Byline Certificate Made Easy
Get the powerful eSignature capabilities you need from the company you trust
Select the pro service made for pros
Set up eSignature API with ease
Collaborate better together
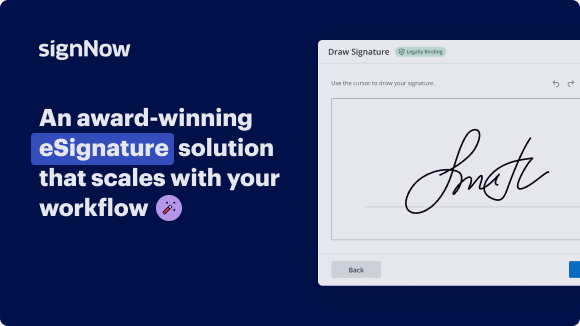
Byline certificate, in minutes
Decrease the closing time
Keep sensitive information safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — byline certificate
Employing airSlate SignNow’s electronic signature any organization can increase signature workflows and eSign in real-time, supplying a greater experience to clients and employees. Use byline certificate in a few simple actions. Our mobile-first apps make operating on the move achievable, even while off the internet! Sign contracts from any place in the world and complete deals in less time.
Take a walk-through guideline for using byline certificate:
- Sign in to your airSlate SignNow account.
- Locate your record within your folders or import a new one.
- Open up the record adjust using the Tools list.
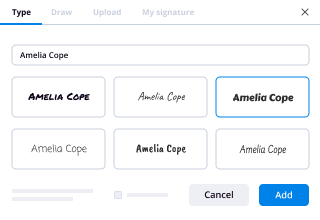
- Place fillable fields, type textual content and sign it.
- List numerous signees by emails and set the signing sequence.
- Indicate which recipients will get an signed version.
- Use Advanced Options to reduce access to the document and set an expiry date.
- Click Save and Close when done.
Moreover, there are more innovative functions accessible for byline certificate. List users to your shared workspace, view teams, and monitor teamwork. Numerous consumers across the US and Europe agree that a solution that brings everything together in one unified digital location, is what enterprises need to keep workflows functioning easily. The airSlate SignNow REST API allows you to integrate eSignatures into your application, website, CRM or cloud. Try out airSlate SignNow and enjoy quicker, smoother and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results byline certificate made easy
Get legally-binding signatures now!
What active users are saying — byline certificate
Related searches to byline certificate made easy
Byline certificate
good afternoon everybody so yeah my session today I'm going to talk about mage cart maggot cart maiik are lots of people say different things there's no official way to say it so just stick with what you're comfortable with and just really sort of look into what they're doing how they're doing it and the different groups that are out there and how they're developing over time in terms of the activity that they're doing so I'll start by looking at two of the most high-profile breaches Ticketmaster and British Airways they're good examples because they're both different mechanisms for how they delivered the skimmers onto the different sites so quickly broad cover those then I'll take a look at the different groups how they're evolving and what they're doing and a brief update on some of the more recent activity that we've seen sort of deviate out into browser-based injections sort of topic on its own I think major cart and card skimming is is in many ways just sort of the tip of the iceberg it's perhaps the easy to monetize activity but there's lots of stuff that you can do with browser injection so I'll take a quick look at that then talk about the different ways to detect or prevent it and if we have time I'll be honest I don't think I will have time with all the other stuff I'm trying to cover live we have time I'll try and run through a risk like you total solution to show how we do some of the investigations that lead us to finding the infrastructure that sits behind the different groups that are carrying out these attacks so in June of last year Ticketmaster hit the headlines they'd lost carelessness suppose 40,000 customers credit card details and this caught the eye of the security research team at risk IQ because it was the language that they used they talked about not a breach of their systems not about you know databases and passwords being salted and hashed and so on but you know specifically they talked about malicious code embedded in a third party technology on their website that led to this breach it was on the website for what four months in international customers and I haven't seen any real discussion about the overall impact to their international customers but they talked about being on both sites for nine months so now these these injections are out there they sit on websites nobody notices they're just quietly skinned credit card information as they go oh take a source side step here to talk about how risk IQ operates because I think it will help as I go into the analysis to understand a little bit of what we do this is a very busy slide I apologize for that I'm only going to talk about the first half of it but risk IQ spends its days crawling the internet we've got hundreds of different proxy points around the world that our crawlers exit from to visit the sites on the Internet our goal is to crawl the whole of the Internet I have to be honest and say that's quite a heady goal and one that we haven't really reached yet but by feeding information into the system that's domain registrations passive DNS records blacklist feeds and a whole bunch of other things now crawlers set off at the beginning of every day to go out and visit the web and they as they go they collect every bit and byte that they encounter so the full document object model of every site certificates cookies trackers all of the JavaScript that's important for what we're going to talk about here today they that information and they follow links there we refer to them as virtual users its headless browsing so we do present ourselves as a sort of a human user if you will we don't do a double you get on the site and then leave will visit it many times over the course of a day