Cloud Security Trust Digital Sign Made Easy
Get the robust eSignature capabilities you need from the solution you trust
Choose the pro platform designed for pros
Set up eSignature API with ease
Collaborate better together
Cloud security trust digital sign, in minutes
Cut the closing time
Keep important data safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — cloud security trust digital sign
Employing airSlate SignNow’s eSignature any organization can speed up signature workflows and eSign in real-time, supplying a better experience to consumers and employees. Use cloud security trust digital sign in a few simple actions. Our mobile apps make operating on the go possible, even while off-line! Sign signNows from any place worldwide and make tasks in less time.
Take a walk-through instruction for using cloud security trust digital sign:
- Log on to your airSlate SignNow account.
- Locate your needed form within your folders or upload a new one.
- Open the document and edit content using the Tools menu.
- Place fillable boxes, add textual content and eSign it.
- Include numerous signers via emails configure the signing sequence.
- Choose which users can get an completed copy.
- Use Advanced Options to reduce access to the template and set an expiry date.
- Click on Save and Close when done.
Moreover, there are more extended features available for cloud security trust digital sign. List users to your collaborative workspace, browse teams, and track teamwork. Numerous users all over the US and Europe concur that a solution that brings everything together in one unified digital location, is what organizations need to keep workflows working smoothly. The airSlate SignNow REST API enables you to integrate eSignatures into your application, internet site, CRM or cloud. Try out airSlate SignNow and get quicker, easier and overall more efficient eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results cloud security trust digital sign made easy
Get legally-binding signatures now!
FAQs
-
How do you digitally sign?
Suggested clip How to digitally sign a document | airSlate SignNow Document Cloud - YouTubeYouTubeStart of suggested clipEnd of suggested clip How to digitally sign a document | airSlate SignNow Document Cloud - YouTube -
What is digital signature example?
Digitally signed messages may be anything representable as a bitstring: examples include electronic mail, contracts, or a message sent via some other cryptographic protocol. -
How do I do a digital signature in airSlate SignNow?
Choose the Fill & Sign tool from the airSlate SignNow dashboard and open the document you need to sign. Click the Sign tool, then Add Digital Signature. Please note that digital signatures must be enabled by your airSlate SignNow administrator. Select cloud-based digitial ID certificate, then click Apply. -
What is a digital signature Why is it used?
A digital signature is a mathematical technique used to validate the authenticity and integrity of a message, software or digital document. ... In many countries, including the United States, digital signatures are considered legally binding in the same way as traditional document signatures. -
How do I insert a handwritten signature in Word?
Sign your name on a white, unlined piece of airSlate SignNow. Scan the signature and save it as a bmp, . ... Start Word. Go to the Insert tab and select Pictures. Navigate to the signature file and select Insert. Select the image and activate the Picture Tools tab. -
What are the two things that a digital signature allows us to do?
This action achieves two things: it authenticates your digital signature, and it confirms the document hasn't been altered since you digitally signed it. You can also digitally sign an electronic document sent to you from another source, as long as they have included the signing function in the document. -
How do I sign a digital signature in airSlate SignNow?
Choose the Fill & Sign tool from the airSlate SignNow dashboard and open the document you need to sign. Click the Sign tool, then Add Digital Signature. Please note that digital signatures must be enabled by your airSlate SignNow administrator. Select cloud-based digitial ID certificate, then click Apply. -
What counts as an electronic signature?
Under the ESIGN Act, an electronic signature is defined as \u201can electronic sound, symbol, or process attached to or logically associated with a contract or other record and executed or adopted by a person with the intent to sign the record.\u201d In simple terms, electronic signatures are legally recognized as a viable ... -
How digital signature is created?
To create a digital signature, signing software -- such as an email program -- creates a one-way hash of the electronic data to be signed. The private key is then used to encrypt the hash. The encrypted hash -- along with other information, such as the hashing algorithm -- is the digital signature. -
How do I secure a digital signature in PDF?
Open airSlate SignNow, then open a PDF document that you want to sign digitally. Click \u201cAdvanced,\u201d \u201cSign & airSlate SignNow\u201d and \u201cPlace Signature.\u201d When prompted to do so, drag the rectangular signature block to the place in the document where you want it to appear. -
What is digital signature in cyber security?
