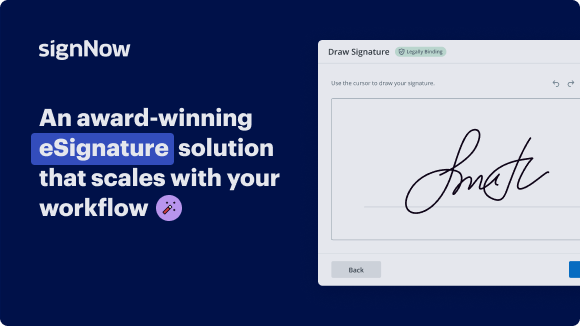
Fax Electronic Signature Currency with airSlate SignNow
Upgrade your document workflow with airSlate SignNow
Flexible eSignature workflows
Fast visibility into document status
Simple and fast integration set up
Fax electronic signature currency on any device
Detailed Audit Trail
Rigorous protection requirements
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — fax electronic signature currency
Using airSlate SignNow’s eSignature any business can speed up signature workflows and eSign in real-time, delivering a better experience to customers and employees. fax electronic signature currency in a few simple steps. Our mobile-first apps make working on the go possible, even while offline! Sign documents from anywhere in the world and close deals faster.
Follow the step-by-step guide to fax electronic signature currency:
- Log in to your airSlate SignNow account.
- Locate your document in your folders or upload a new one.
- Open the document and make edits using the Tools menu.
- Drag & drop fillable fields, add text and sign it.
- Add multiple signers using their emails and set the signing order.
- Specify which recipients will get an executed copy.
- Use Advanced Options to limit access to the record and set an expiration date.
- Click Save and Close when completed.
In addition, there are more advanced features available to fax electronic signature currency. Add users to your shared workspace, view teams, and track collaboration. Millions of users across the US and Europe agree that a solution that brings everything together in one unified digital location, is exactly what enterprises need to keep workflows performing effortlessly. The airSlate SignNow REST API allows you to integrate eSignatures into your application, website, CRM or cloud. Try out airSlate SignNow and enjoy quicker, smoother and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
Get legally-binding signatures now!
FAQs
-
Can you fax electronically?
Online faxing is an efficient and eco-friendly way to send important documents. To fax a PDF, use a service that supports the airSlate SignNow document format such as FaxZero, MyFax or eFax. Each service allows you to upload a PDF and send the document to any fax number in a few steps. -
Can you fax from a regular printer?
Most printers are able to automatically receive and print the fax. If the printer is out of ink or airSlate SignNow, it will hold the fax in memory and attempt to print the fax at a later time. Some fax machines can receive a fax and forward a copy of it to an email. Typically this feature is found on corporate level devices. -
Can I send a fax from my Gmail?
Once you are in your Gmail account and ready to send a fax, follow these simple steps: Open your Gmail account and click on the \u201cCompose\u201d button to begin an email. Enter the recipient's fax number followed by @rcfax.com in the \u201cTo\u201d field. Attach the document you wish to fax from Gmail. -
How can I send a fax without a fax machine?
Sign up for a free account on FAX. ... Go to the Send Fax section and enter the recipient's fax number in the To field (country code + area code + fax number) Click on the Add Text or Add File buttons to attach the documents you wish to fax. Send your fax right away and wait for the confirmation email. -
How do I fax a signature?
Locate and click the fax you'd like to sign, then click Sign. In the Digitized Signatures popup, drag your digitized signature and drop it in the spot in your fax where you'd like the signature to appear. Resize or reposition the signature, as necessary. When you're done, click Save. -
Can you fax through email?
Send a fax from the Fax. Plus website, the iOS or Android app, Google Docs, or email services like Gmail and Outlook. Your first 10 faxes are free; after that, you need to sign up for a paid plan. ... Enter the receiving fax number and then attach the document you want to send. -
Can u send a fax via email?
How to send a fax online from mobile? (iOS and Android) ... PLUS iOS app lets you fax document right from your smartphone or tablet. You just need to download the fax app from Play Store or Apple App Store for free, login to your account, go to the Send Fax section, and you know the rest. -
How do I legally sign a document electronically?