clicking on different links so that our behavior does not stand out as automated and we do that because the stuff we're really looking for the malicious stuff sometimes has rules in it to detect automated analysis so by by behaving as human users we're able to collect more information and otherwise possible we do about 2 billion page requests today to give you an idea of the scale of what we're doing and then that information comes into those for the the technical among you you'll notice that the arrows on the cogs mean that the cogs don't actually turn my apologies for that someone pointed it out to me in a presentation a couple weeks ago but three functions that we do as the data comes in from that crawling Network first thing is we carry out the data science piece and by that I mean we look at the connectedness of all of the data that we collect if we find a website what other websites does it connect to you know what refers to it and where does it refer to if there's a certificate on that site where else are we seeing that certificate it's same with cookies same with trackers and we build out this sort of view of the web in terms of the connectedness of everything you see if any of you have used passive total that's how we are delivering that data within passive total so that you can carry out those investigations around infrastructure the second part is that machine learning piece so we will look at as we find things and see different mission malicious behaviors then we can start to alert that so that we can tell our customers we found something that's relevant to them then the final cog is the security research piece and that's the team that did the research for the major cut piece today and they are constantly looking for new threats new problems so that they can not only build them into our platform but also so that we can talk about them at events like this so coming back to Ticketmaster so I said we're doing over 2 billion page requests a day the breach was there for about 90 days so we had somewhere in the region of 200 billion crawls of data to go through I should say Ticketmaster not a customer of risk IQ so it's not like we were actively monitoring their code so it's a bit of a challenge knowing where to start but the good news was Ticketmaster had given us enough information within their press release first of all the Ticketmaster UK was compromised so we could focus on their UK assets they talked about inventor the fact that the script was actually hosted on embeds the hardware and then the task was really to go through looking at all of the scripts that we found that were Ticketmaster UK hosted on in benta let's see what we can find and we use passive total you can see just a quick snip there showing the subdomain of Ticketmaster on the inventor site we went and had a look at the cruel data for Ticketmaster UK dot inventor and this script here or there's this box I've called out in bento Jas Ticketmaster UK inventor calm that's the one that caught our eye that was the one that seemed to be most interesting this is what the script looks like or at least on top of it I've put the major car code in the red box but I think it's also interesting to see the code that's underneath it because that's not obfuscated and that's always sort of a sort of a red flag to us at least when we see a mix of obfuscated and unobligated code in one place if we are not for scope that code then what we found was 67 lines it is a simple major card skimmer to be fair nothing particularly outstanding about it from our perspective I haven't put all sixty lines there because the the text would have got so small even I wouldn't be able to read it standing here but the box of outlines the web f OTC e that's the exfil site so you go onto Ticketmaster you enter all of your credit card details there's a box somewhere on there probably saying if you have any problems click here that's the inventor code they were it was a help function within the site you don't have to use the help function to activate it's just a simple fact that it was on the payment page means that that script was was loaded but as you enter all of your details and when you hit order checkout or one step' this wasn't a custom script for Ticketmaster this was just designed to catch as much credit card information as possible so there are keywords that they're looking for in the script as soon as that word is executed the the button is clicked then the code is sent to web fo TCE so that the information then be utilized by the group that was doing this this was a major use the news story Ticketmaster a well-known brand not just in the UK but around the world at the potential for 10 million customers that's the traffic that goes through the Ticketmaster site but I guess not everybody that goes to the site actually purchase purchasers a ticket at the end of the of the visit they got credit card number user name expiry date and most importantly for me the CVV number that's to me what gives a credit card it's real value if you're going to try and sell it on in one of those dark web forms the previous speaker was talking about I think what is most interesting for me is the fact that this all happens in the users browser none of this was happening in the Ticketmaster environment you know they to a degree they have no visibility of this whatsoever your web application file was not going to pick this up your file your a/v it's all happening on the clients browser how do you detect that activity and then this may be a conversation for another event arguably Ticketmaster were not breached it was a third party that script had nothing to do with Ticketmaster other than the fact that they were using it now the debate goes they should have done a better order on their third parties of course