Scale Signature Proof with airSlate SignNow
Get the powerful eSignature capabilities you need from the solution you trust
Choose the pro platform made for pros
Configure eSignature API quickly
Work better together
Scale signature proof, in minutes
Cut the closing time
Keep important data safe
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

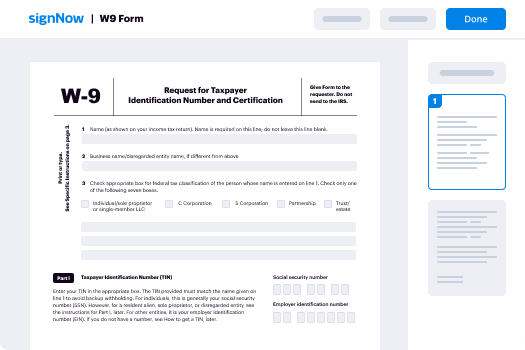
Your step-by-step guide — scale signature proof
Using airSlate SignNow’s eSignature any business can speed up signature workflows and eSign in real-time, delivering a better experience to customers and employees. scale signature proof in a few simple steps. Our mobile-first apps make working on the go possible, even while offline! Sign documents from anywhere in the world and close deals faster.
Follow the step-by-step guide to scale signature proof:
- Log in to your airSlate SignNow account.
- Locate your document in your folders or upload a new one.
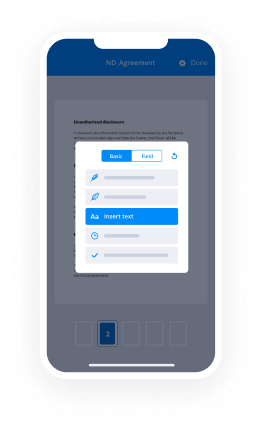
- Open the document and make edits using the Tools menu.
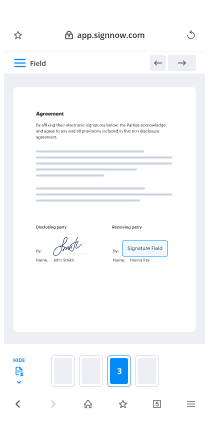
- Drag & drop fillable fields, add text and sign it.
- Add multiple signers using their emails and set the signing order.
- Specify which recipients will get an executed copy.
- Use Advanced Options to limit access to the record and set an expiration date.
- Click Save and Close when completed.
In addition, there are more advanced features available to scale signature proof. Add users to your shared workspace, view teams, and track collaboration. Millions of users across the US and Europe agree that a system that brings people together in one cohesive workspace, is what companies need to keep workflows performing efficiently. The airSlate SignNow REST API enables you to integrate eSignatures into your application, website, CRM or cloud. Check out airSlate SignNow and enjoy faster, easier and overall more productive eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results scale signature proof with airSlate SignNow
Get legally-binding signatures now!
FAQs
-
What is AE signature?
An eSignature or electronic signature is a legal way to get consent or approval on electronic documents or forms. It can replace a handwritten signature in virtually any process. An eSignature or electronic signature is a legal way to get consent or approval on electronic documents or forms. -
What packages require a signature ups?
If you're shipping high-value cargo, firearms, pharmaceuticals, or alcohol, you'll likely need Signature Required Delivery Services. How can you tell if a UPS package delivery requires a signature? You will be emailed tracking information that will indicate if your package requires a signature. -
Does my USPS package require a signature?
Signing for Mail Some pieces of mail require a signature from the recipient at the time of delivery. This includes items sent with Priority Mail Express (if requested), Certified Mail, Collect on Delivery, Insured Mail (over $500), Registered Mail, Return Receipt, Signature Confirmation, and Adult Signature. -
How do I waive my USPS signature?
Option 2: Using the Mailer ID, send Product Tracking and Reporting (PTR) a Waiver of Signature code '3'; Mailer should request the opt out or cancel in advance via the impb@usps.gov mailbox.
