Fax Digital Signature Endorsement with airSlate SignNow
Get the powerful eSignature capabilities you need from the solution you trust
Choose the pro platform made for pros
Configure eSignature API quickly
Work better together
Fax digital signature endorsement, within minutes
Cut the closing time
Keep sensitive data safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

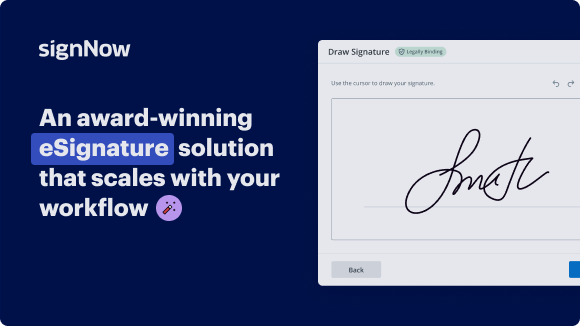
Your step-by-step guide — fax digital signature endorsement
Using airSlate SignNow’s eSignature any business can speed up signature workflows and eSign in real-time, delivering a better experience to customers and employees. fax digital signature endorsement in a few simple steps. Our mobile-first apps make working on the go possible, even while offline! Sign documents from anywhere in the world and close deals faster.
Follow the step-by-step guide to fax digital signature endorsement:
- Log in to your airSlate SignNow account.
- Locate your document in your folders or upload a new one.
- Open the document and make edits using the Tools menu.
- Drag & drop fillable fields, add text and sign it.
- Add multiple signers using their emails and set the signing order.
- Specify which recipients will get an executed copy.
- Use Advanced Options to limit access to the record and set an expiration date.
- Click Save and Close when completed.
In addition, there are more advanced features available to fax digital signature endorsement. Add users to your shared workspace, view teams, and track collaboration. Millions of users across the US and Europe agree that a system that brings people together in one holistic digital location, is the thing that businesses need to keep workflows functioning easily. The airSlate SignNow REST API allows you to embed eSignatures into your app, internet site, CRM or cloud storage. Check out airSlate SignNow and enjoy quicker, easier and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
Get legally-binding signatures now!
FAQs
-
Does IRS accept digital signatures?
The IRS made a temporary policy change on March 27, allowing IRS employees to accept digital signatures and images of signatures on certain documents related to determining or collecting a tax liability: extensions of the statute of limitation on assessment or collection; waivers of statutory notices of deficiency and ... -
How do I fax a signature?
Locate and click the fax you'd like to sign, then click Sign. In the Digitized Signatures popup, drag your digitized signature and drop it in the spot in your fax where you'd like the signature to appear. Resize or reposition the signature, as necessary. When you're done, click Save. -
Can a scanned signature legally binding?
As long as it's correctly done, courts have upheld that imaging and scanning are just as legally binding as airSlate SignNow documents. Legal acceptability of scanned document images depends on the process used to create the documents. -
Does IRS accept faxed signatures?
Yes. Although we prefer original signatures in ink, we will also accept scanned, copied and faxed signatures as well as original signatures in pencil. -
Will the IRS accept scanned faxed or copied signatures?
The IRS will accept images of signatures (scanned or photographed), including but not limited to, the following common file types supported by Microsoft 365: tiff, jpg, jpeg, pdf, Microsoft Office suite, or Zip. -
Is a fax copy a legal document?
Fax copies can be considered legal documents and are often accepted as such in many agencies and establishments. Thanks to the almost flawless anti-tampering method when it comes to faxing, many businesses will accept a faxed copy of an original document, such a signed contract, as legally binding. -
How do I fax a signed document?
To fax documents online, you just need to open that document or picture in your online faxing mobile app or web page, do the required edits including fill in the blanks, add your electronic signature, or add checkmarks, specify the recipient and hit the send button. -
How do I convert my signature to digital signature?
Sign a piece of airSlate SignNow. ... Scan the airSlate SignNow. ... Crop down to the best signature. ... Use the magic wand to select the area around the signature. ... Paste the signature into a new document with a transparent background. Use the magic wand to remove any white still left inside letters. -
What makes a signature legally binding?