As with a handwritten signature, a signer must show clear intent to sign an agreement electronically. For example, signers can show intention by using a mouse to draw their signature, typing their name, or clicking an \u201cAccept\u201d button that is clearly labeled. Consent to do business electronically. -
How do I fax a signed document?
To fax documents online, you just need to open that document or picture in your online faxing mobile app or web page, do the required edits including fill in the blanks, add your electronic signature, or add checkmarks, specify the recipient and hit the send button. -
How do you send a fax electronically?
Go to efax.com/login. Log in to your eFax MyAccount and select Send Faxes. Enter recipients' addresses or add them from your contact list. ... Your recipient receives your document and cover letter exactly as they would a normal fax \u2013 it's as easy as email! -
How do you put a signature on electronic documents?
Attorneys may use an electronic signature in place of a scanned document with their written signature on it. * Signing documents in this manner helps save time as it avoids the need to print out a document, sign it, and then scan it again to e-File. -
Are online signatures legally binding?
Electronic signatures have carried the same legal weight as traditional, airSlate SignNow-based ones since the United States Electronic Signatures in Global and National Commerce Act (ESIGN) was passed in 2000. This legislation ensures that electronic signatures are legally binding in every state where federal law applies. -
Is a faxed signature legally binding?
A contract or legal agreement containing a photocopied or faxed signature is deemed valid and enforceable in most states. ... If a document is a simple contract between parties, a fax is okay to use \u2014 but an original signed document is better. -
How do I send my signature to a document?
Open a PDF file and the airSlate SignNow tool. Open the Bodea Contract. ... Add recipient email addresses. Enter the email addresses of the people you want to eSign the document. ... Confirm form fields. ... Click Send. ... Manage documents sent for signature.
What active users are saying — fax electronic signature currency
Fax electronic signature currency
all right y'all welcome back and in this video i am going to be teaching you about digital signatures now in this tutorial what we're going to be doing is sending 100 points to christy and if you don't know who christy is she is the design lead for the new boston and we can say that i owe christy 100 coins for giving me a slice of pizza sounds like something that i would do actually so all right now i know how this thing works we hit send coins select christy type in 100 and hit send whoa whoa before we do that let's go ahead and think about this so i know from my last videos that i just watched that the moment i hit send this transaction which is essentially in normal terms saying bucky is sending christy 100 coins what it's going to do is it's going to wrap it up in a piece of data and send it off to the network now it's first going to go to a bank and then go to all these validators where they can validate the transaction however thinking about it a little bit closer i know that this is actually a peer-to-peer network and anyone in the world can just spin up one of these servers and join it okay so if there's a piece of data out there floating around with my account number saying i am sending 100 coins to christy how do i know that one of those computers isn't just gonna manipulate it maybe they're gonna say send a hundred coins to dwight or whatever the hacker's name is or maybe they're just gonna try to mess with me and say send ten thousand coins to christy when i only wanted to send her a hundred okay so we have a couple challenges here in a peer-to-peer network we know that we can't store our password anywhere on the network because someone would just steal it in like half a second but somehow whenever i send a piece of data and in this example it's going to be the transaction i need to prove two things one that the piece of data has not been messed with for example someone can't change my 100 to 10 000. another thing that the network needs to be sure of is the sender so for example when i send chris the 100 coins they need to know that i authorized that and of course it wasn't like uh caleb sending christy 100 coins they need to verify that it was indeed me but how do you do that without a password because you know whenever you log into your bank whenever you log into facebook whenever you log into youtube you always use your password so that's how they check but what about in the peer-to-peer network how exactly does that work now in order to really understand this let's go ahead over here and create a new account so i'm just going to name it back on because kind of just felt like it and all right now an important thing to remember is that whenever you create an account on the network what the software is doing is actually generating two key pieces of information the first very important piece of information is called your sign-in key now the signing key is technically your private key if you're reading any books about cryptography or anything so this is your private key and this is your public key now in this network we actually just rename it to sign in key and account number to make it more user-friendly but you know i know a lot of people like to get technical sometimes so there you go so why two why did it generate two things well to understand that we have to understand something else a little trick in mathematics and that is something called a one-way function so check this out even though these things have some letters in them like a c d these are actually just random numbers now they are numbers that are stored in a format that has letters represent the values of the numbers so that's why when i refer to this as a number even though it has letters in it then you know it kind of makes sense so essentially what this algorithm did whenever i created an account is it generated this random number first now once it had this random number it ran it through something called a one-way function and it got