910/2014 Signature Service Made Easy
Improve your document workflow with airSlate SignNow
Flexible eSignature workflows
Fast visibility into document status
Easy and fast integration set up
9102014 signature service on any device
Detailed Audit Trail
Strict protection standards
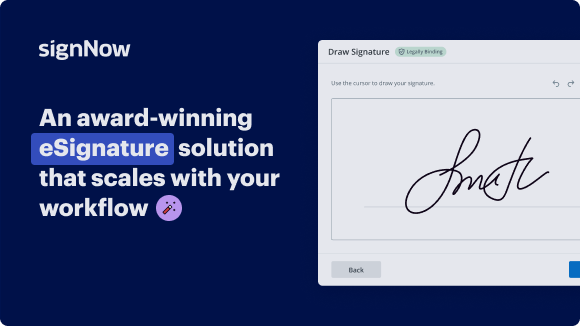
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — 9102014 signature service
Adopting airSlate SignNow’s electronic signature any company can enhance signature workflows and sign online in real-time, supplying an improved experience to customers and employees. Use 910/2014 signature service in a few simple steps. Our handheld mobile apps make work on the run achievable, even while offline! Sign contracts from any place worldwide and close up trades in no time.
Take a stepwise guide for using 910/2014 signature service:
- Log on to your airSlate SignNow account.
- Locate your document within your folders or upload a new one.
- Open the record and edit content using the Tools list.
- Place fillable areas, type textual content and sign it.
- Add several signers by emails and set up the signing sequence.
- Indicate which individuals can get an executed doc.
- Use Advanced Options to reduce access to the document and set an expiry date.
- Press Save and Close when completed.
In addition, there are more advanced capabilities open for 910/2014 signature service. List users to your collaborative work enviroment, browse teams, and monitor teamwork. Numerous users all over the US and Europe concur that a solution that brings everything together in a single cohesive digital location, is what enterprises need to keep workflows functioning smoothly. The airSlate SignNow REST API allows you to embed eSignatures into your app, internet site, CRM or cloud. Try out airSlate SignNow and enjoy quicker, smoother and overall more productive eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results 910/2014 signature service made easy
Get legally-binding signatures now!
What active users are saying — 9102014 signature service
Related searches to 910/2014 signature service made easy
9102014 signature service
Hello dear students, welcome to lecture 13 of security of Information Systems. So today we're going to review and recap what we have seen so far. Actually this is the latest slide and the next week. I will be explaining you to injection hacking methods. We have seen them believe me, but we will see them in in details General Security concepts of a movement. Okay. Alright, so. understand information security properties services definition of information security ISO 27000. So let's remember is all tool 700. Okay. Iso/iec 27001 part of a growing family of iso/iec Information Security Management Systems isms standards the iso/iec 27001 series iso/iec 27001 International standard entitled Information Technology security techniques Information Security Management Systems overview and vocabulary. The standard was developed by subcommittee 27 SC 27 of the first joint technical committee JTC 1 of the International Organization for standardization and the international electrotechnical Commission. Iso/iec 27001 provides an overview of an introduction to the entire iso/iec 27001 family of Information Security Management Systems isms standards a glossary or vocabulary of fundamental terms and definitions used throughout the iso/iec 27001 family. Okay, so you have remember teeth definitions of CIA confidentiality integrity and availability services Privacy and gdpr so what was gdpr? It was a general data protection regulation by the European Union, okay. meaning of and difference between other security Concepts Authentication non-repudiation. So what was it? Let's remember it again. Non-repudiation is the assurance that someone cannot deny something typically non-repudiation refers to the ability to ensure that a party to a contract or a communication cannot deny the authenticity of their signature on a document or the sending of a message that they originated to repudiate means to deny for many years authorities have sought to make repudiation impossible in some situations. You might send registered mail, for example the recipient cannot deny that a letter was delivered similarly a legal document typically requires witnesses to signing so that the person who signs cannot deny having done so Okay, so you see we have digital sign it documents right now in Turkey. Maybe you heard of them. So this is about non-repudiation. On the internet a digital signature is used not only to ensure that a message or document has been electronically signed by the person that purported to sign the document but also since a digital signature can only be created by one person to ensure that a person cannot later deny that they furnish the signature. Okay. That's continued access control and authorization. Okay. perspectives on security controls three categories of security controls physical technical administrative preventive detective corrective security controls security controls during storage transmission processing. All right, so Security Management Security Management know what is 027 K series is about ISO 27000 ISO 27001 and ISO 27000, too title and purpose of each standard elements of isms cycle cryptography hash functions and symmetric ciphers status usage of sha-1 sha-2 and sha-3. Okay. Remember