but technically their security was sound it was a third party that got caught out switching to be a so a couple months later we're in September now another news article on the BBC again this time 380,000 credit card details are stolen in a much shorter time frame and it's three weeks in this case and again it caught the eye of our research team because they didn't talk about database breaches and now they'd been sort of hacked it was a compromise on their website so again and I should say again be aid we're not a customer risk IQ so it's not like we were looking to monitor their systems this is just through our our crawling data let's have a look see if we coul PA and and we'll see what we find and we found this script moderniser 2.6 dot 2 min je s the top snip shows how that file looked before the the breach date that was announced and it pretty static script actually it hasn't changed since 18th of December 2012 and then surprise surprise an hour before the date that ba announced that the hack had ended we've got a new script being uploaded to the be a site we saw that we'll take a look at that we've delegated this one and beautified it a little bit more than the last one 22 lines of code that was all it took to steal those 300,000 credit card details it's it's quite nice it's much tidier than the the Ticketmaster one they even wrote it so this is specific to tube a this isn't her this isn't a a generic script that's why I wanted to talk about the two examples but they actually wrote this for both web browsers and mobile devices the the be a mobile app shares a lot of its infrastructure with the with the website so they've put in an additional four touch component to the to the script so that they can make sure they get some many credit cards as possible not just those on the web we've seen versions of this that are 15 lines of code this was slightly more complicated because ba actually keep the the details of the individual paying in a slightly different place on the website to the terms of the rest of the credit card data but still quite nice the way they've done it and they exfil to be a ways calm and this is just sort of worth its own mention this is nothing to do with British Airways but it's a great copycat domain if you're looking at this code either within the you know the be a organization sort of scanning it looking for any anomalies maybe if you are doing some sort of monitoring on your browser to you know prevent something like this catching you I'm just not sure that you would pick out the be a ways it's just a really nice infringing domain registered a week before or the cert well sorry this snip this snip is from the week a week previous so they obviously had this access for you know this wasn't a smash-and-grab this is a nicely planned operation interesting that they registered a legitimate certificate as well why not use let's encrypt or a free certificate you know these guys were really paying attention to what they were doing yeah it's just I like it and that's mage card that's what they do find a way onto a server I can't tell you how inventive were hacked I can't tell you what happened with BA all we can do is say look scripts were inserted into their infrastructure and people just unwittingly losing their credit card data what we do know about mage cart they've been around since about 2014 we've been tracking them actively since about 2015 they started by playing on the server side with the Magento payment system that's where mage cart comes from you'll see the sniff at the bottom says mage Jes the mage and then tie that in with cart because it's a shopping cart and that's where you've got the name from it it's more as we've seen more groups joining the operation into more of an umbrella term for this type of activity for people doing credit card skimming on the web and we have seen different activity we've seen these sort of cards appearing on on dark web forums in dump sites we've also been able to track some reshipping fraud behavior as well but we haven't done a huge amount of attribution on the actual individuals themselves with left-outs of the people who are expert so that our job is to try and collect this data rather than to analyze who's actually doing it but drilling into the groups so as I say Group one started by targeting actually they started targeting vulnerable Magento servers so they were looking for just simple weaknesses in the system and then starting to target them we initially logged it as a keylogger they were just tracking when numbers were being entered into the forms on a website at the point where you've finished entering the the expiry date of your car that's typically the last field on the credit card what you fill in then the data would be X filled out to another location in this case jjs save got linked they didn't have as much success on the server side pretty difficult to break server-side components and that's why we saw them moved to the de client side it was much more robust in terms of the the insertion of the code and without causing any additional problems you'll be sharp ones among you will notice that I've jumped from group 1 to group 3 grouped who we initially categorize the the monetization activity of Group one as a second group and then we brought them together when we realized it was actually the same operators doing the same work so moving on to group three these guys it sort of industrialized the process they built out forms for a large number of the of the different payment processing systems that are available if you look at this code you'll see it's got a way add yen rad web these are all very common processing systems and just to make it easier you know the keylogger meant you'd have to do some parsing on the data to find the the credit card information