What active users are saying — scale signature proof
Scale signature proof
you [Music] thank you all for coming it's really happy to introduce emmerich and Denny who have been here the last three months it's been great fun working with them this summer and on many different things what they gonna tell you about today is a new set of libraries in a and a domain-specific language in F star called steel that we hope to use to scale up reasoning about state in F star thanks Nico involution it's a pleasure to be here today and present to you the result of our internship many critical systems nowadays still are implemented in low-level languages such as C think for instance of operating systems or of the HTTP stack such systems are really cornerstone of modern cybersecurity and because of that because the failure is really high so they are systems that are a very good target for formal verification unfortunately verified low level programming is still very hard and one of the biggest issue comes when we start reasoning about memory and because especially of aliasing so in a lot of a languages you can have pointers pointing to kind of arbitrary regions of memory and you have no guarantees that if you have two different variables we might not a yes so that means that once you start performing updates to some variables you have to reason about is visible variable with our value in my context actually updated as well or not and that means that's proving that some invariants on let's say states or complex memory objects is becoming much harder to prove as well and all of that is just assuming we are verifying sequential programs once we start thinking about concurrent programs it becomes even harder because certainly you have several agents that are sharing some memory performing updates and memory accesses on the same memory and so you have a lot of interference going on so over the past few years several projects have been successful in verifying low-level programs and I only want to mention a few today that were developed as part of Project Everest the first one is error crypt which is a verified industrial-grade cryptographic provider implemented in estar and which extracts to a mix of scene and assembly code for maximum performance and what are the many really impressive things about ever crypt is that its performance beats state of the arts unverified implementation in many cases the other project I want to mention is ever pass which as the name suggests provides verified passes and serializers and there is ongoing work to actually integrate the verified ever past library in to Microsoft's hyper-v so such projects showed that verified low-level programming was no viable like way total about a hundred thousand lines of code they are pretty massive projects but it still requires a lot of effort it requires a lot of human interaction human annotation and it sometimes feels like climbing a mountain so why is that a problem so f star is an SMT based tool for verification and as many of our SMT based tools it reasons in memory using classical ha logic and select update reasoning and it has many advantages first of all it's fairly general it's very simple it's nice first order logic so it's very nice to encode into SMT logic but it's also known to have issues scaling up so what are the other possibilities over the past 20 years there has been a lot of research into types based guessing control systems in the player community and it's languages such as cyclone of all that have been developed over the past 20 years and this idea is funny made their way into mainstream languages such as the rest language so rust is the language that provides you with many fascinating guarantees such as memory safety under duress freedom and all of that by virtue of typing so what this means is that if you have a rest program that type checks and compiles you are guaranteed to have memory safety and a terrace freedom and so that's great because for many people you get office properties that's all we need but unfortunately it's not yet good enough for critical systems first of all most programs are not verified they are not proven correct so you have safety but you don't have formal functional correctness for instance and second rust has this system called unsafe locks but allows you to temporarily escape rusts dive system and it has its uses it has its reasons but so kind of defeats the purpose of having all of this nice safety guarantees in rust as soon as you're going to be on Safehold so today we are presenting steel which ends up providing ownership and verification via resource typing so still is a domain-specific language with sincerity embedded into a type theory based proof assistance namely F star and/or target which still is really general-purpose concurrent systems programming so still programs are unsure to be always safe and on top of that the user can decide how much he or she wants to verify about the programs it can run from nothing at all we just want memory safety we're fine with that to full-fledged complex security and functional properties and as it is generally embedded into F style we can also prove that it's curve theory is sound within F star logic any addition steel is very extensible with new constructs as its implemented in F style we can just prove implement and prove some new libraries and then package them to give them to the user as part of a stream framework so here are the main ideas and concepts is a steal steal is designed as a separation logic abstraction on top of the F style memory model so we are seeing he predicates as resources and we provide separation and framing for them in order to do inference control we also a lot reason about permissions on such resources that is we can either have an exclusive mutable or shared immutable or read-only access to resources and finally we are aiming the concurrency and so we want to be able to prove and very to implement and verify concurrent programs in a simple folk Jenkins model with locks so overall this internship we laid the foundations for this steel framework and that means we implemented and proved the crawl memory model correct we implemented a system for resources with separation permissions framing and we provided operators to start to implement and verify concurrent programs building upon that we started implementing several verified librarians of skills for both singly and doubling lists but as a disclaimer we don't believe that this remark is mature yet there still are many queries many thing we want to solve like for instance it still requires more annotations than we would like it still needs to be specifications still needs to be formulated in a specific way for things to work smoothly so it still requires a lot of she's on knowledge so in a sense this summit was about steel episode 1 and we are hoping that after a few more month of work we can get it all nice and shiny to give it a bright future wait three details so now that we know why we're doing this steel framework we're going to dive into the main ideas of the framework and as