor has a good experience:Provide crucial information to a visitor, like their name or their department.Communicate vital contact information, like telephone number, email and office number.Inform the guest of which entrance to use and any sign-in requirements your organization has.If possible, determine a meeting spot with the guest in advance and be there prior to the appointed meeting time.If appropriate, preregister the guest with either your human receptionist or visitor registrationThe Mechanics of Connecting Visitors to HostsHow you connect your visitors to your hosts will largely depend on how your reception area is staffed and what the practices of your organization are, but the mechanics are basic. One of the following things has to happen:Reception notifications via a phone call, text, email or instant message - or several of those - is sent to the host, who comes and meets the guest.The visitor is given directions for how to find the host, either by another person or a posted directory and finds the host themselves. This method can have several unfortunate consequences ranging from lost and frustrated guests to unwanted visitors unfettered access to your place of work.The visitor is escorted by another person to their host.Who Makes the Call and Why it’s ImportantWhile the mechanics are simple, there are multiple consequences that could interfere with how work gets done and the impression guests get from your organization. The pros and cons hinge on whose responsibility it is to contact the host:The Receptionist: If you have an obvious reception desk, then the receptionist handles making phone calls, answering questions, giving directions and escorting guests. While this has the benefit of being great customer service, it also requires a very knowledgeable and personable staff member – and it’s expensive. In a busy office, the receptionist might be overwhelmed by people who don’t follow rules or too many people at once. This could leave your desk without staff, and keep guests waiting. It also prevents the receptionist from accomplishing other work, if necessary.The unlucky person by the door: If you are in a modern office or coworking situation, you likely don’t have a designated receptionist. The unfortunate soul who sits near the door may find themselves constantly interrupted by deliveries, salespeople, prospective candidates and more. They then have to stop what they are doing to use a phone, shout across the room (we hope not!) or guide the guest to the person in question, wasting work productivity in the process.A Digital Receptionist: Having a digital visitor check-in kiosk with a visitor management system can be a simple solution for visitors. It can automatically inform the host of a guest’s arrival via the host’s preferred method. A digital system can be set to contact hosts using email, text, phone, Slack or all of the above. This is especially helpful in the case of unexpected guests, like the flower delivery person sent to bring a surprise bouquet. They simply enter the name of the recipient into the system, and the person is contacted – wherever they are – that they have a delivery. One drawback of a digital receptionist is that it can be quite easy for a visitor to walk right past a kioskPerhaps the most fail-safe method of ensuring that guests and hosts get connected is to have a combination of a visitor check-in app supported by live staff for extenuating circumstances.Conclusion – Get Them TogetherReal-time reception notifications connecting visitors with the appropriate host is vital to getting business done. You want your visitors to feel welcomed, and to leave with the impression that your office has its act together. Contacting their host quickly and efficiently allows everyone to get on with the important job of accomplishing the purpose of their visit.Visitor Management Step 5: Checking OutYour visitor has arrived, been greeted, signed in and has been connected with the appropriate host. When their business at your workplace is complete, what happens? Does your guest just walk out the door? Or is your visitor required to check out?Throughout this series, we’ve been exploring the various steps to a good visitor management system and explaining why some easily overlooked steps and processes can important. Perhaps the most overlooked step of visitor management is visitor checkout. Unless you run a medical office or are in the hotel business, most organizations don’t focus on guests checking out; guests just leave. However, there is one very compelling reason to have guests check out: security.Your Secure WorkplaceSecurity means protecting your people, physical assets and your data. When it comes to securing your workplace from the dangers of onsite visitors, you can’t know if a guest has left your premises unless the guest is required to check out. There are multiple security reasons for a visitor to actively check out of the location.Access: If a guest is given any sort of physical access capability (a key, key card or identification) it must be returned at the time of checkout. If the visitor gives it to the host and just leaves the site, then the host is responsible for returning it, and it is more likely to get lost. If the guest has been given electronic key card access, even if they don’t return the card or item, your system should register that they have left and deactivate access connected to the unreturned key card (like that pile of hotel keys you have).Accurate records: Knowing who was in your facility on which days at which times and for how long can be incredibly important if it is ever necessary to investigate a crime. (We’ll discuss in detail why it is important to keep these records in our final installment in this series.)Visual record: If all visitors are required to check out at the same location (a security best practice), it is easy to station a staff person or a security camera to watch for anything unusual. Strange behavior, unusual bulges in pockets and other visual cues can alert staff to theft or other crimes. If the use of a camera is engaged, it can also provide the physical appearance of a person for identification in connection with a crime – whether that person is a suspect or a victim – and can provide a record of their movements and what they were wearing.Visitor Safety: Imagine if a visitor completed their meeting, accidentally wandered into an unused area and either got locked in or had an accident of some sort. If the visitor isn’t required to check out, how would anyone know to look for them? At the end of the day or at shift changes, it is good practice to review a visitor log and see if anyone is still in the building or has stayed far longer than is normal. (A good host will also make sure to walk a visitor who is unfamiliar with the facility to the exit!)Methods for Checking OutHow your visitors check out will largely depend upon how they check in. If a guest is writing their name on a paper visitor logbook upon checking in, then they might be required to write the time at which they check out next to their initial signature. If you have a large volume of guests checking in and out, this may require flipping through a number of pages and isn’t very efficient. Not to mention that every guest can see everyone else that has visited.If you have a staffed reception desk, the receptionist or security guard may check the visitor out, taking any physical objects, like keys or key cards, at that time. The staff person might be required to update the paper or electronic log, or to ask the visitor to do so.Pointing visitors to an iPad receptionist for checkout is probably one of the most efficient ways to have them check out. This maintains easy-to-search electronic records of the visit. It also gives visitors some active role in the check-out process. It is a signal that their business is complete and they can transition to their next task accordingly.See Greetly LiveSummary – Checking Out Completes the CircleLast time you went to an amazing restaurant, did you save room for dessert? Never underestimate the value of a great last impression.Checking out of your facility is quite simply the final step a visitor ought to take before leaving your facility. With the stress of business complete, and all parties mentally recapping the visit or moving onto their next activities, it is easy to skip. Yet this important step in the visitor management process gives your organization a measure of security nearly impossible to achieve without it.Visitor Management Part 6: Keeping a Visitor LogWe all love visitors! It’s a chance to move your business or projects forward, to showcase your work or even to take a respite from those!When putting a process to your visitor management system, when a visitor to your organization has signed in, accomplished something amazing - or maybe just had lunch - with one of your staff, and then signed out... Do you keep the visitor log?Over the course of this series, we’ve discussed all the important steps of having a visitor management process. The final piece of an efficient process occurs almost completely outside the visitor’s experience. While the visitor is aware of signing in and signing out, whether or not you keep a record of visitors is completely at the discretion of your organization. There are definite benefits to keeping a visitor log.Why keep a visitor log?There are some distinct advantages to keeping a visitor log. You never know when you might need to reference the information. Here are some possible reasons and scenarios.Visitor Recall: Some employees meet with LOTS of people: salespeople, job candidates in a low unemployment market, vendors crucial to delivering a great product, potential and current clients, maintenance workers and even key staff from other sites. If they had an unfamiliar walk-in visitor and did not get the name or contact information of that person – or misplaced it – a visitor log can fill in the gap. Categorizing every visitors correctly in your CRM database and following up can be crucial for sales and relationship building.Following Up with Visitors: Perhaps you wish to send a message to certain visitors. For example, if you run a service organization, you might wish to send a survey after visitor departs your facility. The insights and data they provide will allow for continuous improvement. Or, perhaps you hosted a grand opening party or Meetup event. You might wish to recap the event to reinforce the good feelings or cause. With a properly built and maintained visitor log you can automate these tasks.Crime Investigation: If you know exactly when a visitor checked in and out of your facility, it can greatly assist with the investigation of a crime. If even the pizza delivery person must sign in and out, but for some reason spent an hour in your facility on the same day property was stolen, that is suspicious. The crime need not even be committed at your organization. If law enforcement is tracking the movements of a suspect or a victim, as in this case, the information of whether they entered your premises could be vital.Digital vs. PaperMost visitor logs are going to be in one of two forms: a paper log that people sign in and out of, or a digital record.In our increasingly digital world, it is hard to believe that paper logbooks still exist. There are a number of drawbacks to paper visitor records.Bad handwriting can make them impossible to read.Unless closely monitored, it is easier for a person to fake entries, in particular, the check-in and check-out times. It is also easy to bypass altogether.They take up a lot of space.They can’t be sorted by name or otherwise easily searched.Digital visitor logs, especially cloud-based, have several distinct advantages over paper logs.They can be sorted by any field, including name, date, time of check-in or check-out, host name or more. All of the visitor’s info is easy to read.They can be searched quickly and efficiently by computer.They take up only a small amount of digital storage space.They can store other records with the log, like non-disclosure agreements and waivers.The time is logged automatically by the electronic device, and therefore the time cannot be falsified.How Long Should You Store Visitor Log Records?When it comes to keeping organizational records, we often fall into two camps.Throw Everything Out: It frees up a lot of physical and mental space. (There is a reason Marie Kondo is so popular.) However, if you throw out records prematurely, you could find yourself needing them for reference; financial audits are the perfect example.Keeping Everything Forever: This can be beneficial when you need to reference information, assuming the records are kept in an organized system. If, however, you keep everything indefinitely AND your system is disorganized, you might as well just take a bulldozer to your files.As is usually the case, the best scenario is somewhere in the middle: you may have reason to go back in the records two, five or ten years, depending on your organization’s needs.If you are keeping paper records, it is likely they will either be thrown out long before this or filed away in a manner that it is unlikely to be retrieved. Digital records can be automatically archived or deleted after a certain length of time. Even if you choose never to delete the records, they take up so little space that keeping them will be no hassle at all.Wrapping it all upKeeping a visitor log, preferably in digital form, is the final step in a comprehensive visitor management process. A guest is greeted, identified, signs in, meets up with the host and signs out. Then, the log of these visits is filed away to the benefit of all the different parties who might have need of them. It is the final link in the chain of a successful visit and an efficient process.Originally posted by Greetly at What are Visitor Management Techniques and Steps?. Re-posted with permission.