this account number so a key piece of information to remember is if you have your sign-in key you can always easily calculate your account number from it in fact whenever you back up your account you don't even need to back up your account number itself you just need to back up the signing key because it in a way encapsulates both pieces of information now i say that because in this tricky mathematical algorithm you can't go the other way around if you have someone's account number or your own you can't get the sign-in key from that so it's a mathematical function that only works one way now to really nail down this concept let me just show you real quick the concepts behind functions and inverse functions and then you're going to understand one-way functions so a function is just something that takes some input and returns some output so let's say we had two values a and b and this and right here or ampersand it doesn't matter if it's adding multiplying whatever it's just a demonstration so you have a and b is your input and you end up with c okay now if you had another function that took c and it gave you back essentially the opposite of that where you had c is the input and you ended up with a and b this would be called an inverse function it essentially reverses the original function all right bucky i thought this was a tutorial about digital signatures and not like uh middle school math so what exactly is going on here well check it out if you have a function where you take two inputs and you have a given output which is of course pretty easy to calculate however if the inverse of that function is incredibly hard to calculate then this is called a one way function a function that's easy to calculate one way but more or less impossible to calculate the other way now i don't want to say impossible because you know quantum computers yada yada tomato tomato but that's the main concept of it now a better example of this rather than a b and c would be something like let's say that you had a 1093 and then you multiplied it by 1039 so this and i can already tell my font size is way too big okay okay good enough all right so this will give you one million one hundred and thirty five thousand and six hundred and twenty seven definitely just did that in my head okay i definitely sold this example off the internet but you get the point so you can see pretty easily that if you have two prime numbers then you can get this as a result now the game gets a little bit more fun what if i just gave you this number and i didn't have this at all let me just make it white alright so it's missing so what if i gave you just this number 1 million 135 627 and i said give me two prime numbers that you can multiply together to get this now unlike this function right here where if you had these two values then this solution would be pretty easy to calculate if you only had this solution or the output the two inputs would be very difficult to calculate in fact this might take you if you're doing it with like a pen and paper i don't know a minute maybe and this might take you an hour an hour or two i don't know so that is a better example of a one-way function a function where it's easy to compute the input to output but very difficult to compute the inverse so i'm sure you guys can see where this is going and how it relates to our network and that is whenever you create an account your key pair and that is your signing key in your account number is generated using this one-way function and that is also why if you ever lose your account number but you have your sign-in key then it's easy to get your account number back however if you just have an account number it's pretty much impossible to get your signed key so now we get to look at this awesome chart that i created and it took me like two hours so you guys better like it alright so check it out so i couldn't find a cool photo of a laptop so i just got my little phone here and through the account creation process you're gonna get something called a key pair like we said you end up with a signing key and an account number and let me actually open this and probably don't need this anymore delete that bad boy probably could have done that after the tutorial but okay so sending a hundred coins to christy now as you can see in this digital signature process we need to verify two things one is the sender and that would be me in this example and the other thing is you always need to have some piece of data now in this video that piece of data is going to be the transaction now the transaction is more or less going to say send 100 coins to kirsty so check it out we already went over the key pair process and this is gonna resemble the data now whenever you have that data and this data is just plain text it's json it's whatever you want to sign you're gonna run it through a hash function now in our digital signature process it's actually the ed25519 and it uses sha 512 i believe is the hash function but essentially we have a piece of data we're going to hash it with in this case sha 512 and we're going to end up with a hash value okay now with that hash value we're going to take our sign in key remember this is the private one they got keepsake secret say secret what am i talking about so with this hash value you're going to encrypt it using your sign in key now this encrypted hash is your digital signature so again a digital signature is just a piece of data that you run through a hash function and you get a hash value or a hash now when you sign that hash with your sign in key that output is your digital signature now what we're gonna do is we're gonna take this signature and we're gonna send it to the network with two other critical pieces of information the first one is the original data now why do we send this we send this because first of all it's the important piece of information that the network's gonna have to read and understand what we're trying to do and another thing as you're gonna see later on is they actually use this when verifying the signature so okay we're gonna send the signature the data and what's the last piece of information the last piece of information and i'm sure you guys can figure this out by