you'll be able to see they kind of build on each other so first we have to start if the idea of resource so before in lodestar in the f star that we had before we used to see each function as taking a whole heap and then transforming into another heap but actually these functions they operate in a very small portion of the heap so we wanted to restrict actually what each individual function could say about the heap in order to do that we first have the concept of footprints a resource which is what the functions are going to talk about have has a footprint which is a hip fragment and not the whole heap and then on this footprint to intuit action invariance which is going to be a consistent assertion that's going to be valid across all the hips okay so given those two simple ideas we can define some examples of resources first you have the empty resource the footprint is just the non location there's no location no footprint associated to it and the environment is always true but as we have more interesting resources we have the pointer resource the array resource to each point to a single cell in our memory model and the invariant is that their life they should be live across all hips when we want to talk about them live meaning that they're not the reference they've been allocated and not the reference okay so now we have like the basic blocks of our resource building but we can actually say more rich things about resources for instance we can talk about their contents this resource says that pointer P points to value V the array B points to an array of size two which whose first come first cell is contains a value which is greater than zero and you can see you can use this resource language to actually specify what's happening inside a particular heap so we attach the first component or e-resources which which is the view and the view is quite kind of not as important that is the last two but it's kind of a high-level description of what the contents of the heap are associated to this resource so now that we have our resources we can separate them because in separation logic the we have this very pervasive operation which is a star paradigm and that lets us define the heap as a collection of things that are disjoint to each other and this is this the basic block we're going to use to build our still framework for instance in separation logic you would write a heap containing two pointers pointing to two different values and you can see those pointers are not aliased because there is a case on the star operator and we can see that in our steel framework using our resource language when we define the stars like the footprints are disjoint okay so now then we can actually have some separation logic inside F star with this resource language let's define a list so here is the singly linked list X that corresponds to a list L what resources is that if L is empty then the resource is just empty resource and if L he's had the head of the list and then the tail then the resource is just the pointer X should point to the head start meaning not earliest with the rest of the list so that's nice we now have a way to specify fragments of the heap in a fairly logical and it's what you're used to if you separation logic now we have to enforce that the heap is actually corresponds to this description of the heap and we do that with resource typing we actually leveraged F stars effect system and define a new computation type which is called RSD so for a computation of type alpha we can say that the computation expects to heap satisfying all the things described in resource and provides after the computation a new resource which is going to describe the heap fragments after the computation and you can see here there's a function it's because the final resource can depend on the value returned by the computation so this is first theoretical let's give some examples right now what happens when we want to allocate a pointer so this is the a lock a lock function it takes a value and returns a pointer pointing to that to the this value of this type so what how to specify that using resources well at the beginning you just expect nothing the allocation function should work anywhere so you expect empty resource and then you're going to provide the resource which is going to be pointer pointing towards your value and you can see here we take advantage of the the function mechanism you can talk in your final resource about the value that's been returned by your function let's do another example let's say you want to update the value inside the pointer so this is the classical function take a pointer the new value you want to be the pointer to point to it's a stateful function return e in it it expects the pointer P we don't care what's the value inside the pointer but then in the end we're going to have a pointer that points to V and here we don't use the unit think that's returned by the function ok so now we have a way to specify feel free to rest for the SMS I think you hear something you don't lose them but this is after question fish is pointer P book or resource and the left-hand side of this corner people is that the same that's the same expression of pointer P that's been used so actually here you can see there's a difference and it's PGR yeah so there's there's a it's a different for a reason because you can see here pointer alpha is the type of like the actual value of the last two lines expects PTR P and provides PTR p lv that says so you put over these so keeps your kids or resource and you put it on the left side of that alright so okay so i think there are two arrows sorry for news this is like the classical so so this PTFE and PTFE match to be is a resource refinement okay so it's a roof so VTR fee is just saying you have a pointer is live I don't know what it points to PTR being back story said his life and actually points to be so if you come back here we can have the standard pointer resource and then we can refine these traits are saying that the points are actually points to be put any resource on the left hand side of the matter okay yep and there's an interpretation for any kind of resource in that sense raisin type of the resource you haven't you have to define this refinement for it I mean there is a way to inside the framework to actually needs to define that but it's it's called recent research assignments but maybe you and every resource has a view okay that's a the value that's in the resource okay yeah so for these two functions oh yeah I guess your assignment yep um do these so there's the effect there yeah but these functions have an implementation yes they have it okay this is just the specification development implementation I'm going to talk about so now we can actually specify what our function should do in terms of our new nice separation logic description actually staying on that specification if you want to specify things using a full separation on work style then if you want to specify the increment function for a pointer let's say you have a pointer to an int and yet you want to add 1 to