-
What are the best practices when it comes to managing visitors in a work office environment?
What are Visitor Management Techniques and Steps?Have you ever walked into a restaurant or other place of business, looked around and had no idea what you were supposed to do next? No one said hello. No sign directed you to “Order at the Window” or “Please seat yourself.” No directory on the wall pointed you to a visitor desk. Most guests in that situation will do one of three things: 1) they’ll wander around awkwardly and watch what other people do; 2) they’ll ask someone for help; or 3) they’ll turn around and leave.This is an obvious failure of the organization to accomplish the first technique of a strong visitor management process: recognizing that visitors will come to your organization and they will need tools to make the initial moments of that visit comfortable and pleasant. We all know it is easier to remember negative experiences. Visitors who feel confused, lost or unwelcome may never want to return, and even worse, may tell others about their treatment.People have an inherent need to be recognized. The first step of recognizing visitors can be easy as saying, “hello”, having a sign that reads “Welcome Visitors” or a welcome screen that informs visitors of their next step. Not every location needs to roll out the red carpet for visitors, but every location needs to acknowledge the visitors who do walk through the door.Every organization has different ways of recognizing guests, and they range from very hands-on and labor intensive, to reception automation. Some methods can be combined for maximum impact.Using People to Recognize GuestsHistorically, the most common method used by organizations to make guests feel recognized was to use people. There are really three types of personnel employed to greet visitors.Dedicated receptionist: The dedicated receptionist’s primary job is to welcome visitors and perhaps answer incoming phone calls. They often have minimal responsibilities outside of assisting guests. The greeter at Wal-Mart has minimal duties beyond saying hello and checking the occasional receipt. In some locations where security is a concern, the dedicated person might be a security guard or a door-person.Semi-dedicated receptionist: The difference between a dedicated and a semi-dedicated receptionist is one of responsibilities. A semi-dedicated receptionist is stationed near the door and expected to greet guests as part of the job description (or, maybe they forgot to mention that part), but also has other responsibilities. Most administrative assistants fall into this category. They are expected to greet walk-in guests, answer phones, and perform other tasks, like write letters, manage calendars, set up meetings, and sometimes accomplish large projects. It is surprisingly hard to resume these other responsibilities after interruptions.Informal/unrecognized receptionist: This is perhaps the least considered visitor welcome method, but is, unfortunately, a very common one. The unrecognized receptionist is often a junior employee with a functional role - human resources, accounting, office management - a person who has their own list of priorities. But in today’s modern office happens to sit in a desk by the door. Depending on the number of walk-ins every day, unrecognized receptionists find themselves interrupting important tasks to help guests find their way. Whether they tell you or not, the unrecognized receptionist HATES IT. They resent the guests and the interruptions and prefer to just get their own work done.Using people to greet guests has the advantage of bringing a personal touch to the welcome process. A warm smile, and a “how may I help you?” can provide the start to a truly positive experience.On the other hand, using people is expensive. You have the direct cost of a dedicated receptionist who is paid primarily to greet guests. Or, if you prefer, you have the high cost of productivity lost for semi-dedicated and informal receptionists. And in the case where you have a less-than-effective receptionist – one who greets people gruffly because they are tired of being interrupted – the cost could be greater in terms of negative attitudes toward your organization.Un-staffed Ways to Recognize VisitorsVisitors don’t always want or need to talk to a person to feel welcome. Organizations can spare employee time and save money by making effective use of the following methods for greeting guests.Automated receptionists: More and more locations are taking advantage of automation in order to greet and assist guests. It is common to see airport check-in kiosks, visitor registration kiosks, informational kiosks in visitor centers and libraries, self-ordering stations at fast-food restaurants. Even just an automated announcement connected to your door - “Welcome, please turn right and proceed to the counter” - tells visitors they are expected and what they are supposed to do. Modern offices are rapidly adopting visitor check-in apps to create strong impressions and improve efficiency.Signage: Prominent signs bridge important gaps for visitors. Posted directories, plaques that identify visitor check-in locations or information desks, and directional signs all help visitors to feel comfortable.Automated receptionists and signage have the advantage of being relatively permanent, tireless, and available 24 hours a day. The cost is far less than paying a dedicated person. Also, as crazy as it sounds, people don’t always like talking to people. Being able to use a kiosk or signage is often preferable to having to ask someone for directions. Signs and kiosks may not be able to deliver the warmth of a smile, but they can direct visitors to the person most likely to give them that smile.Conclusion: The Best WayYou guessed it, there is no single "best way". Rather, the best option to greet guests varies by organization, but all of the most effective methods ensure that the guest is acknowledged, either by a sign or a smile. Visitors should feel welcome, and confident that they can accomplish what they came to do. Using forethought and planning, you can ensure your organization recognizes visitors as part of your visitor management process.Visitor Management Step 2: Identifying VisitorsWhen visitors arrive in your place of work, how do you find out who they are and what their business is? Identifying visitors is an important step in the visitor management process. Once you have this valuable piece of information you can create a great visitor experience. Not having it though could cause you to steer a guest the wrong direction, or allow someone onto the premise who should not be there.In Part One of this series, we described how important it is to simply greet guests and make them feel comfortable. Once this is accomplished, the next step in the process is to determine who they are, what type of guest they are, and how best to meet their needs.Visitors VaryOrganizations have varying levels for how they need or want to greet guests, and it often depends on the type of business that person has come to accomplish. You might be thinking, “My organization doesn’t have any visitors,” but you’d be wrong. Even the most insular of organizations will have people from outside show up from time to time. Consider the following types of visitors:Task-oriented visitors: These include postal workers and delivery personnel, maintenance workers, building and code inspectors. These are people who arrive with a set task that must be done at your location (e.g. dropping off a pizza, painting an office, checking the smoke detectors). They are often paid (or tipped) per task so they will leave quickly once it is complete.Important guests: Prospective and current clients or donors, prospective and current vendors, management visiting from the head office, contacts from a related firm, etc., are all important guests. Anyone who your organization wants to have an ongoing, positive relationship with needs to have special care taken to ensure they feel welcome and are treated accordingly.Casual visitors: These are visitors who don’t plan to stay long do business, but need to know how to get where they are going. Consider hospitals, who have people stop in to visit patients all the time. Colleges have family visiting students on campus. Friends and family of employees also fall into this category; the manager’s spouse might show up to take her out to lunch.Visitor-visitors: This might seem like a no-brainer, but places like museums, hotels, tourist attractions, restaurants, and retail are designed to draw people in and welcome those who may only ever be there once.Starting the ConversationOnce a visitor walks in the door, how do you find out what they need?If you are employing a full-time receptionist to greet people, the logical next step is to ask the person who they are, and what they are there to accomplish. With a person at the door, a simple, “How may I help you?” will start the conversation, though other questions may be needed. Depending upon the security needs of your organization, you might require a guest to show an I.D., fill out forms, create a and explain their business.What happens if the receptionist is busy on the phone when a guest arrives? Or if you don’t have a dedicated receptionist, and the person nearest the door is engaged in other tasks?People aren’t the only way to ask guests what they need. More and more offices are using iPad receptionists to allow visitors to check in themselves, whether they employ a receptionist or not. If the receptionist is tied up on the phone but can pause long enough to point a guest to an automated reception kiosk, the guest can continue the visitor registration process instead of waiting around. Guests of all kinds don’t like to wait and appreciate the ability to be proactive instead of inactive.A reception application might ask the following questions:Your Name.The name of the person you are meeting, if applicable.The purpose for your visit.Once the information is obtained, the receptionist or the kiosk can either direct the guest to the appropriate location, or contact the appropriate person to come meet the guest.Conclusion: This is Mission-Critical InformationUnless they are lost and only walked in to get directions to somewhere else, every visitor who enters your organization is there for a specific purpose. However the person is greeted, finding out the reason for their visit is mission-critical to successfully moving them along on their journey. Your method for identifying them, whether a person or a digital visitor management system, needs to have the necessary skills to politely and effectively gather this key information. Then, they must be intelligent enough to guide the visitor to their next step.Only after you have successfully identified the visitor and their purpose can both your visitor and your organization continue the tasks that keep you in business.Visitor Management Step 3: Signing InDoes your organization require visitors to sign in upon arrival? Every organization, and even individual offices within, has different guidelinessurrounding guests and whether or not signing guests in is part of their visitor management system.In parts of this series detailing the visitor management process, we described different ways to greet and identify your guests. Once you’ve identified which type of person or group is standing in your lobby, it is time to determine how much of the check-in process they are required to complete.Whether or not you have visitors sign a paper or digital visitor logbook will depend largely on the rules or customs of your organization, but there are definite benefits to requiring visitors to check in.Security FirstIn today’s modern world, office security is a higher priority than ever before. Schools, government buildings, large firms and factories all have reasons for knowing who is inside their facilities. And while businesses might like to maintain an open-campus type policy when it comes to visitors, that also makes them less secure.Visitors are wild cards. Security best practices require visitors to sign in, which acts as the first layer of protection from would-be criminals – people who would harm people or steal data – by causing them to have to think twice about leaving a trail of evidence.Many organizations require employees to wear or carry identification that doubles as electronic access keys for buildings. Visitors might also need visitor badges in order to access areas, or simply for identification.A good, secure sign-in process will require, at a minimum, the following information from guests:First and last name.Business or organization they represent (if applicable).Purpose for visiting.Name of the employee, host or contact person they are visiting.To go above and beyond, some organizations might also require:A visitor photograph is taken upon entrySigned, or electronically signed non-disclosure agreements or waiversMaking Visitors WelcomeIt might seem slightly counterintuitive, but having visitors sign in can actually help them feel more welcome. While some visitors may be frustrated by having to jump through hoops, this technique is also a signal that your organization has taken visitors into consideration, and it gives guests the knowledge that they’ve come to the right place. When a guest signs in, they know you are aware of their presence and therefore they are less likely to be left wandering around.Also, if visitor badges are part of the sign-in process, you can train your employees to keep an eye out for those visitors who might need a little extra help. Guests often find themselves lost in an unfamiliar location, especially if your building has a lot of twists, turns and levels. Visitor badges give employees the immediate knowledge that the people wearing them are supposed to be in the building, but may not be familiar with the layout.Who Signs In?Not every organization is super-sensitive to security, and maybe not every visitor who comes in will be required to sign in. When thinking about your organization and its security needs, you’ll want to think about what your goals are, and what happens in your visitor management process. In step six of this article we will discuss the benefits of keeping a visitor registration log that includes all guests, but here are some possible questions to consider.Do delivery personnel need to sign in? Will they go beyond the lobby? If not, then signing in may not be necessary. Or, you may require less information for delivery people.How much access will the person have? Could they see or hear sensitive information or encounter semi-dangerous manufacturing equipment? If so, they might need to sign a non-disclosure agreement or a waiver. Such documents can be handled during the sign-in process with an e-signature app.Does your organization want or need to know who is in the building at all times? If yes, then having every person sign in is important. Some organization may not; perhaps you don’t need to know about the visit from an employee’s spouse or the pizza delivery person.Do you have a skilled dedicated receptionist to help visitors find their way? If the answer is no, then an electronic check-in kiosk has the benefit of both signing in visitors and helping to move them along in the process. Otherwise, they may very well be lost from the start.Conclusion – Efficient Sign-In for Happy GuestsWhatever process you choose for signing in guests, visitors will appreciate any steps you take to make the experience easy. Take the time to plan ahead to determine your security