that when you are keeping user passwords in your database you need to hatch them and not only hatch them but you need to keep them as salted hash. Therefore they cannot be broken with rainbow tables if you remember so use at least salted sha-256, okay. Parameters block and key size OFA es value you woke with a let's open this. full dose description When you walk with Advanced encryption standard a SAS remember that block and key sizes are important to make it secure. mac message authentication code basic principle keyed hash function asymmetric ciphers understand usage of keys in encryption and digital signature digital signature understand practical usage combined with hash hybrid cryptosystems threat to classical crypto from Quantum Computing. What was it said from Quantum Computing value use of mica hashing algorithm. They can be easily broken with Quantum Computing to prevent it. We increase key sizes to Nest a reasonable reasonable size and even with Quantum Computing, which is not only theoretical it is not practical yet. Even Quantum Computing screen will not be able to beat them. Okay break them. Key Management key distribution problem understand requirements for key distributions within without pki a lot less pki if you remember public key infrastructure type of protection needed confidentiality or integrity certificates and pki ideas content issuing managing pki trust model revocation crl ocsp OCR okay, it was certificate revoke the invocation list. So let's remember it. In cryptography a certificate revocation list or crl is a list of digital certificates that have been revoked by the issuing certificate Authority see a before their scheduled expiration date and should no longer be trusted. Okay, so let us all see SP. The online certificate status protocol ocsp is an Internet Protocol used for obtaining the revocation status of an by Point 509 digital certificate one. It is described in RFC 6960 and is on the internet standards track. It was created as an alternative to certificate revocation lists crl specifically addressing certain problems associated with using crls in a public key infrastructure pki to Judges communicated via ocsp are encoded in ASN point one and are usually communicated over HTTP. The request response nature of these messages leads to ocsp servers being termed ocsp responders. Some web browsers use ocsp to validate https certificates, okay? City So CAA, not this one and let's go from here. science technology Okay, it's serious. A VHS against online civil aviation Authority probably off. Okay, and we may need to look for it. Okay, let's continue. Risk management understand the factors that contribute to risk. attacker threat agent vulnerability impact And how they are related understand diagram. risk management process ISO 27000 five threat scenario modeling attacker Centric architecture Centric and asset Centric models for risk level estimation qualitative quantitative risk treatment strategies reduce share retain accept avoid computer security protection rings in microprocessor architecture Mutual missions in mutual missions that are topics understand hypervisor VM guest OS host OS type 1 and type 2 virtualization architecture protection ring assignment 2 hypervisor host VM apps Etc. security advantages of running VMS boot security UEFI security functions supported by TPM remember TPM it was Trusted platform module, so let's redo to remember. Trusted platform module TPM also known as iso/iec 11801 nine is an international standard for a secure crypto processor a dedicated microcontroller designed to secure Hardware through integrated cryptographic keys. incident response and forensics elements if I our incident response policy types of ir teams permanent virtual hybrid phases of ir user Authentication types of authentication tokens clock based counter based challenge response password security hashing salting biometric systems criteria for biometric characteristics Iggy government user authentication Frameworks Assurance levels Ada's office Okay. Eight is electronic identification authentication and Trust Services is an EU regulation on electronic identification and Trust Services for electronic transactions in the European single Market. It was established in EU regulation 910 2014's of the 23rd of July 2014 on electronic identification and repeals directive 1999 93 EC from the 13th of December 1999 one to Into force on the 17th of September 2014 and applies from the first of July 2016 except for certain articles which are listed in its article 52 3 all organizations delivering public Digital Services in an EU member state must recognize electronic identification from all EU member states from September 29th, 2018. Assurance requirement classes authentication method strength credential management assurance registration assurance identity and access management meaning of entity identity identifier digital identity I am phases configuration and operation with steps identity management models. Silo model Federated model advantages and disadvantages of Silo and Federated models centralized distributed Federation models Facebook connect Federation scenario meaning and principle of Mac deck rbac and ABAC communication security TLS protocols Security Services key establishment RSA DH TLS stripping attack hsts ipsec modes tunnel transport