Help Me With Sign Florida Banking Presentation
Contact Sales
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Discover the easiest way to Sign Florida Banking Presentation with our powerful tools that go beyond eSignature. Sign documents and collect data, signatures, and payments from other parties from a single solution.
Robust integration and API capabilities
Enable the airSlate SignNow API and supercharge your workspace systems with eSignature tools. Streamline data routing and record updates with out-of-the-box integrations.
Advanced security and compliance
Set up your eSignature workflows while staying compliant with major eSignature, data protection, and eCommerce laws. Use airSlate SignNow to make every interaction with a document secure and compliant.
Various collaboration tools
Make communication and interaction within your team more transparent and effective. Accomplish more with minimal efforts on your side and add value to the business.
Enjoyable and stress-free signing experience
Delight your partners and employees with a straightforward way of signing documents. Make document approval flexible and precise.
Extensive support
Explore a range of video tutorials and guides on how to Sign Florida Banking Presentation. Get all the help you need from our dedicated support team.
Industry sign banking kansas ppt easy
Keep your eSignature workflows on track
Make the signing process more streamlined and uniform
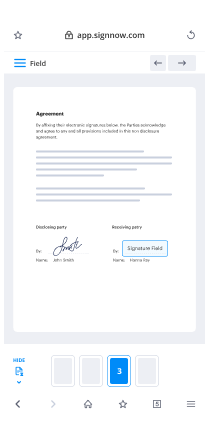
Take control of every aspect of the document execution process. eSign, send out for signature, manage, route, and save your documents in a single secure solution.
Add and collect signatures from anywhere
Let your customers and your team stay connected even when offline. Access airSlate SignNow to Sign Florida Banking Presentation from any platform or device: your laptop, mobile phone, or tablet.
Ensure error-free results with reusable templates
Templatize frequently used documents to save time and reduce the risk of common errors when sending out copies for signing.
Stay compliant and secure when eSigning
Use airSlate SignNow to Sign Florida Banking Presentation and ensure the integrity and security of your data at every step of the document execution cycle.
Enjoy the ease of setup and onboarding process
Have your eSignature workflow up and running in minutes. Take advantage of numerous detailed guides and tutorials, or contact our dedicated support team to make the most out of the airSlate SignNow functionality.
Benefit from integrations and API for maximum efficiency
Integrate with a rich selection of productivity and data storage tools. Create a more encrypted and seamless signing experience with the airSlate SignNow API.
Collect signatures
24x
faster
Reduce costs by
$30
per document
Save up to
40h
per employee / month
Our user reviews speak for themselves






-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
Trusted esignature solution— what our customers are saying
be ready to get more
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
When a client enters information (such as a password) into the online form on , the information is encrypted so the client cannot see it. An authorized representative for the client, called a "Doe Representative," must enter the information into the "Signature" field to complete the signature.
How to sign pdf on window?
- by nate
Submission information:
Posted:
Category: All
Theme: All
Species: Unspecified / Any
Gender: Any
Favorites: 0
Comments: 0
Views: 1191
Image Specifications:
Resolution: 765x904
Keywords:
furry little girl dog little girl
How to make electronic signature without a scanner?
I want to be able to make electronic signatures that I can't scan, and I know I'm supposed to make electronic signatures that I can scan and I don't want my signature to have to get scanned because that would be too difficult. But, to be honest, I don't even know how to make one of those things.
I would like to know how to make a computer keyboard that is easy to read without having to use a magnifier, and I know it doesn't have to have a keyboard on it. So, that's an easy one.
Another thing which, I'm really good at, is the "E" or "E-mail" button. That's a very important feature where I know I have to have it. I'm not even sure I can remember how I got it but I do have the ability to press the "E" button when someone says, "E-mail me," or I can press the "E" button and press "Enter" so I know I have "Email me," even if I don't have it or even if I don't have a computer with a "E-mail" button. I don't think I can do it all at once, I think I would have to do each one as part of it.
I know what you mean, I mean, I know if I say "Send an E-mail to the White House," even though I do have a computer with that "E-mail" button, I know that that "E-mail" button is not going to be on the computer, it's not going to be on my screen when I'm at home, it's not going to be on my screen when I'm on the airplane. So, if they send me a message, I don't know when I get that message, I don't know whether the computer is on or if I'm at home or if I'm on the airplane, I don't know how many...
Get more for Help Me With Sign Florida Banking Presentation
- Can I Sign Florida Car Dealer LLC Operating Agreement
- How Do I Sign Florida Car Dealer Month To Month Lease
- Sign Florida Car Dealer Quitclaim Deed Online
- Sign Florida Car Dealer Quitclaim Deed Computer
- Help Me With Sign Florida Car Dealer Month To Month Lease
- Sign Florida Car Dealer Quitclaim Deed Mobile
- Sign Florida Car Dealer Quitclaim Deed Now
- How Can I Sign Florida Car Dealer Month To Month Lease
Find out other Help Me With Sign Florida Banking Presentation
- Payroll correction review form g4s drmc security training
- Ss 4523 form
- Patient consent form phi patient consent form phi
- Beneficiary nomination form commonwealth
- Fillable online pubs usgs characteristics of streams and form
- Sanitation department rssc form fill online printable
- 7 top questions to ask before opening a bank account form
- Auburn favn form
- Informed consent for exercise treadmill test informed consent for exercise treadmill test
- Competition mail claim for rebate recipient created tax form
- Cdl holder self certification affidavit form
- T tess tor long formdocx
- Jefferson parish schools attendance referral form
- Dd form 1626 veterinary necropsy report checklist and
- Patient factors that affect quality of colonoscopy preparation form
- Gid 52 nt form
- Artist portal sony fill online printable fillable blank form
- Interior design questionnaire form
- Australia human rights commission form
- Application form for the returning officer position