CAIQ Byline Made Easy
Do more on the web with a globally-trusted eSignature platform
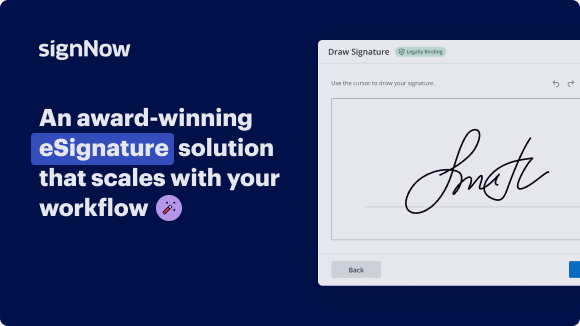
Outstanding signing experience
Robust reports and analytics
Mobile eSigning in person and remotely
Industry regulations and conformity
Caiq byline, faster than ever
Helpful eSignature extensions
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — caiq byline
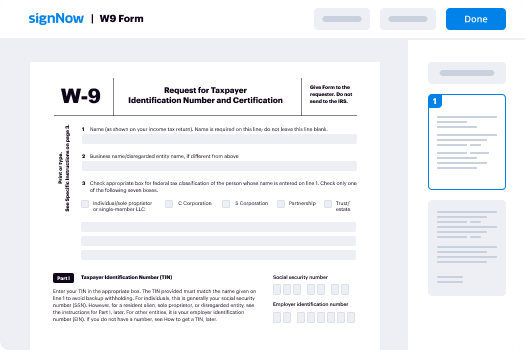
Adopting airSlate SignNow’s eSignature any organization can enhance signature workflows and sign online in real-time, supplying an improved experience to customers and workers. Use CAIQ byline in a couple of simple actions. Our mobile-first apps make working on the go achievable, even while off the internet! Sign documents from any place in the world and close up deals quicker.
Keep to the stepwise guide for using CAIQ byline:
- Log in to your airSlate SignNow profile.
- Find your document in your folders or import a new one.
- Access the record and make edits using the Tools menu.
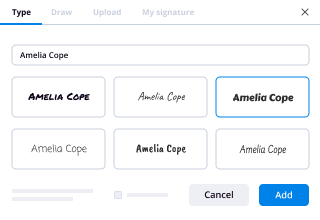
- Drag & drop fillable fields, type text and eSign it.
- Include multiple signees by emails and set the signing order.
- Specify which individuals will get an completed version.
- Use Advanced Options to limit access to the document and set an expiration date.
- Tap Save and Close when finished.
In addition, there are more innovative features open for CAIQ byline. List users to your shared workspace, browse teams, and monitor teamwork. Millions of people across the US and Europe agree that a system that brings people together in a single unified work area, is the thing that companies need to keep workflows working easily. The airSlate SignNow REST API enables you to integrate eSignatures into your app, internet site, CRM or cloud storage. Try out airSlate SignNow and get quicker, easier and overall more efficient eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results CAIQ byline made easy
Get legally-binding signatures now!
FAQs
-
What is CAIQ?
The Consensus Assessments Initiative Questionnaire (CAIQ) is a survey provided by the Cloud Security Alliance (CSA) for cloud consumers and auditors to assess the security capabilities of a cloud service provider. -
How do you assess cloud security?
Identify what type of cloud-based services you want. ... Identify who your data controller is. ... Decide what level of information assurance your data requires. ... Check where your data is being stored. -
How do you evaluate a cloud service provider?
Security. You want to understand precisely what your security goals are, the security measures offered by each provider, and the mechanisms they use to protect your applications and data. ... Compliance. ... Architecture. ... Manageability. ... Service Levels. ... Support. ... Costs. -
What is Ccsk certification?
The CCSK is a web-based examination of an individual's competency in key cloud security issues. Launched in 2010, the CCSK is a widely recognized standard of expertise and is the industry's primary benchmark for measuring cloud security skillsets. -
Is Ccsk a good certification?