As long as it adequately records the intent of the parties involved in a contractual agreement, it's considered a valid signature. Usually this mark is made by a pen, but not necessarily. The signature can be made by anything that marks the airSlate SignNow. -
How do I send a fax with Gmail?
Open your Gmail account and click on the \u201cCompose\u201d button to begin an email. Enter the recipient's fax number followed by @rcfax.com in the \u201cTo\u201d field. Attach the document you wish to fax from Gmail. Send your email, and the fax transmission will begin. -
Does the IRS accept scanned signatures on 1040?
The Form 1040, U.S. Individual Income Tax Return, already uses an electronic signature when it is filed electronically, either by using a taxpayer self-selected PIN, if self-prepared, or a tax-preparer selected PIN, if using a tax professional. -
Can I fax through email?
Send a fax from the Fax. Plus website, the iOS or Android app, Google Docs, or email services like Gmail and Outlook. Your first 10 faxes are free; after that, you need to sign up for a paid plan. ... Enter the receiving fax number and then attach the document you want to send. -
How do I send my signature to a document?
Open a PDF file and the airSlate SignNow tool. Open the Bodea Contract. ... Add recipient email addresses. Enter the email addresses of the people you want to eSign the document. ... Confirm form fields. ... Click Send. ... Manage documents sent for signature. -
Does the IRS accept faxed returns?
You cannot use a fax number for the IRS to file your tax return. While they sometimes accept faxes for some ongoing tax issues, like audits and problems with returns that are already being processed, they don't even publish numbers for people to fax tax returns to, generally speaking. -
Is a faxed signature legally binding?
A contract or legal agreement containing a photocopied or faxed signature is deemed valid and enforceable in most states. ... If a document is a simple contract between parties, a fax is okay to use \u2014 but an original signed document is better.
What active users are saying — fax digital signature endorsement
Related searches to fax digital signature endorsement with airSlate SignNow
Fax digital signature endorsement
in segment 1.3 we're going to talk about digital signatures this is the second cryptographic primitive along with hash functions that we need as building blocks for the cryptocurrency discussion later on so a digital signature is supposed to be just like a signature on paper only in digital form and what that means is this what we want from signatures is two things first that just like an idealized paper signature only you can make your signature but anyone who sees your signature can verify that it's valid and then the second thing you want is that the signature is tied to a particular document so that somebody can't take your signature and snip it off one document and glue it onto the bottom of another one because the signature is not just a signature it signifies your agreement or endorsement of a particular document okay so the question is how can we build this in a digital form using cryptography so let's get into the nuts and bolts here's an api for digital signatures there are three things three operations that we need to be able to do the first one is we need in the beginning to be able to generate keys and so we have a generate keys operation and we tell it a key size how big in bits should the keys be and this produces two keys s k and p k s k will be a secret signing key this is information you keep secret that you use for making your signature and pk is a public verification key that you're going to give to everybody and that anybody can use to verify your signature when they see it the second operation is the sign operation so the sign operation you take your secret signing key and you take some message that you want to put your signature on and it returns sig which is a signature it's just some string of bits that represents your signature and then the third operation is a verify that takes something that claims to be a valid signature and verifies that it's correct it takes the public key of the signer it takes the message that the signature is supposedly on and it takes the supposed signature and it just says yes or no is this a valid signature okay so these three operations these three algorithms constitute a signature scheme and i'll note that the first two can be randomized algorithms the verification won't be it will always be deterministic and in fact if you think about it generate keys had better be randomized because it ought to be generating different keys for different people okay so the requirements for the signatures at a slightly more technical level are the following two requirements first of all that if a signature is that valid signatures will verify if a signature is valid that is if i sign a message with sk with the seek with my secret key that if someone then later tries to validate that using my public key and the same message that that will that that will validate correctly so this says that the signa that signatures are useful at all but then the second thing you want is that it's impossible to forge signatures that is an adversary who knows your public key who knows your verification key and gets to see signatures on some other messages can't forge your signature on some message that he wants to forge it on uh and and in order to explain this property in a little bit more detail it's normally formulated in terms of a sort of game that we play with an adversary so the game i'll depict it here with this diagram so over here on the left you have the challenger who's a tv judge and the challenger is is going to test a claim by an attacker the attacker claims that he can forge signatures and we're going to test that claim and the judge will pass judgment on it the attacker here this guy is actually whit diffy who is one of the inventors of digital signatures of the concept of digital ex signatures and a