Fax Mark Conclusion with airSlate SignNow
Get the powerful eSignature capabilities you need from the solution you trust
Choose the pro service designed for professionals
Set up eSignature API with ease
Collaborate better together
Fax mark conclusion, within a few minutes
Decrease the closing time
Maintain sensitive information safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

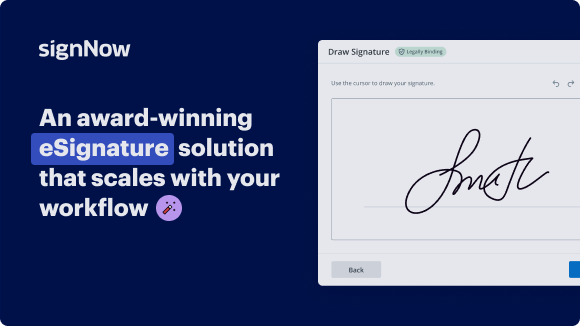
Your step-by-step guide — fax mark conclusion
Using airSlate SignNow’s eSignature any business can speed up signature workflows and eSign in real-time, delivering a better experience to customers and employees. fax mark conclusion in a few simple steps. Our mobile-first apps make working on the go possible, even while offline! Sign documents from anywhere in the world and close deals faster.
Follow the step-by-step guide to fax mark conclusion:
- Log in to your airSlate SignNow account.
- Locate your document in your folders or upload a new one.
- Open the document and make edits using the Tools menu.
- Drag & drop fillable fields, add text and sign it.
- Add multiple signers using their emails and set the signing order.
- Specify which recipients will get an executed copy.
- Use Advanced Options to limit access to the record and set an expiration date.
- Click Save and Close when completed.
In addition, there are more advanced features available to fax mark conclusion. Add users to your shared workspace, view teams, and track collaboration. Millions of users across the US and Europe agree that a system that brings people together in one holistic digital location, is the thing that businesses need to keep workflows functioning easily. The airSlate SignNow REST API enables you to embed eSignatures into your app, website, CRM or cloud storage. Check out airSlate SignNow and get faster, easier and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
Get legally-binding signatures now!
What active users are saying — fax mark conclusion
Related searches to fax mark conclusion with airSlate SignNow
Fax mark conclusion
hello everyone thank you for attending this talk it's a pleasure being in code blue and it's a pleasure being in Tokyo it's my first time in Japan and I'm here to talk to you today about a recent research project that we did we named it what the Fox so just before we begin a bit about ourselves so this is me my name is Genevieve Alma's and I'm a security researcher I work for a checkpoint and my colleague in this research project is a young 18 also security researcher checkpoint which unfortunately could not be here with us today but he is with with us in spirit so before we begin just a bit about the history of fax so it all began in 1846 when a scientist named Alexander they invented the first ever something that looks like oxygen sent the first image of a wire this happened in 1846 just roughly 20 years before the invention of the light bulb right and then it continued in 1860 the first thing that looks like a fax machine came to be again 20 years before the invention of the telephone and then there were more developments like radio fax and then in 1966 a very small company that nobody heard of called Xerox they invented the they came out with the first commercial fax machine it looked like this and then in 1980 a group called ITU defined the current standards for fax namely T 30 T 4 and T 6 so apparently fax had a very big part in the technological history and its really changed the way that we send and receive electronic documents for one to the other but that was all in the past I mean today we have far better ways to send 20 their documents from one to the other right so let's just try and compare facts to one of the you know more common techniques let's say email for example so just to remind you we are comparing this to this right so in terms of quality I really have nothing to add you know you just saw the pictures in terms of accessibility what I'm pretty sure that most of you if not all of you have 24 by 7 access to emails not so sure you are carrying around your fax machines with you in terms of reliability well when you send an email you know that it gets received or not received but when you're sending a fax you have absolutely no verification yes there is this page saying received ok but if there was no paper in the printer for example you still get the same receive so absolutely no reliability in fax and regarding authenticity well we can argue whether or not email is authenticated but there are solutions like public Creek public key cryptography and stuff like that what we don't have is we have nothing for fax absolutely nothing right so looking at this table you might think ok so nobody should use fax anymore right wrong everybody uses fax it's used in naval to in ships in in the open seas to receive this kind of very critical topology maps in Japan fax is very popular almost everybody in Japan uses fax and if you just do some Google combos like you know contact us and fax you will find something like three three hundred and eighty million results on Google so these are they published fax numbers on Google think about how many fax numbers are not published it's simply huge right and and in thinking about that you know it's not only the numbers does know not only how many people are using fax but it's also who is using fax well if you're a small company a media company or a huge cooperate you use fax you have a fax number right I don't know if you receive anything over that fax number but you do have a fax number if you're a bank Bank of China it's the biggest bank in the world and this is the flex number we just Google it up and obviously if you're a government institution you really love facts you wake up in the morning and you want to have some facts so if you want to fax the Donald Trump and the white house this is the fax number again just google it so fax is out there and I think that the crazy thing is sometimes these government institutions they don't only allow you to send fax but it's actually