As a beginner in cloud security, it is good to validate your skills with Certificate of Cloud Security Knowledge (CCSK). If you are the one who has gained some considerable experience in cloud security, then you can go with Certified Cloud Security Professional (CCSP). -
How hard is Ccsk?
Many consider CCSK to be a fairly hard exam, even if it is open book. This is mainly because of the mix of topics, and because it does not test much factual knowledge. Instead it tests for conceptual understanding of the CCSK material. -
What is the cloud security framework?
A cloud security framework provides a list of key functions necessary to manage cybersecurity-related risks in a cloud-based environment. This includes referencing security standards and guidelines put in place to list specific requirements when identifying and responding to network threats. -
What are cloud security controls?
Cloud computing security or, more simply, cloud security refers to a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing. -
How secure is IBM cloud?
Market-leading data protection across the platform. IBM has a long-standing history as a leading security provider. Today, IBM Cloud\u2122 builds on that tradition as the most open and secure public cloud for business. Leverage market-leading data protection capabilities to secure your data at rest, in motion and in use. -
What is a cloud domain?
cloud is a generic top-level domain (gTLD) delegated by ICANN. It is managed by the Italian company Aruba PEC SpA, a wholly owned subsidiary of the same Aruba S.p.A., one of the largest distributors of Hostings and Providers in Europe. ... cloud domain doesn't have any restriction. -
What is domain with example?
Domain names are used to identify one or more IP addresses. For example, the domain name microsoft.com represents about a dozen IP addresses. Domain names are used in URLs to identify particular Web pages. For example, in the URL http://www.pcwebopedia.com/index.html, the domain name is pcwebopedia.com. -
What is access control in cloud computing?
This feature includes the restriction of end-users from accessing confidential files and folders on any web browser. Access Control in cloud computing ensures users can access business data from browsers specified through policy by the IT admin of an enterprise.
What active users are saying — caiq byline
Caiq countersign
if you'd like to talk about anything from this presentation with an AWS staff member please come and find us at the AWS booth next up we are honored to have hugh barrett vp technical solution CISSP CSS LP tell us to share with us a case study on performing a security assessment of the cloud using the risk management framework everyone hear me okay all right like Alexa said I'm Hugh Barrett VP of technical solutions I work for Telus Corporation we're a partner with Amazon and I'm here to talk about performing security assessments of the cloud using tools best practices and the risk management framework so before I jump in you know my presentation is gonna be really revolve around the risk management framework and the MIS 853 set of controls but as I'm doing this keep in mind that you can substitute these controls with your own controls so what I'm gonna try and go through and I'll try and get through this within the 35 minutes that was allotted to me it set the stage when a chat about the risk management framework quick overview talk about air grant air gap regions assessment of the cloud some common control provider themes assessment of your workload and they want to talk about the exact the 360 tool which is a tool that Telos offers to kind of help automate this cybersecurity process now how many of you in here actually are in a cybersecurity discipline all right this will be of interest to you it's it's a boring topic but it's a necessary topic right so the risk management framework how I say this back in the States and I'm quite sure you all known from the States based on my accent but back in the States we have a couple of air gap regions the c2s region and the SC twist region those regions are owned and run by our government and these regions are not connected to the public Internet these regions were built by Amazon they're run by the government and we had to assess these regions meaning you know you always say Amazon talked about that their their regions are very secure from a government perspective that's great trust but verify we wanted to go out there and make sure that they were secured the way we wanted them to be secure and when I say we I'm talking on behalf of the government and on tell us so we're the you know we use the risk management framework to help us get through this and and I'm gonna I'm gonna run through the risk management framework and I'm going to talk about how we actually did this assessment to make sure that the region was secure and then talk about how we secure those things that are gonna go into the region itself so the risk management framework is anyone familiar with NIST and a risk management framework the risk management framework is a six step process it's a it's a it's a very good process you know it came out back in the early 2000s this needed to have a standard that could be used by the entire government right and the model was one government one standard and this opened the door up to reciprocity meaning that if one agency had a system in another agency wanted to use that system that agency should not have to go back and reassess that system right all done with the same standard everyone can accept everyone's results so the first step of the the RMF or the risk management framework was categorize your system and it's a very important step right this is where we ask the system owner to tell us everything about your system document the system gather information about the system tell us what mission that system supports things of that nature step two was tailoring your controls and applying your overlays and applying your inheritance right so in step 2 of the RMF you would