needs and how best to make guests feel welcome. An efficient visitor sign-in process shows your guests that they are not just an afterthought, but rather an integrated part of a well-functioning workplace.Visitor Management Step 4: Contacting the HostWhen any visitor arrives at your workplace, they are there to connect with a person. It might be their host for a meeting, one of the people who receives food or package deliveries or someone they need to consult with. Helping the guest and their host connect is a crucial step in any visitor management process. There is nothing worse than walking into a building and talking to ten different people before you find someone who can actually help you. So how can you make this step seamless?First, of course, you have to ensure you are first greeting guests, if necessary. Upon knowing their purpose, you can determine who they came to see; it may be a specific person, a group of people, a department or even security if they are not wanted at your site.What is a host employee’s job? And what are the mechanics of making sure the host knows their guest has arrived in a timely manner?The Responsibilities of a HostWhen we think of a host, we often think of those who hold a dinner party, house guests or even travelers in their home, like Airbnb. The fact is, whenever an employee has someone come to see them at work, that employee is serving as a host. For however long the visitor is at your organization, that employee is the face of your organization. It is their responsibility to leave a good impression.Here are some basic reception etiquette tasks a host can do prior to a guest’s arrival to make sure their visitor has a good experience:Provide crucial information to a visitor, like their name or their department.Communicate vital contact information, like telephone number, email and office number.Inform the guest of which entrance to use and any sign-in requirements your organization has.If possible, determine a meeting spot with the guest in advance and be there prior to the appointed meeting time.If appropriate, preregister the guest with either your human receptionist or visitor registration.The Mechanics of Connecting Visitors to HostsHow you connect your visitors to your hosts will largely depend on how your reception area is staffed and what the practices of your organization are, but the mechanics are basic. One of the following things has to happen:Reception notifications via a phone call, text, email or instant message - or several of those - is sent to the host, who comes and meets the guest.The visitor is given directions for how to find the host, either by another person or a posted directory and finds the host themselves. This method can have several unfortunate consequences ranging from lost and frustrated guests to unwanted visitors unfettered access to your place of work.The visitor is escorted by another person to their host.Who Makes the Call and Why it’s ImportantWhile the mechanics are simple, there are multiple consequences that could interfere with how work gets done and the impression guests get from your organization. The pros and cons hinge on whose responsibility it is to contact the host:The Receptionist: If you have an obvious reception desk, then the receptionist handles making phone calls, answering questions, giving directions and escorting guests. While this has the benefit of being great customer service, it also requires a very knowledgeable and personable staff member – and it’s expensive. In a busy office, the receptionist might be overwhelmed by people who don’t follow rules or too many people at once. This could leave your desk without staff, and keep guests waiting. It also prevents the receptionist from accomplishing other work, if necessary.The unlucky person by the door: If you are in a modern office or coworking situation, you likely don’t have a designated receptionist. The unfortunate soul who sits near the door may find themselves constantly interrupted by deliveries, salespeople, prospective candidates and more. They then have to stop what they are doing to use a phone, shout across the room (we hope not!) or guide the guest to the person in question, wasting work productivity in the process.A Digital Receptionist: Having a digital visitor check-in kiosk with a visitor management system can be a simple solution for visitors. It can automatically inform the host of a guest’s arrival via the host’s preferred method. A digital system can be set to contact hosts using email, text, phone, Slack or all of the above. This is especially helpful in the case of unexpected guests, like the flower delivery person sent to bring a surprise bouquet. They simply enter the name of the recipient into the system, and the person is contacted – wherever they are – that they have a delivery. One drawback of a digital receptionist is that it can be quite easy for a visitor to walk right past a kioskPerhaps the most fail-safe method of ensuring that guests and hosts get connected is to have a combination of a visitor check-in app supported by live staff for extenuating circumstances.Conclusion – Get Them TogetherReal-time reception notifications connecting visitors with the appropriate host is vital to getting business done. You want your visitors to feel welcomed, and to leave with the impression that your office has its act together. Contacting their host quickly and efficiently allows everyone to get on with the important job of accomplishing the purpose of their visit.Visitor Management Step 5: Checking OutYour visitor has arrived, been greeted, signed in and has been connected with the appropriate host. When their business at your workplace is complete, what happens? Does your guest just walk out the door? Or is your visitor required to check out?Throughout this series, we’ve been exploring the various steps to a good visitor management system and explaining why some easily overlooked steps and processes can important. Perhaps the most overlooked step of visitor management is visitor checkout. Unless you run a medical office or are in the hotel business, most organizations don’t focus on guests checking out; guests just leave. However, there is one very compelling reason to have guests check out: security.Your Secure WorkplaceSecurity means protecting your people, physical assets and your data. When it comes to securing your workplace from the dangers of onsite visitors, you can’t know if a guest has left your premises unless the guest is required to check out. There are multiple security reasons for a visitor to actively check out of the location.Access: If a guest is given any sort of physical access capability (a key, key card or identification) it must be returned at the time of checkout. If the visitor gives it to the host and just leaves the site, then the host is responsible for returning it, and it is more likely to get lost. If the guest has been given electronic key card access, even if they don’t return the card or item, your system should register that they have left and deactivate access connected to the unreturned key card (like that pile of hotel keys you have).Accurate records: Knowing who was in your facility on which days at which times and for how long can be incredibly important if it is ever necessary to investigate a crime. (We’ll discuss in detail why it is important to keep these records in our final installment in this series.)Visual record: If all visitors are required to check out at the same location (a security best practice), it is easy to station a staff person or a security camera to watch for anything unusual. Strange behavior, unusual bulges in pockets and other visual cues can alert staff to theft or other crimes. If the use of a camera is engaged, it can also provide the physical appearance of a person for identification in connection with a crime – whether that person is a suspect or a victim – and can provide a record of their movements and what they were wearing.Visitor Safety: Imagine if a visitor completed their meeting, accidentally wandered into an unused area and either got locked in or had an accident of some sort. If the visitor isn’t required to check out, how would anyone know to look for them? At the end of the day or at shift changes, it is good practice to review a visitor log and see if anyone is still in the building or has stayed far longer than is normal. (A good host will also make sure to walk a visitor who is unfamiliar with the facility to the exit!)Methods for Checking OutHow your visitors check out will largely depend upon how they check in. If a guest is writing their name on a paper visitor logbook upon checking in, then they might be required to write the time at which they check out next to their initial signature. If you have a large volume of guests checking in and out, this may require flipping through a number of pages and isn’t very efficient. Not to mention that every guest can see everyone else that has visited.If you have a staffed reception desk, the receptionist or security guard may check the visitor out, taking any physical objects, like keys or key cards, at that time. The staff person might be required to update the paper or electronic log, or to ask the visitor to do so.Pointing visitors to an iPad receptionist for checkout is probably one of the most efficient ways to have them check out. This maintains easy-to-search electronic records of the visit. It also gives visitors some active role in the check-out process. It is a signal that their business is complete and they can transition to their next task accordingly.Summary – Checking Out Completes the CircleLast time you went to an amazing restaurant, did you save room for dessert? Never underestimate the value of a great last impression.Checking out of your facility is quite simply the final step a visitor ought to take before leaving your facility. With the stress of business complete, and all parties mentally recapping the visit or moving onto their next activities, it is easy to skip. Yet this important step in the visitor management process gives your organization a measure of security nearly impossible to achieve without it.Visitor Management Part 6: Keeping a Visitor LogWe all love visitors! It’s a chance to move your business or projects forward, to showcase your work or even to take a respite from those!When putting a process to your visitor management system, when a visitor to your organization has signed in, accomplished something amazing - or maybe just had lunch - with one of your staff, and then signed out... Do you keep the visitor log?Over the course of this series, we’ve discussed all the important steps of having a visitor management process. The final piece of an efficient process occurs almost completely outside the visitor’s experience. While the visitor is aware of signing in and signing out, whether or not you keep a record of visitors is completely at the discretion of your organization. There are definite benefits to keeping a visitor log.Why keep a visitor log?There are some distinct advantages to keeping a visitor log. You never know when you might need to reference the information. Here are some possible reasons and scenarios.Visitor Recall: Some employees meet with LOTS of people: salespeople, job candidates in a low unemployment market, vendors crucial to delivering a great product, potential and current clients, maintenance workers and even key staff from other sites. If they had an unfamiliar walk-in visitor and did not get the name or contact information of that person – or misplaced it – a visitor log can fill in the gap. Categorizing every visitors correctly in your CRM database and following up can be crucial for sales and relationship building.Following Up with Visitors: Perhaps you wish to send a message to certain visitors. For example, if you run a service organization, you might wish to send a survey after visitor departs your facility. The insights and data they provide will allow for continuous improvement. Or, perhaps you hosted a grand opening party or Meetup event. You might wish to recap the event to reinforce the good feelings or cause. With a properly built and maintained visitor log you can automate these tasks.Crime Investigation: If you know exactly when a visitor checked in and out of your facility, it can greatly assist with the investigation of a crime. If even the pizza delivery person must sign in and out, but for some reason spent an hour in your facility on the same day property was stolen, that is suspicious. The crime need not even be committed at your organization. If law enforcement is tracking the movements of a suspect or a victim, as in this case, the information of whether they entered your premises could be vital.Digital vs. PaperMost visitor logs are going to be in one of two forms: a paper log that people sign in and out of, or a digital record.In our increasingly digital world, it is hard to believe that paper logbooks still exist. There are a number of drawbacks to paper visitor records.Bad handwriting can make them impossible to read.Unless closely monitored, it is easier for a person to fake entries, in particular, the check-in and check-out times. It is also easy to bypass altogether.They take up a lot of space.They can’t be sorted by name or otherwise easily searched.Digital visitor logs, especially cloud-based, have several distinct advantages over paper logs.They can be sorted by any field, including name, date, time of check-in or check-out, host name or more. All of the visitor’s info is easy to read.They can be searched quickly and efficiently by computer.They take up only a small amount of digital storage space.They can store other records with the log, like non-disclosure agreements and waivers.The time is logged automatically by the electronic device, and therefore the time cannot be falsified.How Long Should You Store Visitor Log Records?When it comes to keeping organizational records, we often fall into two camps.Throw Everything Out: It frees up a lot of physical and mental space. (There is a reason Marie Kondo is so popular.) However, if you throw out records prematurely, you could find yourself needing them for reference; financial audits are the perfect example.Keeping Everything Forever: This can be beneficial when you need to reference information, assuming the records are kept in an organized system. If, however, you keep everything indefinitely AND your system is disorganized, you might as well just take a bulldozer to your files.As is usually the case, the best scenario is somewhere in the middle: you may have reason to go back in the records two, five or ten years, depending on your organization’s needs.If you are keeping paper records, it is likely they will either be thrown out long before this or filed away in a manner that it is unlikely to be retrieved. Digital records can be automatically archived or deleted after a certain length of time. Even if you choose never to delete the records, they take up so little space that keeping them will be no hassle at all.Wrapping it all upKeeping a visitor log, preferably in digital form, is the final step in a comprehensive visitor management process. A guest is greeted, identified, signs in, meets up with the host and signs out. Then, the log of these visits is filed away to the benefit of all the different parties who might have need of them. It is the final link in the chain of a successful visit and an efficient process.Originally posted by Greetly visitor management system at What are Visitor Management Techniques and Steps?. Re-posted with permission.