mandatory to send fax there is no other way you cannot send an email it's other postal mail or fax this seemed like a crazy thing to us I mean we are in 2018 how can it be that we still we are still so dependent on fax so in order to understand that a bit you need to understand how those facts looks like today you see 20 years ago fax was this standalone machines right it was only fax but today fax the same old technology is wrapped with newer technologies so for example we have you know services like email to fax fax to email stuff like that we have fax over radio we have fax over satellite and I think that most commonly we have this these things its all-in-one printers these things come shipped with a telephone cord that you can connect and they do fax they do a lot of other things but they also do fax it's default and our research in our research we decided to focus exactly on those all-in-one printers so if you look at these printers from a security point of view you can consider them to be black boxes right and on one side of these black boxes you have interfaces like you know Wi-Fi internet Bluetooth stuff like that those interfaces connects the printer basically to the internal network to the external network Oh to the world and on the other side of this printer there's this little interface which connects it to well somewhere in 1970 I would say to the telephone line and so if you understand that at the end of the day those printers are really nothing but computers I mean they have CPUs they have memories they have an operating system so we talk to ourselves okay what will happen if an attacker sitting somewhere in the world with access to the telephone line and equipped with its targets fax number what will happen if he will be able to send a malicious fax that will enable him to exploit this printer and actually take control of the printer if he would be able to do that he could then give it through any one of the other interfaces let's say the internet and go into the internal network effectively creating a connection between the external world and the internal network through nothing but the telephone line it's 1980 again right so we thought that this is a really cool idea and challenge accepted and we decided to do it so after we got a bit excited about the listing we sat down and actually started thinking about the challenges ahead and it turns out that there are quite a few challenges and let me just name the major ones of them so for example okay how do we obtain the film work how do we obtain the code of this printer and then how do we analyze this framework and then what operating system is this thing running is it Windows is that Linux is it the real-time operating system I don't know and after we understand that how can we debug this thing debug it printer I never debug the printer and then after we understood all this we need to understand how those facts even work I don't know and after we did all that we can start discussing work and we find vulnerabilities inside this printer so these are a lot of questions and today during this talk I'm going to take you through all of these questions one by one hopefully you will understand everything by by the time that I'm finished so let's start with the first question how to obtain the framework of the printer so we had to choose the printer to work on and meet our printer this is the very poop printer that we abused for so long it's an HP printer it's an HP Officejet printer we chose HP not not because we dislike HP simply because HP has something like 40 of the market chief for for printers so they seemed like a very good target to us and this specific model well I can say a lot of tea a lot of things about why why we chose this model but basically it's the cheapest one so yes we bought this printer and now we need to break fax but before we break fax we need to break the printer and I mean literally break the printer so this was the fun part of the research so we took everything apart and it looks something like this basically this is the heart of the printer that's how it looks like from the inside so it has a lot of components on it let's try and look at them so this is a flash rom manufactured by expansion and this is an SRAM so if you look at it it might look like two little components on this PCB and that's right because it has another side and on the other side are the more interesting components stuff like USB Wi-Fi electricity SRAM this big battery that does something I don't know but most interestly most interesting there are two components here one of them is this and this is the main CPU it's a CPU manufactured by Marvel and it's manufactured probably for HP so you can get this online you can do nothing with it it's just it just for HP and then there is this this is the fax modem and what we need to do in our research is to understand these two components and the relationship between them if we can do that maybe we can do our work so as I said the first challenge was to obtain a few more and when we look a bit closer at this PCB we find some things that look very promising two interfaces one of them is called civil debug another called JTAG and it's clearly marked on the PCB so looking at this if you're not familiar with this interfaces so basically they are debugging interfaces they will let you read memory write memory so basically this is what we need in order to to get the code of this filmer so when we looked at this we say ah this is going to be too easy but unfortunately things don't go the way we want to every time is completely disabled we cannot use it and the serial port we were able to connect to it and we got this nice terminal which gives us this arrow for almost every instruction that we try to do ever I don't understand what we don't understand either but what we do understand is that the serial is not going to get us very far so we need to find some other way to get this film well luckily for us after looking a bit we find a very nice FTP site online so this