key exchange tour perimeter security firewall types principles of different firewalls strengths and weaknesses location of entities DMZ or production Network TLS inspection in firewalls intrusion detection principles application security malware types What is owasp in the top 10 vulnerabilities list? No need to know all 10. So that's check them all out again. Remember? Okay, stop. Okay top 10 live in their publication security risks. Injection injection flaws such as SQL nosql OS and ldap injection occur when untrusted data is sent to an interpreter as part of a command or query the attackers hostile data can trick The Interpreter into executing unintended commands or accessing data without proper authorization. Okay. Broken authentication application functions related to authentication and session management are often implemented incorrectly allowing attackers to compromise passwords keys or session tokens or to exploit other implementation flaws to assume other users identities temporarily or permanently. sensitive data exposure many web applications and apis do not properly protect sensitive data such as Financial Health Care and P attackers May steal or modify such weekly protected data to conduct credit card fraud identity theft or other crimes sensitive data may be compromised without Extra Protection such as encryption at rest or in transit and requires special precautions when exchanged with the browser, XML external entities xxe many older or poorly configured XML processors evaluate external entity references within XML documents external entities can be used to disclose internal files using the file. Hurry Handler internal file shares internal Port scanning remote code execution and denial of service attacks broken Access Control restrictions. And what authenticated users are allowed to do are often. Properly enforced attackers can exploit these flaws to access unauthorized functionality and or data such as access other users accounts view sensitive files modify other users data change access rights Etc. Security Miss configuration security Miss configuration is the most commonly seen issue. This is commonly a result of insecure default configurations incomplete or ad hoc configurations open cloud storage. Figured HTTP headers and verbose error messages containing sensitive information. Not only Must ALL operating systems Frameworks libraries and applications be securely configured but they must be patched upgraded in a timely fashion. Okay. Cross-site scripting xss xss flaws occur, whenever an application includes untrusted data in a new web page without proper validation or escaping or updates an existing webpage with user-supplied data using a browser API that can create HTML or JavaScript xss allows attackers to execute scripts in the victims browser, which can hijack user sessions to face websites or redirect the user to malicious. It's insecure deserialization insecure deserialization often leads to remote code execution even if deserialization flaws do not result in remote code execution. They can be used to perform attacks including replay attacks injection attacks and privilege escalation attacks using components with known vulnerabilities components such as libraries Frameworks and other software modules run with the same privileges as the Ation, if a vulnerable component is exploited such an attack can facilitate serious data loss or server takeover applications and apis using components with known vulnerabilities May undermine application defenses and enable various attacks and impacts insufficient logging and monitoring insufficient logging and monitoring coupled with missing or ineffective integration with incident response allows attackers to further attack systems maintain persistence. Pivot two more systems and tamper extract or destroy data most breach studies show time to detect a breach is over 200 days typically detected by external parties rather than internal processes are monitoring. Okay, hopefully tomorrow we will see each one of these in I mean the next week, you'll see each one of these in details what you have remembered them. I am sure and I will take note of this. Okay. All right, because Pine and let's continue. explain main vulnerabilities SQL injection xss. Cross-site scripting broken authentication and session management these three are rulely and indeed lie the top three Majors vulnerabilities that you have to be careful in your professional life. The most common one is SQL injection. If you do not Senate eyes the input of the user or if you don't Hey kid necessary SQL execution protection such as parameterised queries you are in great danger hackers are using a fully autonomous both Veil covers to figure out find out SQL injection vulnerabilities in your web services or websites. Okay xs/s close sighs typical scripting is Another one and you have to be extremely careful again when you are taking user input you have to sanitize it or display it with sanitization and broken authentication and session management is also another one when you design a login and register system, you have to be extremely careful. Okay. So these are the three major main vulnerabilities Prime vulnerabilities that you may make, okay. This is true. secure software development security by Design secure agile software development alcohol clean exit