-
What is the main reason of the downfall of blackberry company?
Shortly after the release of the first iPhone, Verizon asked BlackBerry to create a touchscreen “iPhone killer.” But the result was a flop, so Verizon turned to Motorola and Google instead.In 2012, one-time co-CEO Jim Balsillie quit the board and cut all ties to BlackBerry in protest after his plan to shift focus to instant-messaging software, which had been opposed by founder Mike Lazaridis, was killed by current CEO Thorsten Heins.Mr. Lazaridis opposed the launch plan for the BlackBerry 10 phones and argued strongly in favour of emphasizing keyboard devices. But Mr. Heins and his executives did not take the advice and launched the touchscreen Z10, with disastrous resultsLate last year, Research In Motion Ltd. chief executive officer Thorsten Heins sat down with the board of directors at the company’s Waterloo, Ont., headquarters to review plans for the launch of a new phone designed to turn around the company’s fortunes.His weapon was the BlackBerry Z10, a slim device with the kind of glass touchscreen that had made Apple Inc. and Samsung Electronics Co. Ltd. the dominant names in the global smartphone market.But one of RIM’s directors was frustrated by what he saw, and spoke out, according to one person who was in the room. There is a cultural problem at RIM, he told the group, and the Z10 was a glaring manifestation of it.The speaker was none other than Michael Lazaridis, the genius behind the BlackBerry, the company’s co-founder and its former co-CEO. Minutes earlier, he said, he had spoken with Mr. Heins’s newest executive recruits, chief marketing officer Frank Boulben and chief operating officer Kristian Tear.Mr. Boulben and Mr. Tear had dismissively told Mr. Lazaridis that the market for keyboard-equipped mobile phones – RIM’s signature offering – was dead.In the board meeting, Mr. Lazaridis pointed to a BlackBerry with a keyboard. “I get this,” he said. “It’s clearly differentiated.” Then he pointed to a touchscreen phone. “I don’t get this.”To turn away from a product that had always done well with corporate customers, and focus on selling yet another all-touch smartphone in a market crowded with them, was a huge mistake, Mr. Lazaridis warned his fellow directors. Some of them agreed.The boardroom confrontation was a telling moment in the downfall of Research In Motion.Once the giant of the smartphone business, RIM, which was renamed BlackBerry Ltd. in the summer, is now on its knees. The company reported a $965-million (U.S.) fiscal second-quarter loss Friday, primarily because of a massive writedown of Z10 phones that sit, unsold and unwanted, about eight months after they first hit the market. The company is cutting 4,500 jobs, 40 per cent of its work force, in a desperate bid to bring costs in line with plummeting revenue.Investors, who have lived through the destruction of more than $75-billion of the company’s market value over the past five years, are still wondering how BlackBerry managed to blow its runaway lead and became a bit player in the smartphone market it invented.An investigation by The Globe and Mail, which included interviews with two dozen past and present company insiders, exposes a series of deep rifts at the executive and boardroom levels.Those divisions hurt the company’s ability to develop products just as it faced its greatest challenge from more nimble and creative rivals – and contributed to the downfall of Canada’s biggest technology company.Once a fast-moving innovator that kept two steps ahead of the competition, RIM grew into a stumbling corporation, blinded by its own success and unable to replicate it. Several years ago, it owned the smartphone world: Even U.S. President Barack Obama was a BlackBerry addict. But after new rivals redefined the market, RIM responded with a string of devices that were late to market, missed the mark with consumers, and opened dangerous fault lines across the organization.Months before their boardroom showdown, Mr. Heins and Mr. Lazaridis found themselves in another strategic standoff in which they were pitted against Jim Balsillie, Mr. Lazaridis’s long-time business partner and co-CEO.Inside RIM, the brash Mr. Balsillie had championed a bold strategy to re-establish the company’s place at the forefront of mobile communications. The plan was to push wireless carriers to adopt RIM’s popular BlackBerry Messenger (BBM) instant messaging service as a replacement for their short text messaging system (SMS) applications – no matter what kind of phone their customers used.It was a novel plan. If RIM could get BBM onto hundreds of millions of non-BlackBerry phones, and charge fees for it, the company would have an enormous new source of profit, Mr. Balsillie believed. “It was a really big idea,” said an employee who was involved in the project.But the plan ran into stiff opposition at senior levels. Not long after Mr. Heins took over as RIM’s CEO in January, 2012, he killed it, with Mr. Lazaridis’s support.That was it for Mr. Balsillie. Weeks later, he resigned from the board and cut his ties to the company.“My reason for leaving the RIM board in March, 2012, was due to the company’s decision to cancel the BBM cross-platform strategy,” Mr. Balsillie said in a brief statement to The Globe and Mail, his first public comments on his departure. He declined a request for an interview.Mr. Lazaridis, who declined to speak about board matters, resigned as a director this past March after delaying his retirement by a year at the board's request.Now, BlackBerry’s future is in doubt. This week, Fairfax Financial Holdings Ltd., a Toronto-based investment company, announced a plan to lead a $4.7-billion takeover of the company. The offer is conditional, and requires a group of so-far uncommitted institutional investors to back Fairfax and provide financing.The company’s near-collapse is a painful situation for Mr. Lazaridis, a gifted engineer who co-founded RIM in a tiny Waterloo office above a bagel shop in 1984.“It’s really hurting me,” he said in an interview. “I can’t imagine what the employees must be thinking. Everyone is talking about the most likely scenario being that it will be broken up and sold off for parts. What will happen to the Waterloo region, or Canada? What company will take its place?”Competition risingMike Lazaridis was at home on his treadmill and watching television when he first saw the Apple iPhone in early 2007. There were a few things he didn’t understand about the product. So, that summer, he pried one open to look inside and was shocked. It was like Apple had stuffed a Mac computer into a cellphone, he thought.To Mr. Lazaridis, a life-long tinkerer who had built an oscilloscope and computer while in high school, the iPhone was a device that broke all the rules. The operating system alone took up 700 megabytes of memory, and the device used two processors. The entire BlackBerry ran on one processor and used 32 MB. Unlike the BlackBerry, the iPhone had a fully Internet-capable browser. That meant it would strain the networks of wireless companies like AT&T Inc., something those carriers hadn’t previously allowed. RIM by contrast used a rudimentary browser that limited data usage.“I said, ‘How did they get AT&T to allow [that]?’ Mr. Lazaridis recalled in the interview at his Waterloo office. “ ‘It’s going to collapse the network.’ And in fact, some time later it did.”Publicly, Mr. Lazaridis and Mr. Balsillie belittled the iPhone and its shortcomings, including its short battery life, weaker security and initial lack of e-mail. That earned them a reputation for being cocky and, eventually, out of touch. “That’s marketing,” Mr. Lazaridis explained. “You position your strengths against their weaknesses.”Internally, he had a very different message. “If that thing catches on, we’re competing with a Mac, not a Nokia,” he recalled telling his staff.RIM soon earned a chance to show up its new rival. RIM’s early smartphones had been a hit for Verizon Wireless, one of the biggest U.S. wireless players. Frozen out of the iPhone – Apple had signed an exclusive deal with AT&T – Verizon executives approached RIM in June, 2007, and asked if it could develop “an iPhone killer.” The product would need to have a touchscreen with no physical keyboard. Verizon would back the U.S. launch with a massive marketing campaign.RIM executives jumped at the chance. At one management meeting, Mr. Balsillie called it RIM’s most important strategic opportunity since the launch of its two-way e-mail pager.The product was the BlackBerry Storm. It was the most complex and ambitious project the company had ever done, but “the technology was cobbled together quickly and wasn’t quite ready,” said one former senior company insider who was involved in the project.The product was months late, hitting the market just before U.S. Thanksgiving in 2008. Many customers hated it. The touchscreen, RIM’s first, was awkward to manipulate. The product ran on a single processor and was slow and buggy. Mr. Balsillie put on a brave face, declaring the launch to be “an overwhelming success,” but sales lagged the iPhone and customer returns were high.The Storm campaign didn’t seem so disastrous at the time: RIM was in the midst of a torrid global expansion. In August, 2009, Fortune crowned it the world’s fastest-growing company. A year after the Storm launch, market research firm comScore reported that four of the top five smartphones U.S. customers intended to buy in the next three months were BlackBerrys.But the Storm had failed to give Verizon Wireless the Apple-killer it coveted, and RIM soon abandoned the product. So the carrier turned to Google Inc. and its new operating system, Android, and built a massive marketing campaign around Motorola’s Droid phone in 2009 – at the expense of marketing dollars to support BlackBerry products. Verizon’s “iDon’t” campaign highlighted all the shortcomings of the iPhone that Android addressed with its consumer-friendly user interface.Rather than hurt Apple, the Droid and other Android-powered phones began to steal share first from Palm and Microsoft, and then RIM. By December, 2010, Android’s market share in the U.S. had grown to 23.5 per cent from 5.2 per cent a year earlier, as RIM’s dropped by 10 points, to 31.6 per cent, according to comScore. By late 2011, Android commanded 47.3 per cent of the U.S. market, while RIM had just 16 per cent.A shift by smartphone usersThis post-iPhone period was an era of strategic confusion for RIM. The overall state of the industry “was a bit schizophrenic,” said Patrick Spence, RIM’s former executive vice-president of global sales, who left in 2012. “There was a time when the [wireless] carriers tried to keep data usage predictable. Then it shifted to a period of trying to drive much more usage in different packages, when the iPhone became compelling.”If there were new rules of the game, RIM would require new tools. The summer after the Storm launched, Mr. Lazaridis bought Torch Mobile, a software development firm that created Internet browsers for mobile phones.But the process of moving, or “porting,” the Torch browser onto RIM’s highly-customized system proved complex and time-consuming. RIM’s technology was based on Java computer code and an operating system built in the 1990s, while the Apple and Android systems used newer software platforms and standards that made it easier to build friendlier user interfaces. “This really meant we were not positioned for the future,” Mr. Lazaridis said. In order to survive, RIM would have to change its DNA.RIM executives figured they had time to reinvent the company. For years they had successfully fended off a host of challengers. Apple’s aggressive negotiating tactics had alienated many carriers, and the iPhone didn’t seem like a threat to RIM’s most loyal base of customers – businesses and governments. They would sustain RIM while it fixed its technology issues.But smartphone users were rapidly shifting their focus to software applications, rather than choosing devices based solely on hardware. RIM found it difficult to make the transition, said Neeraj Monga, director of research with Veritas Investment Research Corp. The company’s engineering culture had served it well when it delivered efficient, low-power devices to enterprise customers. But features that suited corporate chief information officers weren’t what appealed to the general public.