determine what controls you're gonna use by determining what type of data your system processes step 3 how did your system in your application implement each control so they start step two you would pick let's throw out a number 855 controls as a system owner you had to go through and document how your system implements each one of these controls right we need to have that documentation so we have a way to validate whether or not you're meeting these controls step 4 assess the security controls at that point we have a group of individuals we call them Assessors they go out there and they look at how you documented how you implemented the controls and they go out and test it to make sure that your system actually does what it says it was gonna do right no difference then when you go through your typical application development life cycle step 5 was the risk risk management step right so the Assessor assesses your control finds out that something failed the risk executive would go out there and determine whether or not that failure was anything significant right and that person had the ability to say we're gonna accept this risk or you have to go back and fix this before we can deploy your system into the cloud or into your data center at that matter step 6 was continuously monitoring so after step 5 and you did your risk assessment they gave you the thumbs up you got your what we call your authorization to operate or ATO we would then continually monitor that system to make sure that it's meeting the same set of controls that it was meeting when we did the assessment right and we call that continuous monitoring so we use this process to assess and certify that the Amazon air gap regions that we have deployed for our government and the the section of the our government that was using these air gap regions was our intelligence community right we had to make sure that this thing met the controls and was secure enough for them to start putting their mission critical workloads into these into this cloud so just some more of the risk management framework and these are key some key words I'm not gonna really talk on this too much I want to get into the meat of the presentation but the risk management framework is made up of three simple words right or three simple key words confidentiality integrity and availability right so for every system in the government we ask you to tell us how how sensitive this day is this data right you had to pick three choices low sensitivity moderate sensitivity or high sensitive your confidentiality we also want to know what is the impact to the system if this particular piece of information got out to the public right so that's how you determine your confidentiality of the system the next thing we have to determine is in the integrity of the system right and the integrity again it's three simple values low moderate or high and integrity talks about how accurate is this data if somebody was to change this data would it adversely affect your mission or could affect your your health care or anything right and then we had availability again three simple values how available should this system be low meaning that if the system goes down the operation will still run not a big deal high availability mean if the system went down it was it was critical to the mission the mission could not continue and that's that's how you judge these three values right everything in the everything in the risk management framework is based on confidentiality integrity and availability so how does this work before I get into that there's a couple of slides I had I wanted to make a point here so in the nest meant in the risk management framework we have controls and some people call them requirements we call them controls when we started you had a control that's let's say c1 for instance and there were 10 things you had to do to test to make sure you meet that control right can you imagine if one of these tests failed do you meet or don't meet the control right that was the problem we were having so we decided to take that then this regulation we broke it down a little further so we got rid of the AC one control and we broke it down into four different controls right how many of you ever had to read any regulations and they said well make sure that your system does this and does this and does does this right that was - that was too vague right we needed to something I said make sure your system does a and the next one said make sure your system does B and we have test procedures on how to validate that so now it was easier for us to say if you fail a c1a1 you're good you passed on the other three AC 181 was not very critical you can still pass that control right so we took it to a different level of granularity just so we can get that type of detail in our risk assessment so this matrix represents how the how the RMF was was used and how it works and how these confidentiality integrity and availability allow you to pick your control so every single control and again you can replace these miss controls with your own controls right every single control has a value as to confidentiality integrity and availability right so if you see X anywhere you see X anytime your confidentiality your integrity or availability has that particular value this control was applicable to your system right everyone following that so it's it's a mechanism or a formula for you for us to pick controls the next thing we did in the RMF is you didn't have to identify all the different data types such as system processes right does your system process you know first name last name address does it process personal identifying information does it process financial information you know does it process you know counterintelligence data right and you have to determine how important that particular data is based on confidentiality integrity and availability again right so you see those three words show up a lot so if my system was processing financial data the confidential confidentiality of