the value then if you want to specify it to easy separation logic you actually have to say ok there's a ghost value which is like the value contained inside the pointer and then you have to say ok the the value after is V plus 1 but this is not the style in which we're used to specify functions in F star historically because we don't want to carry these ghosts arguments around because we're actually extracting to see so we have me to make sure they realize Excel Excel so we actually provide a hatch to actually use the old style of specification in conjunction with the separation logic so let's say you're defining your increment function again you're specifying your increment function again but then you're adopting a less precise description of the resource because here you only tell him about the shape of the heap you're not talking about the contents and to talk about the contents you can add another clause in your specification which is going to be a traditional insurance close and and shirts close is going to provide you with all the new which with which you can access the view of your resources before and after the computation so then you can say ok so the new view of PTR V which is like the value inside the pointer is equal to the old view of PTR P plus 1 and that allows you to have more stateful specification style if you don't want to carry this gross value around okay that was assignment now let's move on to the implementation of these functions no they're not keywords they're in the implementation they're just functions they're functions that that take a resource which you have in context and return you have you have a require skills that's symmetrical Ventures you have like expects provides and then requiring Accenture so it ensures is the same as provides and then you have a requires clues that sustain lives explained as I wanted to just improvise and then have a view they're wider key points to all wired people's watch and say that nobody can say that you can't say that then that's one of the pitfalls of separation of this reciprocation you have to actually carry all the values in your program in the specification okay yeah it's not for you actually decide which you prefer it's either like a lot further and there's no in between that's right okay today you could have said you could have one bounder goes badly for some of your pointers but not rather other parties yeah there could be a little ground and you could find the gross value once they additionally well it happens to be quite often let's say zero so yeah you could talk about something that doesn't exist anymore and new well so actually this is like going to a very technical point but I can provide you the answer these all the new functions they're actually functions that have a restricted domain and you can only apply them to stuff that is inside your resource context so if you if for the allocation function that provides would be the empty heap and so you can apply new to only things that are contained inside the empty resource which is nothing so we guarantee that you can't talk about things that don't exist okay thanks but this might be a little technical so let's move on with the old and new are certainly not the whole heap yeah we will never let you speak about the contents of the interactive all these specifications are small footprint if you leave up provides the assumption that the research doesn't change and edit where the resource goes away so for now you always have to include expects and provide services so you have to describe and in your provides post if the resource isn't there it goes away like provides EMP as yeah ok let's move on to implementing these functions we feel we're in the process of specifying so the way you implements and prove memory safety about your functions in separation logic is that you use the framework the framework says that you have a function from Q to R Q to R then you can apply it to some P star Q and it's going to give you a pistol or P is going to be untouched by the function the neat thing is that you can actually express that role as a still function a special function that's going to take the initial and final resource context the function Q and R and it's just going to return your computation with the right resource context so with that function and actually this is like the workhorse of still because all of your function calls they should be encapsulated inside the frame rule so that for each state full operation and the heap you know precisely which part is modified in which part is untouched and that's said that's what allows us to have modularity when reasoning about the heap but the frame wall and encoding all of that inside F star and reaching a level of automation and usability for the user it has been challenging for instance let's say you have some P star Q star or in the context and that you have a function which just works on queuing it returns the Q prime then what you want is you want to actually select the Q inside and then perform your computation then recompose the things together but actually you have to prove all these steps so first you have like to rewrite this term using a associativity and commutativity isolate the q apply the frame wall apply F then recompose that always still the frame wall your crew Prime and then actually rewrite the term again in rows you have your E prime here and all of these steps have to be proven and the way to do that with an SMT is that you take this term and you like explode the context with all of the possible rewritings of that in hope that if you further in order to apply that you select the correct one this is not very efficient the second problem is that we going higher order with these companies because before if the updates selects heap model we just had higher the first order term terms which could fit to the SMT but then since our resource our heap predicate the star which is like takes two resources in return a resource is actually higher order because these types they hide some some functions inside them so these specifications and this verification conditions that are stemming from the specification using separation logic are not going to compose wall of the SMT so the classic way to solve verification conditions not manually first are just to feed them off SMT but since 27 we have tactics and we have in something called mana a star so what we're actually going to do is that work we will be crafting tactics to solve all of the verification conditions tied to our separation logics specification framework and the rest we're going to fit two SMT as before and it's using that mix of tactic and SMT that we can reach a level of usability and a niceness for the user in the framework so this is the first concept of still and we have something that lets you specify function using separation object and proof that they respect that specification using the framework but now as Emmerich mentions we want to be able to talk about ownership and what if you want to share data across different actors or something right now with the stuff