“The problem wasn’t that we stopped listening to customers,” said one former RIM insider. “We believed we knew better what customers needed long term than they did. Consumers would say, ‘I want a faster browser.’ We might say, ‘You might think you want a faster browser, but you don’t want to pay overage on your bill.’ ‘Well, I want a super big very responsive touchscreen.’ ‘Well, you might think you want that, but you don’t want your phone to die at 2 p.m.’ “We would say, ‘We know better, and they’ll eventually figure it out.’ ”Trying to satisfy its two sets of customers – consumers and corporate users – could leave the company satisfying neither. When RIM executives showed off plans to add camera, game and music applications to its products to several hundred Fortune 500 chief information officers at a company event in Orlando in 2010, they weren’t prepared for the backlash that followed. Large corporate customers didn’t want personal applications on corporate phones, said a former RIM executive who attended the session.Meanwhile, it turned out consumers didn’t care so much about battery life or security features. They wanted apps. Apple’s iOs and Google’s Android systems were relatively easy for outside software developers to use, compared to BlackBerry’s technically complicated Java-based system.Blackberry’s apps looked “uglier” than those programmed in more modern languages, and the simulator used to test the apps often didn’t recreate the actual experience, said Trevor Nimegeers, a Calgary-based entrepreneur whose software company, Wmode, has developed apps for BlackBerry. Further, RIM exerted tight control over developers before it would sign off on their apps for use on BlackBerrys, stifling creativity. “Developers wanted to be embraced, not controlled,” Mr. Nimegeers said. As a result, hot apps such as Instagram and Tumblr bypassed BlackBerry.A split companyOne key to RIM’s early success was its corporate structure. It is unusual for a company to have two CEOs – Mr. Lazaridis focused on engineering, product management and supply chain, while Mr. Balsillie looked after sales, finance and other corporate functions – but for a long time, it worked. Mr. Lazaridis’s side of the shop made the phones, and Mr. Balsillie’s sold them. The two men were collegial and collaborative.Below the top executives, however, the two sides of the company didn’t always get along. And as the company grew into a leviathan with $20-billion in annual sales, the structure sometimes made it difficult to get definitive decisions or establish clear accountability. That contributed to a chronic problem for RIM: speed. “They were always slow to market, and there were always delays in launching,” said James Moorman, an analyst with S&P Capital IQ Equity Research. “It was compounded by miscalculating the speed at which the consumer market changed.”Sometimes, feedback from customers that might inspire changes would die at middle management, because senior executives didn’t want to bring it to Mr. Lazaridis, a former insider said.The split company also lost a major unifying force when chief operating officer Larry Conlee retired in 2009. Mr. Conlee was a whip-cracker who held executives to account for decisions and deadlines, establishing a project management office. Many insiders agreed that after he left, a slack attitude toward hitting targets began to permeate the company. “There was a gap” after Mr. Conlee’s departure, Adam Belsher, a former RIM vice-president, told The Globe last year. “There was no real operational executive on the product side that would really get teams to hit deadlines.”After relying on its own technology for so long, Mr. Lazaridis decided the company’s next advance would come from outside. In April, 2010, RIM announced a deal to acquire Ottawa-based QNX Software, a cutting-edge software maker that would provide the building blocks for the BlackBerry 10 operating system – the new platform Mr. Lazaridis knew the company needed.QNX was a specialist in industrial controls that used up-to-date software tools to run applications ranging from 911 call centres to wireless broadband services in vehicles. Its technology was the perfect core for smartphones and tablets, RIM’s leaders felt.Mr. Lazaridis decided to take a page from the business strategy book The Innovator’s Dilemma by Clayton Christensen. The book outlines how established organizations that succeeded against challengers often did so by allowing small, cloistered teams to develop their own disruptive products, free from the influence of the rest of the organization.Mr. Lazaridis decided he would isolate the QNX team and get them to focus solely on the new operating system, while leaving existing programmers to work on products for its existing platform, BlackBerry 7. Eventually he hoped QNX, led by its CEO Dan Dodge, would retrain his entire organization.But first, RIM had to answer a key question: If it wanted to remake the BlackBerry on the QNX system, what was the best way to do that? Should it move over some of its old Java-based applications, or rewrite them all from scratch? If the company abandoned Java altogether, what would it mean for third-party developers who used it?These were not easy decisions. Discussions among the senior leaders in Mr. Lazaridis’ organization dragged on for a year – far too long, according to several insiders.Eventually, the decision was made: BlackBerry 10 would be built from scratch. The problem with that approach was that a new team was being entrusted to recreate the BlackBerry. Those who had created the original system were still working on devices for the BlackBerry 7 platform. Once again, the company was split.“We had bought a powerful operating system and needed to move to it. But the BB7 was late,” Mr. Lazaridis said. “Every week, I was getting requests for more hires, more resources. The conundrum was, how do I pull resources off the BB7 to rewrite all the apps on top of QNX?”PlayBook painThe QNX team’s first assignment was to work on an operating system for the PlayBook, RIM’s answer to Apple’s successful iPad tablet. Mr. Lazaridis saw the work as a precursor to the BlackBerry 10 line of smartphones and was impressed by what the team brought to the product. “It helped our developers experience the power and elegance of QNX,” he said.But the QNX team was overwhelmed and needed to draw heavily on the company’s other resources to complete the PlayBook. Similar issues arose later on the BlackBerry 10. The tablet, originally slated to come out in the fall of 2010, didn’t appear until April, 2011, and it failed to sell. It was an awkward accessory to RIM’s smartphones, and lacked e-mail, contacts and apps. Once again, RIM had missed the mark: Tablets that sold well worked as standalone devices, which the PlayBook wasn’t.Some questioned the wisdom of launching the PlayBook in the first place, feeling it was a needless and costly distraction. And the decision to isolate QNX also created tensions and morale problems: Those who weren’t on the team worried about their future.“To me, the most logical thing would have been to integrate the operating system organizations into one,” said one senior executive who was caught up in the fray. “Then you’d have a whole team, not 150 people sitting around saying, ‘I don’t know what I’m going to do next,’ and another 150 people saying ‘I’m over my head.’ ”Meanwhile, RIM’s lack of an advanced smartphone meant that it continued to bleed market share to Apple and Android, especially in the United States. In December, 2010, Verizon Wireless announced it would invest in fourth generation (4G) LTE technology to accommodate the growing demands of customers who wanted to surf the Internet on their phones. It signalled to device makers that it would look to feature 4G smartphones in its marketing.RIM’s 4G phone effort was the BlackBerry 10, but it was far from ready. RIM executives tried to make an engineering argument to carriers that 4G technology was no more efficient than 3G, and that its Bold phones were just fine. Mr. Lazaridis, Mr. Heins and chief technology officer David Yach “were trying to reshape the argument because they knew our products couldn’t go there,” a former executive said. “It was a fight to stay in [promotional] programs with carriers. We lost channel support and feature ads.”The PlayBook debacle and mounting delays of the BlackBerry 10 harmed the organization in other ways.For years, Mr. Yach and Mr. Lazaridis had enjoyed a close working relationship. But as the well-regarded Mr. Yach began to question the company’s ability to hit deadlines on products, his views were dismissed and he was made to feel he wasn’t a team player, damaging their relationship, observers said. He left the company in early 2012.The PlayBook flop merely added to the sense of a company in decline; 2011 became a signNow turning point for RIM. As it became clear the brand was getting trounced in the market, and the BlackBerry 10 project was hit by signNow delays, the stock plunged, falling from $69 (Canadian) in February to less than $15 by the year’s end.The pressure mounted on Mr. Balsillie, Mr. Lazaridis and the board. In January, 2012, they stepped aside as co-CEOs and handed it over to Thorsten Heins, a German executive who had run the company’s handset division.Almost immediately, there was division about how to roll out the BlackBerry 10. The original strategy had called for the company to launch an all-touchscreen version first, because sales were still going well for the company’s BlackBerry 7 keyboard phone.But by 2012, sales of BlackBerry 7 phones had lost steam, and Mr. Lazaridis, now deputy chairman, felt the company should switch its priority to getting a keyboard version out, to meet the demand from BlackBerry die-hards.“This is our bread and butter, our iconic device,” he told an executive at the company. “The keyboard is one of the reasons they buy BlackBerrys.”Mr. Heins’s new management team held firm, sources close to the board said. “They believed everything was going to full touch” and that the QNX-designed system was clearly superior to what was available on other mobile operating systems.To Mr. Lazaridis, abandoning the company’s competitive advantage in the hopes consumers would embrace yet another touchscreen was too risky a strategy, setting up the showdown at the board last year. In the end, management agreed to continue developing the Q10 keyboard phone. But the all-touchscreen Z10 would be launched first.By the time the first BlackBerry 10 smartphones were unveiled in January of this year, market observers generally agreed that the products were two years too late – a view widely shared among many senior RIM insiders.