is the FTP site apparently it's an HP FTP site which contains every female version for every HP product ever produced in the entire history it's a huge FTP site it actually took us something like two weeks to find our film work inside this mass of film was it was very funny but then we found the file and now that we have the ephemeral update file which is supposed to contain the code for the film well we now need to understand how do we upgrade the printer phew I never did it before and I have no idea how to do it with this file and so we need to understand the answer to this question is surprisingly funny how do you upgrade the printer film oh yeah you just print it of course it turns out that this printers has this listening port that receives print jobs this is defined by an HP document called PCL excel future reference protocol class 2.1 supplement that if you are still sane after reading all this thing you understand that the printer accepts a thermal upgrade just the same way as it receives a print job that's it and looking at our file it really correlates with that because you see it says pjl print job language this is exactly what what we expected to see so now that we understand this we need to somehow open this file so we can read it it's compressed somehow and after reading this PCL a document we kinda understand that this thing is composed of a lot of encoders so we need to decode them one by one I'm not going to go too of the decoder because you know it's basically it's quite boring but just to give you a the overview of it it contains stuff that's called null decoder 50 code Delta or decoder there are all decoders they do something like if the previous line was all spaces then if the next line is also all spaces just write one instead of the line it makes sense when you're talking about a print job you know when I print a print page but when you're talking about a film or a binary file it makes absolutely no sense but still this is what it uses and we left about this and said that you know when you're a hammer everything looks like a nail and we turns out that when your printer everything looks like a print job including the framework so okay we managed to decode everything and now we have something that looks like a valid file and now we need to understand how to analyze it so we start to look at this file and write in the beginning of this file we see something that looks like a table so with the we define it and we we understand that it really is a table and this is a table that actually defines sections you see it says something like loading address section name and location in binary so this is great because now we understand that this big file that we are looking at is just composed of smaller sections in it and this table actually defines each and every section so we can now break this into the respective sections and look at every section and that's exactly what we do and then we find one section that looks really interesting to us it's actually the biggest section and it really looks like what we're looking for we are looking for the code for the place for the printer and this is what we see take a look it says hello I don't understand right it's exactly the same thing that we saw on the serial so probably yes this is our code this is what we were looking for but if you look closely it's not exactly there well almost there because some characters are missing from this thing so it's not complete and those characters are consistently missing from the entire file so although we know that we are there until we know we will know what these bytes are we can't go on so we really need to understand what they are so the question is what is this why are those bite missing probably it's another compression algorithm well we have no idea why you need another compression it makes no sense but it's actually the least craziest option that it's it's another compression algorithm so we decide to go with this way also if we try to compress this thing with something like dilib one of the most standard compression algorithms we get 80% better compression and we know that the printer has dilib in it because we can see the strings for the lip so why didn't they use the lip I don't know but the problem is still there and we need to and we need to handle it so now we need to understand those missing bytes in let me walk you through the the analysis process of this so this is one of the code snippets that I just showed you and let's try to decompress this thing together so if you look at this thing basically it's composed of two main categories one is ASCII characters stuff that we can read right and the other is non ASCII characters stuff that we can't read right and look at this it'll bite you and let's take out the ASCII characters and we are left only with the non ASCII characters now these are actually our missing bytes this is what we can't read this will was replaced with something else we need to understand what was it replaced with and now if you stare at this long enough you will start seeing a pattern let me make it a bit clearer to you you see it's composed of again two types of missing bytes one is one byte and two bytes and double bytes and the distance between the born bytes looks suspiciously pattern Asia with the eight bytes 9 bytes 9 bytes 9 bytes 8 bytes and this starts looking like a pattern I mean and if you look at this from a different perspective maybe the pattern will start being a bit clearer you see the FF and the FF they look the same the f7 and the f7 they look the same but what does it mean and in order to understand this you need to sharpen your binary view a bit and if you understand it FF stands for 8 1 bits and if you do this consistently for everything then now you see your button you see the zero bit always falls within this to bite hole always and it's consistent throughout the entire page so the entire file so that's great because now we understand that the first bite is simply a bitmap it's defining the next eight