A digital signature is a mathematical technique which validates the authenticity and integrity of a message, software or digital documents. It allows us to verify the author name, date and time of signatures, and authenticate the message contents.
What active users are saying — cloud security trust digital sign
Related searches to cloud security trust digital sign made easy
Cloud security trust digital sign
this is part 5 of microchips cryptography primer in this part we will discuss the chain of trust what if Alice and Bob don't know each other until now we only consider the case of Alice and Bob knowing and trusting each other if Alice and Bob are strangers before they can trust each other they must establish a chain of trust for both of us for both of them in which they share a common trust anchor or root of trust this root of trust will essentially vouch for Alice to Bob and vouch for Bob to Alice certificates are used to assure entities are genuine the trust anchor is usually the OEM or it could be a certificate authority a CA like key Rio semantic GoDaddy is etc how exactly are certificates used to establish trust in this cartoon example we assume that Bob's mom and Alice know and trust each other but Alice has never met Bob of course Bob knows and trusts his own mother Bob's mom happens to know that Alice will bump into Bob later on today so she asks Alice can you please give my son a message for me Alice responds Bob doesn't know me how will he trust the genuine the genuineness of the message no problem give him the certificate of message authenticity with this certificate he will be able to realize the message comes from comes from me and no other and he'll be able to trust it Alice bumps into Bob later on that day and says hey I've got a message from your mom Bob being suspicious says who the heck are you and what have you done with my mom Alice then presents the certificate Bob reads it realizes the message came from his mom and no other and he's very happy to hear from her now this is an example of message authentication you could imagine Bob's mom could have given Alice a certificate directing Bob to trust whatever Alice says from that point on this is the way systems are sometimes pruned off and given to clients if you know if we can go back to our lighting control or no lighting Network example a lighting company will come in to say a college campus and they'll put lights all over the college campus and during the install phase they will use the chain of trust right back to their headquarters but when they're done the college doesn't want them to have control over the lights they want their local server to have control over their lights so the lighting company will give a certificate to the local server which will then broadcast that to the entire network and now the entire network knows that the local server is the master of the network what's inside of these certificates the two most important things inside of the certificate is the subject public key and the digital signature using Bob's mom and Alice as an example when Bob's mom gave Alice a certificate what she did was she took Alice's public key that would be the subject public key and she signed it with her private key and that would be that digital signature now if this was an enclosed system and there was no need for interoperability with other vendors and other devices that would be enough the subject public key and its digital signature would be enough for all of the nodes in the network to trust but that's not always the case sometimes we have to interoperate with other vendors devices so we have this X dot 509 certificate with a lot more information in it it has the notice the second line it says algorithm ID other vendors might not know you're using say sha-256 or aes-128 or whatever you have to tell them also you might want to have a validity date or dates so something's not valid before particular time and not valid after a particular time and there's all kinds of things that we can put in this X dot 509 certificate along with the subject public key in digital signature now how does all of that other data get assured now how does the entire certificate become assured we know how a public key would be assured Bob's mom would simply sign the public key if we're using a certificate she wouldn't sign just the public key what would happen is all of this would be placed in a document that document would then be hashed and we would have a digest of the document Bob's mom would then sign that digest thereby assuring the entire contents including the subject public key let's look how certificates are used in a real-world system let's look at the example of asymmetrically authenticating ink cartridges for example these ink cartridges will be made by both the OEM and licensees of the OEM so we'll need a chain of trust because you'll have two different manufacturing sites creating encourages and both ink cartridges need to be authenticated in this case you'd never want to use a symmetric key because you would have to share that symmetric key with your licensee and you would have no way of knowing how well that licensee would would protect that key let's look at how this provisioning process happens in the factory the OEM will have a route of trust they'll either own this route of trust directly or they'll hire a certificate authority to manage it but the route of trust will have an authority private key and authority public