“Buying QNX was the right play ultimately,” said Mr. Spence. “But we didn’t make the turn fast enough. Everyone underestimated the complexity” involved in building the new system.A BBM planFor 20 years, Jim Balsillie and Mike Lazaridis operated in tandem, building an increasingly successful partnership that allowed each other’s strengths to flourish.They shared an office in their early years, even possessing each other’s voice mail passwords.As RIM grew, they worked in separate buildings but spoke several times a day. “They had a relationship I wish I had with my wife,” one mid-level executive said.But they had different personalities and their lives seldom intersected outside the office. They have barely spoken since leaving the company.For Mr. Lazaridis, science was both a job and a pastime. Mr. Balsillie was brash, competitive and athletic, and wore his reputation for being aggressive, even bullying in meetings, as a badge of honour. If anything, he viewed that outward toughness as a job requirement, not unlike tech CEOs such as Steve Ballmer at Microsoft Corp. or Apple’s Steve Jobs. “Show me how else you build a $20-billion company,” he once confided to a colleague. “If I was Mr. Easy-going, they would kill BlackBerry.”The two rarely disagreed on key strategic moves – until their last year together. Mr. Lazaridis believed BlackBerry 10 would herald RIM’s renaissance. Mr. Balsillie wasn’t so sure.Mr. Balsillie was concerned that Google had commoditized the smartphone market by making its Android operating system available for free to any handset maker. By 2011, wireless carriers were warning him that they would be ordering fewer BlackBerry products unless he dropped his prices to match rival manufacturers.So Mr. Balsillie pushed an alternative plan.The idea started with Aaron Brown, the executive who oversaw the services division at RIM. By 2010, this division was earning $800-million per quarter in revenue from the monthly service access fee it charged mobile carriers for every BlackBerry subscriber. More than 90 per cent of that was profit. Carriers tried to chip away at those fees – Google and Apple didn’t charge them – but RIM always pushed back. Mr. Balsillie was particularly insistent on keeping the service fees. But the executives knew the company’s weakening position in devices would increase pressure on services revenues as well.Even after its terrible year in 2011, RIM still had several advantages, including close relationships with the world’s major carriers. It also had BlackBerry Messenger.RIM developers created the BBM app in 2005 to enable users to communicate not by e-mail but by using their devices’ “personal identification numbers” or PINs. It was the first instant messaging service built for wireless devices, and it caught on quickly. It was reliable, free, always on and users could send as many messages as they wanted at no extra cost, unlike basic text messages. PINs were random codes, not phone numbers or e-mail addresses, enhancing privacy. That made BBM extremely popular in countries where citizens didn’t enjoy as many freedoms as Western democracies, and helped drive handset sales there.BBM’s developers added a few clever elements that also made it addictive. For example, users would know when a message had been delivered and when it had been read, marked D and R. Today there are 60 million monthly active users.But BBM only worked on BlackBerrys. As Apple and Android took off, BBM knock-offs appeared that could function on those devices, including Kik Interactive Inc., founded by Ted Livingston, a former RIM co-op student. Today Kik, boasts 85 million users, more than BlackBerry (which sued Mr. Livingston for allegedly copying its program). Others, such as WhatsApp, are even larger. Instant messaging “is the killer app of the mobile era,” Mr. Livingston said. “We think there will be a Google or Facebook-sized company that comes out of this category.”RIM’s Mr. Brown believed he could tap into this unfolding trend. While working with Mr. Balsillie on other projects, around late 2010 and early 2011, he began to talk up the concept of offering BBM on other mobile platforms.Mr. Balsillie loved it. At the time, some carriers were pushing for rebates on their monthly service fees. Mr. Brown was willing to comply if the carriers would agree to open new parts of their business to RIM. He and Mr. Balsillie struck upon an idea: Why not give carriers the opportunity to offer BBM to all their customers – no matter what devices they used?Most wireless executives were not fans of instant messaging services and other “over-the-top” apps such as Skype because they eroded the carriers’ revenue from text messaging.To counter that threat, carriers banded together to develop a standardized “rich communication service” (RCS) platform that would enable their customers to exchange text messages, videos, games and other digital information. But the initiative has gained little traction; one commentator recently labelled RCS a “zombie technology.”SMS 2.0Mr. Balsillie began floating the idea that carriers could instead offer BBM as their own enhanced version of text messaging, generating revenue for carriers while providing a cut for RIM. He called it “SMS 2.0.” (SMS stands for “short message service.”) RIM would agree to reduce the fees it charged for services, in exchange for gaining access to hundreds of millions of non-BlackBerry users.He and Mr. Brown discussed several options. For example, carriers could offer BBM as part of a standard “talk and text” plan for entry-level smartphone users. Because of its extra functions, BBM would save customers from having to buy a data plan.Or, carriers could offer an expensive plan that included BBM and other offerings from BlackBerry, including one gigabyte of cloud storage on which they could keep photos or songs. The carriers could then sell extra services such as radio through BBM. It would also make the wireless companies’ customers “stickier” – less likely to defect – since they couldn’t move stored data to rival mobile carriers as easily.The SMS 2.0 plan was a throwback to RIM’s move a decade earlier to form partnerships with mobile providers and share revenues. It was a chance to make BBM the dominant chat messaging service, and would have created a new storyfor the BlackBerry brand.A few carriers responded positively to Mr. Balsillie’s initial entreaties and by mid-2011, he was calling SMS 2.0 the company’s top strategic priority.To round out the strategy, and build a suite of cross-platform services, RIM made a few acquisitions, such as instant messaging firm LiveProfile. The service had about 15 million users and worked on Apple and Android devices, giving BBM the entrée it needed to those platforms.But the plan deeply divided the company. BBM was still an important driver of BlackBerry sales. Making it widely available to competitors represented an added threat to RIM’s faltering handset business, led by Mr. Heins at the time. Many inside the company felt a cross-platform BBM made sense, but only when BlackBerry 10 was out. Mr. Balsillie and proponents of his plan felt that would be too late.“It’s fair to say [the risk to handset sales] was a shared concern of everybody I spoke to,” said former RIM executive Mr. Spence. “But it was hard to deny the fact [carriers’ text messaging] revenue was declining. These carriers were looking for a solution and this was a potential solution.”One former executive felt Mr. Balsillie was overestimating the revenue potential of his software-driven strategy. As Mr. Balsillie talked up SMS 2.0, Mr. Heins and his team increasingly cast doubt on it internally. “He was absolutely canvassing behind the scenes working to kill it,” said one company insider.As for Mr. Lazaridis, he was supportive of launching BBM for rival operating systems, but was concerned about the costs and risks involved in building out the SMS 2.0 strategy, said a source close to the board. “We weren’t in a position to be investing in free services that required massive capital expenditure [and could provide] zero payback for maybe a few years if we’re successful,” the source said. Like others, Mr. Lazaridis worried about handset sales.But Mr. Balsillie was increasingly convinced that SMS 2.0 was the way to go. After pitching the plan to CEOs of 12 of the largest wireless carriers in the world in late 2011, he believed he could sign up at least one major U.S. carrier – insiders say AT&T was interested – as well as Telefonica and one or two other European carriers. That’s all it would take, he felt, to convince others to adopt BBM en masse.But other RIM executives who were part of the growing SMS 2.0 team also encountered resistance.Mr. Balsillie was pushing to formally launch SMS 2.0 at an industry conference at the end of February, 2013. But with the company under mounting pressure to overhaul its top leadership, he and Mr. Lazaridis handed the reins to Mr. Heins in late January.A few weeks later, Mr. Heins killed the SMS 2.0 strategy, backed by Mr. Lazaridis.“We had to get the BlackBerry 10 out, and we couldn’t be distracted,” said a source close to the board. “Everything else was shelved. And if that meant getting rid of strategies that didn’t fit, or weren’t complete, or required resources, I think [Mr. Heins] did the right thing.”The Globe and Mail requested interviews with Mr. Heins and with Barbara Stymiest, the chair of the board. The company declined, but agreed to agreed to provide answers to written questions.Asked why he shelved SMS 2.0, Mr. Heins said in an e-mailed response: “There are so many [instant messaging] alternatives in the marketplace that we wanted to be careful to launch only when we felt we could clearly differentiate our offering.”Mr. Balsillie, no longer an executive but still a board member, urged directors to reconsider, but they backed the new CEO. Mr. Balsillie couldn’t abide by the decision. He resigned from the board in late March, then sold all his stock. Few people knew the reason for his departure, including his long-time co-CEO, Mr. Lazaridis.BlackBerry did launch a version of its BBM application last weekend for iPhones and Android devices, but simply as a stand-alone app. Andrew Bocking, the executive who oversees BBM, said that with built-in capabilities to have group chats, share photos, calendar items and other features, “it really takes BBM to a whole other level … I believe there is an opportunity for a dominant player in instant messaging and there will be one winner-take-all.”To those who championed the SMS 2.0 strategy, most of them now gone, RIM should have been well on its way there already.A fizzled launchFinally, close to six years after Apple unveiled the iPhone, the long-awaited BlackBerry 10 made its debut at a glitzy launch event in January, featuring singer Alicia Keys as the company’s “global creative director.” It was a minor detail in a much larger story, but the made-up title and meaningless job irked some who wondered why the company was distracting itself with celebrity endorsements while in the fight of its life.The Z10 device itself won a number of positive reviews. The New York Times’ David Pogue, who previously had predicted that the BlackBerry was doomed, began his review: “I’m sorry. I was wrong.” But eight months later, it’s hard to see the launch as anything other than a total business failure, given the sheer volume of unsold smartphones now written off.The marketing campaign was confusing and vague: An ad that ran during the Super Bowl failed to explain what made the product distinct. A source close to the board said directors weren’t shown the ad before it ran, and some didn’t understand the content or the slogan, “Keep Moving.” There were no lineups, and no buzz for the product – nothing like the frenzy of publicity that seems to surround the launch of each new version of the iPhone.Once again, the market had shifted, and there was little demand for the Z10 in an era where sophisticated operating systems were commonplace and phones were getting cheaper. The one advantage the BlackBerry may have had over its rivals – a physical keyboard – wasn’t present in the first model to hit the market.