bytes wherever there was a replacement there will be a zero of it that's it so great we understand what is this one byte but now we need to understand what are those two bytes that's a big question and if you know anything about compression then you know the Dozen there's not a lot of options it could either be something like a forward or backward pointer oh it could be a dictionary an index to a dictionary oh it could be something called a sliding window well we can pretty easily say that it's not a for the backward fighter and also we can say that it's not a dictionary simply because you know if we try to reference that we can't find what we are looking for so we're all these options out so it must be a sliding window and when we have this information we go to our favorite favorite place to Google to try to find something similar and we run in run into in some dark corner of the Internet this nice site explaining something called the soft disk library format it defines a lot of things but inside this there is a compression algorithm that looks similar to ours actually it looks really like ours actually it looks exactly like ours exactly and we found it very funny because this thing was invented around 30 years ago and used in history in one place can you guess what place was this no no it wasn't HP at all it was in Commander Keen yes this is a compression algorithm designed and used in commander game the game that I grew up playing so that's we found this really funny but now that we understand this we can actually understand what these two bytes are so basically what they are they just they just define a window location and data length which is all the information that we need in order to compress this thing let me explain to you how this book so we have an input text and output text and a sliding window right and let's try to decode this string here okay using this this method so the first byte is a bitmap we don't know what the value will be so we'll leave it open for now and we begin so a we write it both in the output text and in the sliding window then be the same C D and then when we eat a a is already present in the sliding window so we don't need to write it in the output text and then B is just the following character so again we don't need to write it and then E is a new character so what we write here is 0 0 0 2 what it means is go to the sliding window at position 0 and take the first 2 bytes right and then you continue e f g that's that's all there is to it now you know the bitmap there was a replacement here and you know the value here and that's it that's how you decode this thing it looks very easy when you look at it that way right but we're looking at the Trib reverse is I think a bit more problematic so that's great now we can open this file and now we actually have a film where code that we can look at and now we need to understand what operating system and what is this code even and this took us quite some time but let me just give you the brief explanation of it so we are looking at the operating system a real-time operating system called red X the CPU it's running on is arm 9 it's big-endian and it's manufactured by a company called Green Hills which is manufacturing stuff for missiles and airplanes for the US military so it's pretty good real time operating system and then it's composed of several components like system and stuff common libraries and tasks tasks are the rough equivalent of processes in in in normal operating systems and in system we have a two-stage bootloader and some networking framework and stuff like that and then common libraries just common library libraries libraries that we all know and use and tasks yeah we can define this task and we see the and after we have this picture here so now we know that we need to concentrate on these tasks nothing else is important these tasks are the tasks that control the fax functionality so if we look at them we might be able to find vulnerabilities in there but just a second before we do that we see something that looks pretty suspicious here and this is spider monkey I don't know if you're familiar with spider monkey what it is spider monkey is the JavaScript implementation of Mozilla and we were thinking to ourselves why would the printer need to implement JavaScript it's not a web browser there's absolutely no logic for for it to use JavaScript and we found this question pretty intriguing so we started looking up where is it used in the printer and it turns out that the question is pretty simple it's used in a feature called puck PA see these stands for proxy Auto configuration it's something that configures your proxy automatically when you connect to the network and the most important thing is that the top player of this functionality was written by HP and when we're looking at this top layer functionality we see something that looks like this look at this so it turns out that before doing the proxy auto-configuration the printer connects to this URL fake URL one two three four com it just connects you it does nothing with that connection just connect to it maybe some kind of sanity testing I don't really know why but it does do that and the interesting thing here is do you know who owns this domain fake URL one two three four com any guesses it's not HP you're right I do it wasn't registered so I registered it for $5.00 and now every HP printer in the world connects to my domain hey that's very nice and if if HP is listening I'm willing to sell this domain for a very good price please contact me so yes that's it and now after we talked about all this we can finally talk about facts so TTL td30 also known as itu-t recommendation t 30 is the de facto protocol for sending fax over phone line it's actually does all the heavy lifting all the facts functionality is in this T 30 photo : if you have a fax machine it is using T 30 there is no other option for it it was designed in 1985 and it was less updated in 2005 yeah 30 years ago so we started looking at this protocol