you will see injection attacks in details top 10 universities. So this week I will also read again your semester project. Your semester project can be made only with single person. Okay, so you cannot make your semester project with someone else. Okay, so Read it line by line. semester project of CSE 413 security of Information Systems 2020 project description V to the 15th of December 2020 project delivery and of finals, please read this document at least two times. There will be a single project for this course the project will have a 100% grading score. You can send me your project file and asked me how it looks time to time. I will only evaluate the visual appearance and the structure of your article the content of the article will not be evaluated before the final project delivery. Okay. In this project you are supposed to prepare a detailed academic style article written about the below security related topics. Okay, you have to prepare it in all of the Beloved not one of them are not several of them all of them. Okay. So this was being asked to me therefore I will be updated project details. Let's open it and let's change the leaving but you're here. So I will update it once again. Okay. this project can only be made so okay you not group with your Rats, okay. So this is number one thing that I'm going to change and the second thing in this particular spot. Probably it has ridden about the bill of but all of them, not you all of them opportunities is really important. It has included all of them. Let's make this clear. So not you are going to pick one of them or pick several of them. You have to make your article covering all of them. OK all of them. This is important. So let's save this. I don't know why it has got some error, but it looks like Okay, save it, but let's continue. What is information security? What is data privacy? Find a real happen case example of data privacy breach what exactly what we mean by real example? ARS Technica is a very good website for finding such event finding needs about such events. For example, you see they have it such as data breaches and there are so many articles you can use them. Okay? what are the human factors in information security and what vulnerabilities it can lie do find a real happen case example of human factor vulnerability related hacking Okay. What is cryptography and subdivisions of cryptography? Oh find a real happened case example of cryptographic vulnerabilities related hacking so you can find Neves articles about all of these on I think arstechnica or you can look for other resources as well as technical is something that I read regularly. How does http work explain in details how to strengthen TSL security? Oh find a real happen case example of man-in-the-middle attack. What our data execution prevention address space layout randomization and CPU protection ring how platform virtualization Works in what are hypervisor levels? What our code injection cross-site scripting xss email header injection host header injection ldap injection OS command injection SQL injection sqli XPath injection attacks explain in details. Oh find a real happen case example for all attack types. What is Incident Management explain in details? What are digital forensics and digital evidence explain in details? Oh find a real happened case example where digital forensics played critical role? What is user authentication and explain different types of user authentication models? Oh find a real happen case example of user authentication vulnerability related hacking. What are password-based multi-factor certificate-based biometric and token-based authentication explain each one in details? Oh, give detailed example of token-based authentication. By the way, you can also deliver your project at the end of between Lemma exams. However, in that case you would get a theft in your final score and you will get your score in the between Emma exams, of course. What is tour the onion router and how does it work what our firewalls and how do they provide security? What is malware explain in details? Explain the followings in details? Backdoor trapdoor logic bomb Trojan Horse worm virus stealth virus polymorphic virus metamorphic virus exploit. Okay, when I say explain I am expecting from you a betters article than what we are showing in our Lecture slides. Okay. Do not just copy and paste lecture slides. That is not what I want. I want you to do research find proper sources. Also, whenever you use an image a video or whatever give them references. So right in your under your picture for example the source of the image. Okay. This is important in academic writing. What is ransomware how it works and how to prevent it? Find a real happen case where ransomware costed millions of dollars of loss. In addition to the article you are going to prepare you are supposed to record a very high-quality video use OBS studio and record quality to indistinguishable quality audio 48k and explain every page of your report. This video is supposed to be at least one hour long. You have to have a proper microphone set up. The video will be uploaded to YouTube with full quality and the link will be shared in the article. You have written Youtube upload has to be public or unlisted. The article has to be written with fluent and grammar correct English as well as it