within the data that you've just pilfered by creating those forms they just make it much easier to bring the data route group for entered the market this is probably late 2017 we saw these guys maybe early 2018 they came from the banking Trojan environment so you know these guys have been doing this for a long time they obviously realized that there was low-hanging fruit here and built out their capabilities the snip of code there shows that them doing counter analysis activity in their JavaScript their original JavaScript about fifteen hundred lines of code so you know well I want to talk about Ticketmaster that was 67 lines of code this is much beefier not nearly as efficient but interesting in how they were doing timing analysis to see if it was a machine looking at their code rather than just a human victim if they did detect machine analysis then they they provide benign JavaScript rather than the the the nasty stuff group five these are the guys that caught Ticketmaster out as I say they went for a third party and the results were exceptional if you tally up the number of sites that we found which have been compromised by group five there's over 20,000 it's there you know some of them will be low volume some of them at high volume but yeah they've just found a simple script that they can insert into any presumably vulnerable JavaScript it's out there it's in plugins so they've only had to compromise where there really is 10/10 systems and they've had fantastic results from it 20,000 other sites now running major car systems the skimmer itself is nothing unusual it's just the the attack vector went to mass scale rather than rather than so it's focused attacks group six is very focused attacks we haven't seen a huge number of sites compromised by these guys but when they do it's usually big I would have talked about this I don't want to go into too much detail but just to come back to that that'd be a ways calm I love the way that their URL also follows the the syntax coming from the the legitimate be a site similar with new egg new egg is a u.s. online shopping site new x.com if they followed the capitalization from the legitimate site it's just such a you know great attention to detail I can't help but admire it group seven these guys caught our attention simply because they're not doing the standard exfil they're using compromised domains legitimate domains find that find a subdomain that they can actually all the data to and then transfer the data from there makes it much harder for takedown to take place we've been working with abuse CH and shadow server on a very regular basis as we as we identify a new infrastructure being stirred up around any of the major contactors we're working with them to carry out takedowns these guys are much harder to do because the domain is legitimate then you have to kind of follow a you know contact an organisation is this your domain who ministers it did you know you're being used as a mule blah blah blah it takes a lot longer it's much harder to do that up to group seven took us up to roundabout the end of last year since then we've seen another six or seven groups popping up and we're now starting to get a little bit sort of more detailed in terms of when we attribute them it's just becoming too much work um and following the attribution you know eight and ten in this group essentially you know there is nothing new in what they're doing other than the fact it's new infrastructure so again we will work to take down their infrastructure but we're not particularly tracking the people who are just doing copycat of everything else group 9 is is possibly one of my favorites credit servility group who actually posted about this for this one so group three were compromised a site they were happily skimming the data was good this this is nice and then group nine compromised debt and you know you'd think that they might coexist peacefully but they didn't group nine changed their code so that whenever they detected that the mage three activity that's part of the group three activity they generate a random number replace one of the numbers in the credit card with that random number and then send that to group three there is no honor among thieves the last speaker was saying you know reputation is everything on the dark web and if you can trash the data that they're trying to sell you're really working to take out your opposition is just you know a love lovely example that was found their group eleven this was vision direct vision direct when they announced that they'd been compromised said it was only the UK and one or two other sites we saw it on a significantly more infrastructure I think all of those listed there one of eighteen is it we're all compromised at the same time they introduced more keywords I talked about one stuck checkout and I come over the other while buying out or something these guys added admin account login and password and this has been something that's been in the back of my mind ever since we started talking about these injections is you know credit cards are just a tip of the iceberg aren't they what else could you collect any any site that collects information and runs JavaScript I suppose is is a is a target and these guys have just broadened that reach so to say yeah we can collect anything we don't know what we'll get who knows but a lot of the injections that we're seeing you know we believe at least they're automated and they're just pray and pray their code into whatever JavaScript they can why not why not see if you strike lucky with with some of the account login information you never know what might come back so I thought that was an interesting development and I wonder if we will see anybody else sort of going further with that group twelve these guys