distinguished cryptographer so i thought i'd let him play the attacker role here okay so the game works like this the first thing we do is we use generate keys to generate a secret key a secret signing key and a public verification key that match up now we give the secret key to the challenger to the judge and we give the public key to both parties both to the challenger and to the attacker so the attacker only knows information that's public he only knows the public key and his mission is going to be to try to forge a message the challenger knows the secret key so he can make signatures right now if you think about a real life application and a real life attacker would be able to see valid signatures from their would-be victim on a number of different documents and maybe the attacker could even manipulate the victim into signing innocuous looking documents if that's useful to the attacker so in our game we're going to allow the attacker to get signatures on some documents of his choice and we see that in the diagram like this the attacker is going to send over a message m0 to the challenger and the challenger is going to sign that message and send the signature back the attacker can look at that scratch his head a little bit and send over another message m1 the challenger will sign that and we do that for as long as the attacker wants the attacker can send over any sequence of messages he wants and get signatures on them once the attacker is satisfied that he's seen enough signatures and we're going to let him see only a plausible number then he's going to pick some message m that he wants to forge a signature on and he's going to try to forge a signature and of course there's a rule that says that this m this message that he's trying to forge a signature on isn't one of the ones that messages that he's already seen because it would be really easy for him to forge to send over a valid signature on m0 i mean we sent him a valid signature on m0 earlier so he's going to pick some other message that he hasn't seen his signature for already and he's going to send over what he claims is a signature on that message and then the question is can he succeed so the challenger is going to run the verify algorithm use the public verification key and on that message and the signature that the attacker provided and is going to check whether it verifies and if it does verify if this returns true then the attacker wins the attacker has forged a message and so this game is what we use to define what it means for a digital signature scheme to have the unforgeability property and if we want to get really precise what we say is that the attacker's probability of winning this game is negligible and that that's true no matter what algorithm the attacker is using in other words we're going to say that the signature scheme is unforgeable if no matter what algorithm the attacker is using the attacker has only a negligible chance of successfully forging a message and if we have that property together with the much easier property that valid messages verify then we have a digital signature scheme that is suitable okay now there's a bunch of practical things that we need to do to turn that algorithmic idea into a more practically implementable signature mechanism for example the algorithms we talk about are randomized at least some of them will be and so we need a good source of randomness and this the importance of this really can't be underestimated banned randomness will sink you your algorithm will be insecure and i'll just point out here that attacks on the source of randomness are a favorite trick of intelligence agencies and those are the people who know what kinds of attacks are likely to be successful in practice there's a limit on the message size that you're able to sign because real schemes are going to operate on bit strings of limited length the fix to that is simply to use the hash of the message rather than the message itself that way the message can be really big but the hash will be only 256 bits and because hash functions are collision free it's safe to use the hash of the message as the input to the digital signature scheme rather than the message and by the way a fun trick which we'll see used later is that you can sign a hash pointer and if you sign a hash pointer then the signature covers or protects the whole structure not just the hash pointer itself but everything it points to and everything it points to for example if you were to sign the hash pointer that was at the end of a blockchain the result is that you would effectively be digitally signing the entire contents of that blockchain that's a useful trick that we'll see used later okay now let's get into the nuts and bolts bitcoin uses a particular digital signature scheme that's called ec dsa that's the elliptic curve digital signature algorithm and it's a us government standard and we won't go into all the details of how ecdsa works it relies on some extremely hairy math and trust me you don't want to see all the details of how that works you can look it up if you're interested so we'll skip that one thing i'll note though is with ecdsa good randomness i said this before but i'll say it again because it's really essential good randomness is especially essential with ecdsa if you use bad randomness in generating keys or even in signing you probably leaked your private key it stands to reason that if you use bad randomness in generating a key that the key that you generate is maybe not secure but it's a quirk of ecdsa that if you use even if you use bad randomness just in making a signature using your perfectly good key that also will leak your private key and then it's game over so we need to be especially careful about this in practice this is a common mistake so that completes the discussion of digital signatures as a cryptographic primitive and then the next segment we'll move on and talk about some applications of digital signatures that will turn out to be useful in building cryptocurrencies
Show more