that was already presented all the function they require exclusive your ownership if you remember the update pointer which I've shown you earlier here having the pointer Peak resource in the context when you call it means that you have exclusive ownership over that pointer and it is the case because you can't duplicate resources in your context because the context is the least of these don't resources so if you have two pointers aliasing to the same thing they can't be disjoint from each other but what if we want to wait we only wanted to read P then we have like a read-only P in our context and then the type checker should like this allow these kind of updates mechanisms well we can actually do that it's a classic extension to separation logic we can define read-only resources read-only are and readwrite are redirect resources then for instance our pointer dereference specification which is like takes the pointer and returns the value inside it just expects to read only resource and provides the read-only resource pointing to it and here we know that because they are read-only the contents haven't been modified okay so how do we produce these read-only resources we have a rule for that the Sherrill which takes a pointer and we will return another pointer so it expects the first pointer to be read right and then it's going to return another pointer which is going to be the immutable copy of the first pointer and you can see that in the final heap the two pointers are disjoint using our separation logic framework although there are aliases so in that way we can control precisely were what's the a lacing that can be done the so this a classical extension to separation logic usually comes which way okay so we have like multiple read-only copies of the resource but then we want to gather them back and recover full permission at some point and usually separation objects include some scopes allocations the allocation mechanism for like having some read-only and then gathering them back and the N but we said okay we have a Cintiq so why not go like more general than that so we actually implemented fractional permissions we just said okay so you have a resource in the heap it says permission like a fraction between 0 and 1 1 meaning that you have full permission so then the gavel roll is that okay you just have two pointers they're disjoint but have permission F then when you gather them back you just have a single pointer with the some of the permissions of both and the other pointer is not in the context meaning that you can't talk about it anymore it's not live anymore you can't access this it's gone of course you can't do you can't do that with like every pointer you had there have to be alias to the same thing for you to to be able to do that so the nice thing about this extension is that it stays within the trusted computing base and the memory model because we can implement those permissions as a ghost values stored somewhere inside the heap and all the permissions when you manipulates permissions inside the steel framework everything is static it's statically checked and you have to account for all the permission things but we can do that because we have a semi that's going to users with these tasks and actually if you don't want to use fractional permission because it's too complicated and you if your needs are something much simpler like scopes allocation of Riesling resource then you can define it as a verified library on top of the existing framework and that allows us to define more restrictive patterns of permission usage while staying in the song sound world and now for the next main idea I'm going to hand over yep ERP if you won't say anything it has permission one without presence yeah last main concept of Steel is how do we handle concurrency how do we implement and verify concurrent programs so our target here is we want to prove that our programs are that arrays free and we're going to assume that we are in a sequentially consistent model and we are focusing especially on simple controls model which is a simple scoped full joint model with a pollinator and we're going to be sharing mutable memory using blocks so how does this work steel is very heavily inspired from separation logic and separation logic has a standard extension called concurrent separation logic to handle concurrency really being if you have two functions F and G but work on different heap Pregnant's you can just execute them in parallel assuming the different fragments are actually separated so in other words what this means is if you have two functions that operate on disjoint separated regions of memory it is safe to fork execute them in parallel wait until they terminate and then join again to resume the execution of the main program and so that's something that is very is easily accessible in still we can just define this parameter that takes exactly these two functions and assuming they actually operate on separated resources we can execute them in parallel safely and back the model that is already fairly expressive for instance if you think about a merge sort on list the way merge sort works is you speed released somewhere you take two sub lists you sort them recursively and very pneumatic energy and so that's something that is very polarizable because you can just sort you to somebody in parallel and that's something that can be captured by power because this two sub lists are actually disjoint similarly in our context when we have different pointers to omit a difference immutable point of two resources we are considering whether we are separated as well so using this pair Combinator we can also share immutable resources across agents but what happens if we actually want to share mutable memory one of the classic example is this consumer producer mala well basically you have two agents that are sharing one data structure usually you queue and one of the agents is feeding the queue the other one is emptying the queue and basically they are both performing updates and reads on the same data structure in parallel so how does this work luckily for us concurrent separation logic also has a solution which is based on locks so the idea is if we have a heap predicate P initially in our context we can take a look that is associated to this specific hit predicate and once this hip region is locked after creating the lock it's not available anymore because we cannot access it before actually acquiring the lock and so because of that we have this acquire and already functions that take a specific lock and say well if I acquire a lock I know how these vessels in my context meaning I can operate on it I can access it I can update it and conversely valleys will say we are not releasing the lock we don't have access personally to be sauce anymore but other people will be allowed to access rock and one of the many very interesting things here is this resource is not just a memory object it also comes from a predicate with an invariance and this invariance will be ensured by verlox so the idea is whenever we acquire the lock we also