has to be properly structured. Also, it can be rich in images every resources. You use must have a reference to the source. Okay in your explanation video, you can explain it. In Turkish. Okay, let me at that. semester project file Okay. The aim of this project is teaching you every kind of information security related topics. It is not just preparing a document by copy paste from the internet therefore not only your article quality. But also how well you explain them in the video is important. Try to cover as many as topics. You can remember you have to explain every topic you have written in the video only the topics you covered in the video of your article will be counted for scoring. Okay, so let's fix this sentence. Remember you have to explain every topic. Okay, that is in the video. You have sex whenever talking in the video that you have Niger in your article on the same project. This project article, you know, it sounds feathers. The structure and visual appearance of your article will also get you higher score. Also how well it is written and how good in grammar is also important. So try to do your best Turkish students can record the video in Turkish. The article has to be in English if you are a foreign student, but can speak Turkish better than English. You can also record the video in Turkish. Everyone will be sending a word or PDF document along with their final project files. This document will contain screenshots of your all comments to the lecture videos. All of the 14 lecture videos take screenshots with high resolution. Your comment has to be clearly readable those who fails to send this document will be counted as not attended to the lectures. Therefore they will get FF. Also another think is thought Keep me that they are not able to find their command. If you can't find your comment in our videos then open it in private window and open our YouTube page. Okay, it looks like we have two thousand on Google doesn't list our page. So let's open from here. Okay, for example, I will show you what I mean. So you have open it the media then in the comment section sort them by name is first. Okay, when you do this, you see the your comment is appearing here if it still doesn't appear here you can recommend so what you're going to do is for example, you would take screenshots with print screen. Okay, and use any screenshot software or you can also alternatively use. Signature shot future of NASA a PowerPoint or yeah, PowerPoint is also fine. For example, let's open a PowerPoint and here there is a screenshot and let's see if it does support Chrome. Yeah, looks like it doesn't support Chrome to take screenshot. So you need to use image software. For example, you can use paint as well which exist on every window of computers here paste it here copy from that 80 hours. For example, PowerPoint or open a virtual human hand. Actor, however, when you before adding death that crop is like this OK you see I am selecting the corps command copying it and pasting only that command Okay, so and in front of your comment, you have to write it like this lecture one then go to the lecture to and take your comment and like right lecture to and pasted below with your comment. Okay, so you will also send Change me this file along with your project documents. Okay, I think it is enough for this week. Let me update the project file as well as a master project file and slides. Okay, let's update project file. If you have any questions, you can ask me from my email or from our discourse Channel. Okay, let's update it here as well. Okay. Okay. Okay, this week is being kind of short the next week will be much longer. And so think this as a time to prepare and work on your project and hopefully see you next week and of lectures.
Show moreFrequently asked questions
How do I eSign a document before sending it?
How do I sign a PDF electronically?
How can I type my name in the sign field in a PDF?
Get more for 910/2014 signature service made easy
- Print electronically sign Release of Liability Form (Waiver of Liability)
- Prove electronically signed VAT Invoice Template
- Endorse digisign Assurance Agreement
- Authorize signature service Lean Business Model Canvas
- Anneal mark Interior Design Contract Template
- Justify esign Architectural Proposal Template
- Try countersign Service Quote Template
- Add Participation Agreement digi-sign
- Send Construction Quote Template esign
- Fax Restaurant Reservation signature block
- Seal Doctor's Note signature
- Password Service Quote Template email signature
- Pass Affiliate Agreement signatory
- Renew Professional Physical Therapy electronically signed
- Test Professional Medical History byline
- Require Distributor Agreement Template esigning
- Comment deponent digital signature
- Boost viewer countersignature
- Call for beneficiary electronically sign
- Void Painting Contract Template template digital sign
- Adopt Timeshare Agreement template initial
- Vouch Screen Printing Quote template signature
- Establish Pet Adoption Application template countersignature
- Clear Executive Summary Template template digital signature
- Complete Travel Planning Registration template electronically signed
- Force Service Proposal Template template signed
- Permit Landlord Rent Receipt template digi-sign
- Customize End User License Agreement template esign