key there will then be a manufacturing line that manufacturing line will have a hardware security module on it which will protect the public and private keys of the manufacturing line we will be making ink cartridges the disposable device on this manufacturing line and each ink cartridge will have its own public private key the first thing that happens is the manufacturing line will send its public key to the route of trust the route of trust will sign it with their private key adding a certificate this certificate will assure the world that this manufacturing line is genuine the manufacturing line will ask the secure element in the ink cartridge for its public key the manufacturing line will sign that public key with its own private key creating a certificate which tells the world or assures the world that this ink cartridge was made on that particular manufacturing line now when this ink cartridge gets out into the world people are going to want to know more then was this in cartridge made on that particular manufacturing line they need to know that the manufacturing line is genuine in itself so that information is also placed inside the ink cartridge now let's imagine ourselves in someone's home they have a printer they went to the store and bought an ink cartridge and they put it into the printer the first thing that we need to know is that the printer has the authority public-key every printer that we make would have to have would have to be programmed with the authority public key this public key it resides inside of a crypto element some of you may be saying wait public keys are not private are not private they're public information so why does it need to be protected it needs to be protected because if someone were able to change that public key they could essentially hijack the entire ecosystem and then have your printer only accept these rogue print cartridges it wouldn't even accept true OEM print cartridges anymore so the first thing we do is the printer has to verify the manufacturing public key it requests that public key and the certificate from the ink cartridge it uses the knowledge of the authority public key as well as the public key from the ink cartridge the manufacturing public key along with the certificate to authenticate the signature inside of that certificate once that authenticates now it can be trusted we now verify the device public key the printer asks for the device public key along with the certificate it verifies the signature on that certificate once that is verified okay we can go to the next step which is the challenge and response we need to challenge Andres and and get a response from the ink cartridge because if you look at everything we've done here so far you could easily record that and replay it at a later date how do you know it's truly the ink cartridge we have to test it we do trust the device public key but if that ink cartridge is truly who it claims to be it should also have the Associated device private key so we make a random number and we send it to the ink cartridge asking it to sign that random number the digital signature comes back and we verify that digital signature yes or no now we know the ink cartridge is truly genuine the whole idea of a disposable means that you'll eventually throw it out we could authenticate OAM ink cartridges all day but if we don't somehow limit their life people could simply refill them so all of our devices in fact most secure elements from most vendors have a monotonic counter it's a one way counter it can't be reset and we reprogram this counter for how many squirts the ink cartridge should have let's say it's a million squirts and after a million squirts we assume this ink cartridge is empty no matter how much ink is still left in it now let's create a signed an authenticated message Alice we'll start off with Alice's private key and the plaintext message she wants to send we're not going to encrypt anything here we're just gonna send it plain text and Bob will receive it and realize it comes from Alice nobody else but Alice and it was unaltered Alice hashes the plaintext creating a digest which she signs with her private key creating a signature she then puts the plaintext into a digital envelope along with the signature and sends this off to Bob Bob receives this digital envelope from Alice takes out the plaintext hashes it puts the plaintext to the side doesn't use it yet he doesn't realize it's genuine or not uses the digest from the hash along with Alice's public key to verify the signature now let's start talking about encrypting messages before we encrypt as you already know from previous parts of this presentation we need session keys or a session key maybe multiple maybe one depends on which cipher we use so let's talk about creating session keys with public key probably the best way in the PKI infrastructure to create a common key between two elements is diffie-hellman this presentation assumes elliptic curve cryptography so we will talk about ECD H this is elliptic curve diffie-hellman it's an anonymous key agreement protocol allowing two parties each with their own public private pairs to establish a unique secret between them assume Alice and Bob have public private key pairs if Alice takes Bob's public key and dot multiplies it with her private key and Bob does similarly if he takes Alice's public key and dot multiplies it with his private key math magically they will arrive at exactly the