that data was moderate the integrity of that data was low what's excuse me was high but the availability was low which means if the if the financial data wasn't around business could continue as usual right if the financial data was altered in any way it could have an adverse effect against my business so that's how that was laid out and that's how we were determined how we determine the pick controls with the risk management framework now I know you all in your government probably don't use the 853 but you could take your set of security controls and apply them to the same formula and be able to identify which controls you should deal with depending on the confidentiality integrity of your system right there's another thing in the risk management framework is called an overlay and overlays are very important so I spoke about reciprocity right so if you are your if it's your Department of Defense along with your intelligence community along with your health and human services divisions all of you using that the RMF framework to do your assessments but the defense folks there's a set of controls that are different for them so they would have a defense overlay which they can apply to the controls which will alter the controls based on Defense Health and Human Services may have to apply the privacy overlay right because you don't want your healthcare data being leaked out to the public so there's another set of overlays that I'll show you how to better protect that data but it's all based on the baseline of the C ima values right so we have those as well and then we have the common control providers right now this is usually associated with enterprise systems and you're gonna see how we use that to actually accredit the Amazon air gap regions that we use back in the States but a common control provider allows you to quickly do assessment so you always like to use the example of a DNS server that you can use to help authenticate and find hosts and so on and so forth if your system is utilizing a DNS server and the DNS server was already assessed then there's no need for you to reassess that inherit those controls and get the get the benefit of what that group did and then you know you just move on so karmic control providers we reduce the amount of work associated with your assessment it's a huge time saver right so the whole idea is if if you go through these steps that I just mentioned as you're going through the RMF and RMF risk management framework at the end of the day you'll have a list of controls that you need to assess your system against this time to be the screen from our product that shows you all your applicable controls and shows you what overlays are available for you so now let's let's touch an isolated region like I said before there were two isolated regions that we had in the states right one was our seat to us and one was the SC to us top-secret region secret region we got called in by our government to help them assess the SC twist right they wanted to start up another air-gap region Amazon set up the data center or set up the cloud and they don't have to assess it right like I said before trust but verify Amazon said their regions are very secure the government says yeah but I need to check it anyway so they call us in and they said we need help doing this assessment and the reason they call us in was the first time they assessed the one that had the checkmark air-gap cloud one it took them almost two years to get through that assessment right now they're starting up a new air gap region and they did not want it to take two years matter of fact they only had four months to get it done and they know they couldn't do it manually because the manual way was to take those charts and those matrices that I showed you and put them into a spreadsheet and use spreadsheets in a Word document to try to get this this assessment done so they call us in and you know before I go so is everyone here familiar with an air gap region is does anyone not familiar with what an air gap region is okay I should have asked a negative question so an air-gap region is everybody's familiar with Amazon Cloud right okay just check it so the the Amazon Cloud that you're used to use it is not an air gap cloud right you can get into your browser log on to the hotel Internet you can access your ec2 instance up in the cloud right in an air-gap region you can never do that that region is not connected to the Internet physically disconnected isolated region and it's done for a reason right the the owner of that region or I should say the the person who leases that region because Amazon owns that region they have complete control over who has access to it right complete control over what workloads go into that region they have the ability to enforce a process for vetting any workload that's going into that region and they have the ability to take advantage of all the AWS cloud off what the AWS cloud has to offer and I can tell you I don't know about the Singapore government but the US government if I wanted to stand up an application and it required me to get to servers that could take six months right just to get the two servers and then it could take another six months to get them to approve my application you know with the cloud I fibrin ec2 instance I load up my application I put it through the assessment process and I'm up and running that's one of the beauties of the cloud and the fact that it's air-gap and it's owned by an agency they have a lot more control they can they have a lot more freedom into allowing you to start up and shut down these regions this excuse me these instances so in doing the assessment we realize like I told you before the first cloud took a couple of years the next cloud could not take that long so we have to use some automation so that like I said they came to us they said hey we need your help we have a tool exactly 360 and another tool called exactly continuum these tools are designed to take in any one standard international standard domestic