and it was very hard to analyze because looking it has graphs like this it might look like maybe doable but every one of these nodes as another state machine in it and another state machine in it it was really really really very very messy and there's a lot of dynamic tables and dynamic tables and dynamic tables and really looking at this statically was not going to get us anywhere we weren't gonna go anywhere so what we need is basically we need a debugger we need some way to debug this printer and the question is how can you debug a printer well it's a good question because you see we have a lot of challenges how do how do we debug this if there's absolutely no native way to debug the printer there are no debugging facilities we have no control over the execution flow we can't stop the machine we can go and we can't actually do anything and even if we could do an it something with it does the hardware watchdog how about watchdog is just watching the CPU and if the CPU halts he will just restart the printer and basically what the debugger does when you put a breakpoint it puts you in an endless loop basically halting the CPU so even if we could put a black dog breakpoint the hardware watchdog will just throw us away and restart the printer so we go no we need to find some way to to overcome this and you know every research project and everything in life needs a little bit of luck and this is where our luck came to be and roughly the same time we do this company called semi Oh found vulnerability called Devils ivy it's a vulnerability in the G soap open-source library and luckily for us the printer has exactly this version of G soap so we have a vulnerability in our printer and we can actually exploit it using its web interface so that's great so now we can exploit the printer so we have control over the execution flow but just to show you how it looks like this is the vulnerable part in the printer the containing the Phase IV if you don't spot the vulnerability it's okay it's here basically the bootable ability is an integer under flow so what this means I don't know if you're familiar with data rates for for sending fax over for printers only but this means that we need to send over to bytes of data in order to to exploit this vulnerability and each one of these iterations takes us around seven minutes so we have to exploit this thing start walking on it and then you know we crash something and then we have to wait for another seven minutes and another seven minutes and another so we waited a lot of seven minutes during this research and it looked something I think like this a lot of coffees do this go get coffee do this go get so it was fun okay so we need to find some way to debug this thing we need to find some way to basically read and write memory now that we have control of the over days accusin flow we need to load our own code and we need to somehow bypass memory protection on the printer and somehow embedded the bugging stab into the Kohen film what we did is design our own debugger we called it scout it supports x86 accessible on both arm and thumb mode we used it before to debug Linux kernel and we can also use it in an embedded mode in this mode it's very versatile so if you have any similar research that you are doing you can basically take this thing define the functions if you know their locations and boom you have a debugger and if you want this tool you can go ahead and get it here we have it on our github account it's I think you will find it pretty useful if you are doing anything like this so yes now we can actually debug this thing and now after we did all this we need to understand how does facts even work so again let me give you the brief explanation of it a fact says there's a sending fax sending modem and receiving modem does the CPU that does all the heavy lifting and then there is all the print jobs and and and and stuff to do printing so we start with the first stage at the first stage there are several phases a phase called network interaction probing arranging equalizer and echo canceller and a training phase if you don't know these phases it's okay but basically you all know them because they sound like this so that's the all they do basically at the end of the day is create a tunnel between the receiving and the sending modem talent called an HD SC tunnel and over this tunnel all the all the other protocols they work so basically now the modem and the CPU are using t30 protocol and T 30 protocol is also divided into several stages in phase a we are the caller ID saying hello I'm this thing and then in phase B we're doing some kind of handshake like I have these features you have these features let's decide that we are using these features pretty standard and then phase C we actually sent the data and then on face D we say okay thank you goodbye basically this is T 30 in a nutshell so let me show you when you send a fax how does it work so a normal fax a black-and-white fax is sent as a tiff file although this entire thing that I showed you over the hdl-c tunnel and then over the data section in phase C and then it gets to the to the printer itself and basically what you sent is the tiff body now the printer needs to have a tiff header in order to print this thing and that affair is composed of the data that is send in phase a and phase B so now we have a complete TIF file and it goes to printing because this is what you do with fax you print it so that's nice but now it turns out the totality has a lot of extensions to it and some of these extensions are really really weird I think one of them is called they're kind of extension yeah it turns out that you can send colorful fax did you know that I didn't know that and I actually have no idea why should you send their colorful fax but apparently you can and it's supported on almost every printer it's almost default in it the procedure is pretty much the same procedure the only difference is that now instead of sending a tiff file we are sending a JPEG file and also