same number this is a way of arriving at a shared secret between two parties that never has to be transmitted Alice will know what Bob's public key is from when she authenticated Bob and Bob offered her the certificate and she verified the signature and remember all that so eat Bob and Al and Alice will have each other's public key and trust them so they do this diffie-hellman math and they wind up arriving at exactly the same number which is very convenient by the way this is used in TLS and when it's used in TLS it's known it's not known as a shared secret it's known as a pre master secret and none of another one of those annoying examples of different names for exactly the same thing sending encrypted message using diffie-hellman Alice wants to send Bob a secure message and Bob needs assurance the message came from Alice and was unaltered so Alice decides to send a message to Bob so the first thing she does is calculates the shared secret she has uniquely with Bob she takes Bob's public key that multiplies it with her private key and comes up with the shared secret once alice calculates the shared secret she's ready to go she starts off with her private key the plaintext and the shared secret she hashes the plaintext creating a digest which she signs to create the signature she then encrypts the plaintext with the shared secret creating ciphertext which she puts into a digital envelope and sends to Bob on Bob's end he needs to recreate that shared secret so he picks up Alice's public key dot multiplies it with his private key to create exactly the same shared secret that alice arrived at Bob opens the digital envelope that outlet that Alice sent and takes the shared secret to decrypt the ciphertext turning it into plaintext he then hashes the plaintext creating a digest which he uses along with Alice's public key to verify the signature and say yes or no this came from Alice or not if it's yes then it came from Alice and no one else and it arrived unaltered but the method we just described would use the same shared secret over and over as the encryption key we really shouldn't do that we should have session keys I explained this before in a in an earlier part of this presentation so a best practice would be to use diffie-hellman again this time we it's called ECD he4 looked a curve diffie-hellman ephemeral a ephemeral meaning short-lived the way this would work was would be first Alice and Bob would of course authenticate each other now Alice would have confidence in Bob's public key and vice-versa Bob would have confidence in Alice's public key now both Bob and Alice would spawn new public private Keys they would send their new public keys to each other the authenticated messaging we covered this earlier in this presentation they would take the new public key and of the other and dot multiply it against their own private key this would create a new shared secret based on the new public private keys they created they would use this new shared secret as their session key once used the shared secret along with the public private keys used to create it are completely destroyed and the next time communication occurs that process is repeated robust notification must be implemented prior to this because you would not want to authenticate potentially an adversary to create a shared secret with you this is often referred to as perfect forward secrecy if you can imagine say a video camera in your home or a security system it's in there for 10 years after a while you forget it's there you don't know what you've done in front of it you don't know what it's captured you don't want people to be able to decode everything 10 years worth of video if for some reason your keys were compromised using this EC DHE those keys can never be compromised because everything is is destroyed if someone were to do a brute-force attack on one transmission and they were let's say they were even successful with it they would have to do that brute-force attack on every single transmission that your camera made and that's just infeasible our devices can spawn new public private keys in milliseconds but let's assume you're using devices that were unable to do that so you couldn't use EC tha you could also use a KDF this is a industry standard deterministic pseudo-random number generator whose output depends on an initialization vector so you would use your your shared secret and a random number in this ktf or you could just use a random number and hash it with your shared secret to create a session key let's review how the whole system would work Alice and Bob have their public private keys through a chain of trust and authentication they would reliably exchange public keys they would then implement diffie-hellman to create a shared secret again if we're talking about TLS here it would be called a premaster secret they would create their session keys somehow they would use EC DHE ephemeral ECT H or they would use a key DF or they would simply hash their shared secret with a random number to somehow they would create a session key which would be used on a cypher to create plain Tec to take plaintext turn it into ciphertext and then turn ciphertext back into plain text now that we've gone over the fundamentals of cryptography the functions now let's talk about what's needed on a hardware level for strong security the first thing we need is a high entropy random number generator attacks on the randomness of the numbers used is