acquire a heap invariant which is associated to a lock and then that means we can do whatever we want with the resource and when when we release it we will need again to prove that this invariant is satisfied and that is safe because whenever we have a lock nobody else no other agent can actually access the resource not even read from the resource so in a sense we don't need to preserve invariants between the acquisition and the release we only need to prove that it's preserved again when we release the lock and other agents to access the rock so again instill this is fairly straightforward to specify we can just for instance have this acquire function that takes a lock on a resource it doesn't need anything at the beginning and gives you the resource back and that's something so always in variants we are check statically again using SMT solving since we are doing verification but availability of locks is checked at runtime we have blocking semantics meaning if you try to acquire a lock and the lock is already owned by somebody else you are just going to wait until this log becomes available so that also means that at the moment kissed we are not trying to prevent deadlocks it might be a case that you are waiting for a lock that will never be released and so your program will block to be here on the left is a predicate integration logic and it's which is no because this new cells will have will be about the different hip fragment so in a sense it's not just a predicate it's a hip fragment with a predicate on this specific hit fragment so if you just allocate new cell you will be in a different key fragment and hence you will have a different resource you can do that so this so you can have a resource for a necklace that says this this captures a abstract location in memory that is potentially unbounded and but it's reachable from say the head of the list and you can allocate and say cons I to the tail of this let's say and then package it back into the same as the same resources before so for concurrency all of the operators we have currently don't have an implementation and because of that to ensure that we still have all of a safety properties for all state programs we need to provide a proof of Sun Ness of our controller model and that's something that we are still working on with this tier work in progress but so basically I just want to give a general idea of this proof so we are working in a sequential model which means that we are Americans consider what functions are a list of atomic instructions being either operating sun block acquire release all updates or reads from memory so we have two functions here F and G that have a list of atomic operations and they operate on separated resources and we are sharing the hearts unlocked memory so basically what we want to prove is that for any possible interleaving of Base atomic operations but is non-blocking then we still have this specification that is admissible but is assuming we have this initial start with sources in the end we indeed get this star resources and that's something that we are actually formalizing and proving in F star this is not a proof on paper but that is still a work in progress so building upon this I want to spend a bit of time just presenting what we can actually do with this steel framework and one of the best examples of that is how do you implement link lists so link lists have our fairly dynamic structure with a lot of aliasing and because of that that's a nice example to showcase what offering or can do so as any presented previously it's very straightforward ins to define what the released resource is it's just you have a pointer and if the pointer opens to an empty list you actually don't have anything you have empty heap if it does not if it points to a non-empty list you have pointer that points to the head of a list and then recursively you have the next pointer that points to it rest of release and so this is a nice clean concise specification for lines to encapsulate all of the invariants about your list using that you can define you can rebel give signatures for the usual operations on lists for instance appending an element at the beginning of a list so here what we are saying is if we have a pointer to a cell that is separated from tourists we can just append this element at the head of a list and what you get in the end is a pointer to the whole list where the elements was appended and similarly we can define a map operation where we are saying again we have a pointer to a list initially we have a function that will operate on the cells of these lists and in VN what we get is the same list where the F function was applied to all of the cells of a list and so in comparison this is what it looks like in low style which is the current DSL for doing low level notification in F star just this specification of what is a valid list takes about 20 lines in F star and I omitted this for brevity but basically it's saying we have this invariant and then we have to define exactly what the heap fragment is it's much more complex design and then for instance defining the same function append cons takes a lot more work because we have to specify carefully all of invariance we have to specify exactly what is modified I don't want to go too much into detail but it's just if you look on the left it looks much cleaner and nicer than what is on the right and so because of that in the currents stages of Steel we are providing cons heap date and map primitives for lists and we're specification takes about 30 lines of code in sitio it takes about a hundred lines in low star and let's just our specification once you start looking at the implementation it becomes much much worse because implementation in steel is going to be very straightforward as I'll show in a minute while implementation in nostril would involve a lot of limas to reason again about aliasing and things like that so what does this implementation actually look like in steel I just want to show a very small excerpt of how the map function actually works and this is the recursive case of a map function where you are first applying the function to a head of a list and then recursively applying map to will take up a list so here what we are seeing is that we need to apply this framework or separation logic to do that because when we are first updating the head of a list the rest of a list should remain untouched and similarly when we are updating the terriblest head of a list you remain untouched and that's still a limitation of a framework which is we have to apply this frame rule explicitly we have to give exactly what is in the context initially and at the end of the execution of each function would much rather have something simple at that which is well I want to apply function I'm applying a function that's all I need to know if the framework should take care of all of that for us that's a fairly tricky problem it requires a lot of engineering and language design and we are working on having a better frame inference and perhaps some syntax that would do that