are interesting I mean they're using script tags which we haven't seen in many of the other groups it's much more plug-and-play they compromised ad the line AB company and that got them again just great coverage you can cover a huge amount of ground if you're if people are actively putting your compromised code onto on too many sites so nice coverage that they achieved there and they broadened out into French in German now to date we've been seeing mainly English some some Latin American Spanish but these guys broadened it to French and German as well so again we're seeing nice seeing a little bit more internationalization in terms of the the targets that we're seeing why why shouldn't the French and the Germans get skimmed as well oh and that's just breaking out the script tag so Group four I talked about these were the guys that came from the banking the Trojan environment have completely rewritten their code it's now 150 lines previously it was more of a fishing overlay now they're they're doing you know what we considered to be more sort of mainline skimming they've really started to change their behavior they're now only putting five domains per IP they're going to more hosting providers than we've seen previously we think that's a direct result of the takedowns that we're doing the good news is that we're not using you're only using the infrastructure piece in the last the last step of the puzzle just to broaden out what they're doing the initial detection has nothing to do with the infrastructure so they can keep on running and hiding and shuffling but it fortunately manages to get detected anyway I was quite impressed that they started to include encryption in their new piece of code as well at least they're mindful of PCI DSS regulations so that that's good and this one this one's kind of hot hot off the press we saw a sudden dramatic spike in injections that we were detecting about two weeks ago I've put tens of thousands and then possibly hundreds of thousands at this point in the investigation I couldn't tell if it was just the researcher getting excited or if it was genuine genuinely hundreds of thousands of site that were being impacted and we couldn't work out where the spike was coming from the guys were sort of starving so sort of pull the threads and seed so you see what the common factor was and it seemed that the JavaScript that was compromised in all of these different cases was being hosted on s3 buckets not just sorry I don't mean one JavaScript with all of the different Java scripts that were being used with being hosted on different s3 buckets and so they started looking a bit further and then they kind of realized these s3 buckets are all world writable is that impossible I couldn't believe that I was watching pull your presentation earlier and I was waiting for you to bring up a slide that showed don't let your buckets be world writable and I try to find a screenshot that showed where they would you know somehow default to be world writable people are hosting JavaScript that other people are using in s3 buckets which are completely editable you download it insert your skimmer upload it back up and hey happy days right we're gonna go public with this not not with the names of the people infected but just to say that for God's sake don't put world writable files on the internet unless you really really really mean to two of the victims we've identified a prepaid credit card providers yeah this is it's great stuff right other updates just sort of things that we've found you know I try to keep a list of the things that are going on group seven these guys came from from the malware environment and they initially they started just doing this but they had a little look at doing malware drops so again another another to a possible bacteria when you when you're when you're when you finally got a compromised site what else can you do other than just skim skim credit cards we haven't really seen that evolve into anything other than their tests we just saw changes in their code it showed what they were experimenting with maybe they're now doing their experiments offline we're not sure we saw text support scammers trying to join in that was based off the infrastructure we saw the same infrastructure that's being used for tech support scams being used for skimming they weren't successful I guess that's why the tech support scammers are not tech support is you've got to know what you're doing in order to do this there's about 20 off the shelf skimmers now if you look in some of the difference or a dark web forums different prices different availability different support available and we're seeing obviously the last couple weeks aside because it's been dramatically different but about 40 to 50 major car compromises a day I I think that's the absolutely tip of the iceberg we are not targeting our crawlers on payment pages we are not out there looking for mage guys it's just we keep finding it and it's our estimate that if we were to target the crawlers to look for it specifically go for every payment page you can we reckon this would be up to the 500 mm mark we're just finding enough to keep us busy we don't need any more but it's just interesting to see that so vulnerabilities is the main one I think in terms of how they're getting insert and the automated scripts that we're seeing you know just either old or vulnerable codes being used to carry out these injects injections third-party scripts just broadens the reach that you get as you as you compromise different scripts and then we are seeing focus compromises also BPA will you know certainly a targeted very very specific and targeted compromise different levels of sophistication as I've said and then different exfil processes although to be fair we only releasing