one of the primary tax on cryptography so you really want to have a high quality high entropy random number generator any microcontroller you decide to use needs in a mutable area of genuine code which can be trusted this unchangeable unhackable area of code is relied upon to be used with your hardware cryptography to then ashore all the remaining code is genuine and then and only then do you bootstrap the system you need a hardware enforced persistent secure area for secrets and the critical crypto primitives hopefully with anti-tamper protections crypto authentication devices protect more than just the secrets and keys they have to also protect these crypto primitives of authentication integrity check key spawning things like that the reason is if you are able to hack these functions you no longer need the keys an adversary could have your device authenticate just about anything you need a strong cryptographic methodology and a robust chain of trust this presentation is assuming elliptic curve cryptography which is the current standard ECC has essentially replaced RSA due to the smaller key size and similar level similar levels of security ECC 256 bit is roughly equivalent to RSA 3072 bit so ECC is a very robust methodology to use you also need a well-thought-out ecosystem in infrastructure one of the awful truths is that any device can be hacked if someone is in physical possession of it and they have the motivation and the means to hack it you do not want any compromised unit to then compromised your entire ecosystem so we need to try to build ecosystems which can hopefully detect a compromised unit but even if it can't detect a compromised unit build it in such a way so that compromised unit can't compromise the entire ecosystem and again we we have this discussion with clients all the time and try to help them with this why hardware security features why not do this and firmware you know why not save the money the problem is many volt first you can't hide keys and firmware as much as you think you can you can't the problem is the keys are the result of high entropy random number generators and that means that the key itself is high entropy the problem with code in the embedded world is it's incredibly low entropy so all someone has to do is send your your your chip to a lab along with about $500 and they will D capsulate the chip and probe the chip and give you back the hex file of that microcontroller and the keys will shine out like beacons because they have such high entropy they will be different than all the other data around it hardware security devices are incredibly difficult to do that with for a number of reasons they have active shield to cross multiple layers all memories into are internally encrypted so even if they were able to get past the shields and get the get to the cells the information stored in those cells is encrypted we have data independent crypto execution it means that when you're very close to a key sometimes algorithms will resolve very quickly and if you're very far from a key they'll take much longer we take exactly the same amount of time no matter your no matter if you're one bit away from at the key or if all 256 bits are wrong we have randomized math operations so we don't do things in normal order internal state consistency checking voltage tampers temperature tampers etc all to thwart physical attacks another reason why you should consider hardware is it's much faster and lower power the functions that we're talking about our complex with lots of CPU cycles if they were if they were implemented on a microcontroller they'll use lots of power and take a long time on this graph you'll see key generation we'll do this in a couple of milliseconds whereas a cortex-m 0 plus running at 48 megahertz will do this in more than 3 seconds thanks for watching microchip channels and I hope you learned more about embedded security
Show moreFrequently asked questions
How do I eSign a document before sending it?
How do I sign a PDF from my email?
How do I sign a PDF online?
Get more for cloud security trust digital sign made easy
- Print signature service Lease
- Prove email signature Customer Satisfaction Survey Template
- Endorse eSign Service Quote
- Authorize digital sign Lease Amendment
- Anneal signatory Bridge Loan Agreement
- Empower electronically signed T Shirt Order Confirmation
- Try digisign Pet Adoption Letter
- Add Assurance Agreement eSign
- Send SaaS Sales Proposal Template eSignature
- Fax Free Graduation Certificate autograph
- Seal Training Acknowledgement Form electronic signature
- Password Indemnification Agreement signed electronically
- Pass Outsourcing Services Contract Template electronically sign
- Renew Pet Custody Agreement electronically signing
- Test School Counseling Progress Report mark
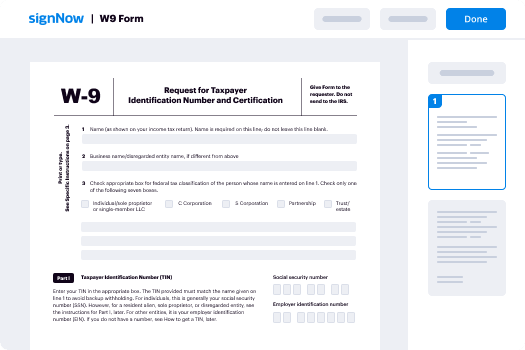
- Require W-9 Tax Form signed
- Send corroborator signature
- Accredit spectator initial
- Compel recipient digital sign
- Void Freelance Quote Template template esigning
- Adopt certificate template digisign
- Vouch Notice To Vacate Form template electronic signature
- Establish Proposal Letter template countersign
- Clear Founders’ Agreement Template template sign
- Complete Child Medical History template electronically signing
- Force Sales Agency Agreement Template template initials
- Permit Professional Model Release Contract template eSign
- Customize Interior Design Contract Template template eSignature