this huge jumbo arrow right here that is the account number okay so what the network needs to verify all of this information which is essentially saying i'm sending chris the 100 coins from bucky is the account number the original message in the digital signature now i repeat that because take note that what you are not sending is your sign-in key huh that is interesting so the network's apparently going to be able to verify it without giving away the signing key that's pretty cool okay so now let's continue on our journey through the network that's the sound it actually makes going through the network in case you guys didn't know and okay there we go so by the way um this part at the top just resembled what i was doing on my local computer and then this part below the dotted line resembles something that the banks or the validators would be doing so let's just say that we're the primary validator to give us a little bit more of context and we are looking at this block that just got sent to us by bank and we need to verify that it was indeed bucky who sent this data so this is actually a pretty interesting process and it's kind of uh two steps and then you compare two values to see if they're equal so let's go over the first step first so what we're going to do just like bucky did whenever he signed this and remember bucky took that original data ran it through a hash function and it got a hash value what we are going to do is the exact same thing now he just didn't send us the hash value because even if he did we wouldn't trust this hash value anyways we would want to calculate our own just uh you know just to be sure so we're going to take that same data run it through the same hash function and get the same hash value as bucky ended up with right here now after that what we are going to do is we are going to take this chunk of the block the digital signature and we are actually going to decrypt it using the account number okay so this is essentially the opposite of before because before what you did is you had a hash value and you encrypted it using your signing key and you ended up with your digital signature but now we are starting with the digital signature we are decrypting it using the account number and what we're ending up with is the hash value okay so essentially the opposite of the signing process and by the way this entire thing is called the verification process so we as the primary validator are going to do those two processes each of which end up with a hash value now after both of those things are done we are going to compare both of those hash values this one and this one this one came from the original data and this one came from the digital signature that bucky provided now if those two hash values are identical then the signature is valid and that's it now the beautiful thing about this is if we just go ahead and recap one last time is that bucky is able to keep the sign-in key on his own device now with that signing key which is like a personal password in a way he can create pieces of data that he can send to anyone in the world and those people can verify that the data did indeed come from him and also that it was not tampered with because if it was tampered with in even the least bit if you changed one little character on the digital signature or just added one little character in the message or just tweaked the account number even by just a tiny bit the hash value is going to be way off and is going to be invalid so through this process we are able to create a peer-to-peer digital currency network while keeping our signing keys private and letting the network validate everything correctly all right i was actually thinking about ending the video there but then i was like maybe they want to see this bad boy in action so i created this little program and check it out what this is essentially doing is it already has a signing key built in no coins in there if you guys think about stealing it and all it's doing is it's creating a message it's gonna form it and then this other script is gonna verify it so one script to create it and one script to verify it all right so this data right now is just saying hi my name is bucky roberts let me just go ahead and run that and yep this is the message that it created and when we verify it if it looks good it just says valid right here all right so now let's do something else like send 100 christy all right i just want to show you this real quick so when i run this it's going to create a valid block essentially a valid signed message in by the way this is the account number this is the message and this is what the digital signature is going to look like now this is going to be valid whenever i verify because i didn't do anything with it so it says valid let me just pump that up all right now check out what happens whenever i manipulate anything so let's say that okay this is bucky's account number 53bo the why give me that account number anyways let's say that i hackerman had an account 63bo well whenever the network tried to validate that it would say invalid okay let me just change that back so apparently we can't change the account number now what if we do something like this instead of send a hundred coins to kirsty let's just do send ten thousand coins to christy run this invalid again okay so i have to change that back trying to hack this thing okay valid now signature 6e37 okay now if i'm a bank i'm thinking that i can just make my own signature so what if i just tweak this six to a two and run this invalid so okay let me just change that back in valid again all right so apparently if i in i in this example am pretending to be a bank server or a primary validator or whatever try to manipulate any single piece of data in this digital signature schema then it's going to be invalid only when everything signed by the creator which is me bucky my other identity only when the data is in its completely original form with every single bit every single byte in place untampered with that is the only way that this is validated so with that said i hope you guys loved my chart i hope you like this example thank you guys for watching don't forget subscribe and i will see y'all later
Show more