automatically for the user so the last example I want to quickly mention is doubly linked lists over the next few day over the last few days Nick implemented doubly linked lists in steel and helium atoms a few other like common primitives such as allocating a list concatenating to doubling lists appending an element at the beginning or at the tail and doing that for the whole specification implementation and proof took about four hundred lines of code and it took Nick a few hours as well do that in comparison where is a doubly linked list in losta which is slightly more complex but this library to specify all of it in variant and especially to prove all of the implementations correct with respect to aliasing takes thousands of lines of code so it seems to suggest that steel is much more adapted to this kind of complex aliasing problems and it also seems to be making for proofs that are both faster and more robust when the existing does not framework so in comparison please yes how many of those 400 lives are restraining quite a few so it's really even nice that once the frame-off is mature so that's kind of like the current status and it's hopefully should be even better once we are actually in a few so yeah one thing I'd read we were writing these applications of the brain by hand but the tactics are solving that are still doing all they see rewriting so I just have to assert what I what we supposed to have right now and what resource I expect to get afterwards and the tactic does the rest so it's not yeah it's still sort of manageable you need you need this many organizations but in a sense I don't think you need any external Emma's to prove anything while you know if a.w think his library that currently exists in la style is full of such famous original Italian what's my final knot and yeah one of the interesting part is this w linked list structure that's actually something that is not expressible in safe rust and the reason for that is that breast safe type system has some restriction on addressing and especially it is restricted to on alias 3 shape to that structure so W linked lists are I think is too complex for cron trust you need to implement it in the unsafe world if you want to do at university so you so your answer to dealing with unsafe blocks is to not have it is to prevent is to not need them not to be able to deal with them at the moment we think we don't need them and I just took in a minute about what could possibly be a way to dealing with unsafe blocks yeah so I thought it's internship what we have to have to do we still think that novice promote to be mature we need a few more months of work in order to be comfortable with unleashing users and the biggest item is we want to make this framework more usable I hinted at some things for instance this prime rule that we have to apply explicitly we have some ideas perhaps doing a front-end syntax to hide some of the gory details make it easier for a user to use offical movie framework and that's really a lot of language design work to do that we also want to make sure that we are fine-tuning as much as we can the queries that are fast to SNT solvers so that we have some nice abstractions but we don't want to leak accidentally some things that are not needed by us into solver and might just confuse it and if we want to have a comprehensive framework that allows you to the verified low-level programming we also probably need more basic libraries like we currently have a fairly comprehensive library for both pointer on the race and basic ones for lists and W Inc lists with foreign minister more like based data structures and so on and additionally one other thing we want to do is have a nice and complete operation with the existing law style which is again this framework to do a lot of our programming in their style movements and the reason for that is that first of all we have many fascinating projects such as ever crypt or overpass but are currently implemented in no style and we would really like to build upon them not just throw them away because we are changing the framework so we need a way to be able to build upon them to preserve our guarantees and to have all of these that employer operates smoothly and the second reason is that possibly you could almost see unsafe plugs as a pharmacy and lost our can be pretty adapted to some forms of C so it would perhaps be possible if you really want to break out of guarantees to verify the equivalent of very unsafe plugs into your style and interoperate so that's also something we are thinking about we are not sure exactly what we will need would be so that's our future and the last item we have left is also to actually wrap up this concurrency model so first of all there exists technique to statically prevent deadlocks we want to see if we could apply them to a framework and also see if the framework still remains efficient and scalable this way and we also need to well complete a proper Sundays to ensure that everything remains safe and nice so to conclude over the summer which finally gave F style its long-awaited star which is great what took so long well separation logic if you just have SMT solving it's it's not working it's not scalable it's too hard to specify it as I ordered order logic it just doesn't work so first of all we had to wait for F star to have miss tactics framework that allows you to reason about these kind of things but there have also been previous lands at doing separation logic of tactics and if you just use pure tactics it becomes tedious for instance where was a previous implementation with tactics of appending to linked lists and it took about a hundred lines of manually applying time it was very tedious it was just not so nice to program with so what really worked with us with summer was the nice combination the great combination of tactics and SMT solving with right abstractions including resource typing to make its work and to make it scale and building upon that we have many fascinating applications that could be targeted and we can finally go beyond crypto verification so a first one is if we can verify concurrent programs we might be able to verify concurrent the network protocols such as quick and the other one is if we can actually scale up to bigger systems we might just be able to verify critical system components in let's say a zero so there is some work with your hyper-v people we might be able to verify some parts of hyper-v or some parts of Asia yes and we might also have many possible synergies with our projects in normally we are fairly close to what Christ is doing so maybe we could be able to verify rest programs inside of Steel and we actually want to see if we can design a fronted language to verify rest programs directly inside steel and whereas also is govern a language that is developed currently at Microsoft Research Cambridge which basically does ownership based systems programming and it would be interesting to see if we can perhaps verify some of its components inside of steel and have a nice collaboration with people so that we can have