standard anything and what run that standard through an assessment process and come out at the end with a risk assessment fully baked so they needed to define a process because it the first time they did it there was no process they needed a way to enforce that process they also need a way to collaborate with Amazon in doing this compliance of that cloud they need to apply risk management they wanted something that would apply the risk management framework and then support multiple standards right believe it or not before before the risk management framework came about from this a lot of the different agencies and the government was using different standards very hard to move systems around when somebody's accession against ISO the other person is assessing against you know diskette somebody else's accession against the RMF so we support the multiple standards we map all those standards together but it was a lot easier when it's when it's just one standard and support multiple standards one more thing I want to say about that in our product we have a way to map standards so if I was to do an assessment using the RMF framework and I had to give you that assessment and you're using the Singapore regulation we can map those regulations one to one and you can take my assessment and it'll get applied to your set of controls and you can just look at how things stack up against your regulation versus the the regulation that's we're using very powerful feature used a lot by several of our agencies just so they can it they can achieve what we call reciprocity right so what do we have to do to assess this new cloud region that was coming online right the air-gap region and everybody remember what air gap means now right so we had to get detailed documentation of the region so we had to go out to amazon and amazon had to tell us everything about the region if you went to Amazon and asked them that question they're probably tell you to drop dead right but you know when you're waiving hundreds of millions of dollars they detailed it they gave us detailed document about the region a categorization of the data that will be processed we sat down and we said okay here's all the data that will be processed in this region you know intelligence data data targeting data XYZ data and we identified every single data and we use what they call the NIST 860 to identify the CI and a values of each of those individual data types that took some while but we got through it then to select the controls and overlays based on that CIA value we were able to select all the controls and they came up to about 855 controls that we had to then assess against needed a detailed description of how the air gap region met each control so we sat with Amazon and Amazon start with their service team and they for every single control how do you handle passwords they documented how to handle passwords how you do handle the encryption they documented how you're handling Chrisman's how you handled kms keys who gets to do that you know all of that was laid out for us something that they would normally not tell you know an average person right because that's their that's that's Amazon proprietary information and we have to treat it as such right so we don't go talking about that but we needed that because we had to verify that what they told us was how things work so for each implementation then we had to independently assess to make sure that what they said it it did it actually really did and then we had the the government leadership had to go through and look at any areas any areas where there were deficiencies if there were any and determine whether or not they wanted to accept the risk or have Amazon fix the problem so that they can get the region to a point of a secure level so you know we went through those steps and like I said we we got through this assessment in roughly about four months of an entire region so with that you know I I can stand up here and tell you that amazon's regions are very secure because we didn't find anything right so the way we did it so you know we looked at the amazon infrastructure and we applied all those controls and we assessed everything about the infrastructure the buildings you know the the the power the air conditioning is there a guard at the front is the guard have a gun is there a guard dog we all that we went through and we came up with about 856 controls that we had to test for that infrastructure layer of amazon right after that we generated what we call a security package and a security package is just documentation about how the region stacks up from a security perspective how it met each of the controls which ones it passed which ones it didn't pass what were the risks so on and so forth after we got the infrastructure layer done the next thing we had to do was identify out of those 856 controls how many of those controls actually could be inherited right so for instance I don't know if any of you ever seen in Amazon data center they're pretty impressive there's a there's a bunch of controls in the NIST framework called physical controls right and these are things like this they're a camera outside the building or the camera is X amount of feet apart you know is there a cooling system is there a backup powers there regardless all the physical controls right anything you would expect from any data center where you're gonna put your workloads so we identified controls similar to that and we would say ok if you're gonna put your workload in the Amazon Cloud you don't have to worry about power cool in space because they take care of that so that's something that's a control you can inherit and use right away right so if your application has to meet the PE controls you're done Amazon did them for you you get him for free after we went through and did all the all the analysis of the encroach controls after we did the assessment of that infrastructure layer of Amazon we came up with about 737 controls that were inheritable right that's great news and you