one group using the proxy proxy process to deliver the deliver the code so broadening out as I said at the beginning I think card skimming is there's only really one application of Java based injection there are all sorts of other things you can do form form jacking you know just just gathering the data it's similar to card skimming but also cryptocurrency miners we're not seeing a huge amount of Bitcoin mining at the moment nine months ago we were seeing a lot more I don't think that's because it's not difficult I don't think it's because people don't want you know can't do it I think it's just the Bitcoin prices crashed nurse just easier to monetize through other means at the moment and give Bitcoin goes back in price then we will probably see more Bitcoin miners being inserted into different sites water-holding the snip on the right is an example of a water-holding attack this is an RFC edge case if you browsers don't worry so much about images as they do about executable files if you can insert a file an image file into a webpage then it passes some of the inspections in this case that snip was on a Ukrainian IT website and if you went to it maybe a Ukrainian IT administrator was having a tea break it's going to catch up on the news you're in the middle of reading a very interesting article on whatever it is and then SMB window pops up saying one of your connections has timed out you just want to quickly add your admin username and password and get back to your cup of tea and your news article and of course this is just fishing you know about information so just a good example of a water holing attack and then just finger printers we see a lot of people just simply collecting information for whatever means they may be using that data for whether it's traffic weary directors driving traffic to different places you know it's hard to work out I do see this as the new front line I think lots of people have invested huge time and resources in securing their data in their data centers and for good reason you know that that's probably the best place to start but it means that criminal groups are now looking at other ways to steal information and I think this is a great place to do it I was talking to a friend the other day who was saying their mortgage application [Music] this year was completely online two years ago I got a piece of paper that I had to sign and send back but you know all of that data is going through client browsers which are not policed and monitored in the same way as all of those traditional systems that you would find in major organizations so this data is out there and it's available to be to be taken I'm running out of time so I need to speed up a little bit don't know how I'm doing five minutes thank you so we were just looking at different injection types the script tag that I showed you from major cart group 12 it's just nice and easy it's plug and play makes it much easier to automate the process of adding script tags the supply chain so the ticket master breach inventor that was just nicely done the third parties aren't necessarily a security organization that you're targeting so it's just a nice way of breaking in putting those scripts at the top or the bottom it's easier to detect but it's also least likely to break anything I've seen a few examples in the last month of scripts that have been injected and broke the broke the script that they were trying to inject in so it can go wrong if you try to get too too cute we do see them trying to put the injection into the executable scope rather than you know making a mistake and only runs on certain occasions and bento would be a good example of that that was customer help tool and if there haven't been any executable scope they'd only be able to collect the credit card details when someone was asking for help and they probably get all of their conversation as well as the credit card data function inlining is just quite a nice way of doing it it's quite quite tidy just suddenly add a new function to an existing one and again much harder to spot than the RFC educators the example I gave you at the beginning the watering hole attack I'm super envious other people that can read those RFC reports in detail understand them and then find the vulnerabilities within them but those people do exist and my respect to them even if they're doing doing it for all the wrong reasons in terms of how can you protect yourself you know I think I think I work for risk IQ we talk about managing your external attack surface and that for me is the way to go here you need to understand what assets you've got I would now whether you could say you know how many websites your organization actually has very much doubt that any of you could give me an accurate number and I think that's just as again the tip of the iceberg how many of you know what JavaScript you're hosting on your site how much of that javascript is hosted locally how much of it is by third parties how much of it is on world writable s3 buckets so you need to understand your external attack surface you need to manage that you need to bring it under control make sure everything is patched and not leave things out there which shouldn't be out there talking about JavaScript specifically iframes sandboxing a lot of people criticize BA not for not having iframes in operation on on the payment page I've seen a lot to talk about content security policy sub resource integrity checking all super good things they will definitely make it a lot harder to do this I also think that's much easier said than done the you know the complexity of a lot of web infrastructure now doesn't mean you can just flick this stuff on and go yeah we're done it we're much secure there are projects behind us and significant you know forklift