it's not just a JP it's a full JPEG file so we are sending both the header and the body of the JPEG file and then again it lets get receive by the printer and then printed so yes that's very nice and now we can start talking about well we can find vulnerability so you saw all of these layers of sending attacks basically we could look at any one of these layers in order to find vulnerabilities but we decided because it's most convenient to start looking at the topmost layers and specifically we wanted to look at the JPEG passing because we're sending a full JPEG file so maybe we have more control of the of the user data and maybe we can find vulnerabilities there so before we discuss the vulnerabilities let me explain to you how a JPEG file looks like basically this is kind of a JPEG file it's composed of sections like a start of image up and then it has a size and data and then another section with its size and data and then another section with its data and then another section which is the end of image this how basically a JPEG file look it looks like and now let's try to look at one of these sections specifically it's a compression section okay a compression is a repeating motto in our research so this section defines a compression table it looks like this it has a header it has a size it has a four by four matrix and then it has data right this is how this section looks like and the way it works is that you basically take this four by four matrix and then you sum up all the values and you see if you sum up all the values here you will get the value six it's one and two and one and two and then you take six bytes from the data section right because this is the sum and you copy them into a 256 stuck buffer right look at this for a second do you see anything strange here well if you're dealing with vulnerability research you probably already understand the problem here and let me explain it to you what will happen if I will send here all ffs what will happen is that the printer will think that he needs to take roughly 4k of data from the data and copy this 4k into a 256 bytes long stalks a buffer so this will create another flow this is just as simple as that so basically we have a stack overflow a very very primitive and very nice stack overflow we have absolutely no constraints because we can send any data we have no forbidden BOTS we have a round 4k of controlled data that we can send and the file even contains more information that we can use later in our exploit chain so this is great so we have an exploit now for the printer over fax and now that we have it we need to bypass all the OS mitigations that the printer provides just kidding there is no there are absolutely no protections on this operating system so basically once you stackoverflow you basically control the printer so these are the two CDs that we received from HP for for the vulnerabilities HP define them as critical with a CVS ESCO of nine point eight which is pretty rare for any vulnerability and this is HP's response I must read it when HP learned of this issue they were quickly to provide updates to mitigate risks HP takes security seriously and encourages customers to keep their systems updated to protect against potential vulnerabilities basically this vulnerability affects all HP Officejet printer so that's around 100 different models of HP and it gives you full control of the printer so let me show you a short demo of how this looks like so this is our attacker machine it connects to a modem that we bought in Amazon for five dollars we run the script and we send our malicious fax and this is our printer so now the facts gets received as you can see there it's sent for me evil attack oh hey we found it funny and yes basically we have complete control over the printer but this is not enough because we want to show how we can go from the printer to any computer connected to it so what we did is put eternal blue inside the value of facts that we sent and now every computer connected to the printer will immediately get exploited as you can see here right now so it's a Cal poppin that means that we can do anything we want to on the on the computer basically we did exactly what we planned to do so we showed how we can get into the internal network just using malicious fax so that's pretty much it so some conclusions PSTN public service telephone line is still a valid attack surface even in 2013 facts can be used as a gateway for internal networks and all the outdated protocols up pretty bad for you so try and not use them if you can but what can you do to protect yourself against this thing basically one thing you can do is patch your printers if you have an HP Officejet printer this link here by provided by HP will tell you if your if your model is vulnerable if it's an office yet it is vulnerable and you can download the updates we actually flew to HP headquarters to help them create the patch for this and the patch box I can tell you another recommendation is if you don't need fax don't connect it if you buy this printer don't just connect it to the fax if you don't need it you better leave it alone but if you do need to connect the fax maybe the best thing to do is to segregate your printers and havin EV them on a separate villain or something like this so if somebody can take control over the printer at least it won't be able to propagate to the rest of the network and though these are all very good recommendations maybe the best recommendation I can give you here today is please stop using facts it's 2018 it's time that we evolve into New York ways of sending documents from one to the other and I can't finish this talk without giving some credits to friends who helped us a lot during this research so these are them they deserve the credit they helped us physically technically mentally and however you would like to say and special thanks to Yan I live near which made it all happen and that's it you can find more of our work here if you want to see thank you very much
Show more