“The only people still clamouring for a new smartphone from BlackBerry were in it for the keyboard,” said S&P’s Mr. Moorman. “Then they come out with a touchscreen. Anyone who wanted a touchscreen was already gone.”As it turns out, both Mr. Balsillie and Mr. Lazaridis were proven right. It was hard enough to compete in a commoditizing smartphone market. Leading with the wrong product on top of that only made BlackBerry’s task more hopeless. Mr. Heins’s strategic errors only compounded the challenging situation he had inherited.The product was difficult to sell for other reasons. One company insider said it could take close to an hour for young sales staff to demonstrate the product in dealer stores.And many long-time BlackBerry users found that the new system was too different from the classic BlackBerry experience for their liking. Many of the little “moments of delight,” as they are called in the company, were forgotten or overlooked by the QNX developers who lacked ties to the company’s past. For example, users can’t hit “u” and look at the last unread message in their inbox, nor can they easily shift to the next or previous e-mail, as they could on older BlackBerrys. Pocket-dialling is a constant hazard.Meanwhile, the company was slow to provide service to business users – such as helping them to transfer applications they had written for the old BlackBerry system. Software developers were left with dead-end investments after learning they would have to rewrite their apps for the new system if they wanted to remain part of the BlackBerry world. Many simply didn’t bother.“The decisions we made over the last two years were made within the context of a volatile, competitive and ever-changing marketplace – and always with the goal of delivering the vital technology that our customers need,” Mr. Heins said in a written response to questions about the success of the BlackBerry 10 launch. While he called the launch “a signNow accomplishment and one that involved the reinvention of our company,” he acknowledged it “did not meet our expectations.”As for Mr. Lazaridis, he has not given up on the enterprise he founded 29 years ago.He is still a minority shareholder in BlackBerry, and continues to be the subject of rumours he may join a group to buy out his former company.Mr. Lazaridis declined to discuss any such plans, but it is clear he believes the BlackBerry story is not over.“Many companies go through cycles. Intel experienced it, IBM experienced it, Apple experienced it. Our job was to reinvent ourselves, which we all believed BB10 would do,” he said.“The fact that a Canadian company was able to compete in that space with two of the largest tech companies in the world is a big deal. People counted IBM, Apple and other companies out only to be proven wrong. I am rooting that they are wrong on BlackBerry as well.”
-
What types of websites are most likely to contain viruses or malware?
What types of websites are most likely to contain viruses or malware? Websites that sell ads from real-time ad broker networks. By far, by far, the most common way for viruses and malware to be spread from Web sites is through poisoned ads.What is the most dangerous website?So be careful when you visit these sites, since your computer may not come out in good health, after your visit.#1 Ucoz. com. Description: Site hosting. Global rank in malware hosting: 14.#2 sapo .pt.#3 Amazonaws .com.#4 Blogspot .de.#5 4shared .com.#6 sendspace .com.#7 comcast .net.Can certain websites cause viruses?Yes, it's entirely possible to get infected by simply visiting a website. Most commonly via what we call "Exploit Kits". Right now, EK are used to deliver a lot of dangerous malware (such as banking trojans and Cryptoware) to computers worldwide. So using a standard Antivirus and Antimalware won't cut it.Can you get a phone virus from a website?How phones get viruses. The most common way for a smartphone to get a virus is by downloading a third-party app. However, this isn't the only way. You can also get them by downloading Office documents, PDFs, by opening infected links in emails, or by visiting a malicious website.Threat 1 >> Malicious Flash files that can infect your PCThe Place: Websites that use FlashsignNow's Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser's cookies, Flash cookies get left behind.If You Have to Go There: To help protect against Flash-based attacks, make sure you keep your Flash browser plug-ins up-to-date. And you can configure the Flash plug-in to ask you before it downloads any Flash cookies.Threat 2 >> Shortened links that lead you to potentially harmful placesThe Place: TwitterScammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.And it's very simple to hide malware or scams behind shortened URLs. A shortened link that supposedly points to the latest Internet trend-du-jour may be a Trojan horse in disguise.If You Have to Go There: Simply don't click links. Of course, that takes some of the fun out of Twitter. The other option is to use a Twitter client app. TweetDeck and Tweetie for Mac have preview features that let you see the full URL before you go to the site in question.Some link-shortening services, such as Bit.ly, attempt to filter out malicious links, but it seems to be a manual process, not an automatic one. TinyURL has a preview service you can turn on.Threat 3 >> E-mail scams or attachments that get you to install malware or give up personal infoThe Place: Your e-mail inboxAlthough phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they're becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something's amiss is the sender's e-mail address.If You Have to Go There: Don't trust anything in your inbox. Instead of clicking on links in a retailer's e-mail, go directly to the retailer's site.Threat 4 >> Malware hiding in video, music, or software downloadsThe Place: Torrent sitesTorrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files--they may be malware in disguise.Ben Edelman, privacy researcher and assistant professor at Harvard Business School, thinks torrent sites are the most dangerous places to visit, since they don't have a business model or reputation to defend (by comparison, many porn sites rely on being deemed trustworthy). "The [torrent] customers, they really don't want to pay," he says.If You Have to Go There: It's probably best to avoid torrent sites entirely, given their untrustworthy content, but if you must visit, use a secondary PC to protect your main system. Use antivirus software, and keep it updated. Scan downloaded files and wait a couple of days before opening them. Brand-new malware can be tricky to catch, but the delay in opening may allow your antivirus software to get the necessary signatures.Threat 5 >> Malware in photos or videos of scantily clad womenThe Place: ‘Legitimate' porn sitesPorn sites have a reputation of being less secure than mainstream sites, but that assumption doesn't tell the whole story. "There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it's a given that you'll be attacked at some point," says Roger Thompson, chief research officer with security firm AVG. "Unfortunately, staying away from those sites won't keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers."And as mentioned earlier, many porn sites operate as actual, legitimate businesses that want to attract and retain customers. That said, it may be hard to tell the "legit" porn sites from malware-hosting sites that use porn as a lure.If You Have to Go There: Be suspicious of video downloads, or sites that require you to install video codecs to view videos (see the next threat, below). Using tools like AVG's LinkScanner and McAfee's SiteAdvisor (or SiteAdvisor for Firefox) can help you weed out the malicious sites.And, again, consider visiting such sites on a secondary machine. You don't want your browser history on the family PC.Threat 6 >> Trojan horses disguised as video codecs, infecting your PC with malwareThe Place: Video download sites, peer-to-peer networksIf you watch or download video online, you've likely been told to download a video codec--a small piece of software that provides support for a type of video file--at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.If You Have to Go There: Your safest option is to stick with well-known video sites such as YouTube and Vimeo. And for catching up on the latest episodes of your favorite TV shows, sites and services like Hulu, http://TV.com, ABC Home Page - ABC.com, and iTunes are safer than peer-to-peer networks.Threat 7 >> Geolocation--your smartphone and perhaps other parties know where you areThe Place: Your smartphoneThe smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use--or abuse--of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called Please Rob Me showed that--for a time--a stream of FourSquare check-ins indicated that a person was away from their home (the site's goal, mind you, wasn't to condone theft, but to raise awareness of the issue).Apple recently updated its privacy policy to reflect changes in how it handles location data in iOS 4. The policy now states that "to provide location-based services on Apple products, Apple and our partners and licensees may collect, use and share precise location data." You can read more on Apple's new privacy terms and what they mean for you.If You Have to Go There: Be particular about the location-based sites, apps, and services that you use. As shown in the screenshot at right services such as Yelp provide good examples of useful location-aware apps. On the other hand, weigh the privacy implications of services like FourSquare or the new Facebook Places feature, and consider how much you feel comfortable divulging. (Read more on how to retain privacy on FourSquare and Facebook Places.)Threat 8 >> 'Poisoned' search engine results that go to malware-carrying WebsitesThe Place: Search enginesSearch engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for "Cameron Diaz and screensavers" had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.If You Have to Go There: Pick and choose which sites to go to. Don't just blindly click search results; check each URL first to make sure that it really leads to the site you want.Threat 9 >> Malicious PDFs that try to fool you into installing malwareThe Place: Hacked Websites, plus your inboxAs Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in signNow is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in signNow and signNow; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.A newer variant takes an otherwise innocent-looking PDF document and inserts malware into it. signNow may pop up an alert asking if you want to run the malware, but hackers can edit those messages to trick you into opening the file.How serious is this problem? In 2009, attacks using malicious PDFs made up 49 percent of Web-based attacks, according to security firm Symantec.If You Have to Go There: First, always make sure that you're running the latest version of signNow.Threat 10 >> Malicious video files using flaws in player software to hijack PCsThe Place: Video download sitesAttackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often "malformed" video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.If You Have to Go There: Keep your player software up-to-date. Apple and Microsoft periodically release patches for QuickTime and Windows Media Player, respectively. Avoid downloading videos