changes that need to be made to make these work I also worry that for some of some of the breaches that we've seen where the the code has been highly customized whether some of these these mechanisms can be bypassed as well we saw one group arguing with a web administrator in a document object model the it was infected the administrator removed it the the major card group said we put it back stop it the next time they said you're very naughty admins next time you do this we will delete your site if you have that much access access to it to a system then these policies are probably not going to protect you and that brings me to my last point which is continuous auditing again you know ba was three months Ticketmaster was three months in the UK nine months in total we're seeing more or of these I think last week Leicester City Football Club got popped anybody by a Leicester City football shirt in in May if you did check your credit card Forbes got popped the week before then you know we're seeing this all over the place in these breeches are all there for weeks if not months you need to be monitoring for this on a regular basis my shameless plug at the end use risk IQ that's what we do we're really good at it so please do I'll be around for the rest of the day please come and talk to me if you want to know more about the presentation or obviously how risk IQ can help and my final piece on your bags is a big risk IQ logo under that as a promo code for passive total if you would like to do some of the investigations you can put in some of the domains that I've shared in presentation today you can do some of your own investigations with that promo code and give you extra searches on passive total thank you very much for your time today I don't know whether I've got time for any questions there are any questions I'm happy to try and take them sorry I didn't warn you earlier did I to action with the microphones any questions was what you saying we do these to use elizy is that simply checking the JavaScript has changed and learning when that happens so for our customers we crawl that that their their sites on at least a daily basis looking for changes that take place within that environment now we can say if the JavaScript has changed we'll tell you about it one of the challenges we've found is the JavaScript changes a lot and therefore you could you you run the risk of getting a lot of noise so what we've what we've developed is is specific detection looking at malicious activity and we will alert you when we see malicious activity so you'll get an audit report telling you what's changed on that maybe a daily or a weekly basis depending on your appetite and then when we see something like I've been talking about today occurring so you can take more immediate action if you comment about the link between the VA breach and the inventor stuff because the better stuff includes loads of creative cedras doesn't it I'm sorry could you comment on the link between the be a breach and the Benza scripts because the adventure scripts include the agency G's in the list of affected parts or is that news you mean the be a reusing inventor on their website so I do know that there were I think I think when we looked at it over 30 different scripts running on the be a payment pages when we analyzed it I haven't looked at it in light of inventor and whether they were potentially compromised two ways be interesting to go back and take a look see if I can spot that they were completely separate breaches if that was the case then that that's a fascinating byline to the story inventor you know came out in June and announced this ba was after that we the attribution that we've given us is two very very different groups major cart groups six are highly focused on you know specific compromise they're not going for that broad brush approach but no I haven't seen that inventor was specifically on the VA website I haven't thought to correlate that back but I'll go back and take a look it would be an interesting thing to look for thank you right oh one more question go on if I've got time we're done okay I'll catch you later thank you very much everybody you [Applause]
Show moreFrequently asked questions
How can I scan my signature and use it to sign documents on my computer?
How do I eSign scanned documents?
How can I sign a PDF file and send it back?
Get more for byline certificate made easy
- Health Insurance Portability and Accountability Act initial
- Prove electronically signing Product Order
- Endorse digi-sign HIPAA Business Associate Agreement
- Authorize signature service Research Proposal Template
- Anneal signatory Pet Boarding Confirmation Letter
- Justify eSignature Holiday Party Invitation
- Try initial Colorado Rental Agreement
- Add Support Agreement signature block
- Send Event Catering Proposal Template signature service
- Fax Silent Auction Gift Certificate countersign
- Seal Product Survey signatory
- Password Certificate of Incorporation initials
- Pass Demolition Contract Template eSign
- Renew Photography Services Contract esigning
- Test Dog Shot Record digisign
- Require Forbearance Agreement Template electronic signature
- Comment cashier mark
- Boost adult electronically signing
- Compel underwriter digital signature
- Void Cease and Desist Letter Template template signature
- Adopt Interest Transfer Agreement template email signature
- Vouch Lawn Care Invoice template signatory
- Establish Attendance Certificate template electronically signed
- Clear Membership Agreement Template template byline
- Complete Basic Scholarship Application template esigning
- Force Recruitment Proposal Template template esign
- Permit Church Event Promotion Request template signature block
- Customize Performance Contract Template template signature service