a more comprehensive tool in a sense so yeah we would like to take some time to give our system very sincere thanks to both Nick and Jonathan or advice over the summer for all of her help and advice they provided we like to thank also tahina and NL for to help they provided with both the F style memory model and vm8 F star framework and also motivates all of project addressed members and DMS our community for many fun and interesting discussions throughout the summer thank you the jumper teams only that he has a specialized solver for separation logic based on realizing something that fit with your check tube so what does it exactly just so we his claim is that as you do the symbolic execution there's no separation logic it's an advantage to know what is neat necessarily equal and you couldn't simplify some terms that press they cannot function default isn't T solver interface doesn't so I guess it might be somewhat similar to what we are doing but one of the nice parts about this framework at least to apply to F star is we don't need to extend it with any additional solver in a sense we are purely using what currently exists we have tactics framework in F star but already exist on that we already trust and we already have an encoding of have stop verification conditions in to get free so if you were only using the encoding community that's right civility is really discharge based hard verification conditions for the three inside of the tactics so doing all of this associative and commutative writing with tactics by manually qusomes so what happens in the hood is that you have this associativity and commutative operator which a star what we do is we normalize both terms of the both sides of the equal inside we have a tactic to normalize terms and then we compare the normalized form that's how we used to be so I think he takes it one step further and okay so do destination conversation yes maybe you can do that we'll look into them so what's up coach generating good generation story so but that is still to reuse the existing pipeline so there is currently a compiler from lost our existing DSL to see and so the idea is we are defining still as an abstraction of the existing lost are so since it's just an abstraction once we try to extract we want to just reuse the existing code and there might be sonic minor changes to do but that's what you know actually extracts pretty well with like existing Kremlin the only downsides as for permissions let's say you want to share data but the way we prove that is inside the memory model is that we have to look in the heap to see what are the permissions and update them so it's going to extract to like read and update but you don't think you don't do anything with the value of the it because it's ghost so we we need to like remove that because it's unnecessary and performance yes it's extract to see more runtime the model of locks you have can you store them in the heat that's right can you what can you store your lock pointers in the heat so that's something that we didn't completely self-taught yet the holocron trans model is still a work in progress but I think that's what we are aiming for right here marks are just values so you can store them in the heap but you can't but locks do not have lifetime of their own you can't reclaim a lot right but will you not run into like step indexing hell with your semantics if you go down this route if you're not careful maybe we should talk more yeah happy does the typical if you want okay it's an implement a lock I'm touching you to keep I like it's something sort of shared space you can't just pass it around catch those passive copies lock or not as I'm not here no yeah it's it's a it's a ref marleah ref I have a question about your frame role vamos syntactically you were using it star Q as a variable yeah what was that cheating or we have that cinta so it was a presentation cheating a lot of the work that still remains to be done with the framework is actually making sure that you can use the frame role of that syntactic shading because basically I'm going to shoot back the the roll back again yeah if it binds P and Q separately not binding P star Q yeah no so the thing is that when you use it currently you actually feeds its mr. Q and then it eats resolved speed because it looks at because knows Q and R from the function it knows P star Q and Q star P star R so the remaining thing is that you have to so it's okay let me let me know okay so you know Q an arc from the function you know mr. Q and P star R so what you don't know is P and the actual there's a tactic that will like find Pete from P star Q and P star or because you know if you in R so that's that's the cheating but it's all very toxic actually so to answer your question no we don't actually write P star Q it right like auto zero and Auto one and then inferring the actual P is done automatically protected and we will be happy to like send you some quick pointers if you want to look more in your data better so so does that mean you have to have precision on your formula here and separation logic or what what about disjunction I guess is a question we don't have this Junction okay it's started only operator yes we combine these sorts of things all right well let's thank that I've written [Applause]
Show moreFrequently asked questions
How do you add an electronic signature to a form or contract?
How can I eSign a contract?
How do you sign a PDF doc online?
Get more for scale signature proof with airSlate SignNow
- Insist on signatory Compromise Agreement Template
- Insist on signatory IT Consulting Agreement Template
- Insist on signatory Joint Marketing Agreement Template
- Insist on signatory Distribution Agreement Template
- Insist on signatory Tripartite Agreement Template
- Insist on signatory Consignment Agreement Template
- Insist on signatory Technical Services Consulting Agreement Template
- Insist on signatory Asset Purchase Agreement Template
- Insist on signatory Financial Consulting Agreement Template
- Insist on signatory Web Design Agreement Template
- Insist on signatory Construction Joint Venture Agreement Template
- Insist on signatory Advertising Agency Agreement Template
- Insist on signatory Radio Advertising Agreement Template
- Insist on signatory Residential Rental Agreement
- Insist on signatory Month-To-Month Rental Agreement Template
- Insist on signatory Loan Agreement Template
- Insist on signatory Software Distribution Agreement Template
- Insist on signatory Exclusivity Agreement Template
- Insist on signatory Source Code License Agreement Template
- Insist on signatory Software Maintenance Agreement Template
- Insist on signatory Architect Agreement Template
- Insist on signatory Website Development Agreement Template
- Insist on signatory Heads of Agreement Template
- Insist on signatory Volunteer Agreement Template
- Insist on signatory Strategic Alliance Agreement Template
- Insist on signatory Telecommuting Agreement Template
- Insist on signatory Salvage Agreement Template
- Insist on signatory Facility Rental Agreement Template