and you'll see why the second part of the assessment we had to now assess all of the different services that we're gonna go into this air gap region right and when I say services I mean things like I am ec2 you know V PC directory services workspaces all those are services right consumer-facing services well not only did we have to assess the infrastructure we had to assess every single one of those services individually against the same 856 controls right because we determined that we wanted to be at this particular security level with the cloud because these are the different data types that we were going to be putting in the cloud so 850 6-7 37 so for each one of the services instead of having to go through and do 856 controls we only had to do 119 controls because the other 737 controls we inherited from the infrastructure right so although it took us let's say it took us two months to assess that infrastructure layer it took us weeks to do each of the services because now we were only responsible for 119 controls right and again in your own environment we place our controls at your controls but the same formula the same technique works and then we had the security packages and that was all the security assessment of the cloud right now all of those security packages made up what we call providers right provider project so now when you want to put your workload in the cloud we identified from each of those services which controls they can share out to workloads so when you do your workload your consumer workload now inherits that right and I hope you know I would hope that every one of you if you're gonna put a workload in cloud you would go through the you go through the drill of determining whether or not that workload is of any security risks right and you should take it through an assessment of its own but anytime there is a control that Amazon is providing for you that Amazon said it's already good is a control that you don't have to do right so then we had to go back and implement the Amazon shared responsibility model and that shared responsibility model says that Amazon will take care of a piece of the security and you have to take care of a piece of the security and that's what this was all about right the black layer is Amazon taking care of their partner's security and the blue layers you taking care of your part of it right so now when you're assessing your workload to put into the cloud if you notice the steps to assess the workload is is really no different than the steps we went through to assess the cloud itself right should be no difference you're following one standard everybody's marching to the same tune again so now instead of starting with the Amazon infrastructure you're starting with the Amazon consumer services right you're putting a workload infant into the cloud you're gonna utilize ec2 you may utilize I am you may use kms because you're doing some encryption then you have your your workload and these are the services that your workload is utilizing right I am s 3 RDS workspace and so on and so forth these are the actual controls that your your workload is gonna be assessed against and these are the controls at Amazon from a consumer perspective is providing to you right and the number of controls that you inherit varies from from East from service to service like if you had a requirement where your system has to make sure it or it's XYZ cloud trail that's audited for you right so part of the ordinate is done by cloud trail and your system has to do their part of the audit in so those two together you know it identifies a shared responsibility model and then you have your security baseline for your workloads then we go into continuous monitoring right in a way we do continuous monitoring there's a bunch of tools that are out there we had our continuum tool remember I mentioned that earlier that tool allows us to pull in things like your Nessus scans app detective web inspect all that comes in to continuum continuum sends that over to our other exact 360 tool and it starts continually monitoring these controls so you know exactly can go against cloud trail it can go against you the I am laws it can look at your easy tools it can make sure that all of your settings and configurations are the way they should be based on your initial assessment and we just keep monitoring that and if anything changes we'll alert you but more importantly we will update documentation for you right when you're using when you when you when you using our tool documentation is not something you should worry about but when you're doing an assessment your auditor is the first thing they want to see is the documentation right so when you have an automated tool when they say I want to see the documentation that's when you go back and you push the button and it just generates the documentation for you other than that you shouldn't generate that documentation if you want to know which controls are failing you go into your automated tool you run the Phil you know control report and it gives you a report right so I'm gonna take the last six minutes and talk about our product because it's a tool you should use when you're using this right away exactly 360 right everything I just talked about it supports matter of fact it was the tool that we use to do the assessment like I told you before when the government did their assessment of the first cloud they didn't use this tool it took them two years when they did the assessment of the second cloud they use this tool it took them four months right easy math I won't even do it because I probably can out the box exactly supports a lot of international standards ISO NIST cybersecurity framework you name it I mean literally we take controls and we apply controls to assets and we tell you where it where you're failing or not failing controls it's just a couple of walk through some screens so that you can see it right you remember I talked about the information types or your data types where you have to identify what