at random. Stick to well-known video sites such as YouTube, or to download services like iTunes.Threat 11 >> Drive-by downloads that install malware when you visit a siteThe Place: Hacked legitimate sitesA drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.If You Have to Go There: The first thing to do is to keep your security software up-to-date, and to run regular malware scans. Many security suites can flag suspicious downloads.Threat 12 >> Fake antivirus software that extorts money--and your credit card informationThe Place: Your inbox, hacked legitimate sitesFake antivirus programs look and act like the real thing, complete with alert messages. It isn't until you realize that these alerts are often riddled with typos that you know you're in trouble.Most fake antivirus software is best described as extortionware: The trial version will nag you until you purchase the fake antivirus software-which usually does nothing to protect your PC. Once you send the criminals your credit card information, they can reuse it for other purposes, such as buying a high-priced item under your name.Threat 13 >> Fraudulent ads on sites that lead you to scams or malwareThe Place: Just about any ad-supported WebsiteHey--ads aren't all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google's Sponsored Links ad program and placing ads that looked like links to major companies' Websites."The bad guys have become very clever at exploiting online advertising networks, tricking them into distributing ads that effectively load malicious content--especially nasty, scaremongering pop-ups for rogue antispyware," says Eric Howes, director of research services for security firm GFI Software.If You Have to Go There: Most large sites, such as PCWorld - News, tips and reviews from the experts on PCs, Windows, and more, have ad sales departments that work frequently with a core group of large advertisers, so it's probably safe to click a Microsoft ad on the New York Times site. But as the Google Sponsored Links incident shows, nothing is entirely fail-safe.Threat 14 >> Questionable Facebook appsThe Place: FacebookFacebook apps have long been an issue for security experts. You don't always know who's developing the apps, what they're doing with the data they may be collecting, or the developers' data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer's hands.If You Have to Go There: Be selective about the apps you add to your profile--don't take every quiz, for example. Check your privacy settings for Facebook apps, as well: Click the Account drop-down menu in the upper-right corner of Facebook's site, select Privacy Settings, and then click Edit your settings under ‘Applications and Websites'. There, you can control which apps have access to your data, and which of your friends can see what information from apps (such as quiz results); you can also turn off Facebook apps altogether.Threat 15 >> Sites that lure you in, get you to sign up, then sell your e-mail address for spamThe Place: 'Free electronics' sitesYou've no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It's easy! These sites aren't typically dangerous in the classical sense--you probably won't get infected with malware--but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.If You Have to Go There: Read the privacy policies. And then read them again. Also, beware of privacy policy loopholes--even though a site says that it won't sell your private data to third parties, depending on the language of the policy, they may still be able to give your information to "affiliates."Threat 16 >> Phishing 2.0 on social networks that tricks you into downloading malware or giving your Facebook login information to a criminalThe Place: Social networksQuestionable Facebook apps and malicious shortened links aren't the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person's Facebook account, then use it to lure that person's friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information--thereby giving scammers one more Facebook account to hijack."One of the bigger dangers currently facing users is malware, adware, and spyware spread through social networks like Facebook and Twitter," says Eric Howes, director of malware research with Sunbelt Software. "Users may receive spam via these networks offering them free deals, links to interesting videos, or even widgets to enhance their Facebook profiles. In many cases what's really being pushed on users is adware, spyware, or even malicious software that can exploit users' PCs."If You Have to Go There: Don't trust every link posted to Facebook, even if one of your friends posted it. Be especially suspicious if the post is out of the ordinary for that person. Check the person's wall or Twitter @-replies to see if anyone is concerned that the person's account has been compromised.And if you suspect that your account has been hijacked, change your password immediately. Both Facebook and Twitter have resources to help you keep up-to-date on the latest threats on both sites. Facebook users should visit its security page; if you're on Twitter, be sure to follow @spam and @safety for Twitter security best practices.Threat 17 >> Oversharing--exposing too much personal information on your social network profilesThe Place: Social networksHow many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn't just a matter of getting a little too personal--it can leave your private information viewable to the general public. But it's avoidable."There is a subtle danger that few people understand with the social networking sites, and that is the idea of information leakage," says AVG's Roger Thompson. "People, particularly teens, put all sorts of information online, without realizing that many more people than just their friends can see that data."Oversharing could very well lead to more serious privacy issues further down the road, Thompson adds. "As today's young teens signNow an age to apply for a credit card, I fully expect an onslaught of fraudulent card applications on their behalf, because they unwittingly divulged so much information. Harvesting is going on now, and we have no idea who is doing the harvesting."If You Have to Go There: This particular threat is relatively easy to avoid, in that a little common sense can go a long way: Just be mindful of what you post. Do you really need to publish your home address and phone number to your Facebook profile?Finally, be certain to check your privacy settings to make sure that you're not divulging your deepest, darkest secrets to all 500 million Facebook users.
Trusted esignature solution— what our customers are saying
be ready to get more
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
When a client enters information (such as a password) into the online form on , the information is encrypted so the client cannot see it. An authorized representative for the client, called a "Doe Representative," must enter the information into the "Signature" field to complete the signature.
What is an eSign message?
An eSign message is a digital representation of the "signature" of your digital signature (see the section below on eSignature) on an e-mail message by adding a "dots" character.
Why do I need an eSign message on all of my digital signatures?
Every digital signature is unique; if you sign any file with the same signature, that signature will be the same across all of those files; if you sign with a signature and sign another signature with the same signature, they will both look the same.
If your signature appears on a file, and its digital signature appears on a message, then the file has to be signed by that same key (keystore for example, or OpenPGP for example). That way, it can be verified that you've not tampered with or modified any data that was in the same file; if it isn't, your message is invalid and will be rejected.
Why do I need to add a dot in the eSign message?
The dot (period) in eSign message refers to one "dot" that is placed in place of your signature in the original message. For example, if a message has a digital signature that says something is signed by x,y,z, then the eSign message will say "x and y and z have signed this message with the signature x and y and z". It's important to note that when you use an eSign message, you will have the same signature in both the message and the signature.
If you want to change the signature, then you must delete and reSign the eSign message, then delete and reSign the original message.
What does it mean...
How to switch to amend and sign pdf?
You can also read up on how to read or create a document in the pdf and then convert it to text using the pdf converter.
Download pdf to text converter
Can you make the document in more than one language or add new text to this page?
Can you change the text and fonts in this page?
Can you change the font and color?
Can you convert this page from one language to another language?
Can you add images?
Can you include some images in your document?
Are there any text links?
Are there any images at the bottom of this page?
Do you have a document you would like us to create?
Can you convert this page from pdf to txt?
Can you translate this page from another language or a different language?
Is this the page you are looking for?
Is this the page you want to use on your website?
Can you add a picture to this page? Please see the section above.
Can you add an audio or video to this page?
Can you copy the text from this page?
Can you move this page?
Can you move the images or text in this page?
Can you remove the text on this page?
Are you sure the page that you are looking for has a link? This is because many pages have hidden links. You may use the Search box on the top right corner of your screen or on the left side if you are using an internet explorer. Please search for any words that you can use to find out the link for this page.
Can you search for the link on this page?
Can you copy the words that have been entered or the text that has...
Get more for Draw eSignature Form iPad
- eSign Missouri Debt Settlement Agreement Template Online
- How Do I eSign Montana Debt Settlement Agreement Template
- Help Me With eSign New Mexico Debt Settlement Agreement Template
- eSign North Dakota Debt Settlement Agreement Template Easy
- eSign Utah Share Transfer Agreement Template Fast
- How To eSign California Stock Transfer Form Template
- How Can I eSign Colorado Stock Transfer Form Template
- Help Me With eSignature Wisconsin Pet Custody Agreement
Find out other Draw eSignature Form iPad
- Sample records form 497311747
- Mi a corporation form
- Sample transmittal letter for articles of incorporation michigan form
- New resident guide michigan form
- Satisfaction release or cancellation of mortgage by corporation michigan form
- Michigan release form
- Partial release of property from mortgage for corporation michigan form
- Michigan partial form
- Warranty deed for husband and wife converting property from tenants in common to joint tenancy michigan form
- Warranty deed for parents to child with reservation of life estate michigan form
- Warranty deed for separate or joint property to joint tenancy michigan form
- Warranty deed to separate property of one spouse to both spouses as joint tenants michigan form
- Fiduciary deed for use by executors trustees trustors administrators and other fiduciaries michigan form
- Warranty deed from limited partnership or llc is the grantor or grantee michigan form
- Michigan warranty deed form 497311763
- 2 trustees form
- Michigan warranty deed form
- Warranty deed for not for profit corporation to municipality michigan form
- Michigan trustee form
- Michigan survivorship form