type of data your application is is processing we have a list of them here right and the RMF has a documentation set that lists all of the different data types and what they perceive the CI and a value should be you can change this if you want control sets we allow you to pick which controls you want to use right now for us since this tool is being used for US government purposes we have US government regs in here but if you look at our library of control of regs we have 256 different regs we have ISO cybersecurity framework we have Defense regs intelligence regs HIPPA for health care a lot of different regulations are built into it here you have an inheritance questionnaire can you imagine if you're gonna put a workload in the cloud and you have to just all you have to do is go through and say oh yeah I'm using ec2 I'm using I am and we just automatically say here the controls that Amazon is gonna give to you and here you don't have to worry about them that's what this does for you and then we we have an automated screen that allows you to document how you're implementing these controls and we have a screen for the Assessors the person that's gonna go out there and test and validate each one of these controls they can go into the tool go through each control look at all the information that you put in and then determine whether or not you pass or fail that control very important important piece that has to be done right and we go through a lot of other things if you want to really see how this works and talk more about what we have done we have a booth across the hall in the Expo Center stop by we can chat for those of you who are interested in the RMF and like I said before I know I know a lot of people say hey well you know that's the u.s. standard we don't want to use it remove our controls and put your own in there and that framework actually is so granular it actually gets to the meat of where the the problems are when you're trying to assess a system so these are the documents that that make up the RMF the ones that you know if you if you really want to learn more about what I was talking about read through these documents do the 37 which talks about the framework the 53 which is all the controls and I can tell you I've seen a lot of controls your controls our controls you know the controls in Canada the controls in mechs are say the same thing right passwords ought it pick up you name it so it's a controllers of control and you have the 860 which is the which is the document that is of a lot of interest that talks about how you categorize data that the system is going to process and if you know what data your system is going to process you can better understand what controls and astringent of those controls that you need to apply to that system right you know a lot of people will tell you that this is a a pretty you know drawn-out tedious process it's not the sexiest part of the cybersecurity discipline but it's probably the most necessary right as any of you ever been hacked any of your systems haven't been hacked before I won't ask that question again you know when a system gets hacked the first thing the first thing at least in the States the first thing we do we go to this type of data to find out what controls were levied which ones that it didn't pass which ones were risk accepted which ones had outstanding mitigations that needed to be done because when that happens we we need to go back there to find out where we are and more importantly we need to find out what mission that system was serving right if that system that got hacked was you know if it was our missile targeting system that's something you need to deal with right away if the system got hacked was the system down in the you know Department of Defense Jim where the soldiers work out we can let that one sleep for a little while and we'll get to it whenever we can so it's good to have this type of data right any developers in the room so you know you probably will not do probably wouldn't write code if they didn't give you the extra quirements written down would you the same thing holds true you know you wouldn't want to set assess a system or put a system into your network without understanding all of the details about that system so that was my last slide again I know I went through this very quickly if you have any questions come across the hall where there we can we can chat with you and give you a demo explain the RMF in more detail to you right thanks a lot [Applause]
Show moreFrequently asked questions
How do I eSign a document before sending it?
How do I sign a PDF from my email?
How do I sign something in a PDF?
Get more for CAIQ byline made easy
- Picture electronically signing
- Prove electronically signed Car Rental Agreement Template
- Endorse digisign Governance Agreement
- Authorize signature service Hotel Receipt
- Anneal mark Motion Graphics Design Contract Template
- Justify esign Landscaping Services Contract Template
- Try countersign Construction Equipment Lease Proposal Template
- Add Participation Agreement signed
- Send Construction Quote Template digi-sign
- Fax Wine Tasting Invitation esign
- Seal Doctor's Note initial
- Password Freelance Contract Template signature
- Pass Affiliate Agreement email signature
- Renew Free Sublease Agreement digital signature
- Test Professional Medical History electronically signed
- Require Distributor Agreement Template byline
- Comment deponent countersignature
- Boost viewer electronically sign
- Call for beneficiary signed electronically
- Void Painting Contract Template template autograph
- Adopt Timeshare Agreement template digital sign
- Vouch Screen Printing Quote template initial
- Establish Pet Adoption Application template electronically sign
- Clear Executive Summary Template template countersignature
- Complete Travel Booking Form template digital signature
- Force Service Proposal Template template mark
- Permit Landlord Rent Receipt template signed
- Customize End User License Agreement template digi-sign